As my fellow cheapskates know, Groupon is an oasis. From discounted vacations to reduced-price massages, it has — nearly — anything and everything. It's great for discounts on dining and travel, but I've never thought of it as a place to shop for smartphones ... until now.
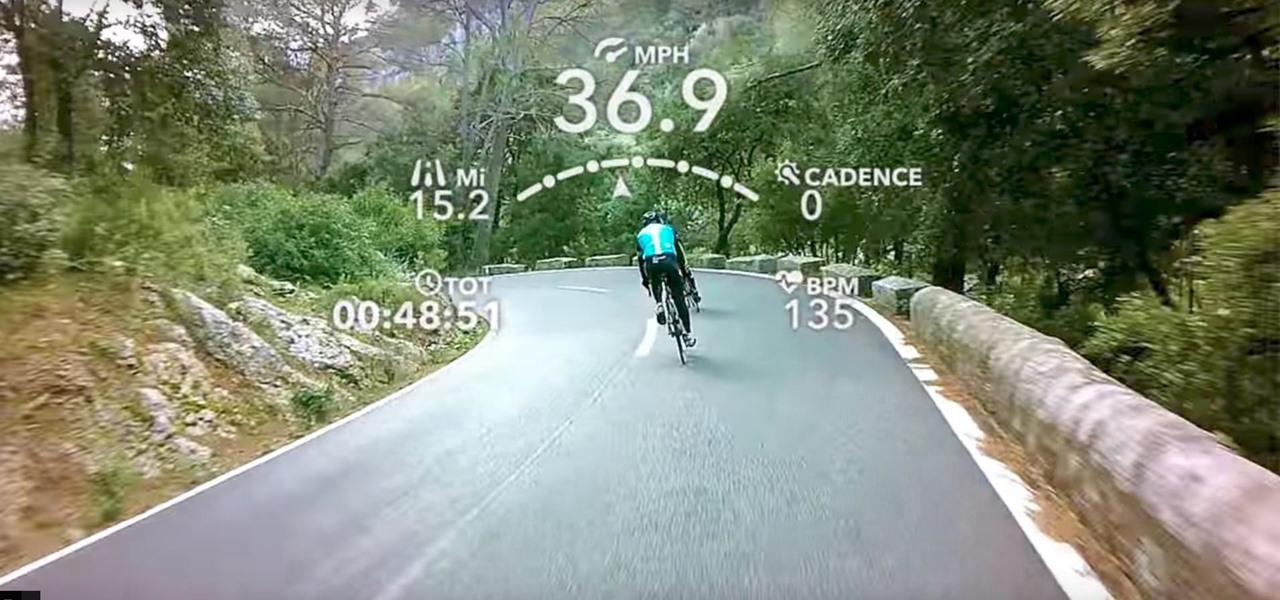
Cyclists of the world, new AR glasses are here to improve your rides. Possessing 2 GB RAM, a quad-core CPU, GPS, 16 to 32 GB of storage, an accelerometer, camera, gyroscope, magnetometer, barometer, Bluetooth, speaker, WiFi, and a mic, these aren't your regular UV-blocking sunglasses. Called the Everysight Raptor AR glasses, these shades project all of the information a cyclist could need to optimize their rides.

The National Transportation Safety Board (NTSB) said it is still investigating the circumstances of a fatal Tesla crash last year to determine if the car or Tesla's Autopilot driverless system was at fault, but revealed more details about the circumstances of the crash.

The company that brought us a BB-8 droid controlled with the Force — okay, just a high-tech wristband — is releasing its take on Spider-Man. Toymaker Sphero collaborated with Marvel to release an app-enabled Spider-Man toy equipped with numerous features, as well as games for your smartphone.

From the iPhone to the HomePod, Apple has revolutionized the tech industry. The company has changed the devices we use and how we use them, creating a new reality for all of us. As Apple continues to innovate, there's no guessing what the company will do. In fact, Apple's newest venture is possibly the most surprising one yet. With the hiring of two television executives from Sony, it appears that the tech giant is gearing up to take their phones and tablets back from Hulu, Netflix, and other...
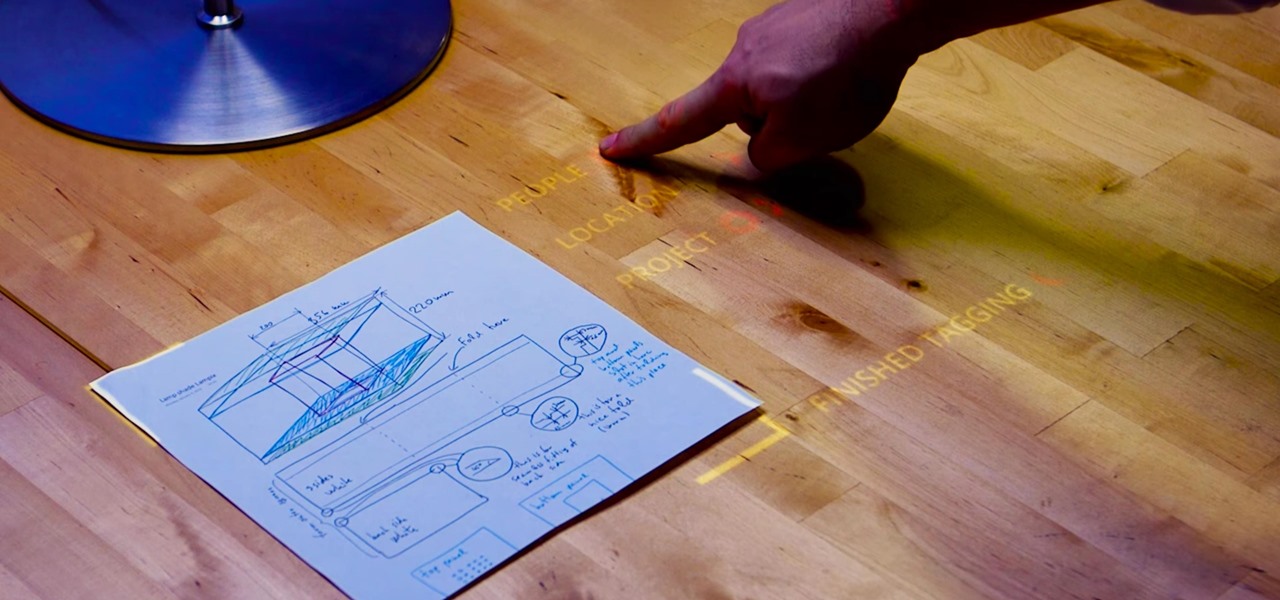
Judges at the South by Southwest (SXSW) Accelerator Pitch Event named Lampix the winner in the Augmented and Virtual Reality category, conference organizers announced today. The ninth annual competition, which took place over the weekend in Austin, Texas, pitted 50 startup finalists against each other in 10 technology categories.

Mimesys, whose core focus has always been about creating holographic representations of humans for virtual and augmented reality, has released a video showing off their holographic communication platform in action. This new communication tool uses a combination of virtual reality, with the HTC Vive and a Kinect, and mixed reality, with the HoloLens, to allow the users to have virtual meetings from anywhere in the world as though they are in the same room.

A company known as Cyanogen, Inc. has been in the news numerous times over the past year, and almost every time their name is brought up, it's amid reports of an impending doom. The writing is on the wall for the makers of Cyanogen OS, as it appears that there is little that can be done to prevent the company from going belly-up in the near future.

Hello, Null Byters. I'm Barrow, and I'm excited to introduce myself as the new admin here on Null Byte. Just like previous admins have done before me, I will be writing new guides, updating older guides if they need it, and responding to some of your issues in the forum. Before I get started with any of that, though, I wanted to talk a little bit about myself and the future of Null Byte.

I found this article a while back and I found it underneath a bunch of junk. Anyway, it's a article on 9 notorious hacker including Walter O'Brien (You know the T.V. show Scorpion? Well that's him). Not to mention the weird names:

Baking a cake is relatively easy... if you happen to have a cookbook or some boxed cake mix nearby. And though you can use the internet or your favorite cooking app, it can be nice to just cook without a recipe. That seems impossible with baking, which is such an exact science, but it's actually relatively easy.

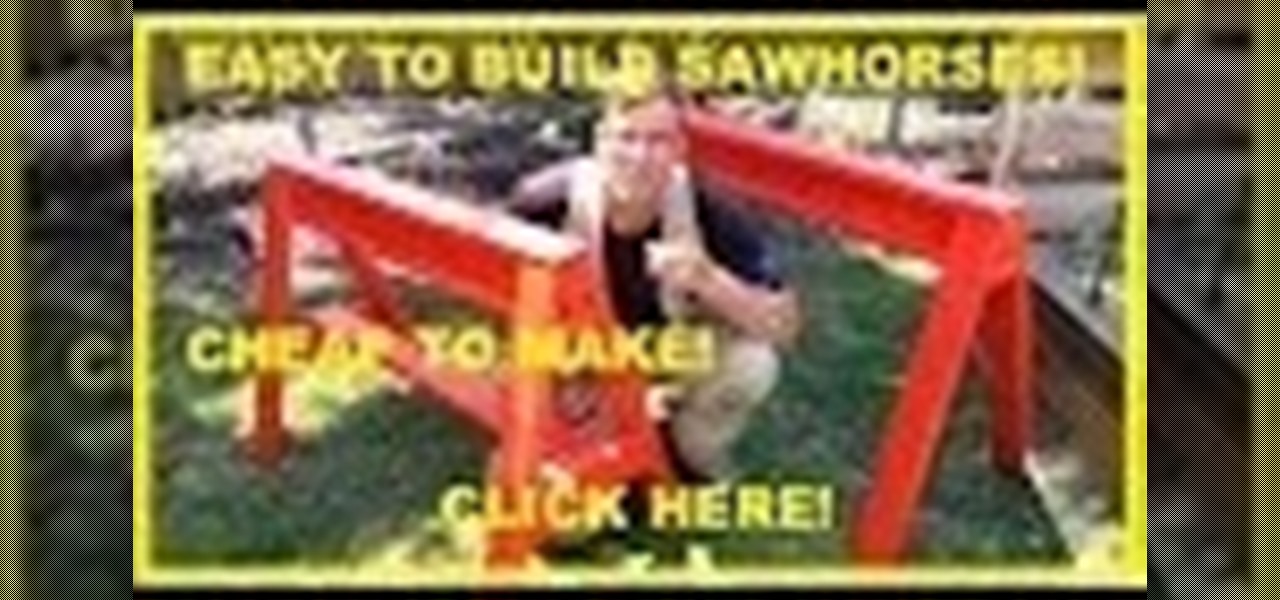
How to build a set of strong, stackable sturdy sawhorses. Let's face it, one of the most useful pieces of carpentry equipment would have to be a set of sawhorses. Every worksite, garage or workshop needs a set of sawhorses. They have numerous uses from stacking timber on, using as painting racks, to using as a temporary workbench by laying a door or some ply across two sawhorses. You can even use them as trestles for a dining table!

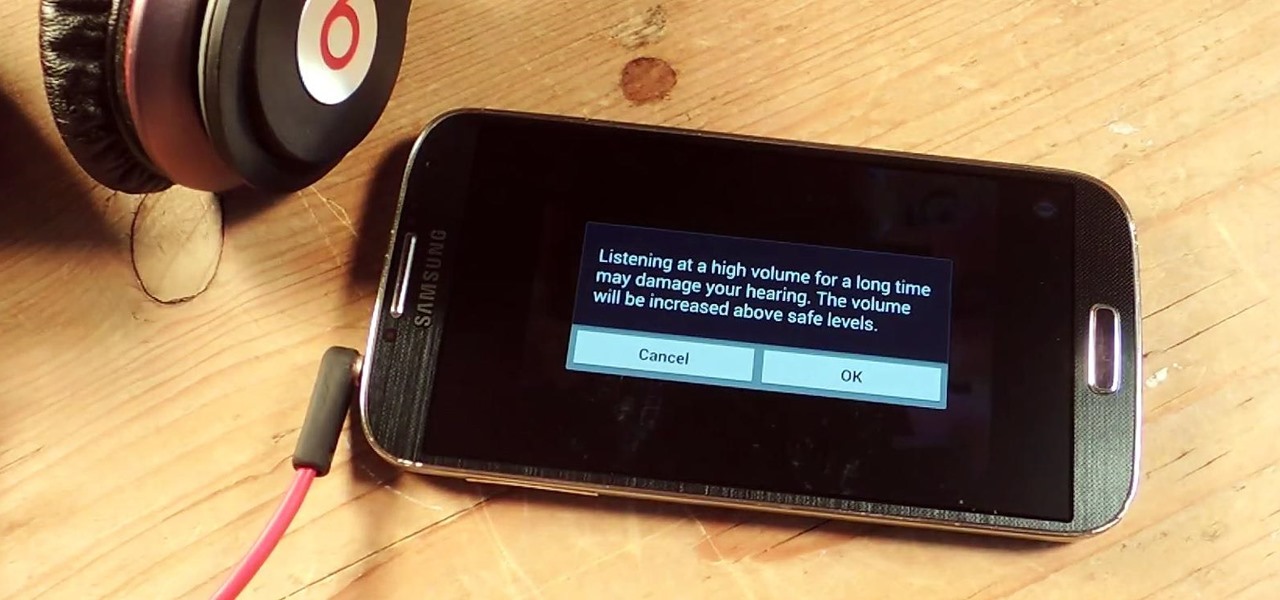
I've been told numerous times that I listen to music way too loud, to the point of potential hearing damage, especially when I have my headphones plugged in. Not only do my friends tell me this, but my Samsung Galaxy S4 likes to nag me as well. Once I pass a certain volume threshold (nine steps) with my headphones, I get that annoying high volume alert. Sorry, my hearing isn't as good as it once was, so let me jam in peace!

Welcome back my social engineers/hackarians! Today we'll be looking into a fantastic piece of software, The Social-Engineer Toolkit or just SET for short. SET is designed, Developed and used by several Social-engineers. So... Let's get started!

Samsung does a good job of making their devices fairly open, and the Galaxy S3 is no different. There are numerous way to root a device, but sometimes the jargon and steps can be a little intimidating for new rooters, and even pro rooters.

Having trouble getting a strong Wi-Fi signal on your Samsung Galaxy S3? Does the signal drop out on you when changing rooms? Frustrating, isn't it?

Numerous studies have shown that people are over-confident in their own abilities. Most people, for example, think that they are better drivers than average.

Sweating or leaving your feet damp after showers can lead to athlete's foot, a skin rash that targets damp, covered areas. Learn about treating athlete's foot from a doctor in this medical how-to video.

Volleyball has numerous unique rules. For example, volleyball is one of the only sports that does not allow throwing or catching the ball. Learn the rules of volleyball in this video tutorial.

Tennis is a great summer sport, which makes having a great forehand essential for any tennis player. Learn how to improve your forehand swing in this tennis video.

Tennis is a great summer sport, and a great backhand is essential to being a good tennis player. Learn how to improve your backhand swing in this video tennis tutorial.

In the coming years, artificial intelligence (AI) will revolutionize every facet of technology and business. AI researchers are in high demand. Salaries in this field are regularly in the hundreds of thousands of dollars.

With the release of the Pixel 2 XL and the iPhone X, smartphones have hit a new high not just in price, but also raw processing power. These new flagships not only cost more than twice as much as an Xbox One or PlayStation 4, they have also become almost as powerful as far as gaming goes. Because of this, a lot of games once reserved for consoles and PCs have made their way to our smartphones.

Not only has there been difficulty finding consensus on a name for driverless, autonomous, self-driving, or automated vehicles, there is also the issue of what we actually mean when we say a vehicle is self-driving, automated, and so on.

Bacteria gets a bad rap. Most headlines focus on the danger and discomfort posed by pathogens like bacteria, but many of the bacteria that live on and in us are vital to our health. Many products out there, called probiotics, are sold with the implication that they're supporting these healthy bacteria that share our bodies — but do they actually work?

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

Welcome back, my greenhorn hackers! As all you know by now, I'm loving this new show, Mr. Robot. Among the many things going for this innovative and captivating program is the realism of the hacking. I am using this series titled "The Hacks of Mr. Robot" to demonstrate the hacks that are used on this program.

Welcome back, my greenhorn hackers! One of the most important issues any hacker must address is how to get past security devices and remain undetected. These can include antivirus software, intrusion detection systems, firewalls, web application firewalls, and numerous others. As nearly all of these devices employ a signature-based detection scheme where they maintain a database of known exploits and payload signatures, the key is to either:

Welcome back, my hacker novitiates! In an earlier tutorial, I had introduced you to two essential tools for cracking online passwords—Tamper Data and THC-Hydra. In that guide, I promised to follow up with another tutorial on how to use THC-Hydra against web forms, so here we go. Although you can use Tamper Data for this purpose, I want to introduce you to another tool that is built into Kali, Burp Suite.

No one wants to appear stupid. Whether you rely on lengthy, complicated vocabulary to show your smarts, or enjoy highlighting your speedy mental math skills, everyone prefers emphasizing intelligence over hiding it.

Welcome back, my amateur hackers! Many of you here are new to hacking. If so, I strongly recommend that each of you set up a "laboratory" to practice your hacks. Just like any discipline, you need to practice, practice, and practice some more before you take it out to the real world.

Welcome back, my tenderfoot hackers! I have written many tutorials on hacking using Metasploit, including leaving no evidence behind and exploring the inner architecture. Also, there are my Metasploit cheat sheets for commands and hacking scripts.

Welcome back, my hacker apprentices! To enter the upper echelons of hackerdom, you MUST develop scripting skills. It's all great and well to use other hacker's tools, but to get and maintain the upper hand, you must develop your own unique tools, and you can only do that by developing your scripting skills.

Welcome back, my tenderfoot hackers! I recently began a new series on digital forensics to help tenderfoot hackers from being detected and ultimately, incarcerated. In this installment of that series, we will look at recovering deleted files. This is important to hackers because you need to know that even when you delete files on your computer or on the victim's computer, a forensic investigator can usually recover them.

Welcome back, my novice hackers! My recent tutorials have been focused upon ways to NOT get caught. Some people call this anti-forensics—the ability to not leave evidence that can be tracked to you or your hack by the system administrator or law enforcement.

A new profile on Apple's exiting design chief Jony Ive, the man behind many of the company's most successful products, paints a fuller picture of what led to his departure.

There are a number of reasons you'd want to delete your Skype account. You may have decided to move away from the app in favor of another service like WhatsApp or FaceTime, or perhaps you want to erase your account due to an online hack. Regardless of why you might want to delete your Skype account, doing so isn't quite as straightforward as it appears.

With Microsoft taking direct aim at enterprises for its HoloLens 2 with a $3,500 price tag, one startup is betting that business will be willing to pony up for glasses-free 3D displays as well.

We've seen a variety of AR experiences related to athletic footwear over the years, but Puma is betting sneakerheads will buy into a version of interactive design where sneakers are the augmented reality experience

Your Instagram feed is jam-packed with interesting and lively photos, videos, and stories that largely offset the iOS app's comparatively bland user interface. If the interface's dull colors have always bothered you, you can splash on some much-needed color to better reflect your personality and tastes.