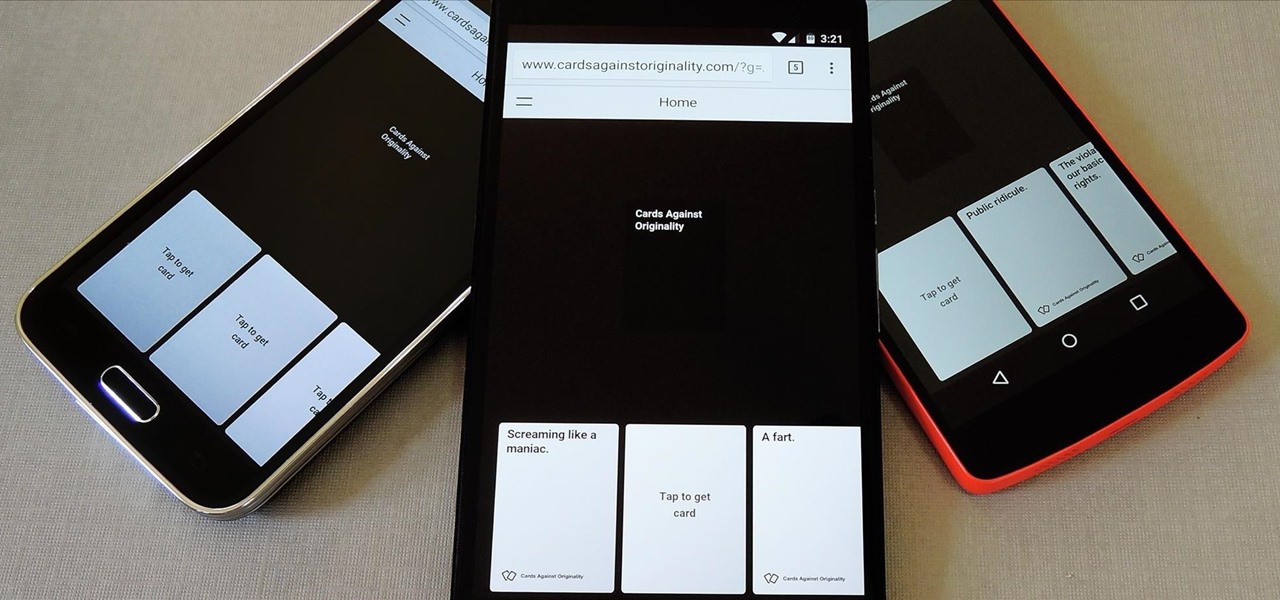
Welcome back, my aspiring hackers! In this series, we continue to examine digital forensics, both to develop your skills as a forensic investigator and to avoid the pitfalls of being tracked by a forensic investigator.

First of all, I would like to apologize for a week long absents for the tutorials of this newly series, Raspberry Pi. But obviously I'm back and I present all you guys a article on turning your Raspberry Pi into a hacking platform. I'm gonna use the platform Kali Linux for the Raspberry Pi. I should note that I'm not gonna go into detail on how to install Kali Linux since OTW already has done a tutorial on how to turn your Raspberry Pi into a Hacking Pi. The point of this particular tutorial ...

Welcome back, my greenhorn hackers! The Holy Grail of any hacker is to develop a zero-day exploit—an exploit that has never been seen by antivirus (AV) and other software developers, as well as intrusion detection system (IDS) developers. In that way, you can exploit systems with your newly discovered vulnerability with impunity!

It should come as no surprise that, according to Details Magazine, nearly half of all people who make New Year's resolutions pledge to lose weight, eat healthier, and/or get fit. There are innumerable companies out there that are ready and willing to take advantage of this momentum: from those hocking "magic bullet" pills that will increase your energy or reduce your belly fat to the myriad shake- and juice-based diets that put you at a near-starvation calorie input—and will probably have you...

Managing hard drives in Linux is crucial to understanding your system and its operation as well as understanding the system you are exploiting or conducting a forensic analysis on. Linux has numerous commands that can provide us with information, control, and management of hard drives, and in this tutorial, we will examine a number of the most important ones.

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

With the explosive popularity of both Thor himself and The Avengers, Thor is an obvious good choice for a Halloween costume. But you don't have to opt for one of the pricey, pre-made costume choices found in every Halloween store in every city. Instead, craft your own in just a few steps, saving yourself money in the process.

One of my favorite things to do when I visit my parents is cook. Aside from the fact that I adore cooking with my mom, there's something comforting about returning to the kitchen that I first started playing in 20 years ago. Nearly all of the tools and appliances are the same ones that I used as a kid, and the familiarity is palpable.

Welcome back, my rookie hackers! As most of you know, Mr. Robot is probably the best hacker TV show ever! This is a great show about a cyber security engineer who is being enticed to hack the very corporation he's being paid to protect. This show is so good, I began a series to demonstrate how to do the hacks he uses in the show.

For many of you, this is common knowledge. But I still regularly see comments posted here and elsewhere asking, "This <AV bypass> doesn't work, because when I upload my payload to VirusTotal...."

Shrimp is one of my all-time favorite foods. It's versatile, delicious, and incredibly fun to use in the kitchen.

Thanks to the internet and its increasingly lack of privacy, secrets don't even seem safe in our own homes anymore. So how do you hide your secrets, stash your cash, or keep your valuable jewelry out of sight where no one can find it? Well, the answer might be right above you... if you're standing under the threshold of a door, that is.

Welcome back, my tenderfoot hackers! A number of you have written me telling me how much you enjoy the Mr. Robot series on USA Network. I am also a huge fan! If you haven't seen it yet, you should. It may be the best show on TV right now.

More than likely, the first thing you noticed after booting up Windows 10 initially was a handful of new items in the taskbar across the bottom of your screen. Windows 8 users were probably glad to see the Start menu button back from the dead, but just to the right of that Windows logo are a pair of brand new entries.

On the whole, Windows 10 is vastly different than its predecessors, but there's not any one big change that distinguishes it from Windows 7 or 8. On the contrary, it's a series of small tweaks and optimizations that makes this version such a departure from previous iterations.

Coffee beans are one of my favorite things in the entire world. They smell intoxicatingly perfect. And when ground up and steeped in hot (or cold) water, they somehow taste even better than they smell.

As much as I love eating weird foods, when it comes to my favorite food, there is only one simple choice: cheese. Since cheese is my favorite to eat, it should come as no surprise that it's one of my favorites to make as well.

With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

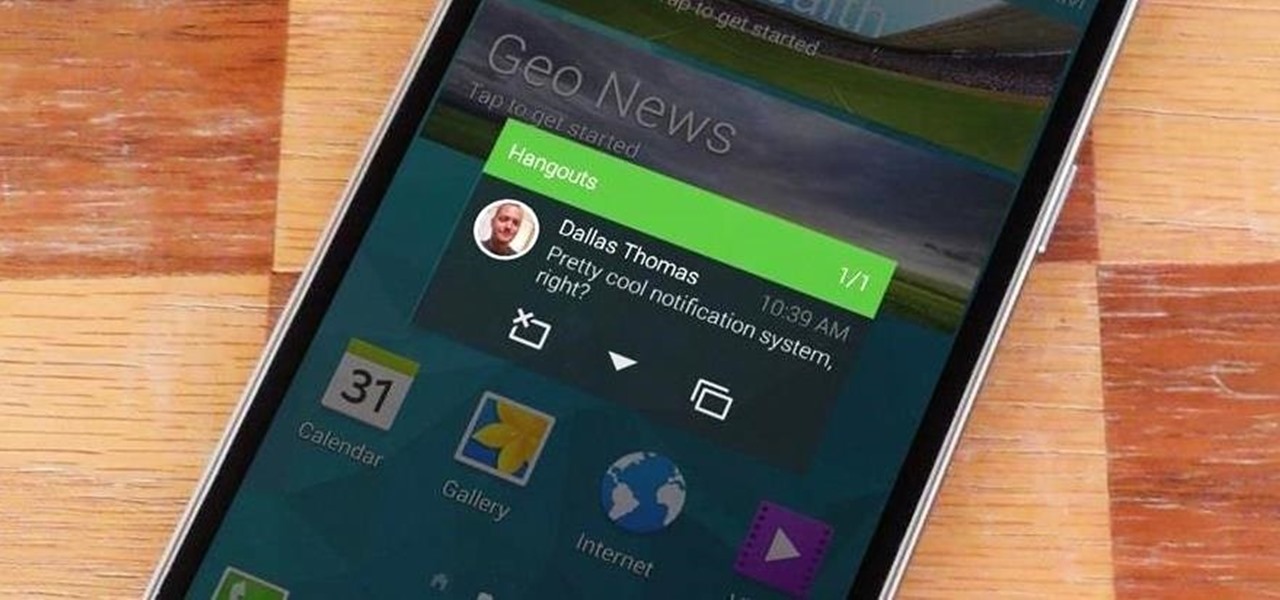
Android Lollipop, introduced an array of new features and aesthetics that pleased many loyal users. One of those additions being the new heads-up notifications. Taking subtle inspiration from iOS, these notifications are visually appealing and can be easily dismissed or expanded, but they do require that you take an action before they go away immediately. Of course, you can always wait 10 seconds for them to disappear, but that can be really annoying if you're in the middle of a game or editi...

Whether it's terrorism or brain-hungry zombies you're neutralizing, first-person shooters are an awesome way to immerse yourself within a new world and kill some time with your iPad or iPhone. And with so many games available in this genre, we wanted to show off ten of our absolute favorites.

Amazingly enough, some of us still have to worry about exceeding our monthly mobile data limits. You'd figure carriers would have given the customers what they want by now by offering truly unlimited plans, but with two conglomerates sitting atop the U.S. cellular market with fat pocketbooks that make for limitless lobbying, they can basically do whatever they want.

"Beer is proof that God loves us and wants us to be happy." We've all seen the quote, attributed to Benjamin Franklin, on numerous shirts, glasses, and bar signs. It's a good, if overused slogan. It makes one clear, indisputable point: beer is great, and life is better with it.

While some of the additions to the emoji keyboard in iOS 8.3 have been criticized for actually doing the opposite of their intended purpose, they've been well received overall. But the biggest winner of the new emojis was one that actually wasn't even released—the "Vulcan salute" emoji.

The shooting of Walter Scott (who was unarmed) has been dominating the news these past few weeks. Scott, who ran away from police officer Michael Slager after a routine traffic stop, was shot in the back and pronounced dead shortly thereafter. Unlike similar cases where a cop shoots an unarmed person, the police officer involved in this particular shooting is currently in jail, facing a potential murder charge.

Since the Nexus Player is an Android device at heart, there are already several internet browsers that can be used on the streaming set-top box. Chrome, Firefox, and a few others will run perfectly fine, but the trouble with these is that you need a mouse to use them.

Show your significant other just how much you love them by surprising him or her with one of life's most precious, romantic gifts—bacon! Best thing is, this passionate treat works for any day of the year (Valentine's Day, a first date, anniversary, etc.), since love and bacon go hand in hand.

Cards Against Humanity is a popular party game with good old-fashioned raunchy adult themes that go quite well with a few alcoholic beverages. Up until now, though, you had to either print out a set of cards or order the official deck to play—unless, of course, all players happened to have devices that sported the same operating system.

One of the best things about talking to other people who love food is that they point you to weirdly beautiful ingredients, like this: No, that's not an escapee from Middle Earth you're seeing. It's one of Mother Nature's best attempts at making fractals come alive into a golden spiral: the Romanesco (sometimes called fractal broccoli, broccoflower, or Romanesque cauliflower). Here's another view: So Just What Is It & What Does It Taste Like?

Welcome back, my amateur hackers! When you are using and administering Linux, it is important to be conversant in the use of the log files. As you know, log files are the repository for much information about our system, including errors and security alerts.

Normally, if you want to close all of the open apps on your Mac, you'd have to either quit them all one by one or restart, shut down, or log out while making sure to deselect “Reopen windows when logging back in." The latter option is great, but it doesn't always work in Mac OS X, and what if you don't want to restart, shut down, or log out?

Welcome back, my hacker novitiates! Eluding and evading antivirus software and intrusion detection systems is one of the most critical tasks of the hacker. As soon as a new exploit is developed and discovered, the AV and IDS developers build a signature for the attack, which is then likely to be detected and prevented.

By now, everybody knows that overcharging a battery will reduce its overall life span. This is why many smartphone manufacturers recommend that you charge your device to 100%, then unplug it immediately. Some even go so far as to automatically stop charging when the device is fully juiced, although not all devices have this functionality.

There are few sounds that actually make me cringe whenever I hear them: silverware scraping on a plate, nails scratching on a chalkboard, and piercing high-frequency tones. While the former two terrors require some physical hardware, sending out high-frequency sounds is as easy as downloading an app.

Welcome back, my hacker novitiates! As you know by now, the Metasploit Framework is one of my favorite hacking tools. It is capable of embedding code into a remote system and controlling it, scanning systems for recon, and fuzzing systems to find buffer overflows. Plus, all of this can be integrated into Rapid7's excellent vulnerability scanner Nexpose.

Did you know that cookies are one of the most popular holiday desserts? Sugar cookies in particular are so easy to make and easy to decorate. They are the perfect treat for your office, friends, and family…or just yourself!

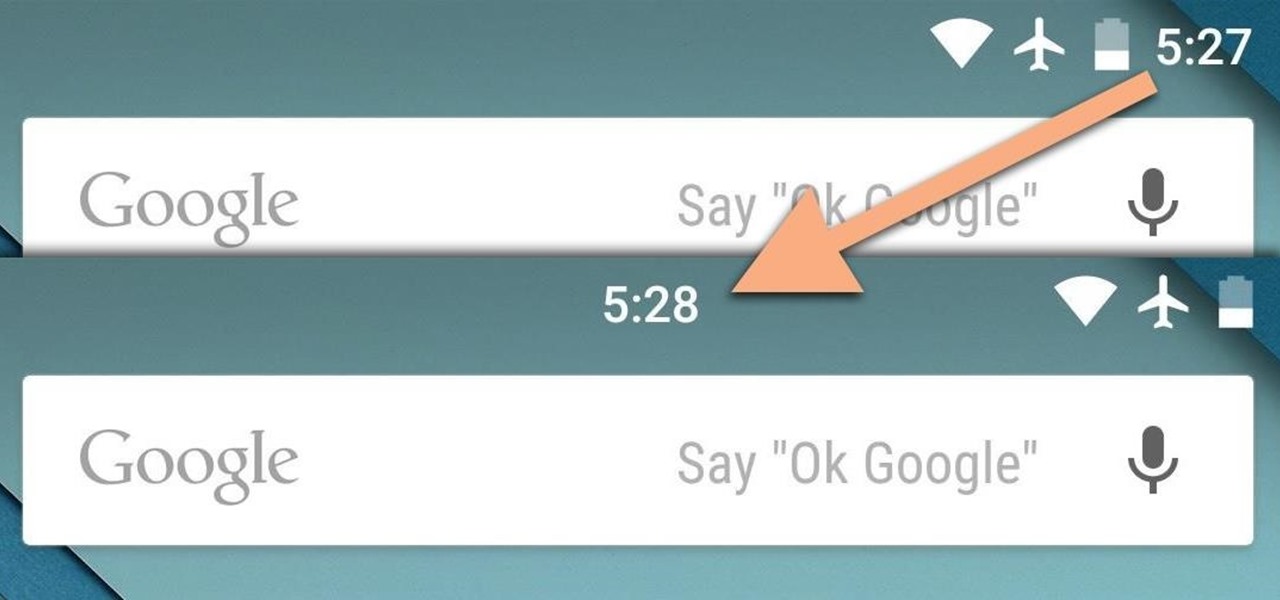
If you're like me, things just seem to look better when they're symmetrical. While Android's status bar icons are indeed weighted against the notifications that show up on the left side of this area, the balance still seems skewed to the right.

Notifications are an integral part of our day-to-day smartphone usage. They allow us to easily see and act upon all of the latest information that comes our way. Well, most of the time, that is.

Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.