The USB Rubber Ducky comes with two software components, the payload script to be deployed and the firmware which controls how the Ducky behaves and what kind of device it pretends to be. This firmware can be reflashed to allow for custom Ducky behaviors, such as mounting USB mass storage to copy files from any system the Duck is plugged into.
Winter is coming for Amazon. It looks like the company is having another go at the smartphone world with its release of new smartphones branded as "Ice".

All Galaxy S8 models apparently weren't created equal. According to numerous user reports, it appears that Snapdragon-powered Galaxy S8 variants are using an older flash storage standard than what Samsung was originally advertising.
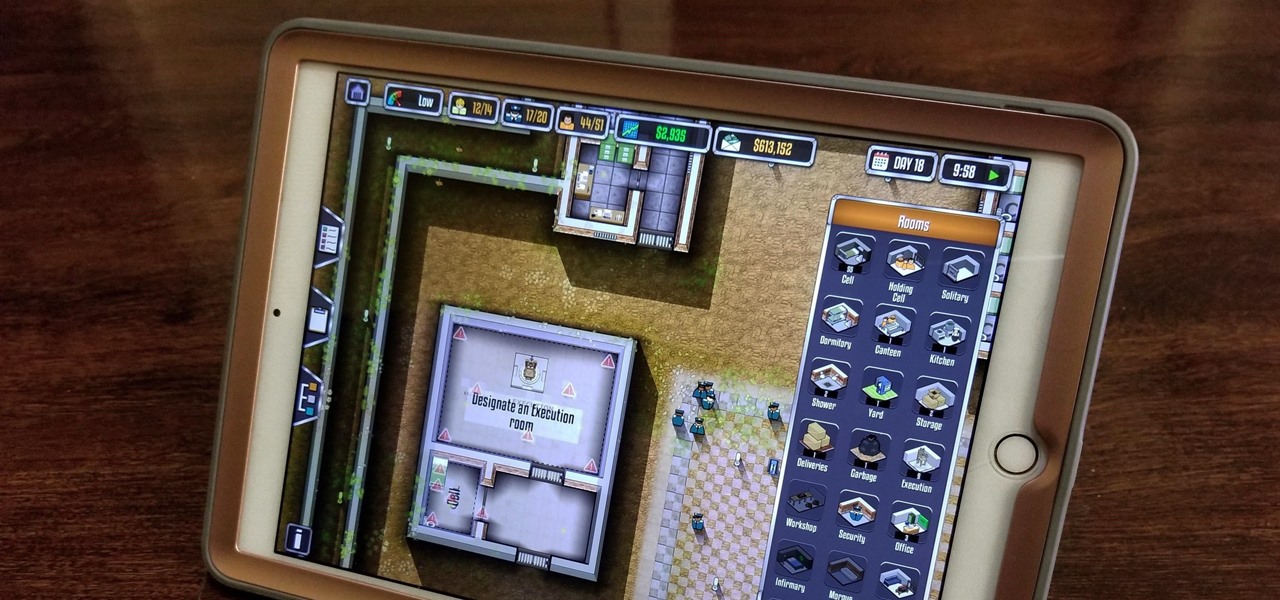
Prison Architect, the BAFTA winner for the Best Persistent Game in 2016, has finally soft launched on iOS. Originally a PC game, Prison Architect lets you build and maintain a maximum security prison. Comparable to running a small city, the game has you manage an ever-expanding correctional facility and contend not only with violent offenders and ever-present prospect of a chaotic riot, but also more mundane affairs like balancing the prison's budget and employee payroll. In addition to the s...

A 'superbug' fungus is currently running riot in the hospitals of New York and New Jersey. This outbreak of Candida auris has contributed to 17 deaths in NYC, according to recent reports.

Dynasty Warriors has finally been unleashed on the world of mobile gaming. The latest installment in the popular series is called Dynasty Warriors: Unleashed, and it sends you rampaging through armies using a variety of devastating attacks, all while collecting and upgrading over 80 unique characters from the Dynasty Warriors series. Each offer their own unique abilities, which lets you create the ideal team to take on the seemingly endless hordes coming your way with cold, cruel efficiency.

The Huawei Nexus 6P was released a little over a year ago, but despite doing moderately well in sales, the device has had more than its fair share of issues. When first released, there were numerous reception and memory management difficulties that left users extremely frustrated, though, those problems were solved with updates pushed by Google.

Koji is a culture made up of a certain fungus (mold) called Aspergillus oryzae, which has been used to ferment rice and soybeans in Japanese, Chinese, and Korean kitchens for centuries. Koji can actually have other involved fungi, but Aspergillus oryzae is the most common, and therefore the names can be used interchangeably. Its end purpose is to enhance the flavor of items like soy sauce, sake, and miso.

New Android versions have always been released on a fairly regular schedule—in late Fall, Google debuts a new Nexus device, while simultaneously publishing the next iteration of the world's leading mobile operating system. But things are different this year, as we now have numerous indications that Android Nougat could be released as early as August or September.

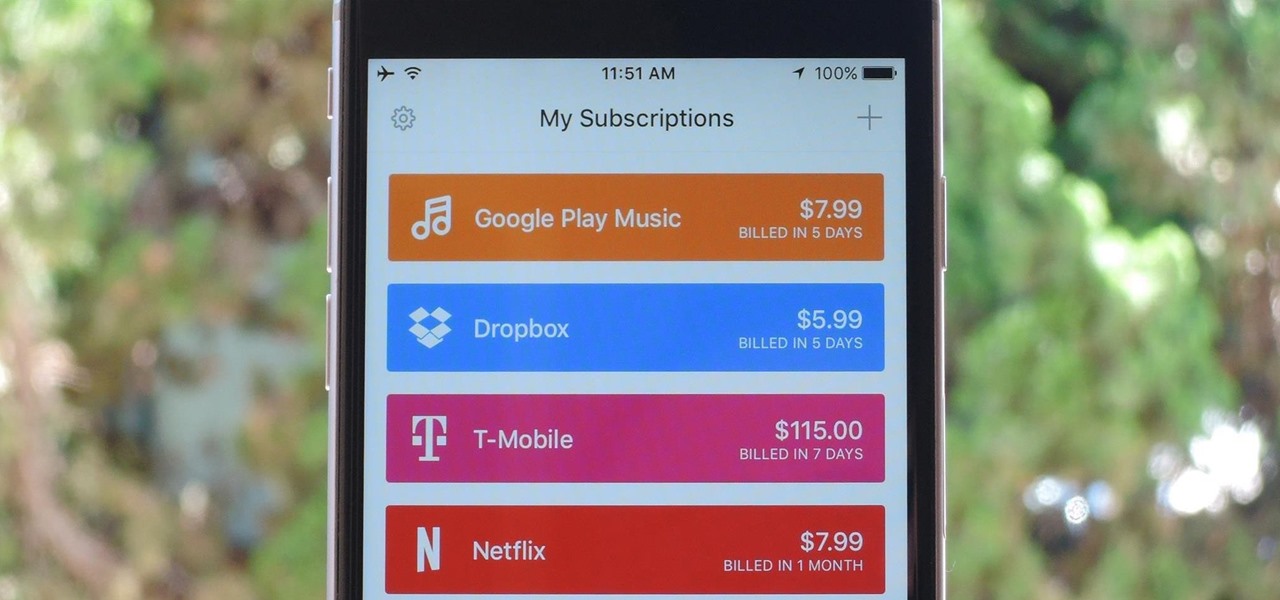
As the internet continues to become a bigger part of our day-to-day lives, we slowly but surely start to rack up a bunch of web-based subscriptions. These internet subscription services—Netflix, Hulu, and Amazon Prime, just to name a few—may seem innocuously cheap individually, but when combined, they actually comprise a significant portion of our monthly bills.

Welcome back, my budding hackers! In this series, I have been trying to familiarize you with the many features of the world's best framework for exploitation, hacking, and pentesting, Metasploit. There are so many features, and techniques for using those features, that few pentesters/hackers are aware of all of them.

Hello ladies and gentlemen, I'm back with another informative(hopefully) article for you all. Once again I would like to apologize for my absence for about a week or so. I have some stuff going on with my life and university and I haven't found enough time to make a fully in-depth article. In this article I'm going to walk you through one of the main networking protocols when it comes to communication across the Internet between programs, aka UDP(User Datagram Protocol).

Welcome back, my hacker novitiates! Often, to hack a website, we need to connect to and exploit a particular object within said website. It might be an admin panel or a subdirectory that is vulnerable to attack. The key, of course, is to find these objects, as they may be hidden.

Welcome back to another episode of Java Tutorials, In today's tutorial, we'll be learning about what methods are, proper syntax when writing Methods, and why they are beneficial in a program's code.

Welcome back! Sorry I've been gone for so long, but if anyone has been keeping up with these articles, you'll know that when I get quiet, something is cooking under the surface. In other words, I've been working on a project lately, so I haven't had much time!

I was fortunate enough to be visiting one of my college classmates in Columbus, GA last spring and saw two large bags of onions in his kitchen... but not like the ones you get at the grocery store. Two standing 50 lb. bags!

Simmering or poaching food is a total pain sometimes. The problems are numerous: a layer exposed to air often dries out and creates a gross skin that can ruin the texture of the sauce, the poaching liquid evaporates too quickly and causes the poached protein to burn, and so on.

Salad spinners are one of the more divisive kitchen tools out there. On one hand, they're incredibly easy, efficient, and useful. On the other hand, they're a single-use tool that takes up a lot of space.

Welcome back! Sorry for being so quiet, I've been rather busy with this project lately! Anyways, in the last iteration of how to train your python, we covered lists. Today we'll be introducing iteration and the two loops python has to offer, for and while. Also, we'll be covering a couple general use functions. So, let's get started!

In the last iteration of how to train your python, we covered the concept of control flow and covered the booleans associated with it. Today, we'll be putting those to use as we discuss how to use if, else, and how to make conditional statements. So, Let's get started!

In the last iteration of how to train your python, we covered basic string manipulation and how we can use it to better evaluate user input. So, today we'll be covering how to take user input. User input is very important to scripting. How can we do what the user says if we can't tell what the user wants? There are multiple ways to take input, we can give the user a prompt and take input from them directly, or we could use flags/switches, and take their input before the script is even execute...

Last time in how to train you python, we covered the basics of variables and output. While we were covering variables, we talked briefly about strings. "String" is just a fancier way of saying "Word". A string is simply a set of characters encased in quotations, this lets python know that it is a word. Sometimes when we do things with strings we'll need to change them in order to do something. Python is case sensitive, for example "Null-Byte" is not the same as "null-byte". This is where mani...

This is second post in my series of posts for finding hacked accounts online. Please do read the part 1 of the post at http://null-byte.wonderhowto.com/how-to/find-hacked-accounts-online-part-1-0164611/

Welcome back, rookie hackers! We recently began an exploration of ways to hack using the Bluetooth protocol. As you know, Bluetooth is a protocol that connects near field devices such as headsets, speakers, and keyboards. Its minimum range is a 10-meter radius (~33 feet) and maximum is at 100 meters (~328 feet).

Hello, fellow grey hat hackers and aspiring coders. I'm back again with another python tutorial. Just that this one is gonna be a lot cooler ;-). We gonna make an encryption program, that well you know encrypts all the files on your pendrive or hdd or whatever you want....Also lots of thanks to DrapsTV. They have helped me a lot with Python and making awesome programs. The video is here:

Welcome back, my greenhorn hackers! As all you know by now, I'm loving this new show, Mr. Robot. Among the many things going for this innovative and captivating program is the realism of the hacking. I am using this series titled "The Hacks of Mr. Robot" to demonstrate the hacks that are used on this program.

There are a bunch of new and interesting features packed inside of Windows 10, but one of the most exciting ones is the Microsoft Edge web browser, the long-awaited replacement of Internet Explorer.

Here's a fact that everyone knows: avocados are delicious in guacamole, salads, and sandwiches. Here's a fact that's less commonly known: avocados are delicious in desserts, too.

Welcome back, my greenhorn hackers! One of the most important issues any hacker must address is how to get past security devices and remain undetected. These can include antivirus software, intrusion detection systems, firewalls, web application firewalls, and numerous others. As nearly all of these devices employ a signature-based detection scheme where they maintain a database of known exploits and payload signatures, the key is to either:

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

I'm a firm believer that a sandwich is the ultimate food. It's filling, but not heavy; it has carbs, protein, veggies, and sauces; and it's easily customizable. Add that all up and you've got the absolutely perfect lunch.

Welcome back, my neophyte hackers! In previous tutorials, we learned how to steal system tokens that we could use to access resources, how to use hashdump to pull password hashes from a local system, and how to grab password hashes from a local system and crack them.

There are lots of great reasons for going out to a fantastic coffee shop for a cuppa. Coffee shops have a lovely ambiance, are a perfect place to meet with friends or do some work, and are a great excuse to get out of the house. Seeking out a perfect cup of coffee, however, shouldn't be one of the reasons that you hit up your local café.

Welcome back, my hacker novitiates! In an earlier tutorial, I had introduced you to two essential tools for cracking online passwords—Tamper Data and THC-Hydra. In that guide, I promised to follow up with another tutorial on how to use THC-Hydra against web forms, so here we go. Although you can use Tamper Data for this purpose, I want to introduce you to another tool that is built into Kali, Burp Suite.

Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world!

Most of you already know that a zero-day exploit is an exploit that has not yet been revealed to the software vendor or the public. As a result, the vulnerability that enables the exploit hasn't been patched. This means that someone with a zero-day exploit can hack into any system that has that particular configuration or software, giving them free reign to steal information, identities, credit card info, and spy on victims.

With all of the different websites we use in our day-to-day lives, keeping track of our numerous login credentials can start to become a hassle. This has created a market for password managers that aim to centralize these account credentials and generally streamline the process of logging into our favorite sites.

Welcome back, my amateur hackers! Many of you here are new to hacking. If so, I strongly recommend that each of you set up a "laboratory" to practice your hacks. Just like any discipline, you need to practice, practice, and practice some more before you take it out to the real world.

Sometimes, it helps to be prepared before jumping into a new relationship; look before you leap! To have a healthy relationship with someone who has an STI, it is advisable that you enter the relationship knowledgeable about sexually transmitted infections and what your risks might be.

Welcome back, my greenhorn hackers!