In this day and age, maintaining your privacy is a perpetual battle, and doing so with an internet-connected device like your smartphone is even more of a struggle. Every website you visit, every app you install, every message you send, and every call you make is a potential vulnerability that could expose you to prying eyes.

Apple's special September event just wrapped up with the company unveiling several new products, including the iPhone 6S, iPhone 6S Plus, iPad Pro, and the new Apple TV set-top box. In addition to hardware, Apple also discussed a couple of its latest software platforms, iOS 9 and watchOS 2. Check out everything that Apple unveiled below.

As our lives grow busier, we get secluded in our indoor activities, consuming all types of fatty junk food and what not. Obesity is a very obvious yet unfortunate outcome of our unhealthy living standards. With it comes the predictable rush towards efforts to lose weight. Consequently, we have designed hundreds if not thousands of ways to lose fat and grow slimmer. To ease out your choice of ways, here is a list of the best ways to lose stomach fat. Step 1: Don't Eat Sugar

While most of your iPhone's features are intuitive or well-covered across the web, there are some features hidden deep within iOS that you probably never even knew about. (These could also apply to an iPad or iPod touch.)

It seems like whenever someone sees my phone, they ask me two questions right off the bat; "What phone is that?" and "How did you get your Android to look like that?"

Welcome back, my tenderfoot hackers! In this series, we are exploring the myriad of ways to hack web applications. As you know, web applications are those apps that run the websites of everything from your next door neighbor, to the all-powerful financial institutions that run the world. Each of these applications is vulnerable to attack, but not all in the same way.

Whether you're just getting your first Android, or are already on your fifth annual cycle of picking up the latest flagship, there is always the question of what to do after booting up your device for the first time.

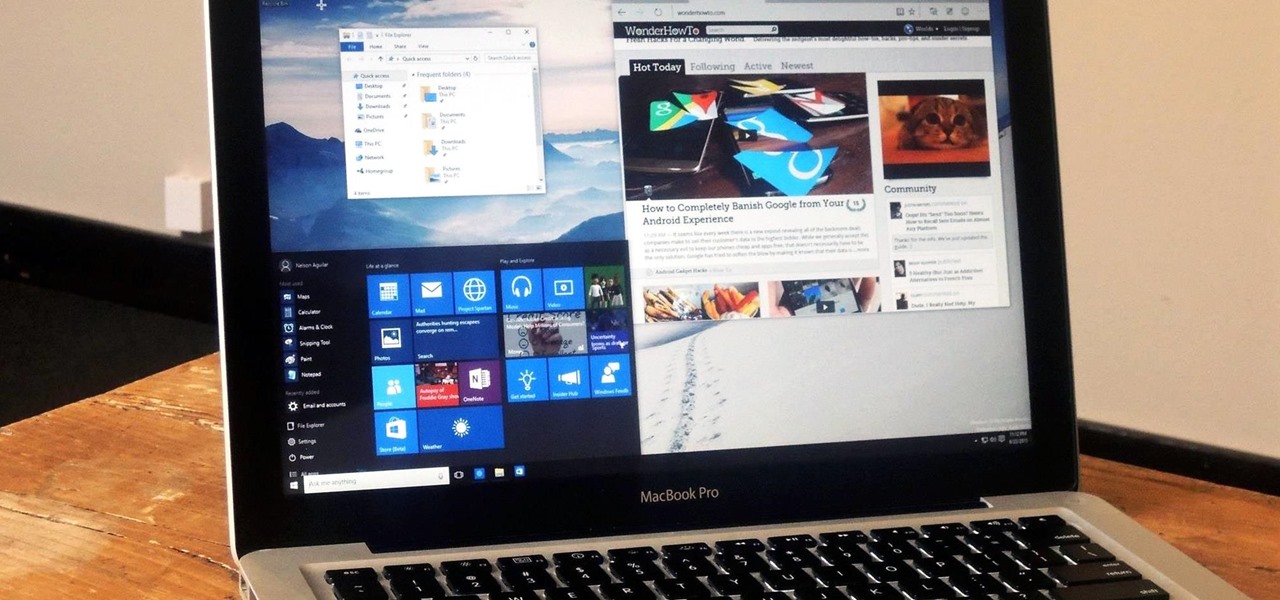
While Windows 10 is still a few weeks away from a public release, that doesn't mean you can't enjoy its brand new features right now. Anyone with an Insider Preview account can install Windows 10 on their computer. And that doesn't just go for those that own a Windows PC—Mac users can get their hands on Windows 10 as well.

All of Apple's products are praised for being extremely easy to use. So much so, that your grandma can pick one up and be a "pro" within a few hours. However, this isn't necessarily a good thing for us real power users who want more granular control of our devices.

Both the Galaxy S6 and S6 Edge have had root methods available to them before the phones were even released, but the problem with these existing root methods is that they would trip the KNOX counter on your device.

In my last guide, I showed how you could crack the combination of any Master Lock combination padlock in 8 tries or less using my online calculator. Now, as promised, I'll be showing you how I devised the attack, which is based off the well-known technique that reduces the 64,000 possible combinations of a Master Lock down to just 100. Here, I will be drilling open a Master combo lock to show you how the insides work.

Desktop users have taken advantage of dual-booting operating systems for decades now. If your core system software is lacking in any regard, dual-booting a secondary OS can give you access to those features that you're missing out on.

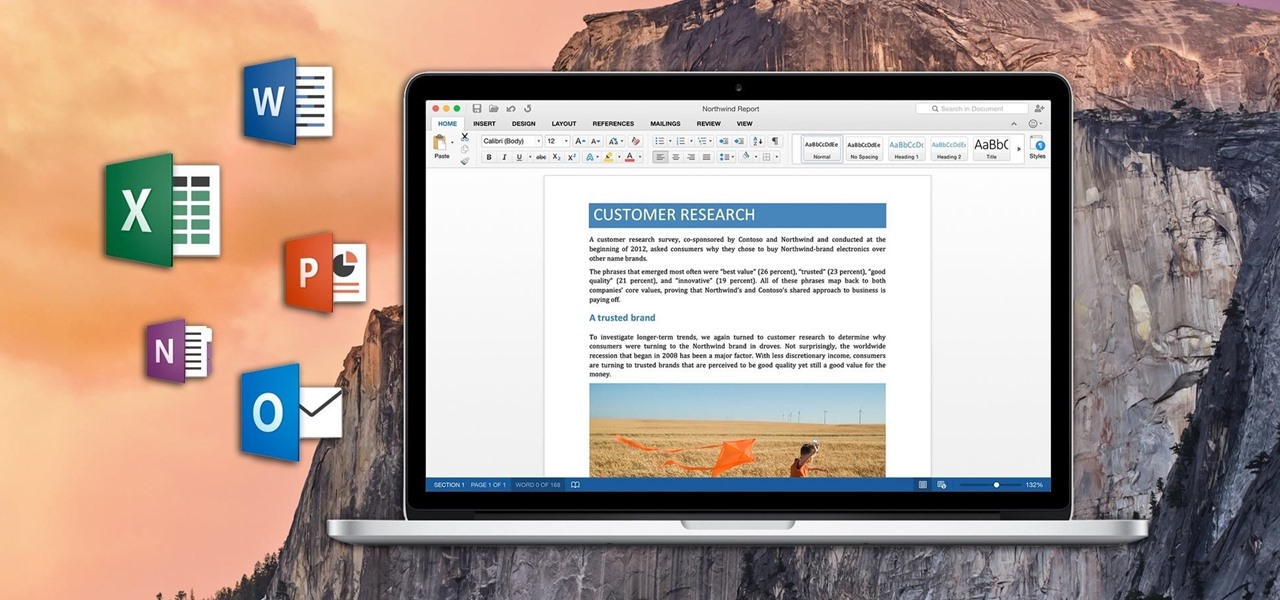
If you've ever attended school or held a job, you're probably well familiar with Microsoft Office, whether you used it or not. It's the most popular office suite available, and has been for some time. Apple does have its own suite of productivity apps (iWork), but Microsoft Office has always been the industry leader for word documents, spreadsheets, and presentations.

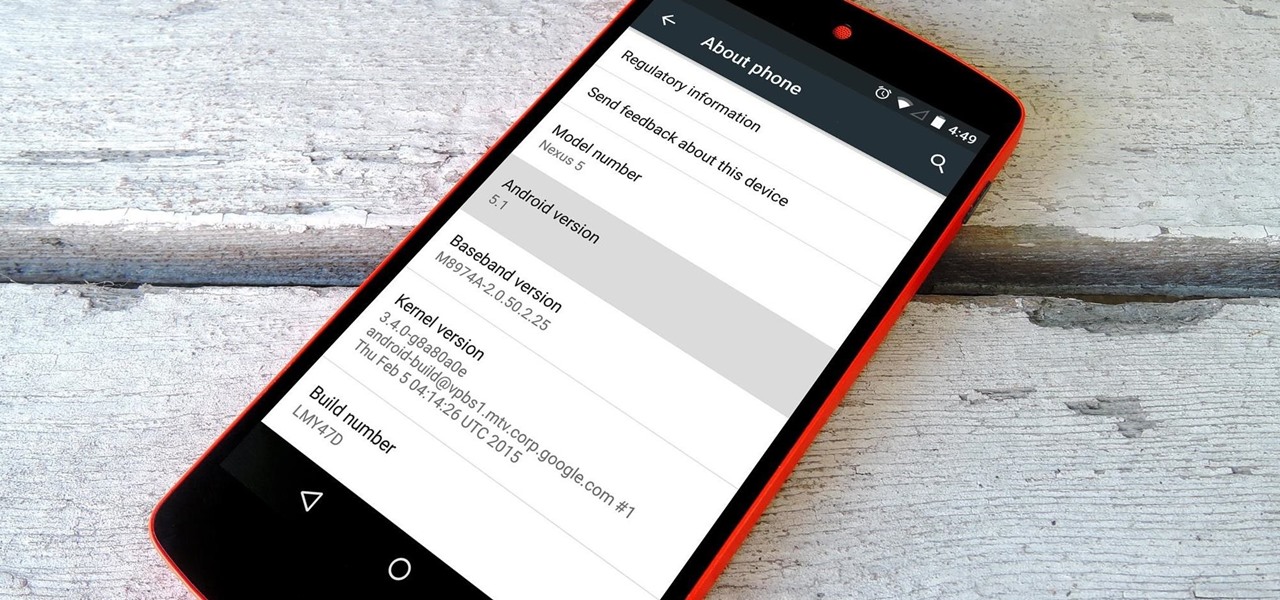
Google inconspicuously announced an Android update yesterday, and while it's not quite the overhaul that the initial Lollipop release was, version 5.1 brings plenty of bug fixes and new features.

Your waffle maker might just be the most underutilized tool in your kitchen. This one appliance can make bacon, eggs, hash browns, cupcakes, falafel, mac and cheese, and cinnamon rolls much more quickly and with less mess than traditional methods. Plus, the results all come out waffle-shaped—what's not to love?

Welcome back, my hacker novitiates! Every so often, a MAJOR vulnerability appears that makes millions of systems vulnerable to attack. The most recent, named Shellshock, basically leaves every Mac OS X, Linux, and UNIX system on the planet vulnerable. As nearly two-thirds of all web servers on planet Earth run one of these operating systems (primarily Linux), that's a whole lot of systems out there waiting to be harvested.

As the largest wireless service providers in the United States, AT&T and Verizon Wireless carry some serious clout. Sadly, they use some of this power to heavily modify the Android phones that they offer.

"The best season for food is the worst season for cooking." These words, spoken by food blogger Dave Klopfenstein of Dave's Kitchen, couldn't be more true.

Cold brewing tea and coffee are all the rage, and for good reason: they're idiot-proof. I, personally, am a total dunce at brewing coffee. It either ends up strong enough to peel paint from a car or so weak that you can see through it. Meanwhile, I have friends who inevitably brew green tea to the point where it's painful to drink it.

Welcome back, my aspiring hackers! In recent tutorials, I have made reference to the name and location of the Linux devices in the file system, such as sda (first SATA or SCSI drive). Specifically, I have mentioned the way that Linux designates hard drives when making an image of a hard drive for forensic purposes.

The long rumored and recently leaked Amazon phone has finally been unveiled, and in the interest of branding, continues down the Fire line—the Amazon Fire Phone. You can check out the full reveal here (warning: it's long), but I'll take you through all the features that sets this device apart from the rest. Before we get into that though, let's check out the specs:

When Apple recently unveiled iOS 8, many of the newly-added features in their mobile OS seemed eerily familiar to Android users. This is probably because the vast majority of these new features have been available in Android for quite some time.

Welcome back, my newbie hackers! Recently, I "upgraded" to Kali as my hacking platform, despite my preference for BackTrack. I did this reluctantly, primarily because new readers here could no longer download BackTrack from their site. I want to point out here that we all must keep in mind that with any software—or for that matter, any product—that is newer is not necessarily better.

Welcome back, my fledgling hackers! Scripting skills are essential is ascending to the upper echelons of the hacker clique. Without scripting skills, you are dependent upon others to develop your tools. When others develop your tools, you will always be behind the curve in the battle against security admins.

Welcome back, my fledgling hackers! A short while ago, I did a tutorial on conducting passive OS fingerprinting with p0f. As you remember, p0f is different from other operating system fingerprinting tools as it does not send any packets to the target, instead it simply takes packets off the wire and examines them to determine the operating system that sent them.

The advent of a new Nexus phone begins with the bigwigs at Google partnering with a manufacturer, then selecting that manufacturer's flagship as the model for the new Nexus hardware.

You probably already know by now that a custom Android ROM can change your user experience and give you what feels like a new OS on your device, and there's no shortage of them out there to try out.

Welcome back, my neophyte hackers! There are innumerable ways to hack a system. We must not overlook any of the possibilities if we want to "own" the system. As systems become more and more secure, we need to be vigilant in our search for weaknesses. In this hack, we'll look at abusing the trust that a user innately has for software updates to install our own listener/rootkit on their system.

Old people are usually perceived as wise and enduring, whereas an old smartphone, like my iPhone 4, becomes the butt of a joke every time I take it out of my pocket. I mean, come on, it's not like I'm still rocking one of these... And if I was, I guarantee you wouldn't beat my score on Snake.

The integration of technology into automobiles is becoming more and more widespread each year. Tesla's Model S features a 17" display in the middle of the dash with navigation, music control, and even an Internet browser. Mercedes is working on incorporating Google Glass into their cars. Even Honda's 2014 Accord LX (their lowest trim level), boasts Pandora music streaming, Bluetooth connectivity, and a rearview camera and display.

YouTube is the third most popular website in the world, after Google and Facebook. Millions of subscriptions happen each day on YouTube, with over 800 million unique users visiting each month. In that timespan, roughly 4 billion hours of video are watched, with 72 hours of video uploaded every single minute.

Microsoft's first venture into the tablet market, the Surface RT, combines many of the capabilities of a normal Windows 8 laptop into a super compact tablet, whose super-thin touch cover and kickstand can transform it into a functional mini-laptop, small and light enough to go anywhere you want. But like most tablets, the Surface comes with a rather limited amount of storage space. The tablet comes in either 32 GB or 64 GB, but we all know that's not the actual amount of storage space you can...

The director of 100 Musicians and Nurse/Fighter/Boy talked with us about old school filmmaking Charles Officer has directed shorts, music videos for K’naan, and the features Nurse/Fighter/Boy and Mighty Jerome, a documentary about Canadian track star Harry Jerome. His new short 100 Musicians, which screens Monday as part of Short Cuts Canada, is a small ode to civic optimism, concerning itself with a lovers’ argument over who exactly misheard a radio DJ reporting the plans of Toronto’s much m...

There's something special about Laika Inc.'s Paranorman... Hey! Did you love Coraline? Are you interested at all in stop-motion animation? Well, watch this feature on Laika Inc.’s new film, Paranorman.

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

Okay, so you've decided to take the plunge, and participate in our Love. Earn program with a how-to article. But, for whatever reason, your article keeps getting rejected by WonderHowTo, and you're wondering, well, where's the love?

In these martial arts training videos, learn the basic principles behind Jeet Kune Do, using no way as way, and having no limitation as limitation. Our teacher will guide you in some beginning movements and techniques, including how to do a simple ready stance and how to combine kicks and punches for a powerful advantage in combat.

Tech tends to move forward without looking back, but that doesn't mean new is always better. One feature that dominated mobile phones in the late '90s had made a comeback thanks to Apple, and you can take advantage of it on your iPhone when making calls.

Lidar, a technology first used by meteorologists and aerospace engineers and then adopted in self-driving vehicles, has slowly crept into consumer electronics over the last five years. If you have a Pro model iPhone or iPad, there's a good chance it has a lidar sensor, and you're likely using it whether you know it or not.