If you've ever stuffed a caramel apple into your mouth around Halloween then you know just how delicious the combination of apples and caramel sauce is. The caramel offers a melting, sweet complement to the tart and crisp apple.

dewalttv teaches you how to cut nested crown molding with a DEWALT miter saw. The advantage of this position is that it doesn't require a bevel angle. The bottom of the molding should be placed against the fence. To cut the right piece, set the miter to 45 degrees to the left and make the cut. To cut the other piece, the left one, set the miter angle to 45 degrees to the right and cut. You are done. This technique is useful when you don't want to worry about setting up a level cut.

In this video, Lusitano 9514 will show you how to make a homemade rubber band bow and arrow out of common household items. To do it, you will only need a basic plastic coat hanger, a long rubber band, and some kind of a stick (for the "arrow"), all of which are quite inexpensive. Watch Lusitano 9514 demonstrate for you exactly how to make the bow and arrow, and show how it works. You will also learn tips and tricks, such as what materials make better ammunition, and what kind of "arrows" are ...

This film explains how to count cards in black jack to gain an advantage. Every suit in a deck is said to add or minus up to a count of zero. So the whole deck has a count of zero. There's some synthesized high speed music in the middle while the presenter extracts the spades to show us. Ten to ace have a value of minus one. Seven, eight and nine have a value of zero and the numbers below seven have a value of plus one. The pluses and minuses cancel each other out to produce zero. The numbers...

This is video is a tutorial on how to save more money in your daily life. The video says that budget professional suggest that we need to set a goal. Decide why you're saving your money. Save your money to where if there were an emergency you could comfortably use your savings. The video suggests taking advantage of your employer's retirement fund. Last but certainly not least, we are told that saving sooner is better than saving later.

In Call of Duty 4: Modern Warfare 2, there's a glitch that you can take advantage of when you have both a javelin and a grenade in your hands. Modern Warfare 2 is pretty much the game of the moment, of the year, of the decade, so exploit this glitch while you still can! Fair warning, though: doing this glitch could get you banned by the powers that be at XBox Live.

Watch and learn how to solve the Hanayama Cast Chain metal puzzle in this video tutorial. The Hanayama Cast Chain is a 6 out of 6 for difficulty.

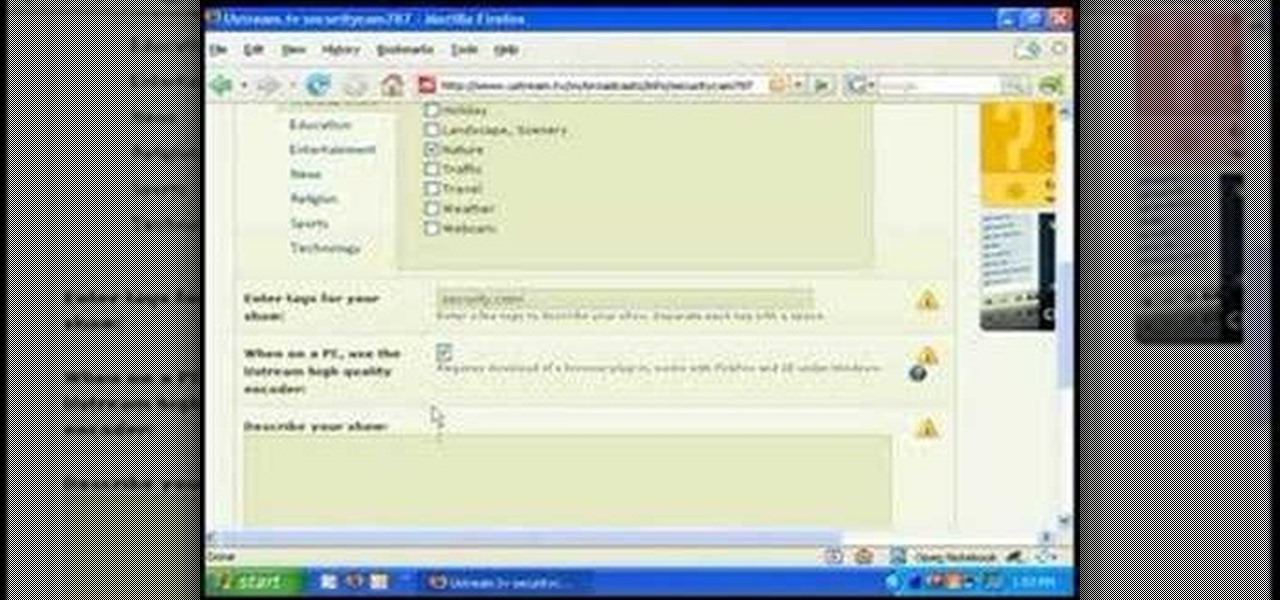
You have a webcam, right? Nowadays, who doesn't? But just because you all have webcams doesn't mean you're using them the same way. And a great way to take full advantage of your peripheral or built-in webcam is by turning it into a security camera. This video will show you how to turn it into a security cam by accessing the video feed remotely over the internet. And it's a really simple solution—you just need to sign up for a USTREAM account, which allows you to stream webcam footage live!

In these two videos, Matt discusses 1.d4 d5 2.e3 Bf5, preventing White's Stonewall setup by beating White to the d3-h7 diagonal. The only way White can play for an advantage is to play 3.c4 with the goal of an early attack on b7. Some of these positions can also be reached via the Slav Defense.

ACMG Ski Guide Cliff Umpleby discusses how to build a T-Slot anchor using ice axe and skis. Once you have your anchor, learn how to use it to rescue someone from a crevasse. Part two demonstrates transferring the load onto the anchor and escaping the system. Part three demonstrates checking the victim and droppping a loop for a 2:1 pulley system. Part 4 demonstrates creating a Z Pulley for 6:1 advantage.

This year's holiday shopping season is shaping up to be fertile ground for augmented reality to show its worth, as both Walmart and Target have crafted immersive experiences designed to engage shoppers in the coming weeks.

Long before Nvidia figured out how to embed neural networks in its graphics processor units (GPUs) for driverless vehicles, it and other chipmakers were already making the same kinds of devices for 3D games and other apps.

After 6 years of development, the big banks seem to be ready to combat Venmo on the money sending frontier, but now it might be too late.

As drug-resistant bacteria become more commonplace, researchers are looking for new antibacterial strategies to disrupt disease-causing microbes. Some scientists are working to create new drugs, while others are trying out drug combinations. Another group, however, are ditching pharmaceuticals altogether and experimenting with non-drug alternatives.

Welcome back, my budding hackers! As you know, I firmly believe that to be a true professional hacker, you need to be proficient in Linux. This is for a number of good reasons.

This origami is much easier as this one, but it still takes a lot of time to make all the triangles.

Can't decide between the Galaxy S4 or the Galaxy Note 2? There are advantages to both the Galaxy S4 or the Note 2, it all boils down to what your needs are such as screen size, battery life, and more.

For years, Samsung has been behind the curve when it comes to fast charging. Up to the Galaxy S10, most of their phones used the very slow Adaptive Fast Charging system. Whether it was the Galaxy Note 7 fiasco or some other reason, Samsung has been reluctant to push the charging envelope. Until now.

Mobile augmented reality pioneer Blippar has now completed its fall from hopeful AR startup to the immersive computing history books.

Welcome back, my hacker novitiates! Often, to hack a website, we need to connect to and exploit a particular object within said website. It might be an admin panel or a subdirectory that is vulnerable to attack. The key, of course, is to find these objects, as they may be hidden.

This is my first tutorial on this website. So, if you think anything to be wrong, just place it in the comments.

All of my hacks up to this point have been operating system hacks. In other words, we have exploited a vulnerability usually in an operating system service (SMB, RPC, etc.) that all allow us to install a command shell or other code in the target system.

I don't know about you, but I like to listen to music throughout the day. As I am writing articles or doing some cardio at the gym, I go through my playlist, only stopping the music in situations where I have to. And ever since I switched to the Samsung Galaxy S10+, this has gotten even easier to do.

MyFitnessPal has become extremely popular thanks to features that help users keep themselves accountable and stay motivated as they eat healthier and lose weight. While the application does a great job of reminding you to log the food you eat in order to keep track of your calories, there is one incredibly useful feature that doesn't get much attention.

Christmas has arrived early for ARCore app developers, as Google just unwrapped a few iterative improvements to the augmented reality toolkit in version 1.6.

While iOS 12 is arguably the best iteration of Apple's mobile operating system yet, one major fault so far is security. On Sept. 26, Videosdebarraquito discovered a passcode bypass that gave access to contacts and photos from the lock screen. Apple has since patched that security flaw, but Videosdebarraquito has discovered a new one that affects all iPhones running iOS 12.1 and 12.1.1 beta.

The crime procedural show is the perhaps the most direct path to the average TV viewer's heart. Could the same hold true for augmented reality games?

Epic Games just released update v3.4 for Fortnite Battle Royale on all four platforms. This new version brings a number of UI changes, performance improvements, and bug fixes, but the addition that will get the most players excited is a new weapon: the Guided Missile.

A recent update to Facebook's News Feed could significantly broaden its reach when it comes to delivering augmented reality content.

You can pinch yourself, but you're not dreaming. Sprint is actually offering a year of (mostly) free, unlimited service for anyone who switches to the carrier. The only stipulation is that you must bring your phone with you, and it has to be one of the 27 eligible devices.

Welcome back, my greenhorn hackers! In many cases when a computer, phone, or mobile device is seized for evidence, the system will have graphic images that might be used as evidence. Obviously, in some cases these graphic images may be the evidence such as in child pornography cases. In other situations, the graphic images may tell us something about where and when the suspect was somewhere specific.

Just last month, Microsoft announced plans to take away a huge chunk of storage from the free tier of their OneDrive cloud service, and users are understandably quite upset. At the same time, they reneged on an offer to give Office365 users unlimited OneDrive storage, and instead, will only be offering 1 TB of storage.

For a photo- and video-sharing app based around privacy, Snapchat sure has a lot of security holes floating around. At one time, you were able to take screenshots of Snapchats in iOS 7 without the sender knowing, which is something that you can still do on rooted Android devices.

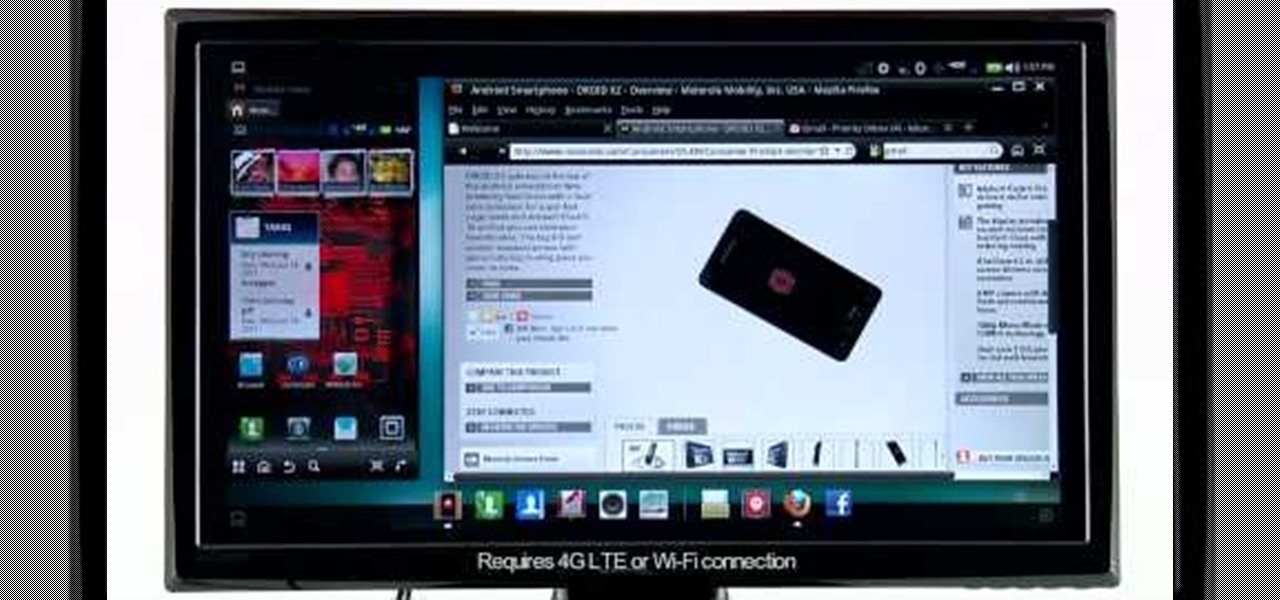
This four part segment from Motorola provides a ton of information and serves as a guide on Webtop for the Droid Bionic.

In this video tutorial, anyone who owns a Droid smartphone can learn how to better navigate their home screen. With this Droid phone tips, you'll be able to maximize your time and create shortcuts to your most used applications. The Droid's home screen in much like a computer's desktop; putting an icon on one of your Droid home screens allows you quick access to a program or app. There are numerous Android phones, but this video focuses on the "Droid" versions, but you may need to play around...

It's a timeless doggie no-no, and one that has been paradied in numerous dog scenes in movies: A plate of delicious fried, steaming food is left by the owner on the table. The owner then leaves for a brief moment. His dog, smelling the delicious goodness, seizes the moment and quickly jumps up, snatches a piece of chicken, and devours it under the table.

Pixel Perfect is the "perfect" show to help you with your Photoshop skills. Be amazed and learn as master digital artist Bert Monroy takes a stylus and a digital pad and treats it as Monet and Picasso do with oil and canvas. Learn the tips and tricks you need to whip those digital pictures into shape with Adobe Photoshop and Illustrator. In this episode, Ben shows you how to build an Egyptian Pharaoh's room in Photoshop.

Check out this strength trick from Revision3, Brian Brushwood and Scam School. We're back with another dirty trick, designed to teach you how to FAKE your way into (almost) duplicating the feats of the world's strongest men.

Ipad is a revolutionary device from Apple with some amazing features. One of the major functions of Ipad is to serve as a E-book reader. Apple provides an application called Ibooks using which you can read ebooks on your device. You can also browse and purchase new ebooks using this applications. Launch Ibooks from your applications menu and it will take you to the collection of books that you already have on your device. Click the store button to visit the books store. From the store you can...

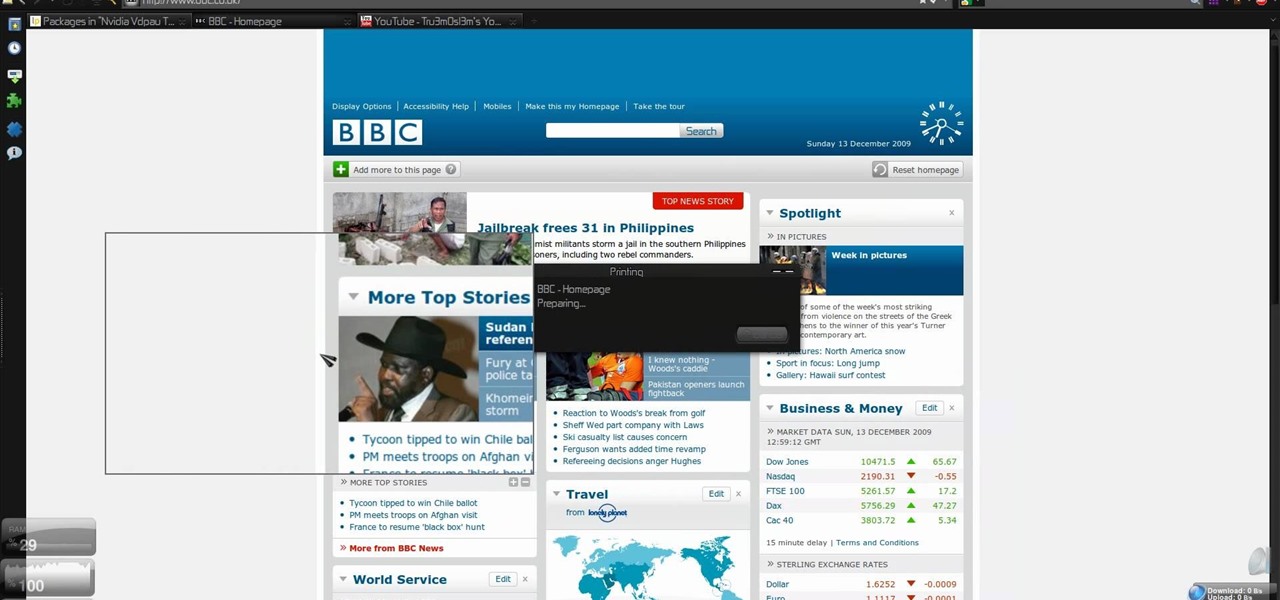
There's plenty of reasons why one would want to convert a webpage to a PDF document. And there's numerous ways on how one can convert that web page (HTML) into a PDF file. Check out this video tutorial on how to convert webpage HTML to PDF on Ubuntu Linux.