Google announced today that it's offering rewards to Android Pay users, and taking advantage of these deals could land you a free 2nd Generation Chromecast, among other prizes. The Tap 10 promotion is pretty self-explanatory: Tap to use Android Pay 10 times before February 29, 2016, and Google will give you a code to redeem a free Chromecast, free music, or both. You'll also be rewarded for Taps 1 through 9 as well. You'll receive a code for one music track from the Google Play Store for ever...

Welcome back, my aspiring hackers! In this series, we continue to examine digital forensics, both to develop your skills as a forensic investigator and to avoid the pitfalls of being tracked by a forensic investigator.

First of all, I would like to apologize for a week long absents for the tutorials of this newly series, Raspberry Pi. But obviously I'm back and I present all you guys a article on turning your Raspberry Pi into a hacking platform. I'm gonna use the platform Kali Linux for the Raspberry Pi. I should note that I'm not gonna go into detail on how to install Kali Linux since OTW already has done a tutorial on how to turn your Raspberry Pi into a Hacking Pi. The point of this particular tutorial ...

Virtual reality technology company Oculus VR announced that it will begin accepting preorders for its long-awaited Oculus Rift headset beginning Wednesday, January 6th, at 8 a.m. Pacific time.

It should come as no surprise that, according to Details Magazine, nearly half of all people who make New Year's resolutions pledge to lose weight, eat healthier, and/or get fit. There are innumerable companies out there that are ready and willing to take advantage of this momentum: from those hocking "magic bullet" pills that will increase your energy or reduce your belly fat to the myriad shake- and juice-based diets that put you at a near-starvation calorie input—and will probably have you...

Managing hard drives in Linux is crucial to understanding your system and its operation as well as understanding the system you are exploiting or conducting a forensic analysis on. Linux has numerous commands that can provide us with information, control, and management of hard drives, and in this tutorial, we will examine a number of the most important ones.

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

Welcome everyone to the second part of the How To Become Anonymous online series. Today I will (briefly) introduce you to what has been defined "The most secure OS" : Tails a Debian based OS. (Official website: https://tails.boum.org/)

YouTube, the popular video streaming website owned by Google, announced on October 21st that it will be launching a new subscription service titled "YouTube Red" for $9.99 a month. Under the membership, subscribers will be able to watch videos without ads. Yup, all videos—from music to trailers to gaming and everything in-between—completely ad-free. Additionally, individuals can save videos to watch offline on their mobile devices as well as play videos in the background.

Well, here we are. We've come a long way, we really have. Watching this community grow has been amazing. Well, before I start babbling on about the community, let me get to the point...

If you own an iPad 2, a 3rd or 4th generation model, or original iPad mini, then you won't be able to utilize the new multitasking elements introduced in iOS 9. Although many iPads can use the Slide Over and Picture-in-Picture features, only the iPad Air 2, iPad mini 4, and iPad Pro have the ability to perform Split View.

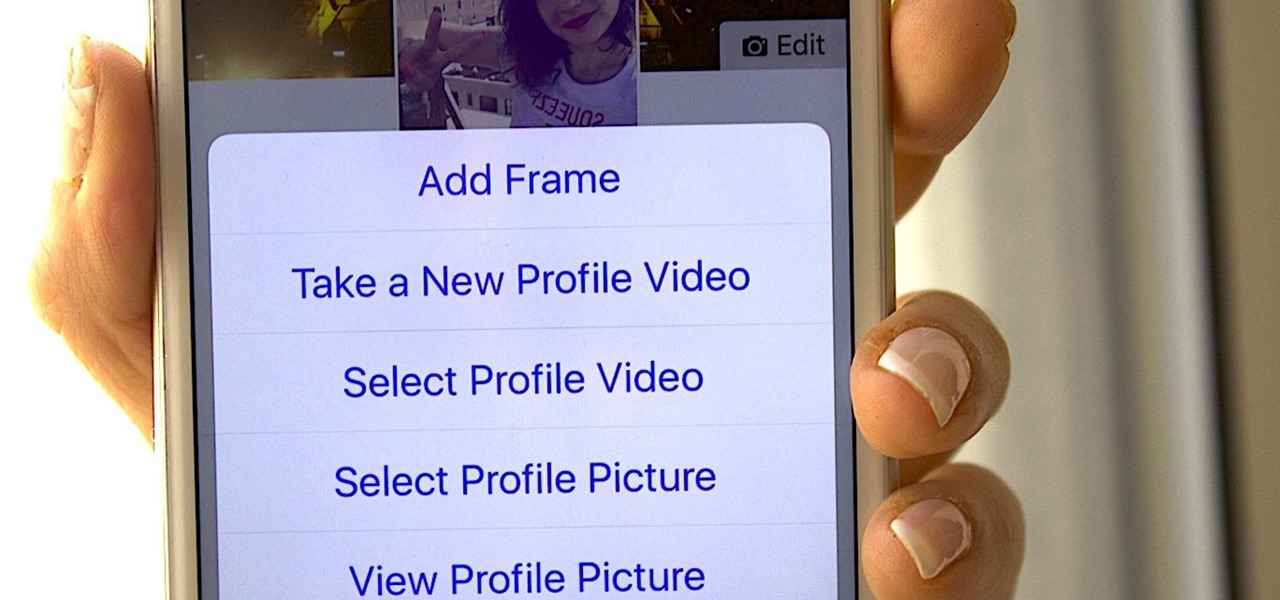
Instead of the still image we've been accustomed to since the inception of Facebook, you also have the option to apply a seven-second video as your profile image, which definitely mixes things up a bit with GIF-like animations. Best of all, this can be done straight from your iPhone or Android device.

One of my favorite things to do when I visit my parents is cook. Aside from the fact that I adore cooking with my mom, there's something comforting about returning to the kitchen that I first started playing in 20 years ago. Nearly all of the tools and appliances are the same ones that I used as a kid, and the familiarity is palpable.

Welcome back, my rookie hackers! As most of you know, Mr. Robot is probably the best hacker TV show ever! This is a great show about a cyber security engineer who is being enticed to hack the very corporation he's being paid to protect. This show is so good, I began a series to demonstrate how to do the hacks he uses in the show.

For many of you, this is common knowledge. But I still regularly see comments posted here and elsewhere asking, "This <AV bypass> doesn't work, because when I upload my payload to VirusTotal...."

Welcome back, my tenderfoot hackers! A number of you have written me telling me how much you enjoy the Mr. Robot series on USA Network. I am also a huge fan! If you haven't seen it yet, you should. It may be the best show on TV right now.

Coffee beans are one of my favorite things in the entire world. They smell intoxicatingly perfect. And when ground up and steeped in hot (or cold) water, they somehow taste even better than they smell.

As much as I love eating weird foods, when it comes to my favorite food, there is only one simple choice: cheese. Since cheese is my favorite to eat, it should come as no surprise that it's one of my favorites to make as well.

With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...

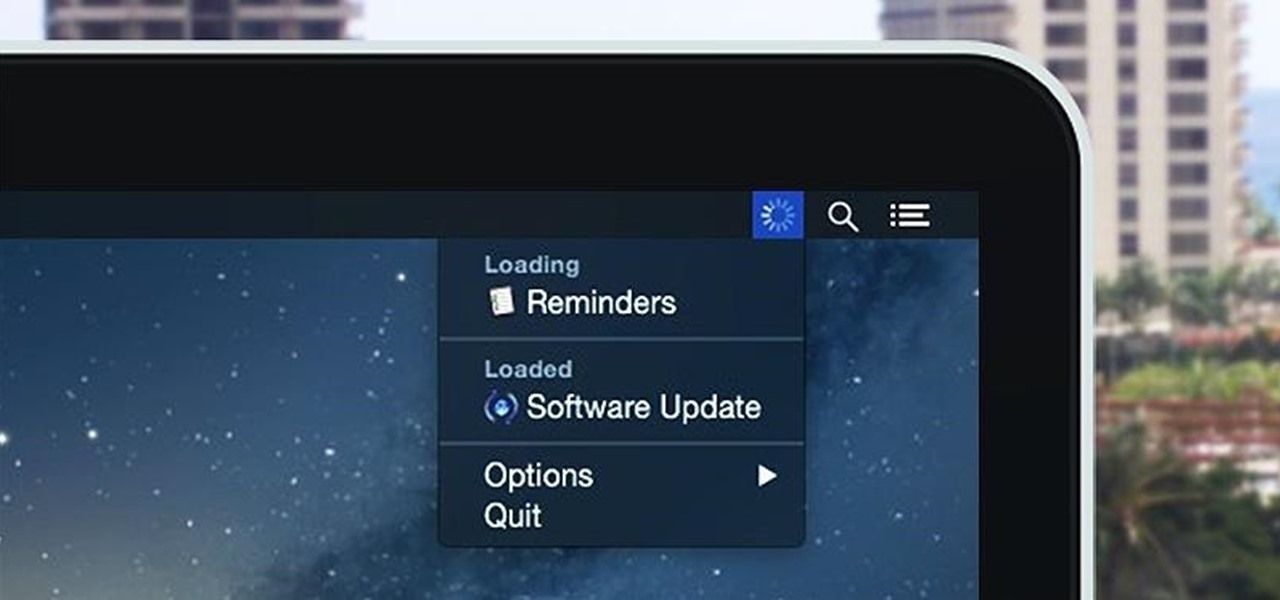
Monitoring your Mac with widgets can be the first step in identifying bandwidth issues, but finding the root of the problem can be a completely different story. Usually you will have to open up Activity Monitor in Mac OS X to look for apps hogging your bandwidth, but with Loading, you can get a detailed data usage report right from your menu bar.

"Beer is proof that God loves us and wants us to be happy." We've all seen the quote, attributed to Benjamin Franklin, on numerous shirts, glasses, and bar signs. It's a good, if overused slogan. It makes one clear, indisputable point: beer is great, and life is better with it.

Welcome back, my novice hackers! In this continuing series on Metasploit basics, let's next look at a module that many aspiring hackers find useful—autopwn.

I was so Scared to get this procedure done. I let this Callus give me Pain for about 1 year.

Welcome back, my amateur hackers! When you are using and administering Linux, it is important to be conversant in the use of the log files. As you know, log files are the repository for much information about our system, including errors and security alerts.

YouTube and the National Football League have announced a partnership that should greatly improve the online experience for gridiron fans. In a posting on their official blog, YouTube outlines a deal that will bring NFL video clips to their immensely popular site while bumping official NFL pages up to the top of relevant Google search results.

An Amazon Prime subscription offers free two-day shipping and discounted rates on many Amazon products, while at the same time granting users access to Amazon's Instant Video library. While this service normally runs $100 per year, Amazon CEO Jeff Bezos announced today that the company will be offering a $28 discount on this price for one day only.

In a long-awaited move, the popular messaging platform WhatsApp has finally made its official web debut. Desktop and laptop owners will be happy to know that they can now message their favorite contacts directly from their computers, without the need to install additional apps.

Welcome back, my hacker novitiates! Eluding and evading antivirus software and intrusion detection systems is one of the most critical tasks of the hacker. As soon as a new exploit is developed and discovered, the AV and IDS developers build a signature for the attack, which is then likely to be detected and prevented.

Animal lovers, especially dog owners, know that pets are a part of the family, but it's often incredibly frustrating to know if and when something just isn't right with our furry companions. If you're out and about most of the day, your dog will be so happy to see you when you come home that you may have no idea they were tired and listless all day long, which can be a sign of health problems for your pup. This is where FitBark comes in.

Welcome back, my hacker novitiates! As you know by now, the Metasploit Framework is one of my favorite hacking tools. It is capable of embedding code into a remote system and controlling it, scanning systems for recon, and fuzzing systems to find buffer overflows. Plus, all of this can be integrated into Rapid7's excellent vulnerability scanner Nexpose.

Coffee shops are great places to unwind and get some free Wi-Fi, but all the bandwidth in the world can be ruined by someone being a noisy jerk. I usually start blasting music through my headphones whenever that happens, but that isn't always the most ideal situation, especially if I'm trying to study or work.

Coffee lovers take their beverage of choice seriously. Some even go out of their way to find their own kopi luwak (cat poop coffee) just to see if it lives up to all the hype.

When it comes to subscription-based music streaming services, the conversation doesn't go much further than Spotify and Google Play Music (previously called "All Access"). Both services are essentially the same aside from slightly different catalogues and social options, and they both run ten bucks a month for unlimited music streaming and offline track saving (although Spotify does have a free, ad-supported service).

Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.

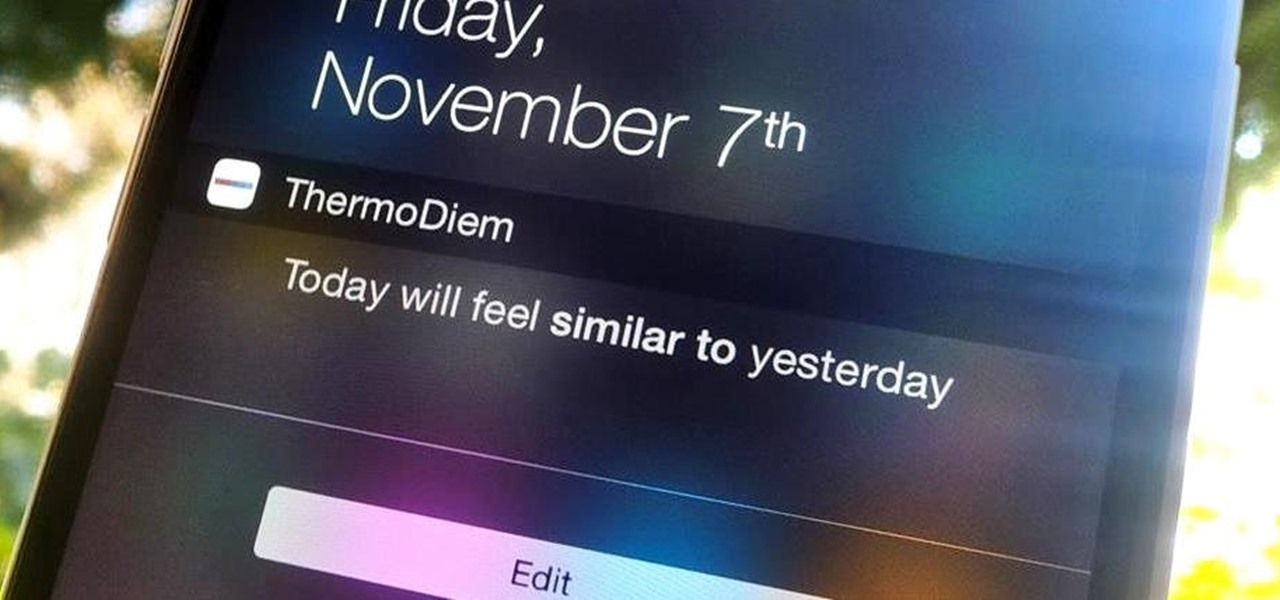
When I get weather information, I prefer to receive it in a straight-forward, minimalistic fashion. Living in California, I could care less about wind speeds, humidity, or any other calculations that I can't analyze in a second. I essentially use the information to help decide whether I'll be wearing shorts or pants on a given day, so give it to me bluntly.

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.

You have to give Amazon credit where it's due. Aside from being a retail powerhouse, they're not averse to dipping their feet in new and sometimes strange areas. Take Fresh, the first major effort at bringing your local goods directly to you in same-day fashion. Or Amazon Dash, which aimed to make adding items to your cart a breeze by allowing for scanning goods or speaking them into a small, hand-held device. Along these lines, the company has now introduced an invite-only product, the Amazo...

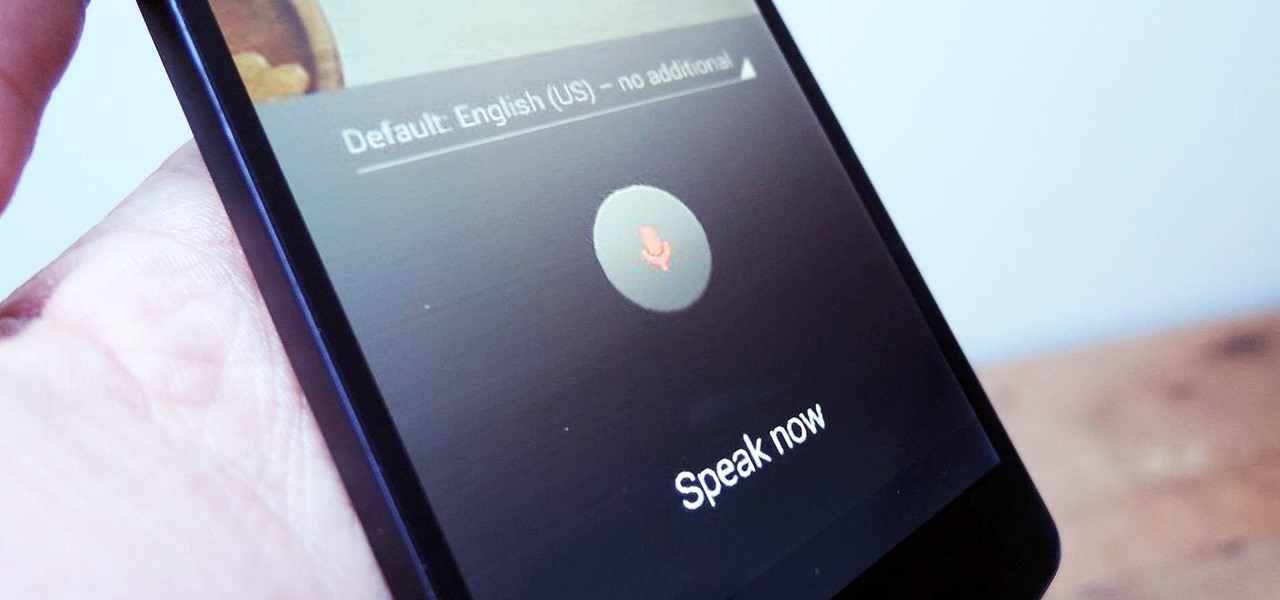
As smartphones become increasingly integral parts of our lives, so does data throttling. Personally, I try to save data any way that I can, so to stave off unnecessary usage, I use the GoogleOfflineVoice to limit the amount of data consumed by voice typing.

Welcome back, my novice hackers! New hackers often ask me the same question: "What is the easiest platform to hack?" My response is always the same—it is not a platform, but rather a particular piece of software that is easiest to hack, which is on nearly every client-side system. That software is Adobe Flash Player.

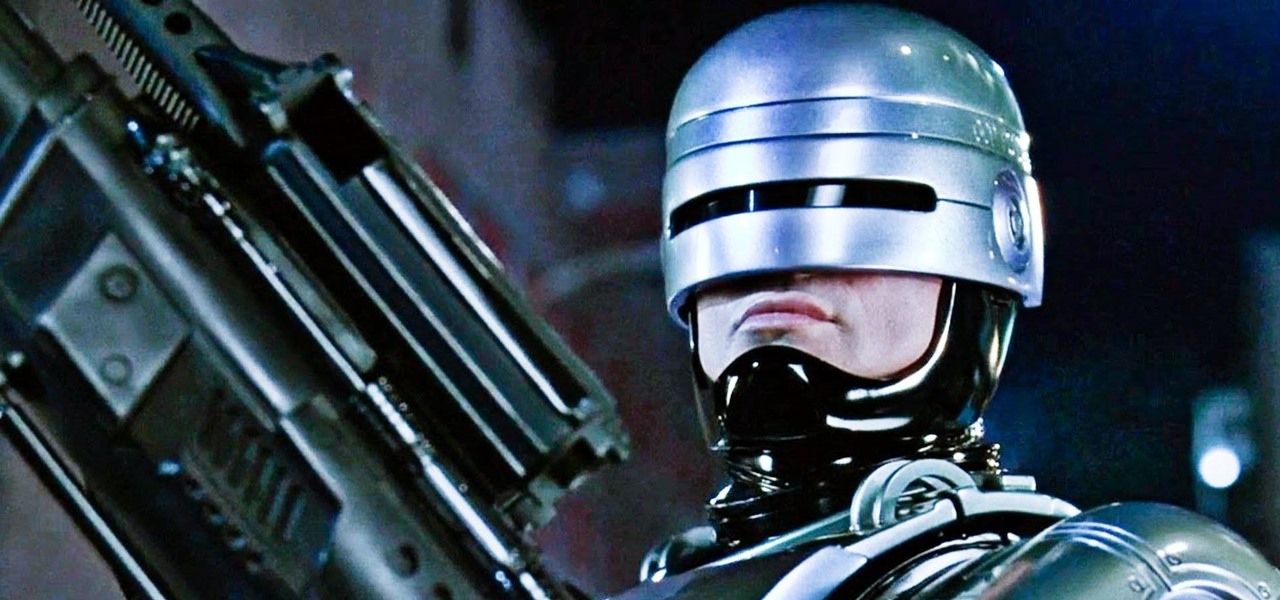
"Dead or alive, you're coming with me!" That iconic quote from the 1987 movie RoboCop was repeated by kids like me for years. The 2014 reboot introduced the baddest robot-cop on the planet to new audiences worldwide. While it didn't live up to the amazingly high expectations set by its predecessors, RoboCop 2014 did show off some newly upgraded gear. The modern look is cool and all, but rolling to a party rocking the 1987 helmet with the retro visor cannot be beat. With Halloween coming up, i...