When you head to your neighborhood gardening center to find a shade tree for your garden, the variety of choices can be pretty overwhelming. There are so many kinds of trees, and each of those trees has its own varieties. In this clip, Dave Epstein from Growing Wisdom will help find the best shade tree for you.

A soil block maker is a cool device for starting your seeds. All you do is fill a container with soil and use the block maker like a cookie cutter. Then you'll have little blocks of soil to plant your seeds in, and you can easily transfer the block to your garden. Now stand back and watch your plants grow!

The vinca, or periwinkle, is a hearty flower that adds a lot to any garden. It comes in a variety of colors, and grows in the sun as well as the shade. But they're so hearty that you have to watch them, or they'll start springing up where they're not supposed to. In this video, Dave Epstein from Growing Wisdom walks you through using periwinkles in your garden.

With low garden tunnels you can protect your plants from frost and insects, and you can overwinter your crops. In this episode of Growing Wisdom, host Dave Epstein will look at how to build a garden low tunnel. He'll focus on using the Quick Hoops Bender for the project.

You can't have a werewolf movie without a werewolf, but how do you make one. Well, you should start of small. Try your hands at the wolf claws. To create these furry werewolf claws, you'll need a glove and some other materials. Watch this video tutorial to learn how to make a breakable prop computer. For written instructions on the actual claws, check out the WikiHow article, "How to Make Origami Paper Claws".

Check out this informational safety video that provides a few motorcycle safety tips. This video was created to encourage safe motorcycle riding. Warning! This video contains SERIOUS motorcycle crash videos! Here are a few safety tips to keep motorcyclists safer. The contents of this video are paraphrased & condensed from a motorcycle magazine article. Avoid severe injury and death by learning a few basic motorcycle safety precautions.

You'd like to treat your friend to a drink from the vending machine, but you only have enough cash for one soda. What do you do?

Learn the Dutch alphabet, definite articles, noun plurals, personal pronouns and the verb "to walk" in this 4 part video series.

Plagiarism is a serious offense, even if you are copying from the web. With this tutorial, learn how to cite websites properly using MLA format and avoid any trouble.

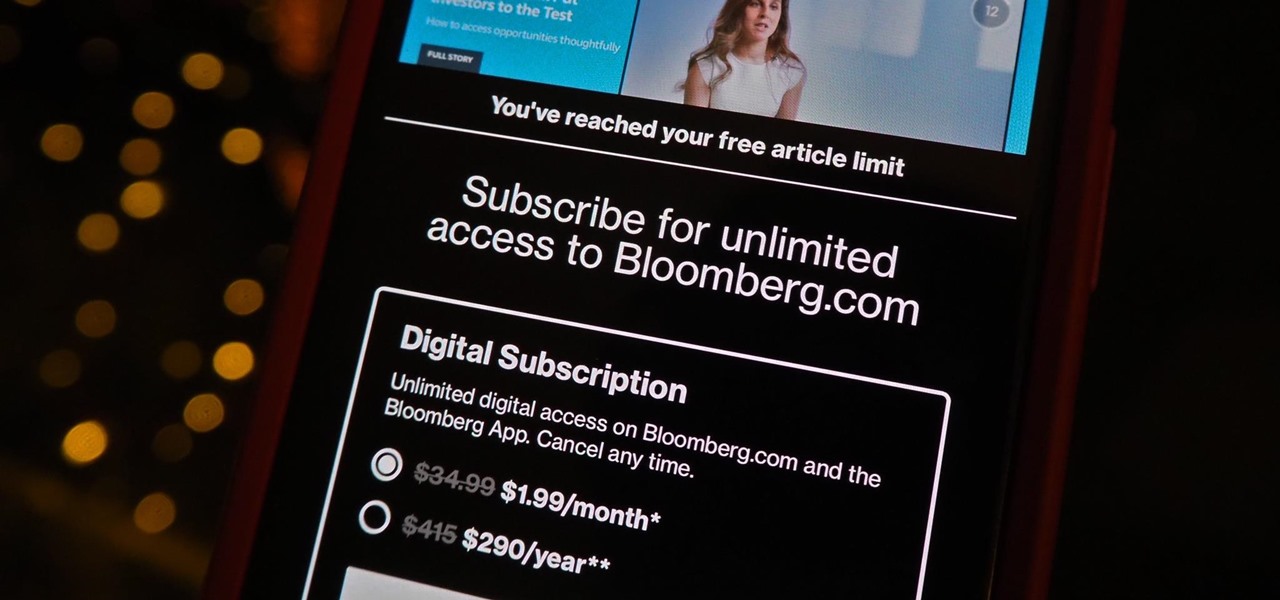
One of the most aggravating things that can happen on Facebook, Twitter, and other social media apps is when a friend shares an exciting story, and a paywall prevents you from reading any of it. You could pay for a subscription to unlock it, but there are so many news sites that it can be both confusing and expensive to spend money on all of them.

You're halfway through reading an article on your iPhone, when the display just turns off. Frustrated, you open the article again, only for the display to go black again. You shouldn't have to keeping touching the screen to keep your iPhone from going to sleep. Luckily, you can delay or even stop your iPhone from doing so with just a few taps.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

Why would Magic Leap, a company preparing to launch its first augmented reality headset this year, need a developer for iPhone and iPad apps? It's not as crazy as it sounds.

A week into my internship, I experienced pretty serious back pain and slight difficulty breathing. I scheduled a doctor's appointment to make sure nothing was wrong, and I got a surprising diagnosis: bad posture.

Not only has there been difficulty finding consensus on a name for driverless, autonomous, self-driving, or automated vehicles, there is also the issue of what we actually mean when we say a vehicle is self-driving, automated, and so on.

Hello everyone! I hope you are having a great day so far. Today, instead of caring about networks we are going to talk about subnetting based on host requirements as promised in my first article about subnetting. Just like in the previous articles we will jump right into the examples because that's the best way to learn.

When you think of all the fun and games smartphones have to offer, it's easy to forget that they also make a great tool for getting things done. With utilities like document scanners, calendars, to-do lists, office apps, and password managers, that little computer you carry around in your pocket has the potential to increase your productivity levels in all aspects of life.

The title might not be in harmony with the post, but thinking a good title that perfectly matches your post... isn't that easy. Especially for this post.

UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - at my blog, here - https://techkernel.org/2015/12/11/embed-metasploit-payload-in-apk-easily/

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

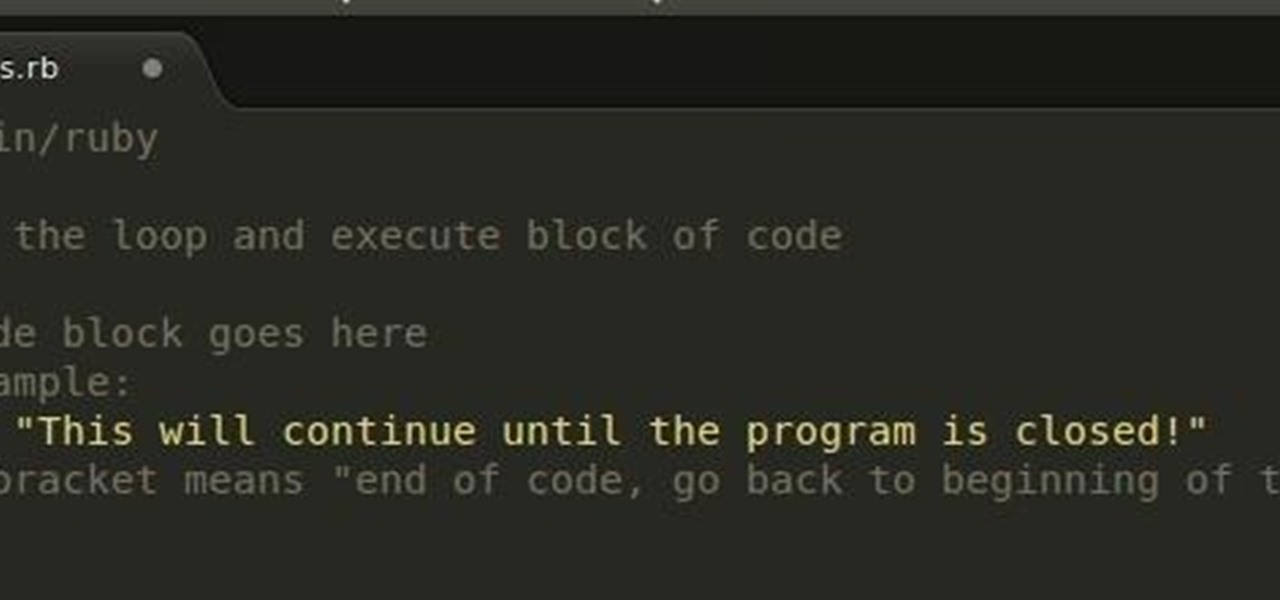
In the last Ruby article, we talked about how to store information in three different kinds of storages: variable, array, and a hash. After we get the data, we have many ways of using them, but, for right now,

Due to recent conflicts, I feel the urge to post this, in hopes that some of you will feel less hatred towards newbies, or a more respectable name, beginners.

Welcome back, my aspiring hackers! Although this article may have been better placed first in this series, I doubt that anyone would have read it when just starting out studying Linux. Now, that you are well into your Linux studies and have some familiarity with how it operates, I'd like to take this moment to explain the philosophy around the Linux operating system.

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.

Audiobooks are great because they require little-to-no effort on your behalf. When driving in traffic, why not listen to George R.R. Martin's lengthy A Feast for Crows instead of repetitive, commercial-laden radio? Maybe it harks back to prepubescent bedtime readings, but having things read to me is a very satisfying experience.

Using Facebook and Twitter as a news source can be frustrating at times, mainly because opening links will divert you away from your current application. Instead of a smooth process, you find yourself going back and forth from app to browser, over and over again.

Welcome back, my tenderfoot hackers! I have written many tutorials on hacking using Metasploit, including leaving no evidence behind and exploring the inner architecture. Also, there are my Metasploit cheat sheets for commands and hacking scripts.

Welcome back, my greenhorn hackers! After the disaster that was Windows Vista and the limited and reluctant adoption of Windows 8 and 8.1, Windows 7 has become the de facto standard operating system on the desktop/client.

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

In this Quick Clip, I'll be showing you how a supercooled soda is transformed into a slushy "slurpee" in under 4 seconds. I was inspired to do this little soda trick by The Super Effect's video on YouTube from a few years ago.

As you have no doubt observed, brothers and sisters do not mate. While they may find one another attractive, they find the notion of sex with one another repulsive. This is because a child produced by siblings has a high probability of sharing the same recessive genes, and recessive genes are often harmful unless coupled with dominant genes.

One of the coolest things for readers using the Samsung Galaxy Note 2 is the stock Smart Rotation feature. While most smartphones use the accelerometer to adjust the screen orientation, Smart Rotation actually uses the camera to detect your face-to-screen angle and adjusts accordingly. Now, if only there was a way that all Android users can continue reading an article or text without sporadic and unexpected 90-degree turns of their screen. Wait, there is!

When subjects are asked to watch a movie and not display emotions (say, a comedy without laughing, or a tearjerker without crying), they evidently use up glucose in particular areas of their brain in a way that subjects who are free to react however they want do not.

There are thousands of articles published every day about smartphones, tablets, eReaders, and any other kind of gadgets you can think of. The problem is that most people only really care about news related to the devices they actually own. So how do you filter out all of the stuff you don't care about? That's what Drippler does. It pulls news, tips, and app reviews and recommendations from all over the web and puts them all in one place, but only for the devices you want to read about. You te...

In recent light of Obama's assertion of executive privilege over important documents concerning the Fast and Furious operation, here's a brief article concerning this controversial power.

Learn how to sew a button by hand. Not wearing your favorite shirt because it’s missing a button? Don’t worry—sewing on a new one is simple and fast.

This video series explains how to write a good news article. Writing for a newspaper is not like writing an essay for school or a book. Watch this series and learn some good tips to writing successful articles.

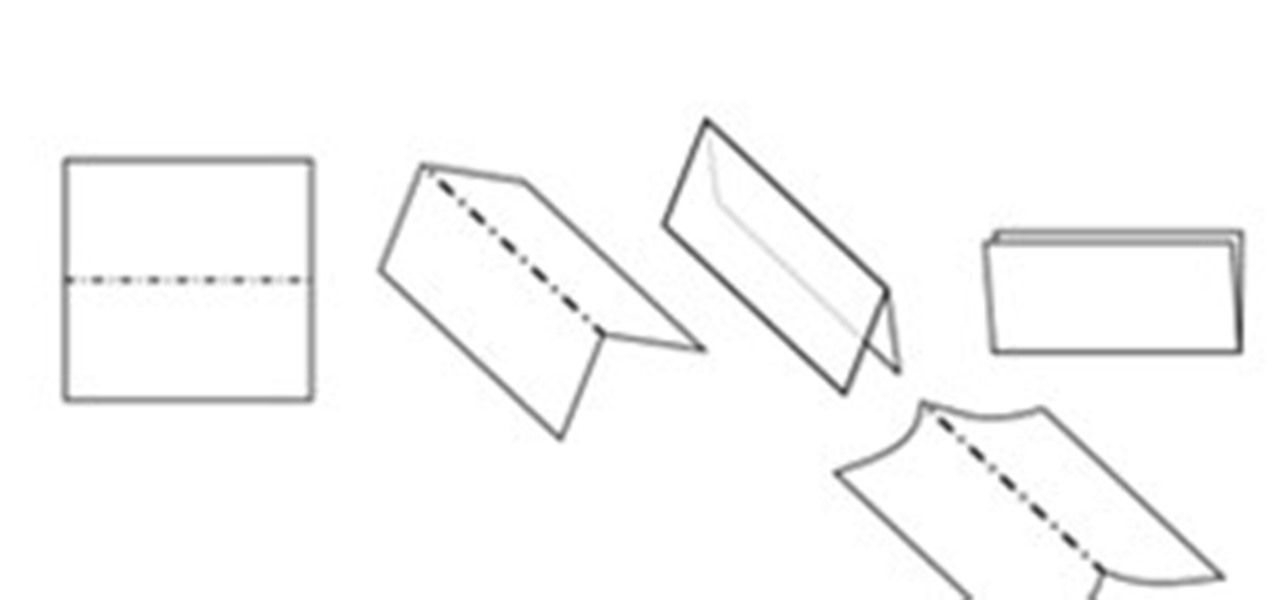
In this article you will learn how to understand written origami instructions, called diagrams. You can follow the video below or read the entire article

There's always a faster and more efficient way of doing things when it comes to Facebook. And if you have a Facebook Fan Page (Like Page) for your website, it's easily done right from your mobile device. Learn this super quick tip to post updates, videos, and pictures right to your Fan Page via your mobile device. Super easy you can do it in seconds.