Backdooring a powered-off MacBook is easy when a few minutes of physical access is allowed. That attack works well if the hacker also shares a Wi-Fi network with the victim, but this time, I'll show how to remotely establish a connection to the backdoored MacBook as it moves between different Wi-Fi networks.

In a previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when a Microsoft Word document is opened. The biggest challenge of this attack is that it requires getting the user to agree to a pop-up prompt. Fortunately, since I posted that article, many new obfuscation techniques have been discovered to make this easier. Today, we explore and combine some of them to make the ultimate hidden DDE attack.

Google's personal messaging service Allo could reveal your search history and other private information to friends if the Google Assistant bot is called upon in chats, according to a story from Re/code.

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.

This tutorial is one technique to use the full functionality of your Pi. The small size makes it ideal for inside hacks, but still has the capabilities of a average desktop or computer. I should mention that a tutorial that OTW has done, but I'm gonna take it a step further. OTW made a brilliant article, but only touched on the surface of the possibilities. I hope this article will both show you many the possibilities and also allow you to start causing havoc, but I'm planning on making this ...

All across the web, you'll find guides on setting up various apps and mods for your Android device—but while these are certainly useful, they all seem to be working under the assumption that the reader has a certain level of knowledge about Android. For someone that's just getting started with the world's most popular mobile operating system, the basics of Android simply aren't covered as well as they should be.

One of the hottest trends in the food world right now is "spiralized" vegetables. I will confess that I am a bit suspicious of any diet or food fad that eliminates an entire food group for anything other than physician-ordered health reasons, but something really good has followed in the wake of the Atkins/paleo/gluten-free movements.

I have been on Null Byte for a long time, a very long time and. I havent always had an account here, ive like many of you also have, been looking and decided to make a profile to contribute.
Basically, this article is a true life experience writing from the introspective mind of the writer and do share more knowledge on how to deal with introvert lifestyle.

In this article, we will build a parallel password cracker using the techniques explained in the previous part. As SHA-512 is the digest function that Kali (and most modern Linux distributions) use to store our passwords, we will make a SHA-512 password cracker.

Hello again, ***UPDATE: Adding links to the other Two articles****

As many of you know, processor's clock frequency improvement got stuck in about 2003, causing the origin of multicore CPU (and other technologies). In this article I'll introduce you on how to run code simultaneously in various processors (I suppose that all of you have a multicore CPU). When you write code without any parallel directive, it only executes in one CPU at the same time (see it below). OpenMP make simple to work with various cores (if not with all of them) , without so much heada...

Welcome back! In the last iteration of how to train your python, we covered loops, today we'll be covering something that I wish I had learned about much earlier in my scripting career, errors. We all run into them, and they can be frustrating, but there is also a silver lining to them. Today, we'll be discussing why some errors are unavoidable, and what we can do when we run into them. Also, this article will be more of a concept and less of writing actual code, but the information is equall...

It seems like every day now that we see a new headline on a cyber security breach. These headlines usually involve millions of records being stolen from some large financial institution or retailer. What doesn't reach the headlines are the many individual breaches that happen millions of times a day, all over the world.

There are a lot of techniques out there for how to cook the perfect steak, from flipping it multiple times to applying a spice rub or dry brine to aging the beef. But it turns out that there's a super-easy way to make a great steak at home, and all you need is a good cast-iron skillet and some salt.

So you've decided to transform your drab backyard into a Japanese Zen garden. You've made the right choice. Yes, tire swings and crab grass can slowly kill the soul. That being said, a bit of planning lies ahead. This article offers a list of How To tips, culled from the Landscape Network and other professional Japanese style landscapers, for planning an effective Japanese style landscape in your home. Step 1: Research.

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

If I were to lose access to the entire internet for the rest of my life, one of the websites I would miss the most would have to be Wikipedia. Wikipedia has ended countless arguments, informed me of how old and single some of my favorite actresses are, and helped me brush up on thousands of historical topics.

Life has many perils: parasites, predators, and pitfalls. Eventually, any organism will succumb, and if that organism has not first passed on its genes, those genes will face extinction.

In this article, I'll be continuing my series on microcontrollers. If you haven't read part one, I'd recommend heading over there and reading it!

"You can never know too much" is a saying you hear all the time. Funny thing is, I have no idea where it originated, and neither do most of the people who continually say it. Nevertheless, it's a statement that very few would argue with.

A Steampunk's Guide to Sex was the subject of a recent successful Kickstarter campaign, and I now hold the finished book in my hands. As such, I can say (mostly) unreservedly that you should buy this book. Allow me to tell you why, before I get into the nitty-gritty about the book itself. Sex is something of an odd topic in America because it's perfectly legal, and yet taboo. Unlike things that are illegal and not taboo, like drug use, murder, theft, etc. What this means is that children can ...

In evolutionary times, we were far more likely to die from starvation than from diseases related to obesity. In those times, when food was available, it was best to stuff oneself.

If you've ever logged on to the popular music application Pandora, your password is saved onto that computer in the local storage...for good.

Traps are great, but sometimes you don't want to kill anyone, you just want to know when they're around. When that's the case, check out this handy alarm system that uses the power of doors! Doors, you say? Yes, doors! Some of you may already be familiar with how obnoxious doors can be in Minecraft, but if not, check out this video of it in action:

Most of the time, when I’m bored during math class, I play with my calculator to satisfy my boredom. Recently, I've discovered that when multiplying any number by 11, 111, or any number similar to it, that it has a pattern (though I guess everything in math has a pattern). I don't know if this technique is original, because I didn't read anything about this. It's just mere observation. If it’s a tried and true technique, let me know.

Sweating or leaving your feet damp after showers can lead to athlete's foot, a skin rash that targets damp, covered areas. Learn about treating athlete's foot from a doctor in this medical how-to video.

Volleyball has numerous unique rules. For example, volleyball is one of the only sports that does not allow throwing or catching the ball. Learn the rules of volleyball in this video tutorial.

Tennis is a great summer sport, which makes having a great forehand essential for any tennis player. Learn how to improve your forehand swing in this tennis video.

Tennis is a great summer sport, and a great backhand is essential to being a good tennis player. Learn how to improve your backhand swing in this video tennis tutorial.

Apple News. Facebook. Twitter. Reddit. LinkedIn. These are just a few of the apps you probably have on your iPhone or iPad that keep you up to date on today's events. Unfortunately, they can also cause information overload. But a new viral speed-reading tool thinks it can help you process your daily news more efficiently.

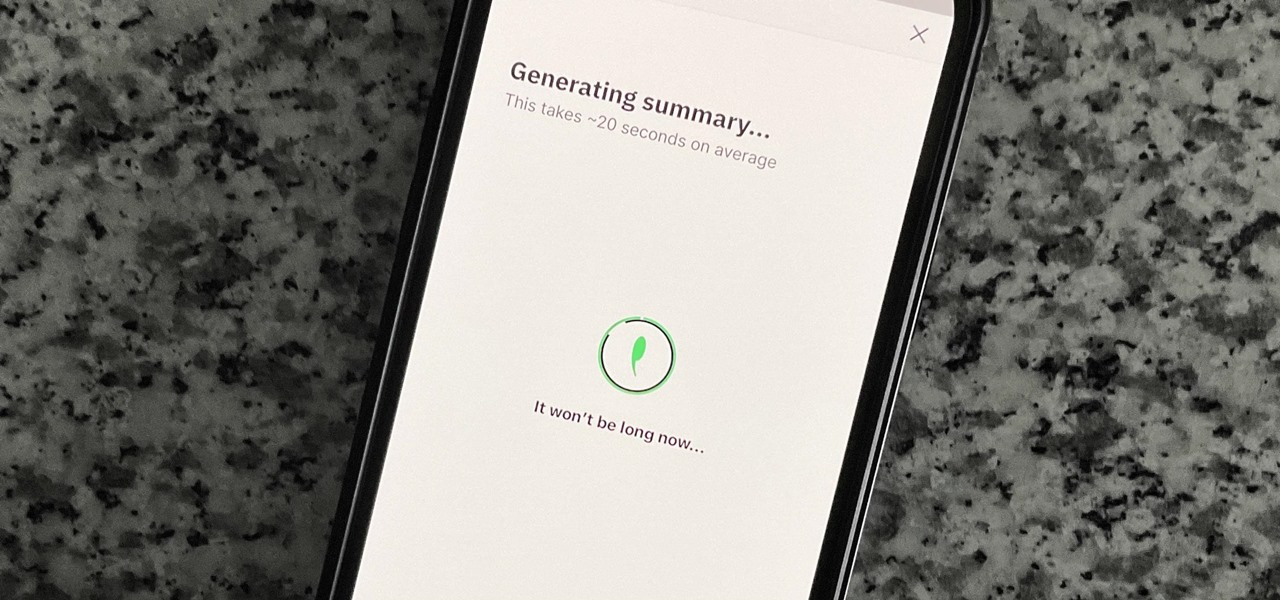
If you're like me, you don't have time to sit down and leisurely read an entire article from start to finish — but you still want to be informed throughout the day. Instead of just browsing the daily headlines, there's a free service that will summarize any article you throw at it, giving you a better idea of what's going on without committing to reading an entire article.

Procrastination is an ugly beast. At first, it seems so innocent to spend five minutes checking Reddit or Twitter. You'll get started on work right after. Next thing you know, it's 1 a.m. and that paper is due in seven hours. Before you start another YouTube video, know you don't have to be like Spongebob. You can be like me, taking control of your productivity with the right app.

With the release of the Pixel 2 XL and the iPhone X, smartphones have hit a new high not just in price, but also raw processing power. These new flagships not only cost more than twice as much as an Xbox One or PlayStation 4, they have also become almost as powerful as far as gaming goes. Because of this, a lot of games once reserved for consoles and PCs have made their way to our smartphones.

In this language tutorial, you will learn how to use the definite article in biblical Greek (Koine). This is a perfect lesson for those scholars wishing to study this ancient language of Greece. Watch this how to video and you will be speaking biblical Greek in no time.

There wouldn't be any chaos in the world without Benoit Mandelbort— chaos theory, that is. Mandelbrot, who just passed away at the age of 85, pioneered fractal geometry and greatly influenced chaos theory. He spent most of his life working in physics, biology and astronomy, and is best known for his Mandelbrot Set, a mathematical set of points in the complex plane (the boundary of which forms a fractal).

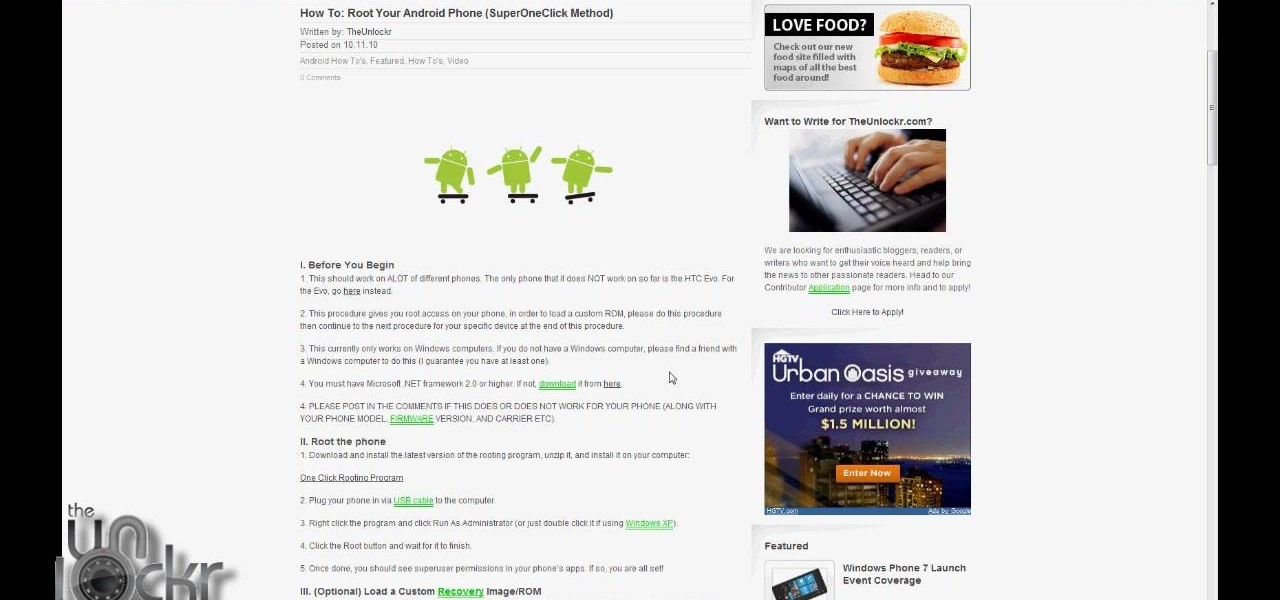
This is, by far, the easiest way to root your Android phone, and it's even got its own name— the "SuperOneClick" method. This is a universal technique that applies to most Android-based smartphones (minus the HTC Evo and T-Mobile G2/Vision). TheUnlockr shows you the secret behind rooting your Droid, so watch and learn. Anyone with an Android-enabled phone can do this.

Is your hatchet in need of a quick tuning? Doesn't quite get the job done anymore? It's time to sharpen it. This also applies to sharpening an axe.

Do you have a great article that you're really proud of, that was printed in the newspaper? Did something amazing happen, and you want to preserve the newspaper article about it? Newspaper is delicate, and can fall apart quite easily if not preserved properly. Check out this video to learn how to preserve a newspaper clipping.