I've created this guide to give you some ideas for how to progress quickly as well as some basics for how to operate FrontierVille. My tips are merely suggestions based on my experience and you are welcome to explore and play the game at your own pace. I hope you benefit from my posts and look forward to answering questions and bringing you more useful information here and on the Facebook page in the future! (All these blue links take you to more content just like this page, click them for mo...

Here are the13 best articles on How to Build a Potato Gun. http://www.scribd.com/doc/15796837/To-Make-A-Spudgun-An-instructionally-informative-document-by-Enoctis

The Motorola XOOM was just released last week to Android-hungry fans waiting the next best thing to Apple's iPad. But should it have been released, considering Verizon's switching to the 4G LTE network soon?

Time is running out. Christmas is almost here, and you still haven't worked your way through that holiday shopping list yet. But don't worry, there's hope yet— thanks to social buying websites like Groupon, LivingSocial, SocialBuy, Eversave, Tippr and BuyWithMe.

Etching your own circuit boards is tons of fun, but etching requires strong chemicals to dissolve the copper plating on blank circuit boards. The normal ferric chloride solution works well, but can be expensive and leaves permanent stains. Luckily, we can whip up our own etchant at home with everyday chemicals! Better yet, our new etchant will turn an eerie green color rather than the dull brown of ferric chloride.

I have an absolutely wonderful time making projects and writing articles for all of you mad scientists! Today, I will bring you behind the scenes for a look at the workbench, tools, and software that make the Mad Science World possible.

Creating any object you want is as simple as point and click if you have a 3D printer at home. If you don't have one handy, there are a few companies that offer printing services online. But to help services realize your design in extruded plastic, you have to make a 3D computer model for the printing machine. For beginners, the free Google SketchUp application is the best choice of software. Using only a few tool bar buttons and a scroll wheel computer mouse, you can model literally any obje...

Graffiti is a great way of getting your message out to the masses. The earliest known graffiti dates back to 30,000 years ago and used the traditional apply-paint-to-wall technique. Though our paint now comes in cans and not from scavenged berries, the actual graffiti process hasn't really evolved from those first cave paintings.

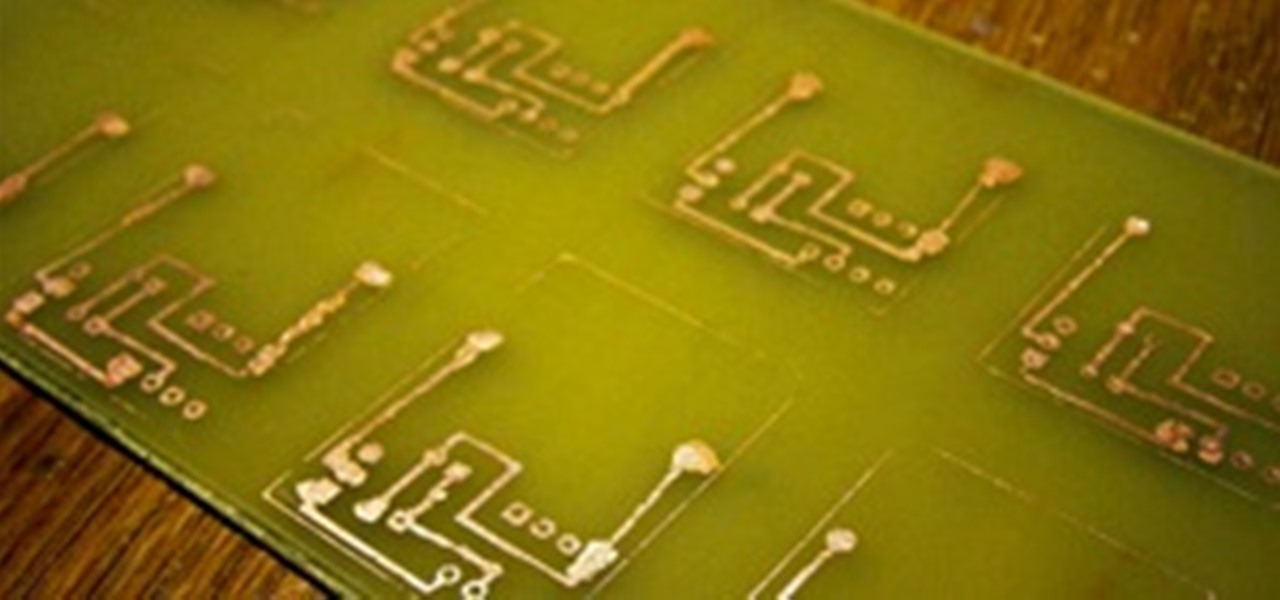
Homemade circuits are amazing. You can build any kind of circuit on a simple perfboard, as we have seen in previous projects. However, some projects require very tiny circuit boards. We could special order some boards from a printed circuit board (PCB) factory, but that will most likely involve a high price per board and a few thousand miles of delivery service to pay for.

You're sitting in front of your grandmother's Windows XP machine that has the worst infection you've ever seen. Safe mode? No dice. Restore points? They're compromised. Even worse, all of the files are hidden and none of the executables will run! This leaves her computer in a bricked state. Without some serious CPR, it will be lost to you. Sure, you could just reinstall the system, but then you might lose all of that valuable data.

People sometimes ask me about the IT industry here in the states. These folks are usually either trying to get into a certain field, or looking to switch or move into another one. Right now, you may currently be a Computer Science major that will be graduating shortly and are interested in the current state of IT security.

Big brother is watching when you're playing around on another system—and big brother is that system. Everything from operating systems to intrusion detection systems to database services are maintaining logs. Sometimes, these are error logs that can show attackers trying various SQL injection vectors over and over. This is especially so if they are using an automated framework like sqlmap that can spam a ton of requests in a short time. More often than not, the access logs are what most amate...

You walk over to your laptop, wiggle your mouse to wake up the screen, then fire up your browser to come visit Null Byte. Catching the article about Anonymous and how they presumably will not take down the Internet, you find yourself wondering... how would someone take down the Internet? Could they even do it?

Industrial espionage, social engineering and no-tech hacking are all very real and there are simple precautions that you can take to protect yourself, which this article will discuss. Whether you are a high-profile businessman or a housewife (or husband), keeping information you want to keep private, private, should be important to you.

If you follow the Anonymous, Occupy, and IT security scenes, you have no doubt heard about a dox release. What is it? How can it hurt you? And most importantly, how can you protect yourself from it? Some of these steps might seem common sense, while others will be an ah-ha! moment. Your private info is both your biggest weakness and your biggest weapon in your battle to remain anonymous. You must learn how to use it as both.

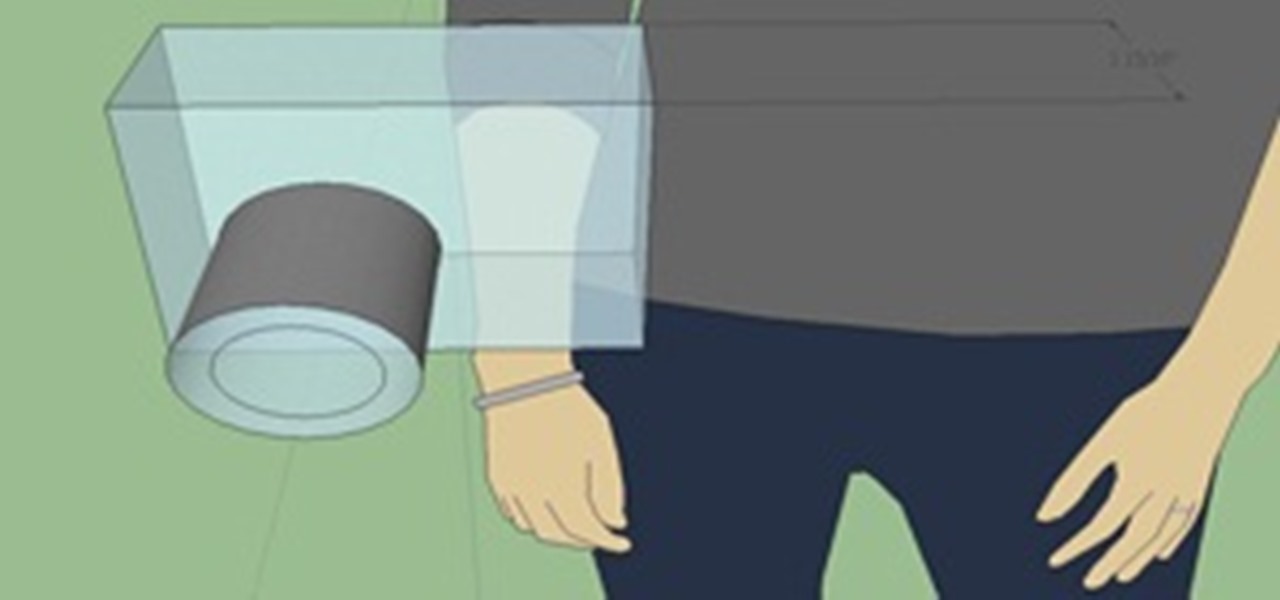
The agents of empire do not always arrive with warning. When you are besieged, surrounded, and infiltrated, imagination is often your best weapon against the oppressors. If all you have at hand is some duct tape and a disposable camera, fear not, you have the makings of a powerful taser!

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

You want to put out a live web server, but you don't want to be owned in the process. An expert eye for security is not needed if you take a few basic steps in locking down the hatches. Most successful attacks today are not the complex, time-consuming tasks you might think, but simple lapses in policy that a hacker can take advantage of to compromise your server.

If you're a frequenter of Null Byte, I bet you have at least some interest in information security. Furthermore, you have a hobby that if applied in certain ways, will get you arrested. I've received quite a few messages from the community here about federal cybercrime law and how it applies to them, so I decided to get together with my lawyer to come up with some answers.

In my recent Darknet series, I attempted to connect the dots on the Deep Web. I covered the two largest anonymity networks on the Internet today, Tor and I2P. While my initial four articles were meant as an introduction, I ended up receiving a lot of interesting comments and messages asking the technical differences between the two. I'd like to thank all of you for letting me know what was on your minds, as you should always!

Accounting and Finance Degree

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

Many windows users, if not all, run into a virus infection once in a while. This is unavoidable when using Microsoft's operating system. Without digressing too much, the fact that Windows is such a popular OS with no controlled software sources makes it easy for viruses and malware to spread. And while there's a plethora of antivirus tools for Windows, sometimes infections (such as certain scareware) can disable the install and/or use of antivirus systems and render your OS unusable until cle...

If you're on a tight budget for food, whether you're in college, or someone just starting out living on their own, you're probably low on money and sick of ramen noodles. Don't get me wrong, ramen can be tasty and filling, and there is almost nothing cheaper.

In the age of automatic video editors and all around software-assisted creativity, how can a humble blogger help people master a program if said program does all the work for you?

Now, I know what you're thinking... "I need an extra sexy coffee table that is like no other."

The Elder Scrolls V: Skyrim set off a bang in the video game world this month. It will likely be video game of the year a few times over. Skyrim is another part to a series set in the fantasy world of Tamriel, a world filled with mystical creatures, folklore, and even its own history. It's quite the beatuiful and immersive experience. If you have not picked up the game yet, please do (my fiancée even plays!). Also, make sure to buy it new, so the hard working coders at Bethesda get the money ...

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. While mining is a basic aspect of Minecraft, it is often overlooked. Every adventure requires iron and diamonds and other ore and if you're playing in hardcore mode then you need all the help you can get.

It's Monday, and once again it's time to highlight some of the community submissions posted to the Math Craft corkboard. In addition, I thought we'd take a look at having fun with the geometrical properties of polygons and circles by using one of the best circles I know, the penny.

If you thought the last post on Two Circle Wobblers was wild, then wait until you see what happens when you build wobblers out of two half circles or two ellipses. In both of these cases, the center of gravity still remains constant in the vertical direction, allowing them to roll down the slightest of inclines or even travel a significant distance on a level surface if given a push or even when blown on.

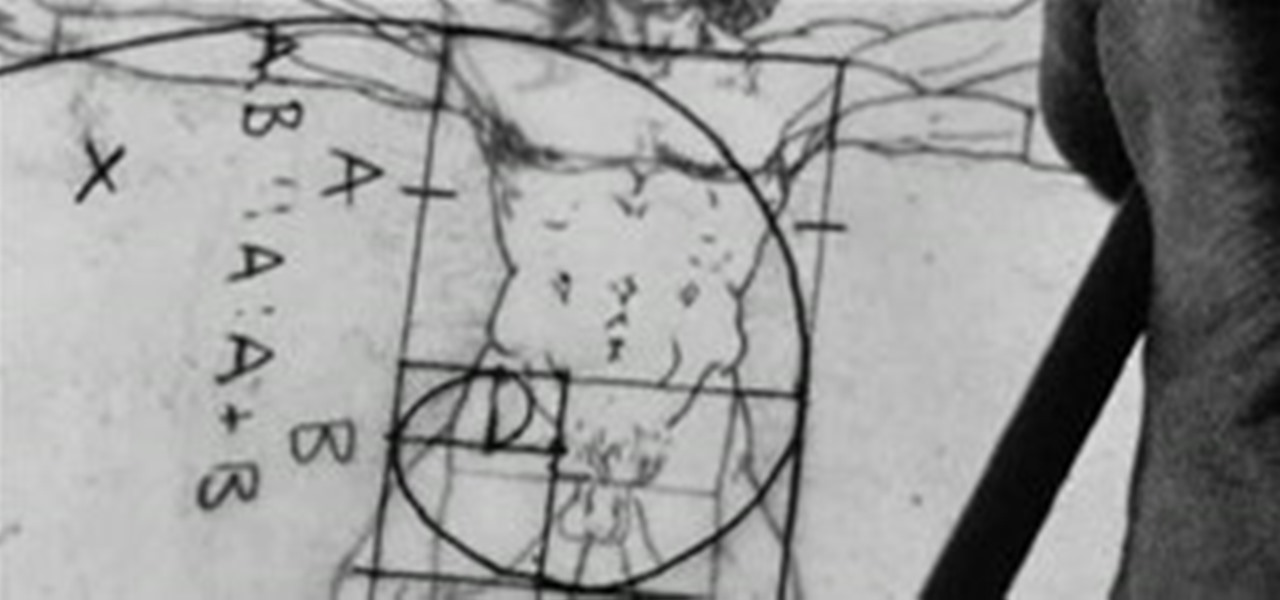
It's Monday, time to highlight some of the community submissions posted to the Math Craft corkboard. One of these posts inspired me so much, I think it merits a closer look. Today, I present a "simple" method for making a golden spiral using just a straight edge, a compass, and a template, inspired by RJ Ellicock's golden ratio post.

I've seen numerous tutorials on how to create a "strong" password. This makes me laugh. These titles imply "one" password, which is wrong in and of itself. A person should have many passwords, all different, and all extremely long. People may ask how they're supposed to remember lengthy passwords and why their current password isn't good enough. Well, I'm going to show you.

If you're interested in bypassing Windows and Linux passwords, there is a great tool from the good people at Kryptoslogic. Have you ever forgotten your administrator password? Have you ever bought a used computer with a password on it? Well, Kryptoslogic have created a boot-disc call 'Kon-Boot', which allows you to bypass any Windows 32 or 64 bit OS, as well as Linux passwords. There is both a paid and freeware version available.

There are seemingly endless photography apps for the iPhone—it is perhaps one of the most popular arenas for application developers. We've covered a few in Giveaway Tuesdays, but nothing comprehensive.

If you follow indie games at all, you've probably heard of Bastion. During its development, it took home numerous Best in Show prizes from E3 and other game conventions while building up an incredible amount of buzz in the games press. Part of what is intriguing about Bastion is its cool art design, which in the last couple months, peaked my interest more so than the gameplay or the much-ballyhooed narration.

Hangouts are one of the most fun features in Google+. As long as you have a webcam and a microphone, you can "hangout" with up to 10 of your buddies on Google+ and do just about anything. Of course, sometimes it can get kind of awkward when you are hanging out and you don't really have anything to say. This problem can be mitigated if you host hangouts with a plan.

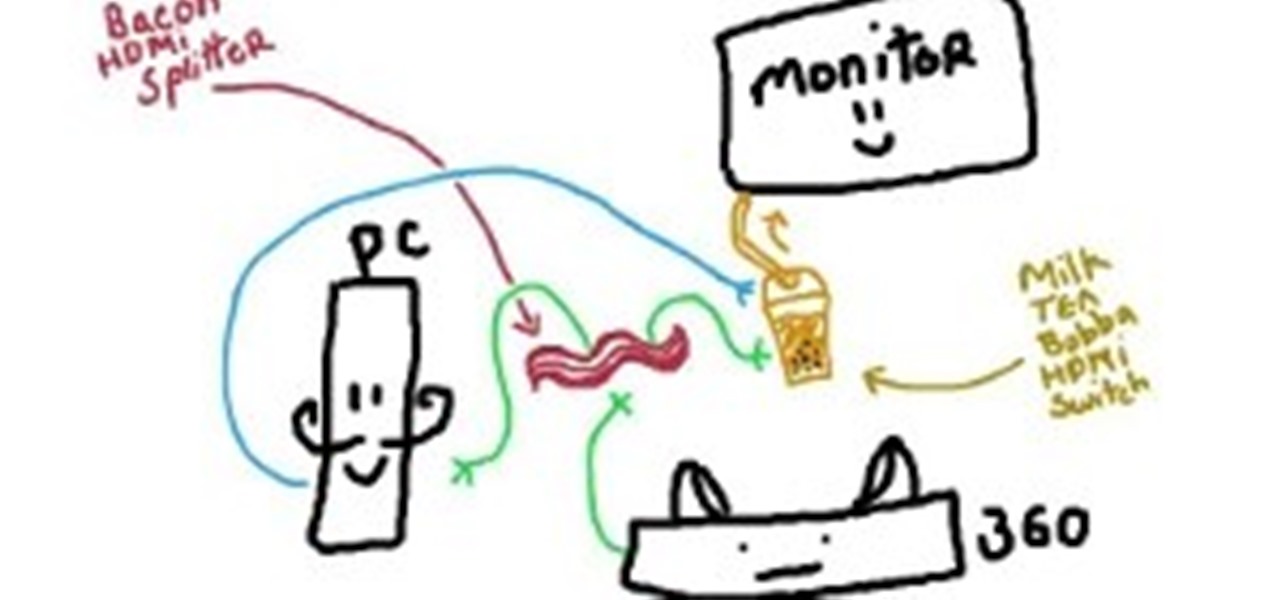
Video capture... how does it work? Apparently, I have no idea. What I thought would be a simple undertaking turned out to be a slow and annoying pain. I just wanted to capture video in high definition and to lessen the time it takes to setup, record, and upload the video.

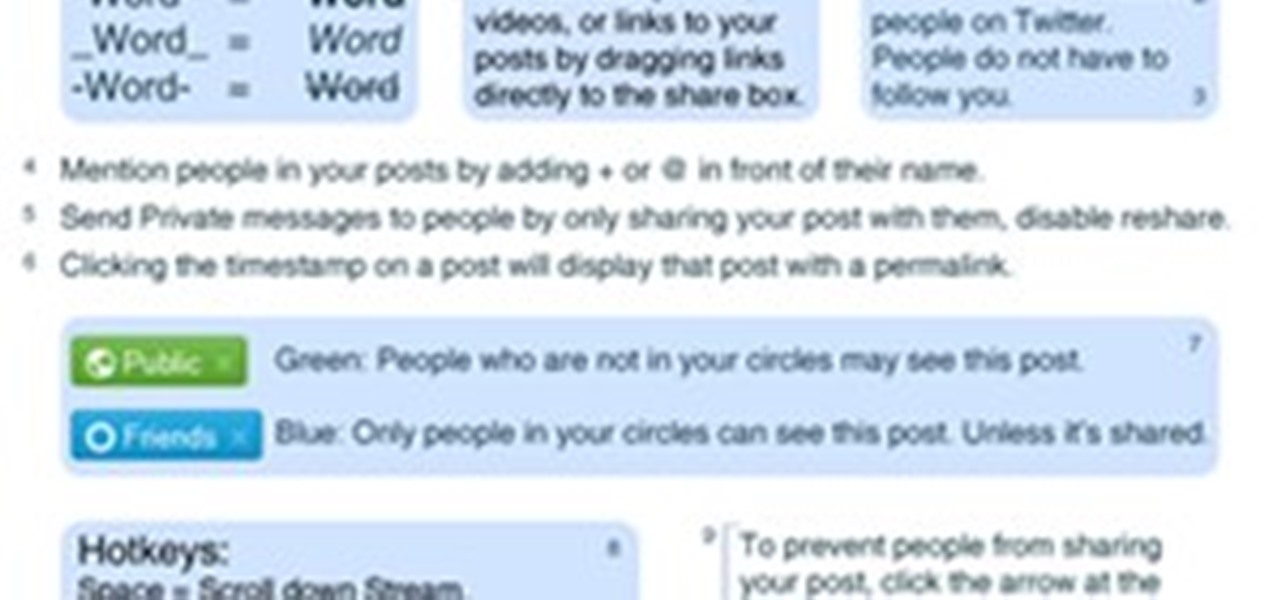
With the Google+ team members being generous and free-flowing with advice on some of the more advanced features of Google+, we'll be publishing a weekly summary of the latest pro tips. Chances are, if you've been following the Google+ team members, you've seen some of these already but you don't have them all in one handy place.

WELCOME & THANKzZz For Your Contribution, Support And Time...! ...Hello, zZz~AKA~StanDP Here...;