Simmering or poaching food is a total pain sometimes. The problems are numerous: a layer exposed to air often dries out and creates a gross skin that can ruin the texture of the sauce, the poaching liquid evaporates too quickly and causes the poached protein to burn, and so on.

This is my first tutorial on this website. So, if you think anything to be wrong, just place it in the comments.

Salad spinners are one of the more divisive kitchen tools out there. On one hand, they're incredibly easy, efficient, and useful. On the other hand, they're a single-use tool that takes up a lot of space.

Welcome back, my amateur hackers! With Halloween right around the corner, I thought you could have a little fun with your newfound hacking skills using a hack that is guaranteed to freak out your boss, teacher, coworker, friend, etc.

Here's a fact that everyone knows: avocados are delicious in guacamole, salads, and sandwiches. Here's a fact that's less commonly known: avocados are delicious in desserts, too.

I'm a firm believer that a sandwich is the ultimate food. It's filling, but not heavy; it has carbs, protein, veggies, and sauces; and it's easily customizable. Add that all up and you've got the absolutely perfect lunch.

Welcome back, my neophyte hackers! In previous tutorials, we learned how to steal system tokens that we could use to access resources, how to use hashdump to pull password hashes from a local system, and how to grab password hashes from a local system and crack them.

There are lots of great reasons for going out to a fantastic coffee shop for a cuppa. Coffee shops have a lovely ambiance, are a perfect place to meet with friends or do some work, and are a great excuse to get out of the house. Seeking out a perfect cup of coffee, however, shouldn't be one of the reasons that you hit up your local café.

Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world!

Most of you already know that a zero-day exploit is an exploit that has not yet been revealed to the software vendor or the public. As a result, the vulnerability that enables the exploit hasn't been patched. This means that someone with a zero-day exploit can hack into any system that has that particular configuration or software, giving them free reign to steal information, identities, credit card info, and spy on victims.

With all of the different websites we use in our day-to-day lives, keeping track of our numerous login credentials can start to become a hassle. This has created a market for password managers that aim to centralize these account credentials and generally streamline the process of logging into our favorite sites.

Sometimes, it helps to be prepared before jumping into a new relationship; look before you leap! To have a healthy relationship with someone who has an STI, it is advisable that you enter the relationship knowledgeable about sexually transmitted infections and what your risks might be.

Welcome back, my greenhorn hackers!

Welcome back, my greenhorn hackers! Although we have focused primarily on technical hacks here, social engineering can sometimes be especially effective. This one requires a bit of technical skill, but not too much. In addition, it's limited by how specific a target you can choose—but it will work.

The space on your phone is extremely valuable, so getting the most out of your screen real estate can help you out when multitasking or for just making your device feel bigger. One thing that is often overlooked when it comes to saving space on the screen is the keyboard.

If you've been using Google's hidden App Ops to lock down and prevent some of your Android applications from exposing your privacy, then think twice before updating to the new Android 4.4.2 software.

Welcome back, my tenderfoot hackers! In some of my past articles, I've shown numerous ways of embedding a listener/rootkit on a remote system, including buffer overflows of the operating system, getting the victim to click on a link to our malicious website, and sending a malicious Microsoft Office and Adobe Acrobat file.

All of my hacks up to this point have been operating system hacks. In other words, we have exploited a vulnerability usually in an operating system service (SMB, RPC, etc.) that all allow us to install a command shell or other code in the target system.

There are numerous opportunities for people with various disabilities to participate in horse riding. Learn about adaptive horse riding from an equestrian program manager in this free sports and recreation video series.

If your cray fish or crawfish has tiny tiny worms crawling over the shell, watch this how-to video to fix the problem.

No matter the field you work in, tech dominates every industry in 2020, and that means that you can always increase your earning potential by adding valuable coding skills to your arsenal. Coding can lead to dream software development career paths, lucrative freelance work, and it can be an impressive boost to your résumé. Now, you can learn these valuable skills at home with The Complete One Hour Coder Bundle, an offer at an unmissable 97% off its usual price, at just $34.99 (usually $1,200).

Amazon Web Services (AWS) offers over 200 services, including networking, computing, storage, analytics, blockchain, mobile, and developer tools. Not surprisingly, numerous companies rely on AWS's massive infrastructure. Instead of building their own server farms, they rent space and computing power from AWS's secure and robust system.

For a decade, Microsoft Azure has been transforming businesses across the globe. The cloud-computing service is leading the way in software as a service (SaaS), platform as a service (Paas), and infrastructure as a service (IaaS) protocols.

It's no secret that learning how to code is one of the best things you can do if you want to land a high-paying career in a world that's heavily reliant on web and app development.

Starting with Android 9 and 10, Google made privacy and security the main priorities for Android updates. Both versions brought numerous changes to help erase the notion that Android isn't safe, but Android 11 might even have them beat.

While consumer-grade smartglasses are the holy grail for tech companies, smartglasses maker Vuzix knows where its bread is buttered, and that's in the enterprise segment.

Before smartglasses makers can dream of taking smartglasses to mainstream consumers, they must first determine the right mix of form, function, and price that will drive customers to buy into what they're hoping to sell.

There's something extremely satisfying about hunting down your online adversaries and knocking them out with a well-placed shot, which probably explains why shooting games are still one some of the most popular time killers for iOS and Android.

This week, while Apple was the subject of thinly sourced reports that it had canceled development of its oft-rumored smartglasses, the Cupertino was actually laying the foundation for its AR hardware future with a new initiative focused on mentoring Chinese developers in mobile AR development.

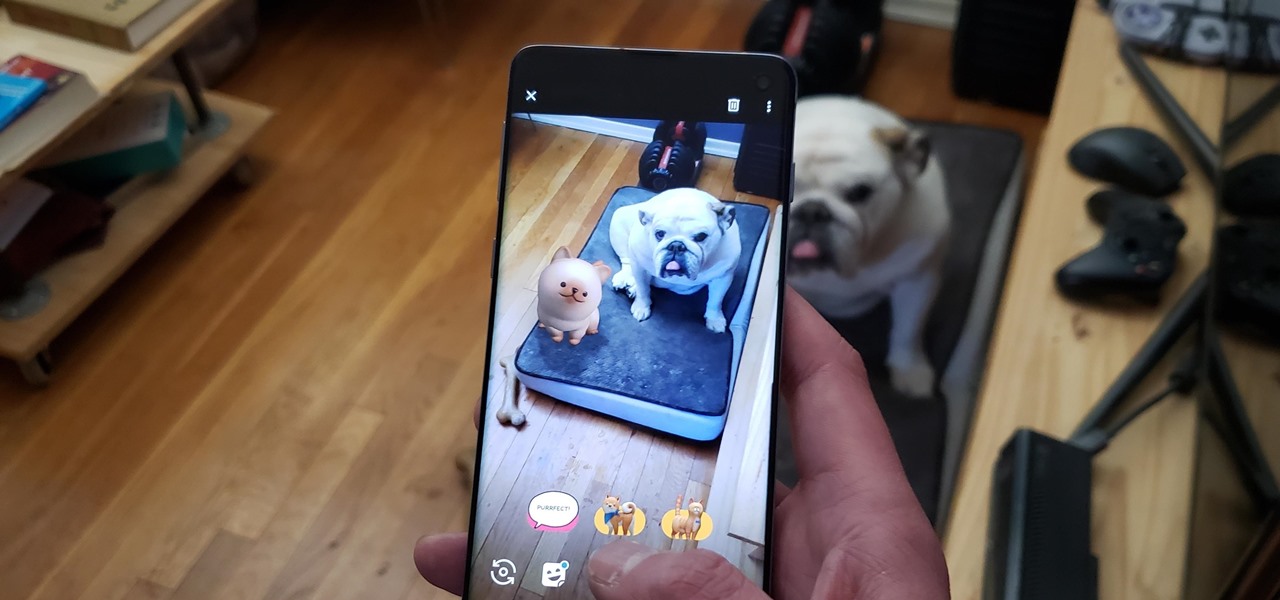
Google's has expanded ARCore support to numerous Android flagships like the Galaxy S10, so if you have a compatible device, you get access to all the cool new apps that can augment the world around you. One of ARCore's most sought-after features, AR Stickers, is normally exclusive to Google's Pixel lineup, but by sideloading the Google Camera app, you can try it on any ARCore device.

Anyone who has been within a block of any wireless brick and mortar store or tech conference in the last couple of years has no doubt seen banners, posters, and videos promoting 5G high-speed wireless services on the way.

Current-generation mobile augmented reality apps offer users numerous opportunities to punch up photos and videos with 3D content, but there's surprisingly few options for users to express themselves using virtual characters.

WhatsApp is the go-to messaging app for millions worldwide and its easy to see why. The app can be considered the Swiss Army Knife of texting thanks to numerous features like Group Chats and Status Stories, in addition to striking a great balance between ease of access and overall security.

Augmented reality and computer vision company Blippar has a new lease on life, as previous investor Candy Ventures has completed a successful bid to acquire the assets of the beleaguered company.

Many apps claim to record phone calls on Android, but very few actually deliver. There's just too many different devices floating around out there for one app to be able to support them all — or so it would seem.

In iOS, the Control Center is an easy way to toggle settings such as Wi-Fi, Do Not Disturb, and Low Power Mode. Its Android counterpart is called "Quick Settings," which provides much of the same functionality with a few bonuses. If you're curious about how this toggle menu works or miss having it before you made the switch from Android, you can test it out on your iPhone right now.

When BlackBerry made the move to Android OS, they were aware of the limitations it presented. Unlike with BB10, they didn't create the operating system and would have to deal with the vulnerabilities already included. As a result, they added numerous security enhancements, and at the heart of this is DTEK.

There's always an iPhone in our list of top phones for privacy and security, due in large part to advanced security measures like Face ID, consistent iOS updates, and easy ways to prevent unwanted access and excessive data sharing. However, some of those options actually do the opposite and hinder security. It all depends on how you use your iPhone, but you should at least know everything available.

While numerous startups are competing to convert the AR Cloud from a pie-in-the-sky to a reality, Wikitude is thinking smaller with the latest edition of its augmented reality SDK.