Every year, football fans get excited about the next crop of blue chip prospects joining their teams, from five-star high school recruits graduating to college to first-round rookies drafted into the NFL.
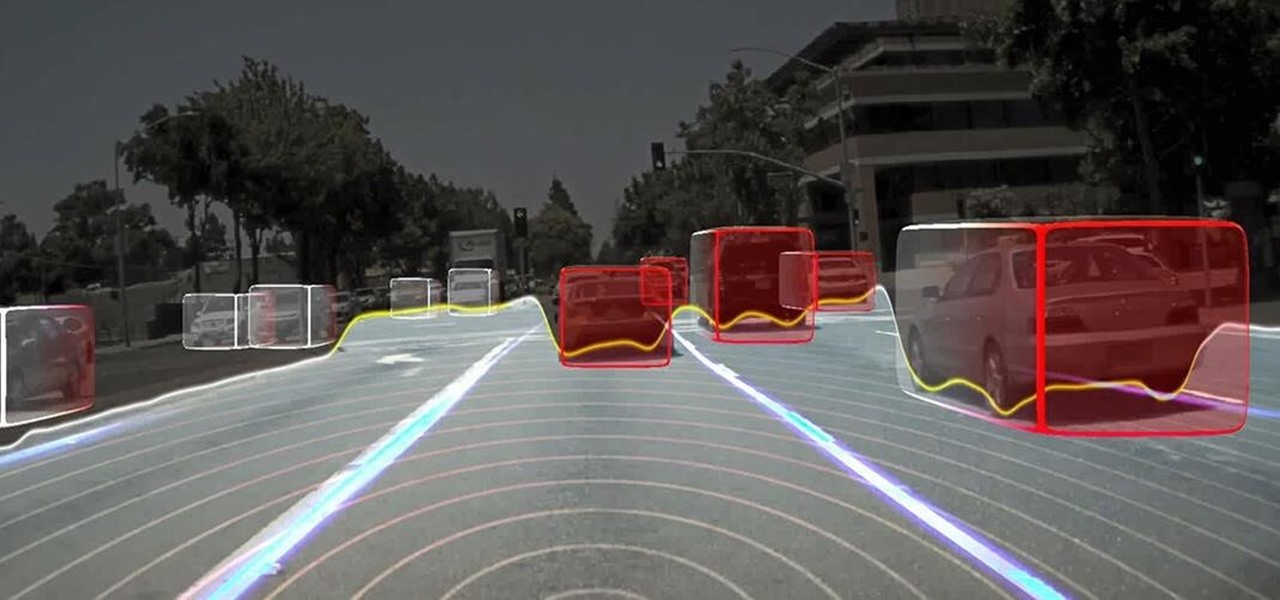
Long before Nvidia figured out how to embed neural networks in its graphics processor units (GPUs) for driverless vehicles, it and other chipmakers were already making the same kinds of devices for 3D games and other apps.

Facing claims of misappropriation of trade secrets and confidential information by Meta Company, DreamWorld, led by Meta's former employee, Zhangyi "Kevin" Zhong, has fired back with a motion to dismiss the lawsuit.
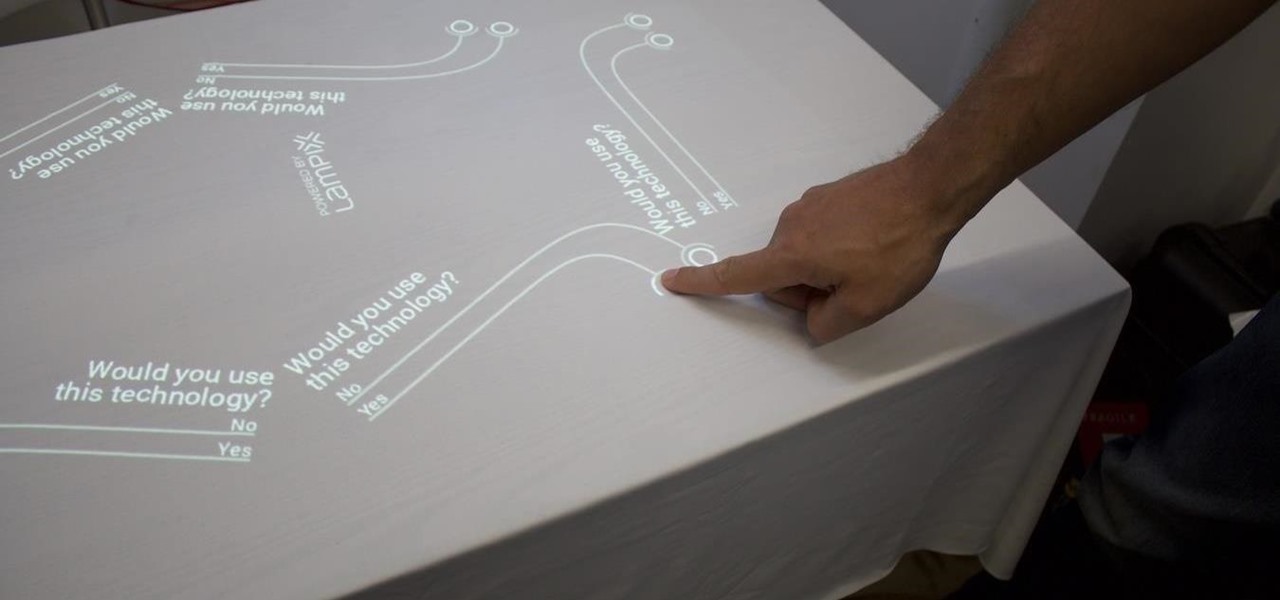
Over the past week, companies took a variety of approaches to investing in augmented reality. Lampix is backing its own effort to build an ecosystem for augmented reality platforms. Nokia and Xiaomi are teaming up on numerous fronts, potentially including augmented reality.

While restaurants and classrooms have enacted policies banning cell phones, one father has had enough of his kids' obsessive phone habits. Dr. Tim Farnum is now seeking to ban the sale of smartphones to children under 13.

We know that healthcare-related facilities can be fertile ground for antibiotic-resistant bacteria, but recent research suggests your produce aisle might be too.

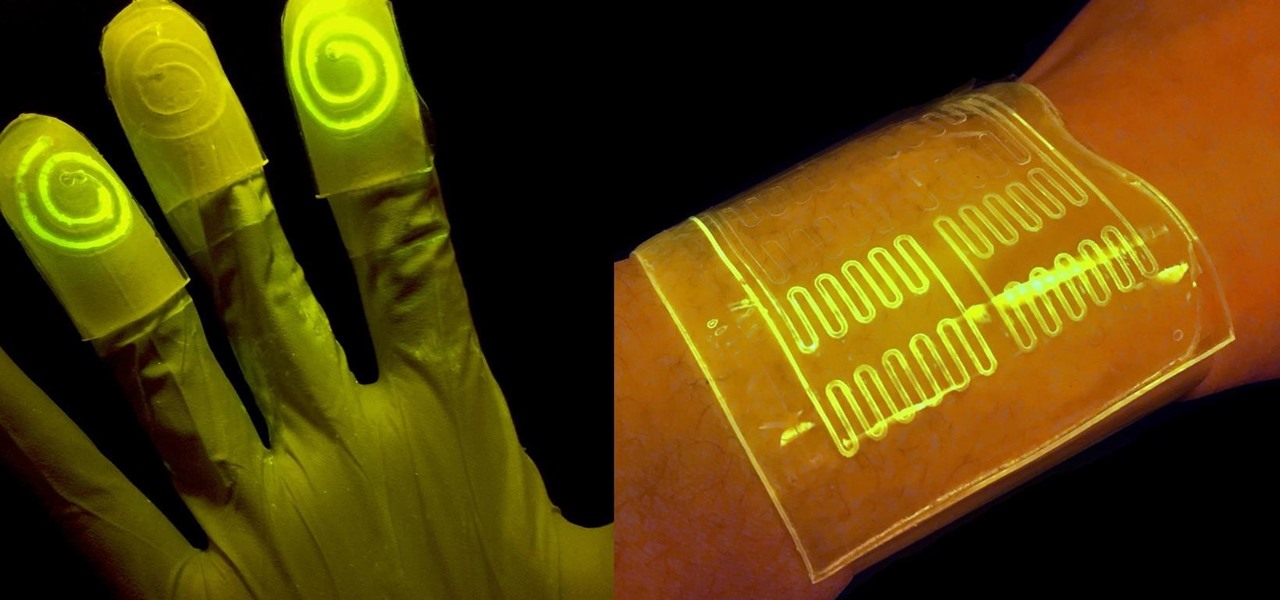
While at work, you notice your gloves changing color, and you know immediately that you've come in contact with dangerous chemicals. Bandages on a patient signal the presence of unseen, drug-resistant microbes. These are ideas that might have once seemed futuristic but are becoming a reality as researchers move forward with technology to use living bacteria in cloth to detect pathogens, pollutants, and particulates that endanger our lives.

Disney Parks are hard at work bringing the technology from a long time ago in a land far away to life for the opening of Star Wars Land parks in Anaheim and Orlando in 2019.

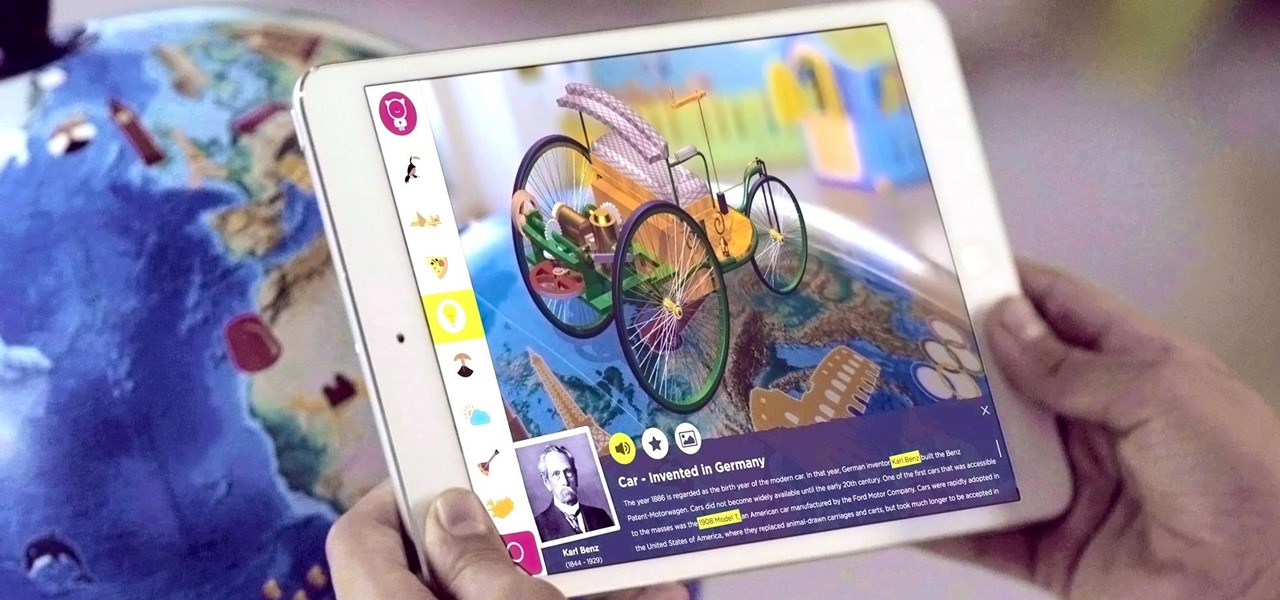
Globes used to be standard in households, usurped in many ways by modern mobile and desktop applications. But one company believes they can upgrade the globe for the 21st century.

Before many games make it to the US-based iOS App Store, they get "soft launched" in a smaller country to get real-world testing for bugs. It's a pilot program, so to speak, as countries like Vietnam or the Philippines have far fewer iPhone users than the US, thus offer a more controlled environment for developers to get feedback and zero-in on issues that may occur in a game's early development phases.

As drug-resistant bacteria become more commonplace, researchers are looking for new antibacterial strategies to disrupt disease-causing microbes. Some scientists are working to create new drugs, while others are trying out drug combinations. Another group, however, are ditching pharmaceuticals altogether and experimenting with non-drug alternatives.

If you really want to play Gran Turismo or Castlevania on the go, Sony's PlayStation Portable is a great way to do it. But it gets harder and harder to justify carrying around a PSP handheld gaming console when you've got an equally powerful Android phone in your pocket already. The PSP had a good 10 years before being discontinued, and your Android can pick up the slack now.

Starting with the Priv, BlackBerry's become an Android manufacturer. This move gives BlackBerry's phones access to Google's sizable app store, but it also presents several hurdles to keeping the security brand they've built intact.

Welcome back my, tenderfoot hackers! Many people come to Null Byte looking to hack Facebook without the requisite skills to do so. Facebook is far from unhackable, but to do so, you will need some skills, and skill development is what Null Byte is all about.

Welcome back, my budding hackers! Digital forensics is one of IT's most rapid-growing disciplines. All hackers should be familiar with digital forensics if for no other reason than to protect themselves. More than one hacker has been apprehended because they were unaware of the evidence trail they left behind.

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

Welcome back, my tenderfoot hackers! Web apps are often the best vector to an organization's server/database, an entry point to their entire internal network. By definition, the web app is designed to take an input from the user and send that input back to the server or database. In this way, the attacker can send their malicious input back to the servers and network if the web app is not properly secured.

Welcome back, my greenhorn hackers! Over the years, I have written many articles here on Null Byte chronicling the many the hacks of the NSA, including the recent hack of the Juniper Networks VPN. (By the way, my speculation in that article has proven to be correct. The NSA did embed a backdoor on those devices.)

Welcome back, my aspiring hackers! In this series, we continue to examine digital forensics, both to develop your skills as a forensic investigator and to avoid the pitfalls of being tracked by a forensic investigator.

First of all, I would like to apologize for a week long absents for the tutorials of this newly series, Raspberry Pi. But obviously I'm back and I present all you guys a article on turning your Raspberry Pi into a hacking platform. I'm gonna use the platform Kali Linux for the Raspberry Pi. I should note that I'm not gonna go into detail on how to install Kali Linux since OTW already has done a tutorial on how to turn your Raspberry Pi into a Hacking Pi. The point of this particular tutorial ...

Welcome back, my greenhorn hackers! The Holy Grail of any hacker is to develop a zero-day exploit—an exploit that has never been seen by antivirus (AV) and other software developers, as well as intrusion detection system (IDS) developers. In that way, you can exploit systems with your newly discovered vulnerability with impunity!

It should come as no surprise that, according to Details Magazine, nearly half of all people who make New Year's resolutions pledge to lose weight, eat healthier, and/or get fit. There are innumerable companies out there that are ready and willing to take advantage of this momentum: from those hocking "magic bullet" pills that will increase your energy or reduce your belly fat to the myriad shake- and juice-based diets that put you at a near-starvation calorie input—and will probably have you...

Managing hard drives in Linux is crucial to understanding your system and its operation as well as understanding the system you are exploiting or conducting a forensic analysis on. Linux has numerous commands that can provide us with information, control, and management of hard drives, and in this tutorial, we will examine a number of the most important ones.

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

One of my favorite things to do when I visit my parents is cook. Aside from the fact that I adore cooking with my mom, there's something comforting about returning to the kitchen that I first started playing in 20 years ago. Nearly all of the tools and appliances are the same ones that I used as a kid, and the familiarity is palpable.

Welcome back, my rookie hackers! As most of you know, Mr. Robot is probably the best hacker TV show ever! This is a great show about a cyber security engineer who is being enticed to hack the very corporation he's being paid to protect. This show is so good, I began a series to demonstrate how to do the hacks he uses in the show.

For many of you, this is common knowledge. But I still regularly see comments posted here and elsewhere asking, "This <AV bypass> doesn't work, because when I upload my payload to VirusTotal...."

Welcome back, my tenderfoot hackers! A number of you have written me telling me how much you enjoy the Mr. Robot series on USA Network. I am also a huge fan! If you haven't seen it yet, you should. It may be the best show on TV right now.

Coffee beans are one of my favorite things in the entire world. They smell intoxicatingly perfect. And when ground up and steeped in hot (or cold) water, they somehow taste even better than they smell.

As much as I love eating weird foods, when it comes to my favorite food, there is only one simple choice: cheese. Since cheese is my favorite to eat, it should come as no surprise that it's one of my favorites to make as well.

With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...

Whether it's terrorism or brain-hungry zombies you're neutralizing, first-person shooters are an awesome way to immerse yourself within a new world and kill some time with your iPad or iPhone. And with so many games available in this genre, we wanted to show off ten of our absolute favorites.

"Beer is proof that God loves us and wants us to be happy." We've all seen the quote, attributed to Benjamin Franklin, on numerous shirts, glasses, and bar signs. It's a good, if overused slogan. It makes one clear, indisputable point: beer is great, and life is better with it.

Welcome back, my novice hackers! In this continuing series on Metasploit basics, let's next look at a module that many aspiring hackers find useful—autopwn.

Welcome back, my amateur hackers! When you are using and administering Linux, it is important to be conversant in the use of the log files. As you know, log files are the repository for much information about our system, including errors and security alerts.

Welcome back, my hacker novitiates! Eluding and evading antivirus software and intrusion detection systems is one of the most critical tasks of the hacker. As soon as a new exploit is developed and discovered, the AV and IDS developers build a signature for the attack, which is then likely to be detected and prevented.

Welcome back, my hacker novitiates! As you know by now, the Metasploit Framework is one of my favorite hacking tools. It is capable of embedding code into a remote system and controlling it, scanning systems for recon, and fuzzing systems to find buffer overflows. Plus, all of this can be integrated into Rapid7's excellent vulnerability scanner Nexpose.

Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.

Welcome back, my novice hackers! New hackers often ask me the same question: "What is the easiest platform to hack?" My response is always the same—it is not a platform, but rather a particular piece of software that is easiest to hack, which is on nearly every client-side system. That software is Adobe Flash Player.