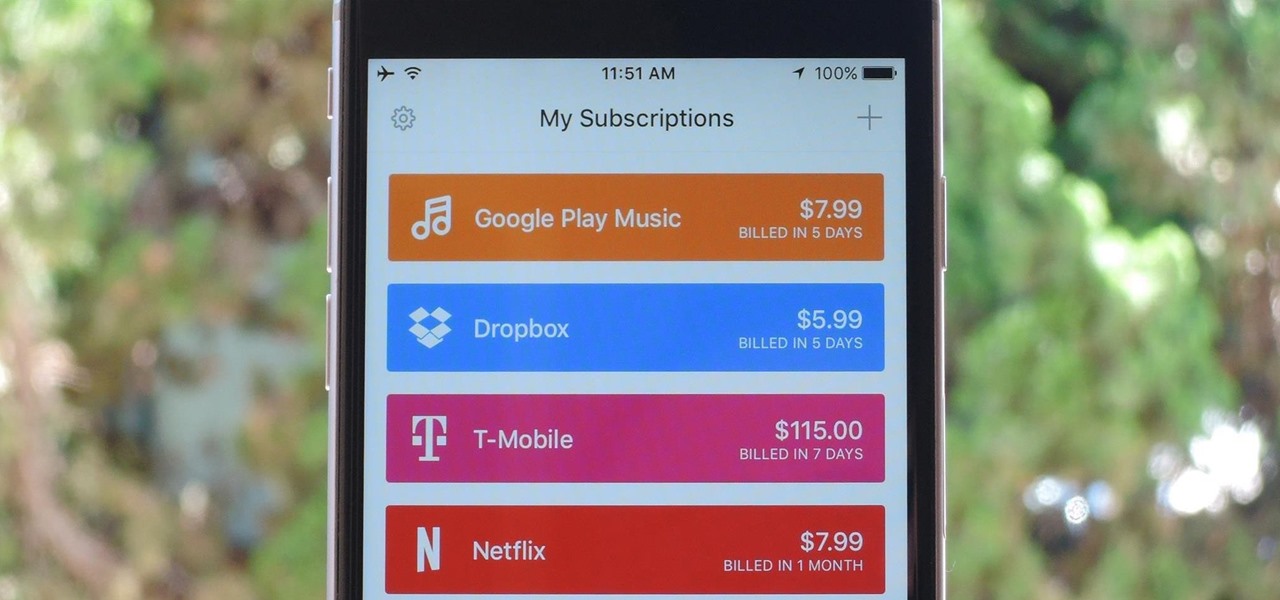
As the internet continues to become a bigger part of our day-to-day lives, we slowly but surely start to rack up a bunch of web-based subscriptions. These internet subscription services—Netflix, Hulu, and Amazon Prime, just to name a few—may seem innocuously cheap individually, but when combined, they actually comprise a significant portion of our monthly bills.

Reddit announced this morning, April 7th, that it has finally released an official mobile app. You can get it on Android and iOS.

Welcome back, my budding hackers! In this series, I have been trying to familiarize you with the many features of the world's best framework for exploitation, hacking, and pentesting, Metasploit. There are so many features, and techniques for using those features, that few pentesters/hackers are aware of all of them.

Welcome back, my hacker novitiates! Often, to hack a website, we need to connect to and exploit a particular object within said website. It might be an admin panel or a subdirectory that is vulnerable to attack. The key, of course, is to find these objects, as they may be hidden.

Welcome back to another episode of Java Tutorials, In today's tutorial, we'll be learning about what methods are, proper syntax when writing Methods, and why they are beneficial in a program's code.

I was fortunate enough to be visiting one of my college classmates in Columbus, GA last spring and saw two large bags of onions in his kitchen... but not like the ones you get at the grocery store. Two standing 50 lb. bags!

Simmering or poaching food is a total pain sometimes. The problems are numerous: a layer exposed to air often dries out and creates a gross skin that can ruin the texture of the sauce, the poaching liquid evaporates too quickly and causes the poached protein to burn, and so on.

This is my first tutorial on this website. So, if you think anything to be wrong, just place it in the comments.

Salad spinners are one of the more divisive kitchen tools out there. On one hand, they're incredibly easy, efficient, and useful. On the other hand, they're a single-use tool that takes up a lot of space.

Microsoft's "Fall Update" to Windows 10, code named Threshold 2, has a lot of new tricks up its sleeve. It's the biggest update we've seen since Windows 10 was released this summer, and it's rolling out to all users right now.

Welcome back, my amateur hackers! With Halloween right around the corner, I thought you could have a little fun with your newfound hacking skills using a hack that is guaranteed to freak out your boss, teacher, coworker, friend, etc.

Lemons are often displayed as a bright and beautiful pop of color in many home kitchen displays. They lend a lovely scent to the air and an aesthetic sense of freshness to any setting. Therefore, it would be easy to assume that lemons are best left at room temperature.

Here's a fact that everyone knows: avocados are delicious in guacamole, salads, and sandwiches. Here's a fact that's less commonly known: avocados are delicious in desserts, too.

Not to be outdone by the announcements of Mac OS X El Capitan and iOS 9, the Apple Watch is also getting a much needed software update. Some of the notable new features we can look forward to on watchOS 2 are Nightstand mode, additional screens for friends, email replies, and other improvements we probably should have already had.

The Galaxy S6 already has one of the best cameras on the market, but a few minor annoyances still linger. Full-sized photos are stored with heavy compression that can cause artifacting, burst mode shots aren't taken at 100% quality, and the camera flash cannot be used when your battery is below a certain threshold.

I'm a firm believer that a sandwich is the ultimate food. It's filling, but not heavy; it has carbs, protein, veggies, and sauces; and it's easily customizable. Add that all up and you've got the absolutely perfect lunch.

It's already that time of year again—LG has unveiled its latest high-end smartphone, dubbed the G4. In past iterations, LG released its flagship devices in the fall. But slowly over the course of the past 2 years, the release schedule has been bumped up to be more in line with HTC and Samsung's springtime releases, and further away from the sales-sucking iPhone event each fall.

Welcome back, my neophyte hackers! In previous tutorials, we learned how to steal system tokens that we could use to access resources, how to use hashdump to pull password hashes from a local system, and how to grab password hashes from a local system and crack them.

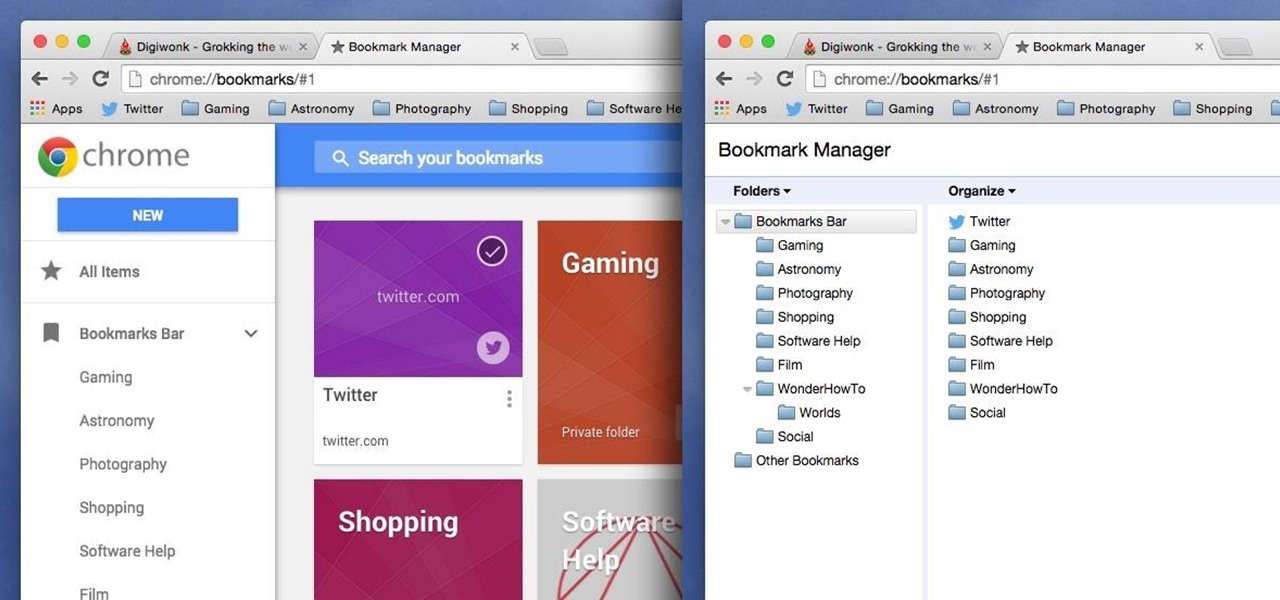
Chrome has been pushing out a lot of new changes lately, but not all of them are as good as they think they are. Earlier this year, there was an update that changed how user profiles worked, which made it harder to actually switch profiles. Luckily, there was a way to get back the old profile management interface, but now there's another "improvement" that you might want to change—Chrome's new Bookmarks Manager interface.

There are lots of great reasons for going out to a fantastic coffee shop for a cuppa. Coffee shops have a lovely ambiance, are a perfect place to meet with friends or do some work, and are a great excuse to get out of the house. Seeking out a perfect cup of coffee, however, shouldn't be one of the reasons that you hit up your local café.

Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world!

When you're expecting an important call or text, it's pretty annoying to hear or feel your phone go off just to find out it was your reminders app telling you that you need to buy more contact lenses. Not quite as annoying as phantom phone vibrations, but it's up there.

The camera in CyanogenMod, CameraNext, takes some pretty impressive shots when compared to those offered by HTC Sense and Sony Xperia, but it doesn't have many of the features that make it a real competitor. Even the Color OS version of the OnePlus One has received better reviews when comparing low-light shots, which implies that it's not the camera sensor that's lacking, but the software.

Most of you already know that a zero-day exploit is an exploit that has not yet been revealed to the software vendor or the public. As a result, the vulnerability that enables the exploit hasn't been patched. This means that someone with a zero-day exploit can hack into any system that has that particular configuration or software, giving them free reign to steal information, identities, credit card info, and spy on victims.

Yosemite is definitely an improvement over Mavericks, but there are still some painfully obvious and annoying bugs that occur within certain apps.

The Nexus 6 uses an Ambient Display notification system that was heavily inspired by the Active Display feature on the Moto X. Essentially, the device shows a black-and-white version of the lock screen whenever you receive a new notification or pick the phone up. This is all made possible by the N6's AMOLED display that doesn't have to waste any battery to power black pixels on the screen.

Samsung's Galaxy Note 4 is a beautiful device worthy of all the critical acclaim it has received thus far. But aside from the S Pen features, most of the Note's user interface has a great deal of overlap with the Galaxy S5 that we all know and love.

With all of the different websites we use in our day-to-day lives, keeping track of our numerous login credentials can start to become a hassle. This has created a market for password managers that aim to centralize these account credentials and generally streamline the process of logging into our favorite sites.

One of the biggest improvements in Mac OS X Yosemite came to the Spotlight search feature, allowing users to not only search through their applications, but also their emails, text messages, iCloud, and the web.

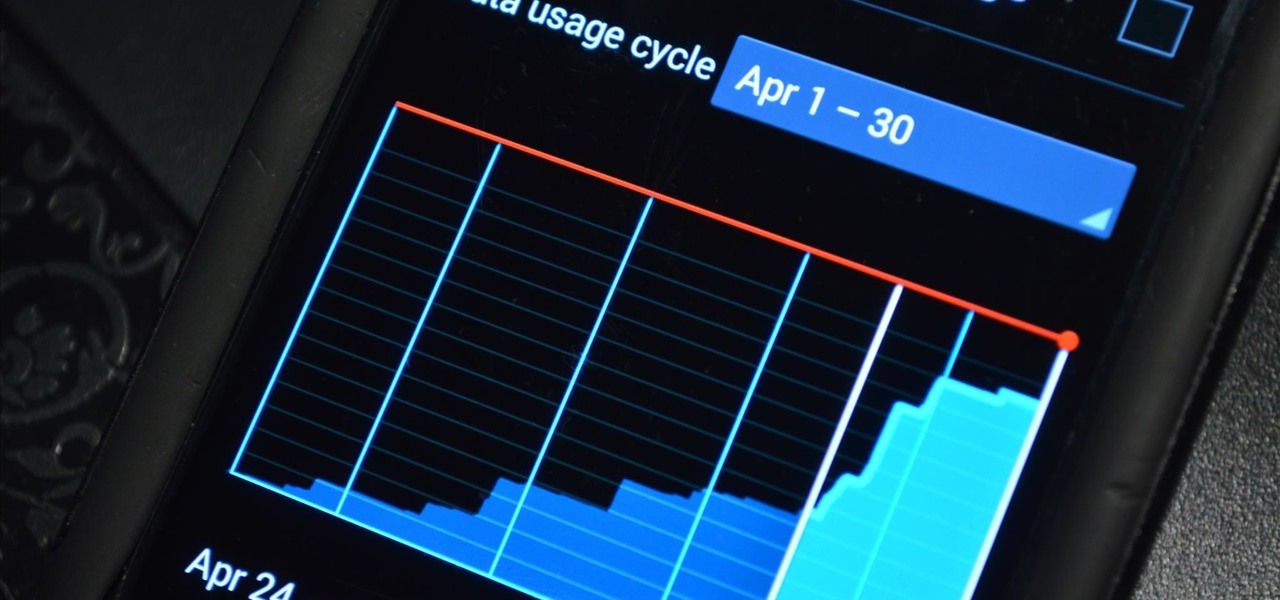
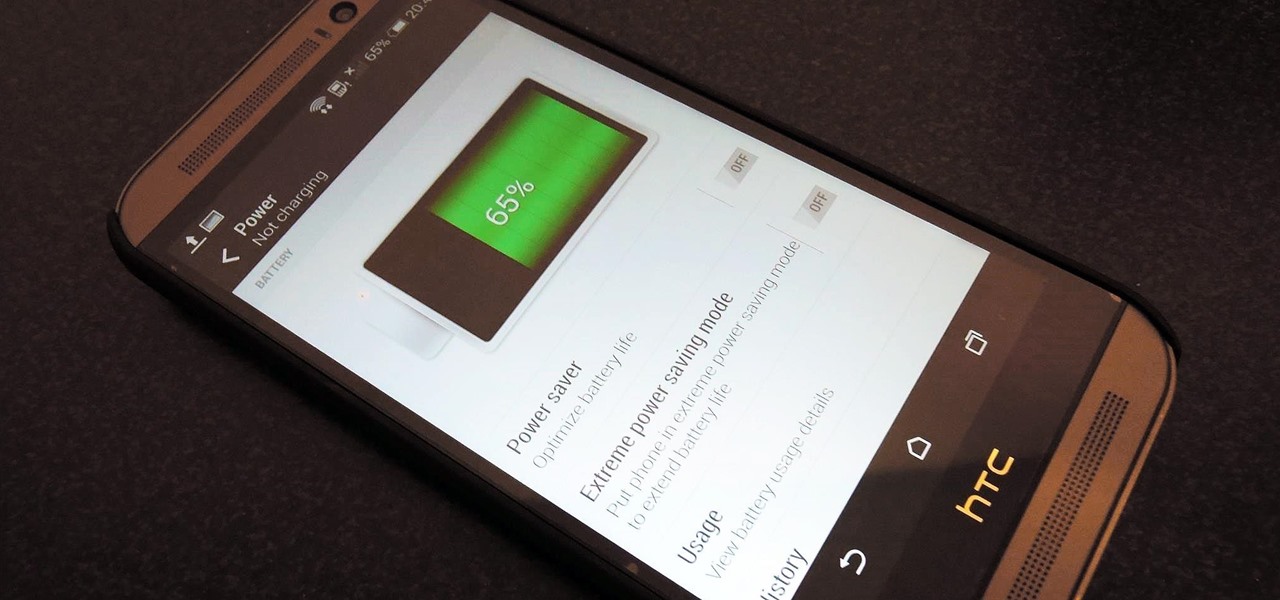
Increased battery life is easily one of the most sought after improvements to a device and often drives intrepid users to root their phones, flash new ROMs, and try out experimental kernels.

Sometimes, it helps to be prepared before jumping into a new relationship; look before you leap! To have a healthy relationship with someone who has an STI, it is advisable that you enter the relationship knowledgeable about sexually transmitted infections and what your risks might be.

Google's text-to-speech engine is getting pretty good these days. In a recent update, the computerized voice that reads on screen text (like Google Now search results) got an audio quality bump that brought its clarity up to its highest level yet. And with each update, that robotic voice becomes a bit more human.

Although lacking in megapixels, the HTC One M8's camera can be considered a top-tier, flagship-level shooter. With the Duo Camera and UltraPixel technology behind it, it can make even the most inexperienced photographer snap pictures like a pro. There seems to be little missing for the average user, but for the more seasoned photographers, some of the standard settings may seem a bit too dumbed down.

Last week marked the announcement of LG's new G3 smartphone, and with it came a ton of new features and improvements to their Optimus UI. While most manufacturers put little effort into their keyboards—probably due to the attraction of third-party alternatives—LG has made their latest iteration one of the best OEM keyboards I have ever used.

It's been over two whole years since the Samsung Galaxy S3 was released, so let's face it—our beloved GS3, once an iconic heavyweight in the tech arena, is almost as washed up as Sylvester Stallone.

HTC claims to have improved the One M8's battery life by 40% over its predecessor, but there is always room for improvement.

Welcome back, my greenhorn hackers!

Team Win Recovery Project (TWRP) is a custom recovery for Android devices and the one used by most softModders, mainly because it has touch-based actions, as compared to the more time-consuming button-based approach that ClockworkMod (CWM) uses.

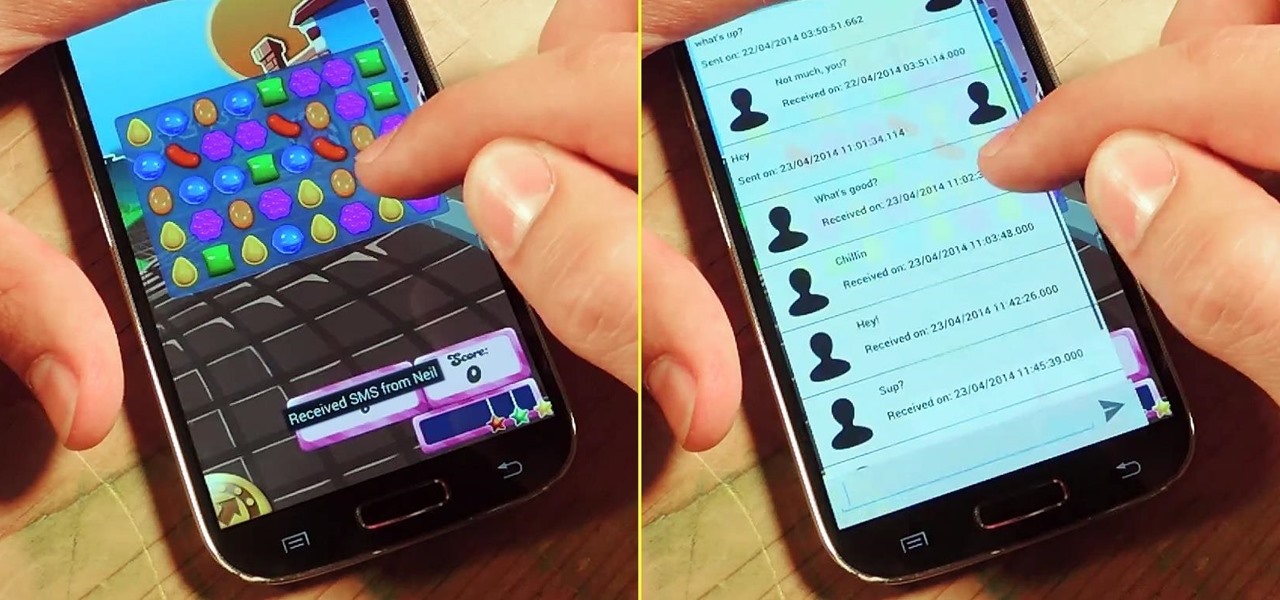
I'm a textaholic, as I've said many times before, but even textaholics forget to respond sometimes. When I'm watching a YouTube clip or devouring delicious snacks in Candy Crush Saga, I'll often ignore incoming texts and forget to respond later.

Welcome back, my greenhorn hackers! Although we have focused primarily on technical hacks here, social engineering can sometimes be especially effective. This one requires a bit of technical skill, but not too much. In addition, it's limited by how specific a target you can choose—but it will work.