Welcome back, my novice hackers! New hackers often ask me the same question: "What is the easiest platform to hack?" My response is always the same—it is not a platform, but rather a particular piece of software that is easiest to hack, which is on nearly every client-side system. That software is Adobe Flash Player.
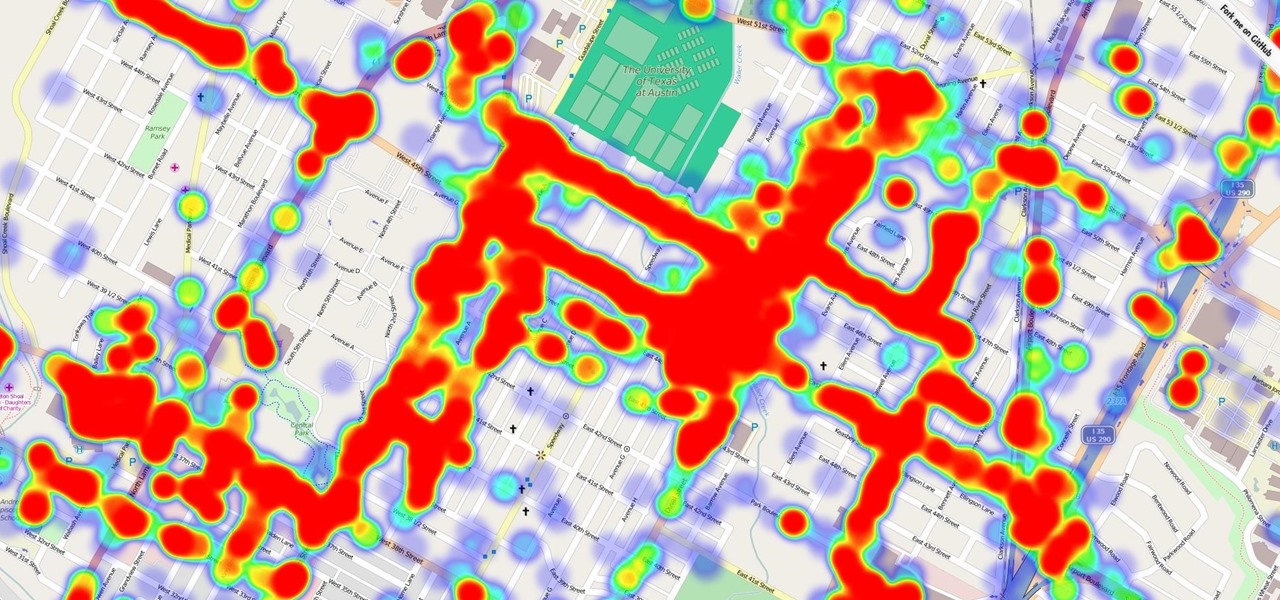
With an Android device left at its default settings, your location history is automatically recorded. You can view and manage this data, but the simple interface of points plotted on a map leaves a lot to be desired.

Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective.

Yellow buses are beginning to trickle into traffic. Retailers are pushing pens, pencils, and notebooks. Grumbling Facebook statuses run rampant through your feed. Surely you recognize the signs—school is starting. For some, it already has.
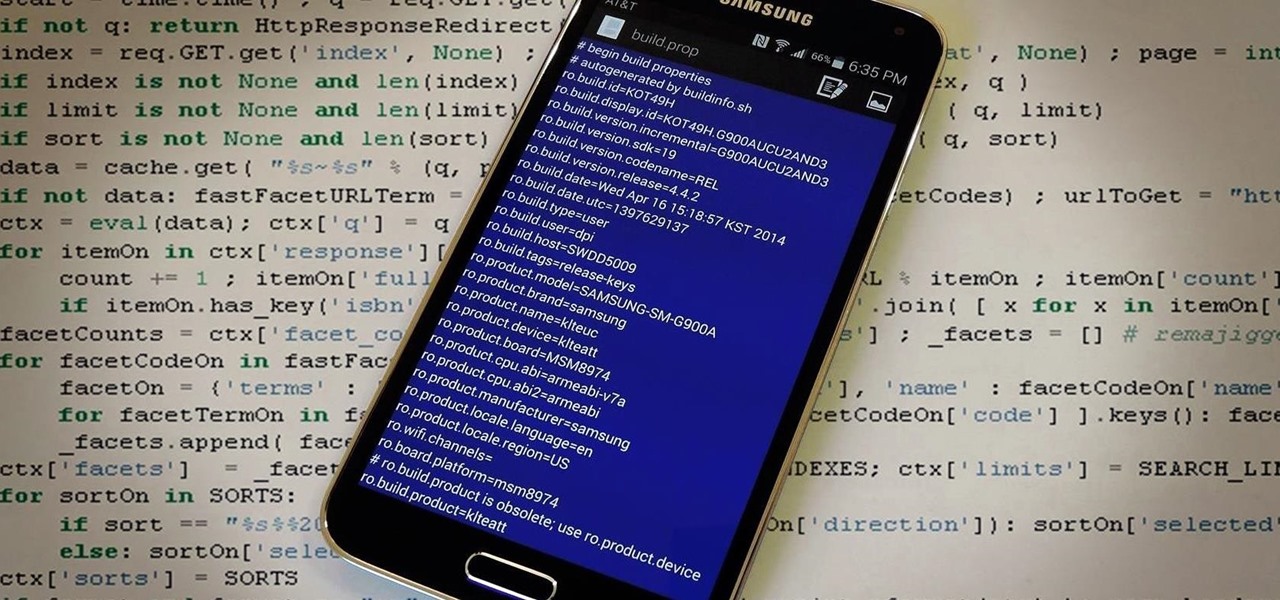
The build.prop file in an Android device is home to many system-level values and settings. Everything from screen density to video recording quality is covered in this file, and people have been editing these entries to get new functionality and better performance since Android has existed.
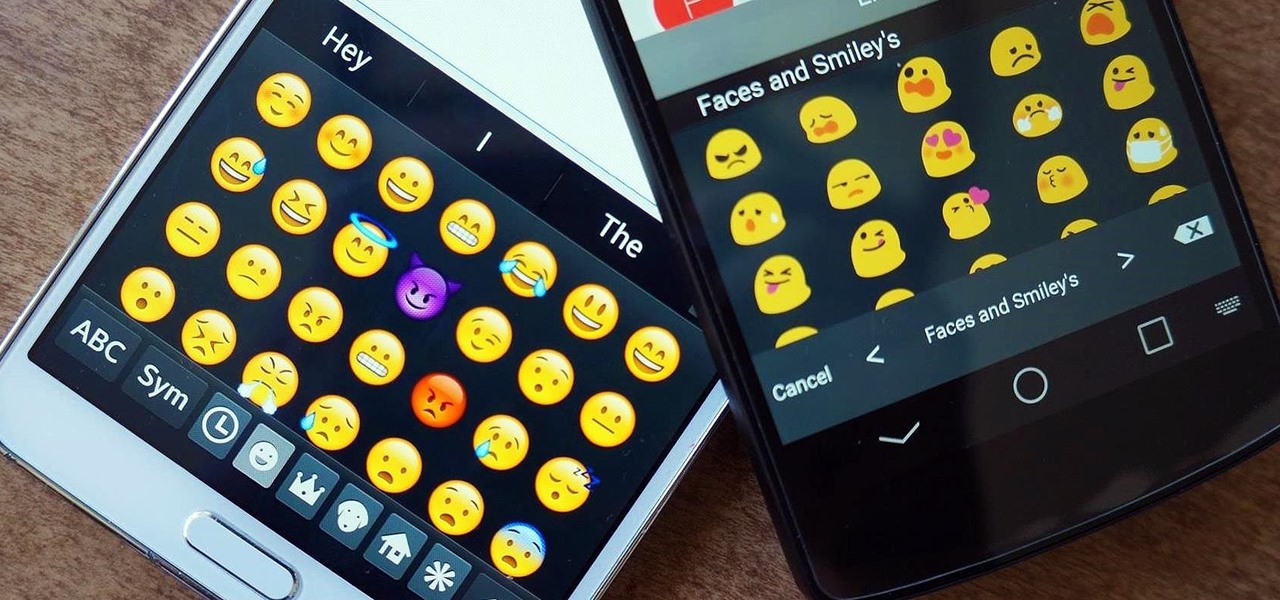
Emoji icons can vary greatly from manufacturer to manufacturer. Normally, this isn't be a problem, unless all of your friends use iPhones and you're the only one that receives a different icon than the rest of your group. And for the record, they don't all correspond to each other, which only makes using them that much more difficult.

We tend to assume that eating is mostly a physical act, but the mind has so much to do with the choices we make.

Welcome back, my hacker apprentices! Last week, I started off my password cracking series with an introduction on the principles and technologies involved in the art of cracking passwords. In past guides, I showed some specific tools and techniques for cracking Windows, online, Wi-Fi, Linux, and even SNMP passwords. This series is intended to help you hone your skills in each of these areas and expand into some, as yet, untouched areas.

Welcome back, my novice hackers! In a recent tutorial, I showed you how to use shikata_ga_nai to change the signature of a payload to evade detection by security devices (firewalls, IDS, etc.) and AV software.

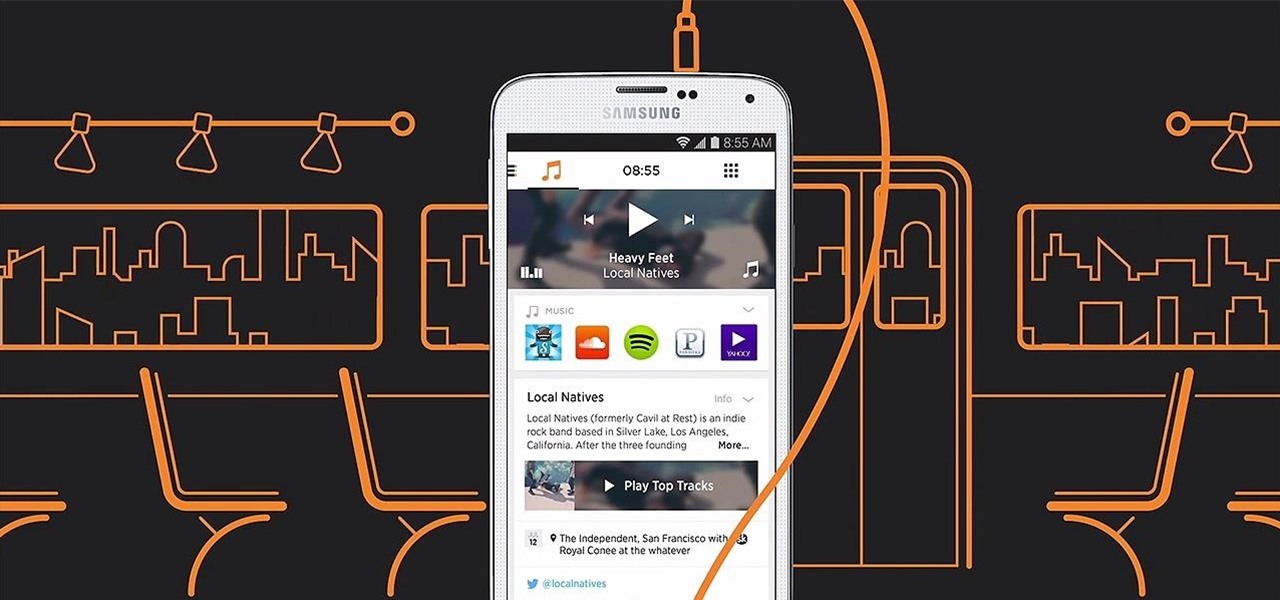
When Yahoo! purchased the home screen replacement app Aviate back in January, many were wondering if the internet giant intended to continue development of the launcher or if the transaction was just another acqui-hire.

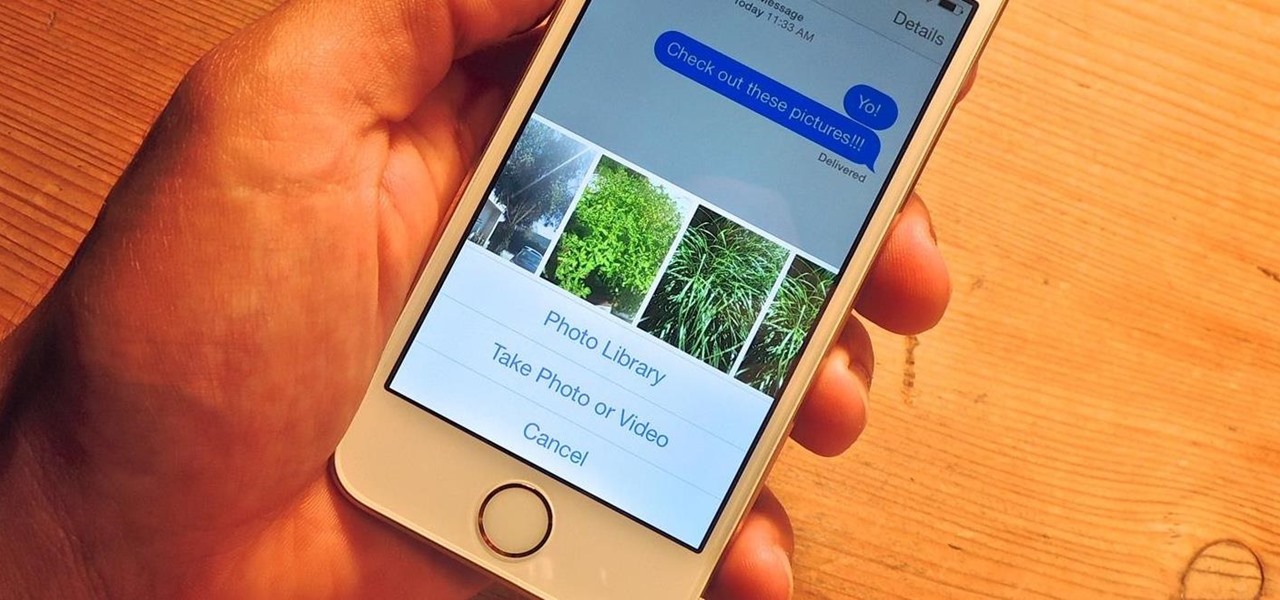
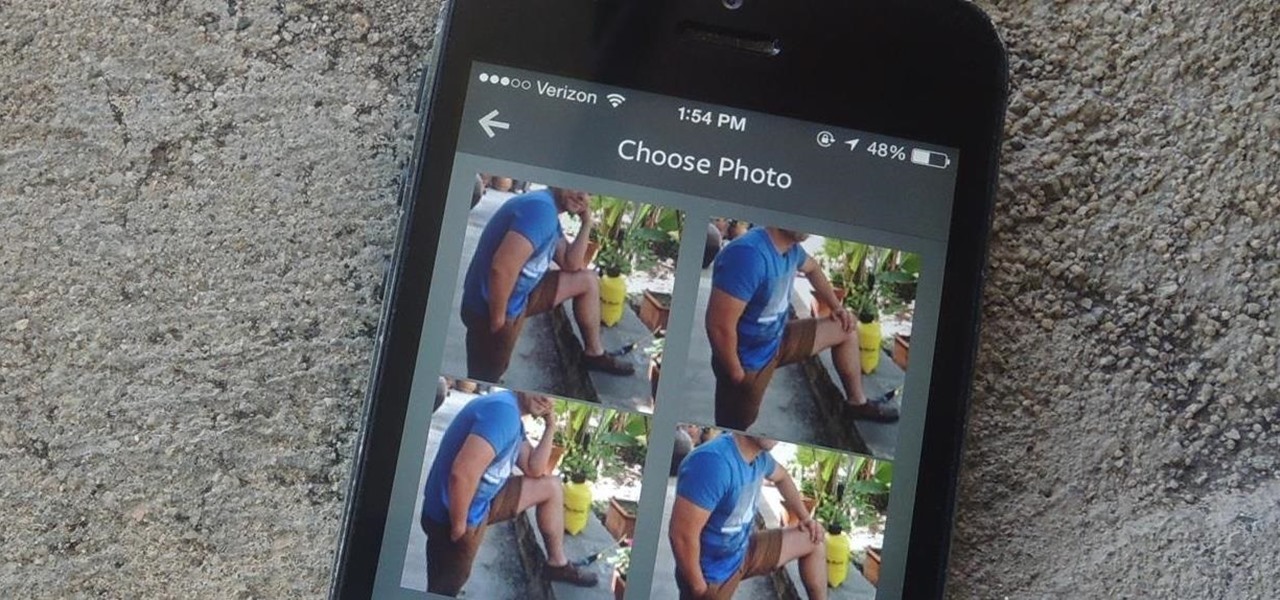
As it is right now, you can only send 5 images by email at the same time from your Camera Roll in iOS 7. There are some workarounds to increase that number, but a new feature in iOS 8 is finally making them unnecessary.

If you're breaking a sweat in the summer heat, but not trying to break the bank, this dead simple trick will show you how to make your own air conditioner for under ten bucks.

I don't read all of my emails, and even though it may sound a little bit odd, I don't listen to all of my voicemails either. For me, the problem isn't reading or listening to them, it's how it affects my iPhone's home screen.

Videos are great for catching fleeting moments, and photos are insanely easy to share with anyone, but how can you get the best of both worlds?

In a world where mobile devices are the new norm for interacting and staying in contact with one another, it's important to make the experience as smooth as possible, and typing is the biggest problem for me.

HTC pulled out all the stops when designing the HTC One M8. From it's sleek body, to it's incredible sound quality, this thing just oozes sophistication. While all of these add-ons are great, they can be incredibly taxing on the CPU, in turn causing some serious lag.

April Fools may be over, but any day is a good day to prank someone, and the best time to do it is when everyone's eyes are glued to the television.

Welcome back, my greenhorn hackers! In my continuing effort to demonstrate to you how to hack the ubiquitous Windows 7, we will going after that notoriously vulnerable Adobe Flash that is on nearly every client Windows system (you are not likely to find it on servers).

Rock-hard ice cream is the bane of my culinary existence. If I try and scoop it out with a spoon, the spoon invariably bends. If I use a traditional ice cream scooper, I end up with a torqued wrist and one or two pathetic curls of ice cream for my efforts.

Seemingly lost in the fanfare of the numerous features and specs of the Nexus 5 were a few highly innovative and handy add-ons—a low-power step detector and step-counting sensor—useful for tracking fitness data.

The newest version of Android, 4.4.2 KitKat, is making its way onto AT&T Samsung Galaxy S4s right now. Itching to try out the latest that Google has to offer? Keep an eye on your status bar for a notification letting you know that a system update is ready.

Last week, Apple issued an iOS 7.0.6 update that fixed a serious security vulnerability that could allow hackers to steal passwords, read emails, and get info from other SSL-encrypted communications.

Welcome back, my budding hackers! As you know, I firmly believe that to be a true professional hacker, you need to be proficient in Linux. This is for a number of good reasons.

Welcome back, my greenhorn hackers! In a previous tutorial on hacking databases, I showed you how to find online databases and then how to enumerate the databases, tables, and columns. In this guide, we'll now exfiltrate, extract, remove—whatever term you prefer—the data from an online database.

Whether it's because you have nosy family and friends or you're just cautious about losing your device, having a passcode on your Android smartphone is essential for protection. However, you don't always need or want a passcode, especially when you're home alone or in your car on the way to work.

We will show you with easy step by step instruction how to create a beautiful edible apple swan. This swan is easy to create and can be done in under 5m. Makes for a great centre piece during a special dinner.

Welcome back, my aspiring hackers! One of those areas of Linux that Windows users invariably struggle with is the concept of "mounting" devices and drives. In the Windows world, drives and devices are automatically "mounted" without any user effort or knowledge. Well, maybe a bit of knowledge. Most Windows users know to unmount their flash drive before removing it, but they usually think of it as "ejecting" it.

Automation applications bring the future a little closer. If you've seen Minority Report or other futuristic sci-fi movies, the intrigue of having your electronics work independently is something we can all appreciate.

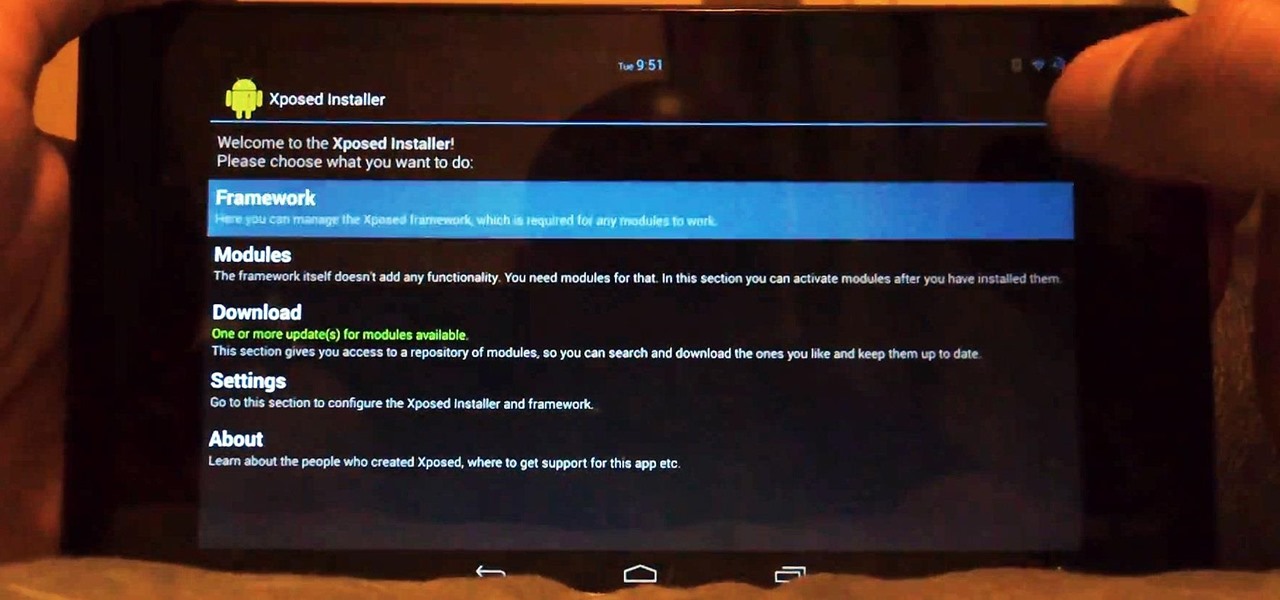
Customization of our Android devices, outside of what Google and mobile carriers allow us to do, used to mandate that our devices were rooted and running a custom ROM.

With over a million apps available in the App Store, you'd think that Apple would have come up with a better way to organize them on your iPhone.

While Siri has never been my favorite, after using her in the new iOS 7, I have definitely become a fan. If you want to know why, check out the newest cool features that Siri has to offer!

A free Wi-Fi hotspot can be a lifesaver. Whether it's because you have shitty reception, need faster connectivity, or just don't want to go over your monthly data plan, free Wi-Fi in public areas is greatly appreciated. While connecting to these free hotspots is fairly easy, finding them can become a whole nother issue. I've been in plenty of situations where I wasted my data plan instead of taking a few steps to the right, where free Wi-Fi would have been waiting for me and my Samsung Galaxy...

Have a load of games you want to play, but don't want to be seen in public playing on your old school Nintendo DS system? Play them on your Samsung Galaxy Note 2!

Everyone enjoys summers more than I do. At least, that's how it seems. While I take pleasure in the decline of clothing covering up my lady friends, I could definitely pass on the heat and absurd air conditioning costs. However, one summer staple that balls above all else is cooking on the grill.

If you're anything like me, you'd like the ability to fully exit your iPhone apps to help free up memory, improve battery life, stop background processes, and fix unresponsive apps. The thing is, you can, with the help of the app switcher. Force-closing apps also helps keep your app switch clean and organized.

Welcome back, my eager hackers! In recent blogs, I've demonstrated how to grab password hashes remotely using Metasploit's meterpreter and pwdump. Once we have the Windows passwords from the SAM file, we can then crack these hashes using tools such as Cain and Abel.

Video: . How To Use a Tampon

Any living creature will die if deprived of sleep for long enough. The longest documented occurrence of a person not fully sleeping and surviving is only 11 days. There is a rare disease where deep sleep is never achieved, affecting roughly 100 people worldwide. Patients usually only survive between 6 to 18 months after the onset of chronic insomnia, and only 3 to 9 months in a parasomnia state without any real REM sleep.

Welcome back, my neophyte hackers! Several of you have written me asking how to crack passwords. The answer, in part, depends upon whether you have physical access to the computer, what operating system you are running, and how strong the passwords are.