Checking the weather ranks among the most mundane but essential tasks you can do on your smartphone. Thankfully, both the iOS App Store and Google Play are loaded with weather apps that add some much needed spice to this daily routine, giving you less of a reason to be caught unaware.

Welcome back, my hacker novitiates! In the previous two posts in this series, we looked at the basics of buffer overflows. In this post, we will look at one technique for finding buffer overflows. We will try to send random, oversized, and invalid data at a variable to see whether we can make it crash or overflow. This process is known as fuzzing. It is often the first step to developing an exploit, as we need to find some variable that is susceptible to overflowing.

Welcome back, my tenderfoot hackers! As hackers, we often are required to get past antivirus (AV) software or other security measures. To do so effectively, we need to have some understanding of how AV software works. In this tutorial, we will take a cursory view of how AV software works so that you can better strategize on how to evade detection by it.

Welcome to the sequel to the latest post on writing 64 bit shellcode! This tutorial will assume that you are aware of everything mentioned in the last one, as I will try to make this tutorial void of formalities and straight to the point! If you have not read the last one, I suggest doing so unless you are familiar with basic assembly programming and system calls. This is by no means rocket science, so therefore I will simply repeat my TL;DR from last time before we get started, so that the a...

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.

The ability to make a meal for yourself used to be one of those life skills you had to learn or otherwise you would starve, but the rise of convenience foods, takeout, and other aspects of modern living have made it entirely possible to be a grown person and not know what to do in the kitchen.

I am an English major physically allergic to all algebraic formulas, so you're unlikely to get any help from me when it comes to solving any expressions. But in the glorious technological age we live in, there are plenty of apps that actually make math and problem solving fun, even a little bit addictive.

It seems like every day now that we see a new headline on a cyber security breach. These headlines usually involve millions of records being stolen from some large financial institution or retailer. What doesn't reach the headlines are the many individual breaches that happen millions of times a day, all over the world.

Coffee! It's so amazing that J.S. Bach wrote a comic opera about caffeine addiction. Meanwhile, more than half of Americans 18 years or older start their day with a cup of the hot stuff. Most of us take coffee for granted, but it's a bean that can surprise you. Read on to understand more about coffee and how to take advantage of all that it offers.

Staying healthy is a progressive challenge we all face throughout our lives, and figuring out just how to do that can be a challenge when it's not your job. For doctors, however, it is. Here's how they keep themselves healthy day to day.

There's an ongoing debate about whether or not it's safe or even desirable to rinse meat before you cook it. Many fall into the anti-rinsing camp, saying that it's not effective at dislodging bacteria, especially on poultry, as we've discussed before. Meanwhile, some argue that rinsing certain meats, like bacon, could be beneficial since it possibly prevents it from shrinking.

Eggs are incredibly important to cooks, and not just because they're tasty and a complete protein (many erratic genius/artist types make a point of eating an egg or two for breakfast). Yes, they are great when perfectly poached, scrambled, hard-boiled, and even scram-boiled, but they serve literally dozens of functions when used in recipes, especially baked goods.

Canvas fingerprinting is the web's trickiest privacy threat, but it's not impossible to stop. With all the media attention it's gotten lately, it's time we lay out exactly how to detect and prevent this invasive tracking technique.

Two slices of whole-wheat toast with lots of butter. Two eggs, poached to a firm yet custardy texture. The yolks should absolutely not be hard-cooked and the whites should be tender, not rubbery. That's my idea of the perfect breakfast.

For the novice cook, fungi can be weird because, well, they're fungi. However, if you've been afraid to get acquainted with mushrooms, you've been missing out. Vegetarians love mushrooms and with good reason.

Welcome back, my neophyte hackers! I have already done a few tutorials on password cracking, including ones for Linux and Windows, WEP and WPA2, and even online passwords using THC Hydra. Now, I thought it might be worthwhile to begin a series on password cracking in general. Password cracking is both an art and a science, and I hope to show you the many ways and subtleties involved.

Just the fact that you own an Android device means you're privy to an entire world of third-party development. Many of the mods you'll see here on Gadget Hacks can be performed fresh out of the box, but with root and Xposed, the list grows longer. But to truly be able to take advantage of all that Android's massive development community has to offer, you'll need to have a custom recovery installed.

Chances are that you've been using your microwave just to nuke leftovers, but they can do so much more than heat up last night's dinner—microwaves can help you peel garlic more quickly, get more juice out of lemons, disinfect your kitchen, dry out herbs, give beauty products new life, cause exciting explosions, and even arc weld.

There's a 2800mAh battery powering the Samsung Galaxy S5, but even it's no match for the constant day-to-day torture you put it through. Taking photos, watching videos, and playing games can make your fully charged S5 powerless in no time.

As a species, our cells are designed to use sugar for energy. Is it any wonder that as humans evolved, we grew to love the taste of sugar?

Welcome back, my neophyte hackers! Have you ever had a neighbor that you're certain is up to no good? Maybe you've seen him moving packages in and out at all hours of the night? Maybe you've seen people go into his home and never come out? He seems like a creep and sometimes you hear strange sounds coming from his home? You know he's up to no good, but you aren't sure what it is exactly.

Welcome back, my hacker apprentices! Metasploit framework is an incredible hacking and pentesting tool that every hacker worth their salt should be conversant and capable on.

Welcome back, my budding hackers! One of the most time-consuming, but necessary, activities in hacking is reconnaissance. Before we can hack a system, we need to know what operating system it's running, what ports are open, what services are running, and hopefully, what applications are installed and running.

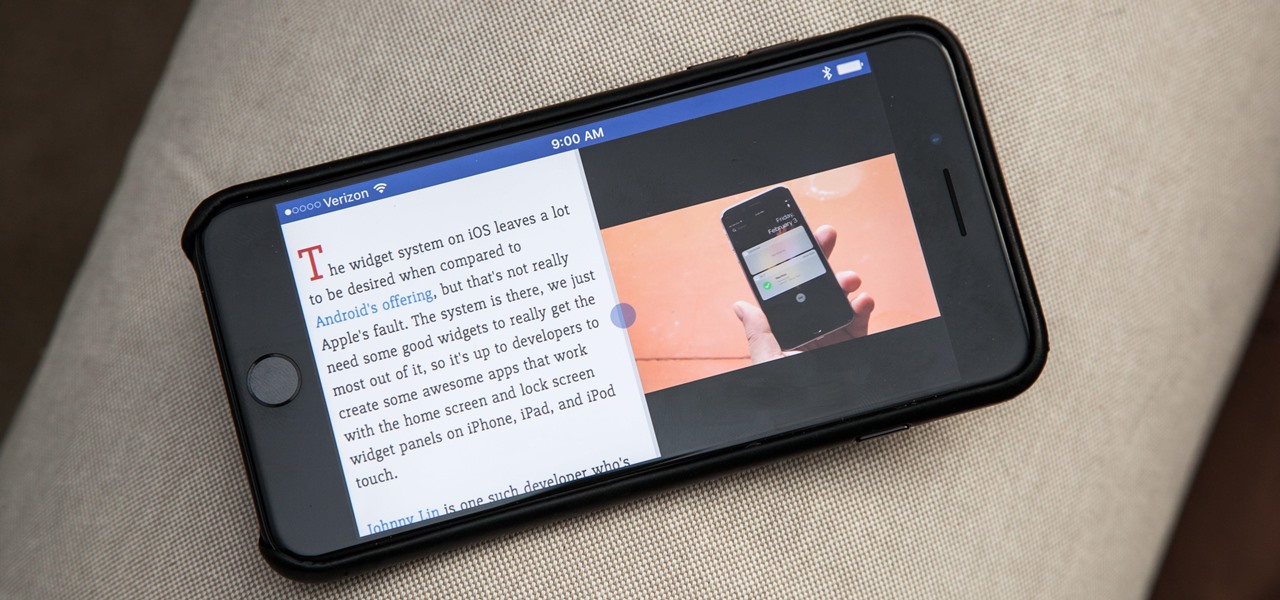
The iPhone has come a long way in its ten-year lifespan, but one thing still missing from the core user experience is native split-screen support. Sure, the displays on iPhones aren't nearly as large as an iPad's screen — which does offer "Split View" mode out of the box — but the iPhone 6 Plus, 6s Plus, and 7 Plus are definitely big enough to use two apps at the same time.

In this article, I will be showing you how to make a crude form of aspirin from the bark of a willow tree. It is a great remedy for headaches, hangovers, and other minor pain. The use of the willow tree as a mild pain reliever goes back to the Native Americans, who used it in much the same way that I do.

It's a controversial headline, I know, but bear with me and I'll explain in due course. Disclaimer: I was once a child, and I played lots of video games. I didn't look anything like this child.

When you're a writer with work published across various online platforms, building a portfolio of your work can be pretty time-consuming. That's where Authory comes in.

Numerous potential exploits are found for every operating system each month, and Android is no exception. Trouble is, lots of Android devices don't receive timely updates — but many are now getting regular monthly security patches to at least shore up these vulnerabilities.

The race for the future of AR wearables gained steam this week with several pivotal developments. First, Apple, the subject of numerous reports and rumors regarding its purported AR headset, is reportedly eyeing an in-person unveiling of the device for later this year, rather than introduce it at its upcoming virtual Worldwide Developers Conference, which would usually be as good a time as any to make a big AR hardware announcement.

Just as the augmented reality industry grows, so too does the segment dedicated to creating experiences for the tools becoming available.

Google's version of Android is best described as AOSP with extra features. But while the Pixel's UI is rightfully praised for its simplicity, those "extra features" aren't as numerous as they are on other OEM skins like Samsung's One UI. Case in point, there's no real system-wide audio EQ.

If you upgrade to an iPhone 12, 12 mini, 12 Pro, or 12 Pro Max, you can take advantage of super-fast 5G speeds, but which 5G network are you actually getting and is it better than the others? Depending on your carrier, you may see 5G, 5G+, 5G UW, or 5G E in the status bar next to the signal strength, and there's a pretty big difference between them.

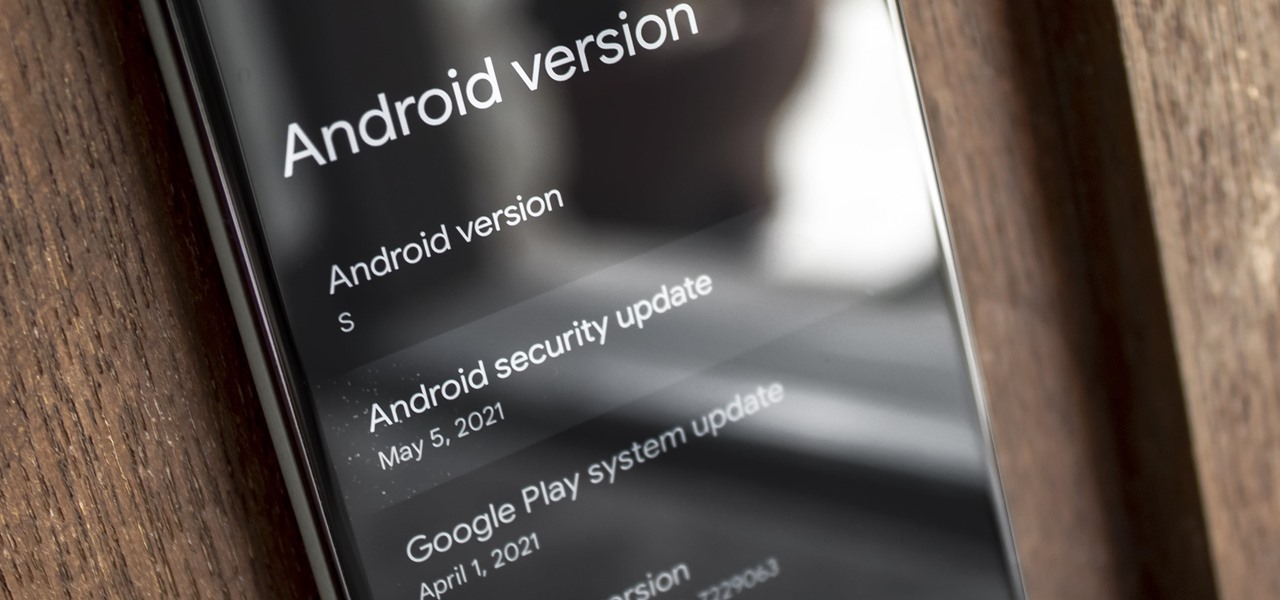
Android 11 is here. Prior to Google dropping the naming scheme, this would have been a dessert with an R name (maybe Rice Krispies Treat or Red Velvet Cake) — but nope, just plain ol' Android 11. And after months of betas and a global pandemic, it finally debuted a little over a year after Android 10.

Smartphones are more like computers than actual telephones. Unfortunately, thieves, hackers, and other bad actors know this and are always looking to make money off your personal data. Thankfully, your Galaxy S20, S20+, or S20 Ultra has tools to combat these threats — as long as you know where to look.

Thanks to numerous smartwatch deals this holiday season, many people are receiving their first one. But what exactly can they do? In regards to fitness, quite a lot. With a growing list of sensors and software updates, these small devices can be the very thing you need to ultimately reach your fitness goals.

In the case of Apple Watch v. Fitbit, the winner comes down to the judge at hand. Apple currently offers two smartwatches — the Series 5 and the Series 3 — while Fitbit offers three models — the Fitbit Versa 2, Fitbit Ionic, and Fitbit Versa Lite. Whatever your assumptions about these devices are, throw them out the window, as each has something unique to bring to the table.

A good smartphone can be the perfect workout companion. You have music for motivation, videos for pushing through boring cardio sessions, GPS to keep you on course, and even an array of sensors for gathering data about your workout. But not all phones are created equal when it comes to helping you stay fit.

Cases and stickers are always great, but they aren't the only way to customize an iPhone. The software on your device is full of customization options, from a better-looking home screen and cooler lock screen wallpapers to app icon changes and a system-wide dark mode. There's literally over 100 ways to make iOS on your iPhone genuinely unique, some of which are hiding in plain sight.

Trying to figure out which music streaming service to subscribe to can be a difficult task when the playing field is so crowded. Each has its benefits, as well as downsides, so finding the right one for your needs and wants can take a lot of overwhelming research. But we've done all the research for you to help you find the best music subscription your money can buy.

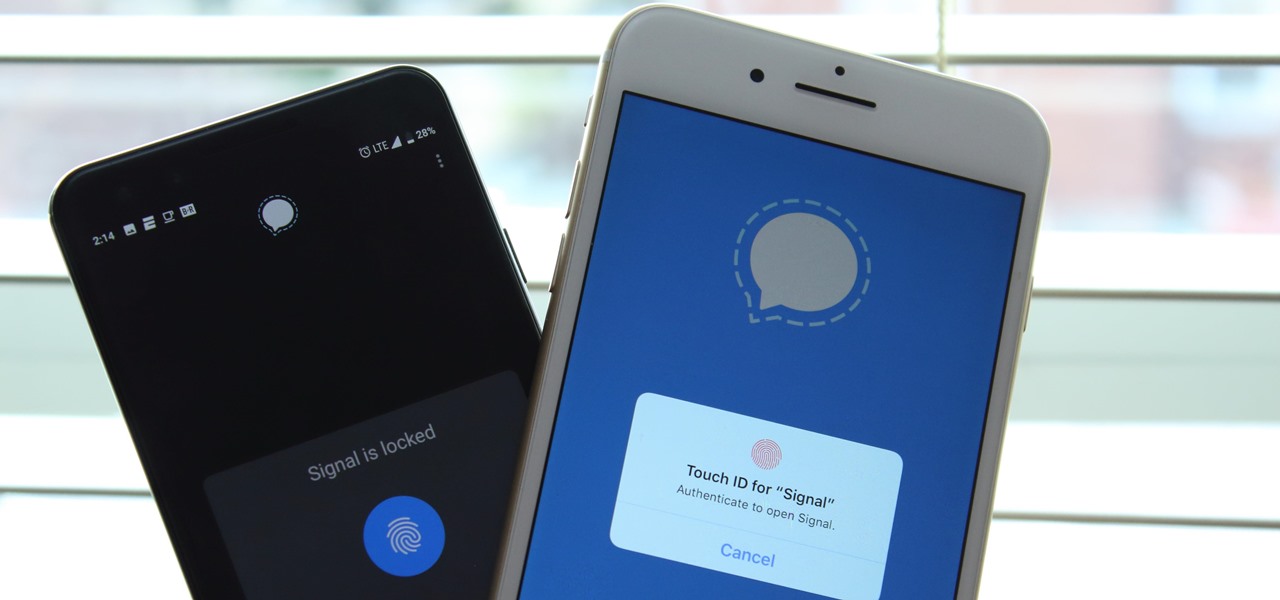
Signal is one of the best end-to-end encrypted messengers on the market. It offers robust security, keeps minimal information about its users, and is free to use. Switching to it as your main messenger can be a bit daunting, so to help, we created a guide to walk you through the process.