While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.
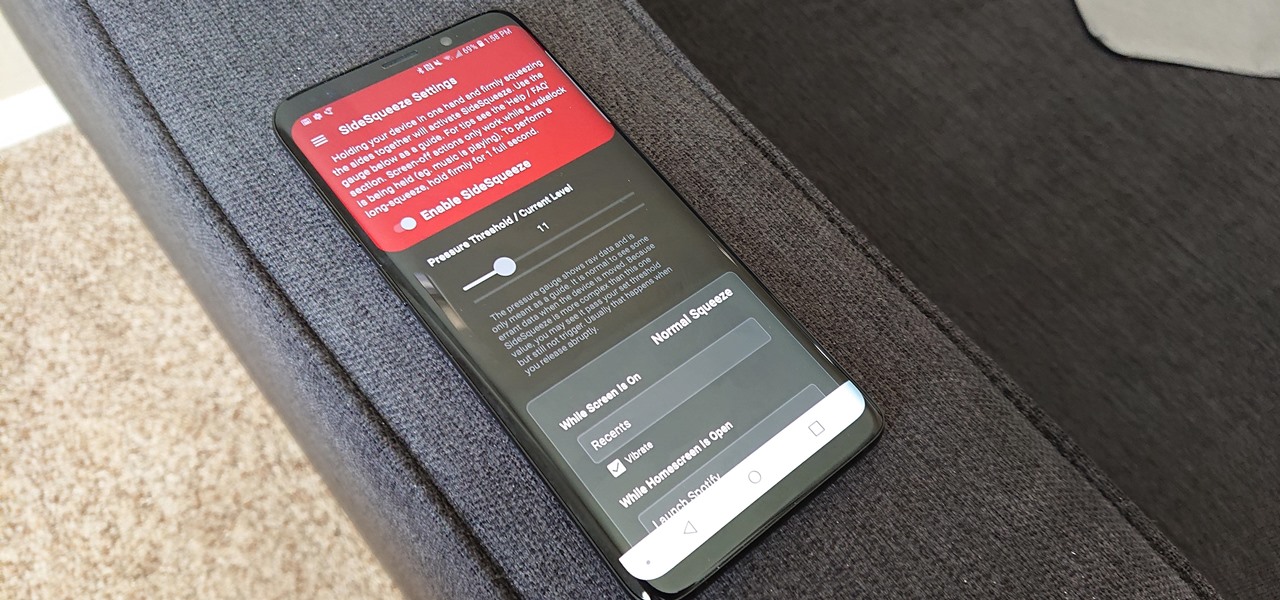
All the Android fans out there undoubtedly remember the squeeze gestures introduced with the HTC U11. Google continued the trend by bringing the gestures to the Pixel 2 and Pixel 2 XL. Thanks to a brand new app, you can now enable similar squeeze actions on your Galaxy S9 or S9+, and even some older Samsung phones.

Super Bowl LII will bring millions of football and non-football fans together to watch the big game on the big screen. But without a cable subscription, this process can be a little daunting. Luckily, the Google Play Store and the iOS App Store offer a few ways to accomplish this — no cable contract required.
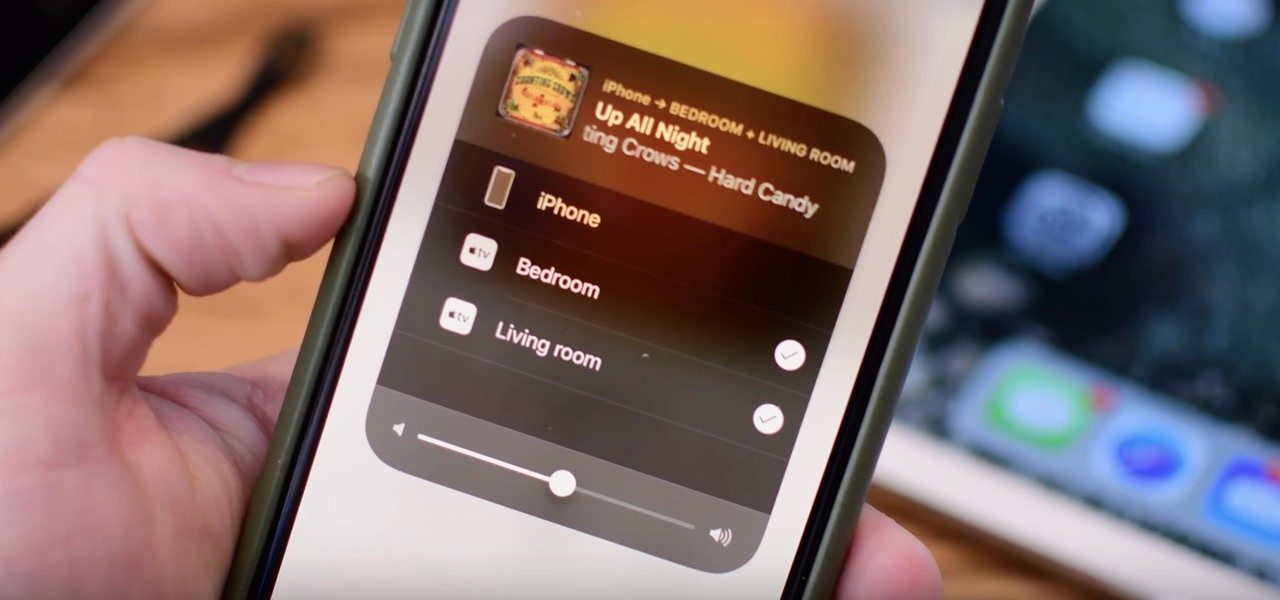
Back in June 2017, Apple promised us AirPlay 2, a simple way to connect and control multiple speakers together via an iPhone or other Apple device. While the feature was included in early iOS betas, by iOS 11's official release, AirPlay 2 was nowhere to be found. After all the numerous subsequent iOS 11 updates, it's finally here in iOS 11.4.
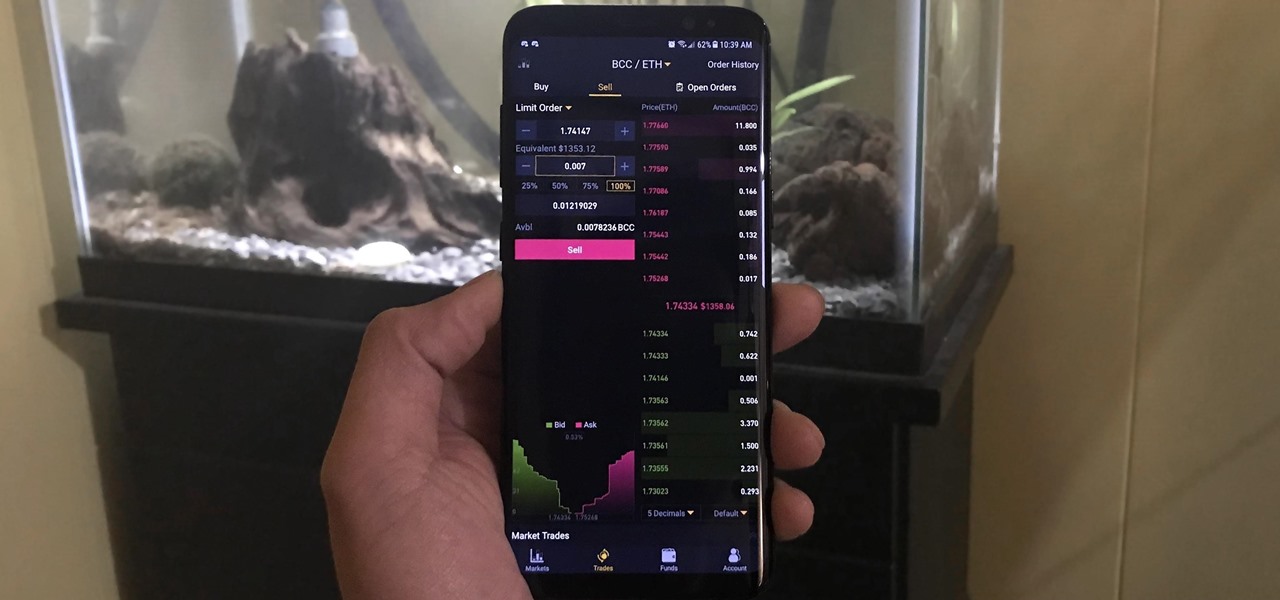
Using Bitcoin (BTC) or Ethereum (ETH) to buy alt-coins like TRON (TRX), Stellar (XLM), or Ripple (XRP) can seem intimidating if you're new to cryptocurrency. Though you'll still need to do your research to avoid potential disasters, Binance takes the hassle out of trading digital currencies on your smartphone.

Many people think antivirus apps are useless — why pay a subscription fee when most malware can be avoided with common sense? But the thing is, there were an estimated 3.5 million malicious Android apps discovered last year, with many of them making their way onto the Play Store. As this number continues to rise, can you truly depend on common sense to protect you?

Telegram routinely boasts about its secure messaging for truly private conversations between two parties. However, default cloud chats in Telegram are only encrypted between client and server, not client and client, which means you have to be a little proactive in making sure your private conversations on Telegram are really private.

Regarding foodborne pathogens, eating fish is not as hazardous as it was a few years ago — but if fins are on the menu, it's good to have a heads-up about what's good and what's bad these days.

It won't come as a surprise to hear that your cell phone, tablet, and laptop are loaded with bacteria and other organic material. While most of these bacteria are harmless, there are good reasons to reduce the capability of your mobile devices to infect you—or other people.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

Yes, I understand some people may consider this a repost. However, I have been searching for this answer for 3 weeks and after reading numerous reddit post, Kali Forums post and Null byte post I finally have gotten it to work for me. I would like to compile and share this information with you guys.

One of the hottest trends in the food world right now is "spiralized" vegetables. I will confess that I am a bit suspicious of any diet or food fad that eliminates an entire food group for anything other than physician-ordered health reasons, but something really good has followed in the wake of the Atkins/paleo/gluten-free movements.

The Microsoft Surface has been the go-to device for many professional artists since its initial release back in 2012. Since then, the Surface line has continued to offer customers a portable, high-powered machine that's a near perfect value for both casual and professional artists. And the Surface Book is its best model yet—a full laptop convertible with a detachable screen and a dedicated GPU.

UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - at my blog, here - https://techkernel.org/2015/12/11/embed-metasploit-payload-in-apk-easily/

If I could only eat one food for the rest of my life, it would definitely be potatoes. In fact, when I recently saw The Martian, I didn't feel that badly for Matt Damon. I mean, sure... he was stranded on a hostile planet, millions of miles from home. But he got to eat potatoes all the time! Pretty fair trade, if you ask me.

When using Linux, we often need to install new software, a script, or numerous large files. To make things easier on us, these files are usually compressed and combined together into a single file with a .tar extension, which makes them easier to download, since it's one smaller file.

Welcome back, my novice hackers! One of the most common questions that Null Byte readers ask is: "How can I evade detection by antivirus software on the target?" I have already talked about how AV software works, but to obtain a deeper understanding, what better way is there than opening up and dissecting some AV software?

Welcome, in this tutorial we shall we looking at creating a safe(r) way to back up your important files. The contents we will be covering are as follows;

Welcome back, my hacker apprentices! A you know, Mr. Robot is my favorite TV show this year, and not just for the realistic hacking. Rami Malek, the actor who plays Elliot, is incomparable in his depiction of a young man with social anxiety who is alienated from a superficial, materialistic society and wants to make a better world. I believe we will see a lot more of this actor in coming years.

Welcome back, my fledgling hackers! Let's continue to expand our knowledge of digital forensics, to provide you the skills necessary to be a digital forensic analyst or investigator, as well make you a better hacker overall. In your attempts to enter a system or network undetected, it is key to understand what a skilled forensic investigator can learn about you, the alleged hacker.

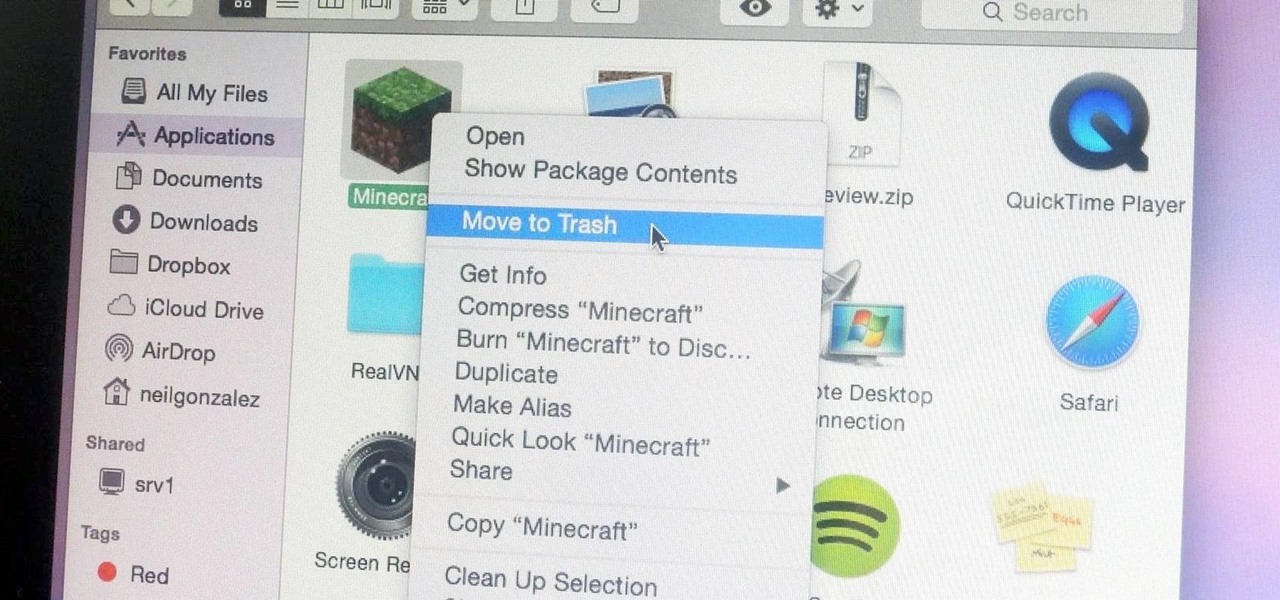
Uninstalling an app on your Mac isn't as straightforward as you would think. When you drag and drop an app into the Trash, then empty it, the main app itself may be gone, but many associated files and folders are left behind. So how do you get rid of them? There are a couple of ways.

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

Summer's coming, and that means burger season. Okay, never mind... every season is burger season. Burgers are universally loved; they're the one meal you can find at numerous fast food shacks and haute cuisine spots.

Welcome back, my aspiring hackers! Although this article may have been better placed first in this series, I doubt that anyone would have read it when just starting out studying Linux. Now, that you are well into your Linux studies and have some familiarity with how it operates, I'd like to take this moment to explain the philosophy around the Linux operating system.

Seldom in recent history has a cyber security event caused so much media stir (maybe because it happened to a media company?) and international relations upheaval. Cyber security breaches seem to take place daily of major corporations, but the Sony hack seems to have captured the American imagination and, for that matter, the whole world's attention.

Welcome back, my budding hackers! People often ask me, "Why are you training hackers? Isn't that illegal?" Although I usually give them a short version of this post, there are MANY reasons why YOU should be studying hacking.

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

We all know that it's important to drink water regularly throughout the day. After all, it has so many benefits, including flushing toxins out of the body and maintaining kidney health and good bowel movements. Turns out that's only part of the story. While being properly hydrated is key to maintaining overall health, it's also a big component of maintaining and even increasing cognitive ability. Plus, drinking enough water regularly can help you lose weight, if you know when to drink it and ...

Welcome back, my novice hackers! The worst thing that can happen to any hacker is being detected by a security admin, the security technologies (IDS, firewall, etc.), or a forensic investigator.

Welcome back, my aspiring hackers! Those of you who've been reading my tutorials for some time now know that I am adamant regarding the necessity of learning and using Linux to hack. There is no substitute, period.

When Google introduced their new launcher alongside the Nexus 5, one of the most innovative features was the "always listening" voice search, meaning that at any time you were on your home screen, triggering a Google search was as simple as saying "Okay, Google."

Welcome back, my hackers novitiates! As you read my various hacking tutorials, you're probably asking yourself, "What are the chances that this hack will be detected and that I'll land behind bars, disappointing my dear mother who already thinks I'm a loser?"

The very first text message was sent on December 3rd, 1992 by Neil Papworth, an engineer for Vodafone, and it simply said "Merry Christmas." He may have jumped the gun on the whole Christmas thing, but you trying coming up with the first text message in history!

TouchDevelop is a browser-based programming tool that allows anyone to build your own Windows 8 apps directly from any touchscreen device, including iPad, iPhone, Windows Phone, Android, PC and Macs. Once the script is created and the app proves to work, it can be placed in the Windows Store for free or purchase.

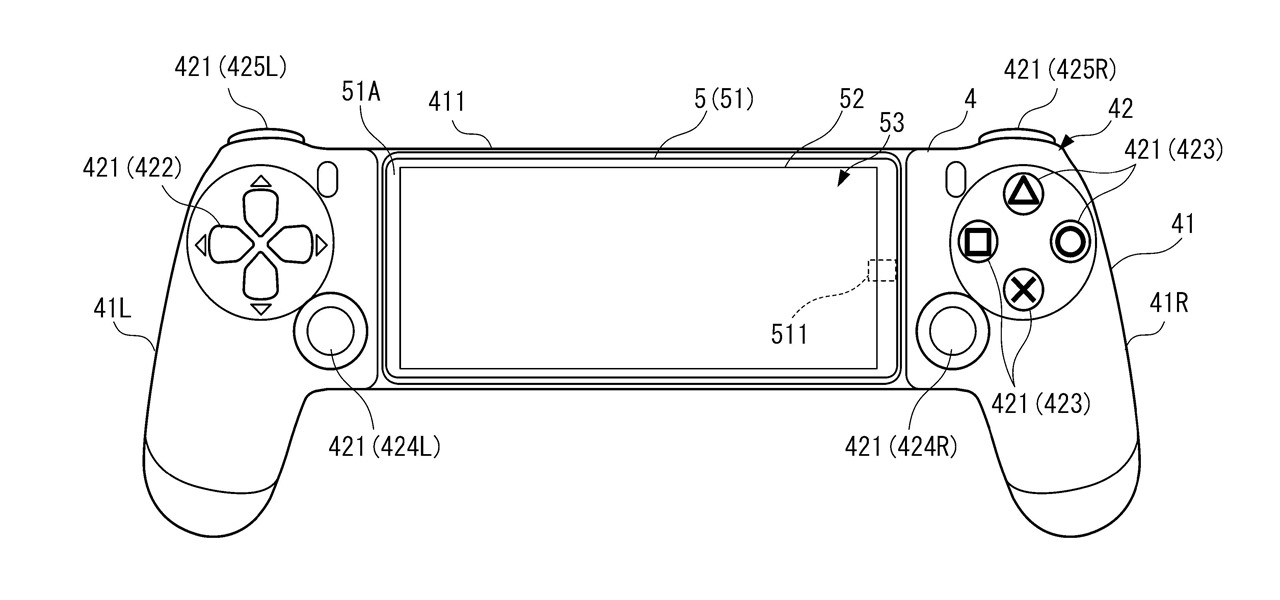
A new Sony patent shows the company doubling down on mobile gaming, and it could mean more advanced controller features for your iPhone or Android phone, similar to those in PlayStation's DualSense and DualShock controllers.

Snapchat parent company Snap has opened up its war chest to acquire yet another company that will play a role in its augmented reality ecosystem.