Last week, we told you about Microsoft's Alex Kipman and his nomination for the annual European Inventor Award, presented by the European Patent Office (EPO). And while that's big news in and of itself, it turns out we overlooked a very important detail buried in the EPO's video presentation. What was it? Only one of the most sought-after data points related to the HoloLens since its launch: how many have been sold.
It is finally happening. After not having a major update since August of 2016, HoloLens owners everywhere will soon get a number of new features added to their devices. At least if they are members of the Windows Insider program.

Last week, the first possible image of the upcoming OnePlus 6 leaked. It was met with mixed reactions, most notably for its apparent iPhone X-style "notch." OnePlus fans seem concerned that the company is implementing a design choice based on what it thinks is trending, not necessarily what's best for the product. If you're one of those uneasy about OnePlus' future, don't be. At least not yet.

On Tuesday, NBA Commissioner Adam Silver joined Magic Leap CEO Rony Abovitz on stage to unveil a partnership between the two companies.

A new smartglasses powerhouse is rising in Europe, led by two of the region's leading brands, optical systems company Zeiss (also known as Carl Zeiss) and telecommunications giant Deutsche Telekom.

While self-driving cars appear to be as inevitable as augmented reality headsets, the auto industry and its technology partners likely have years of testing to complete and regulatory loopholes to jump through before self-driving cars hit most highways.

On Monday, toy maker Merge virtually blasted its way into CES 2018 with a new tech-meets-toys innovation in the form of an augmented reality gun controller for use with smartphone-powered first-person shooter apps.

Back to the Future Part II missed wildly on many technological advances for the year 2015, such as flying cars and rehydration ovens. However, it connected on several predictions, such as video calling and biometric security, and it was in the ballpark (pun intended) on others, such as the Chicago Cubs winning the World Series.

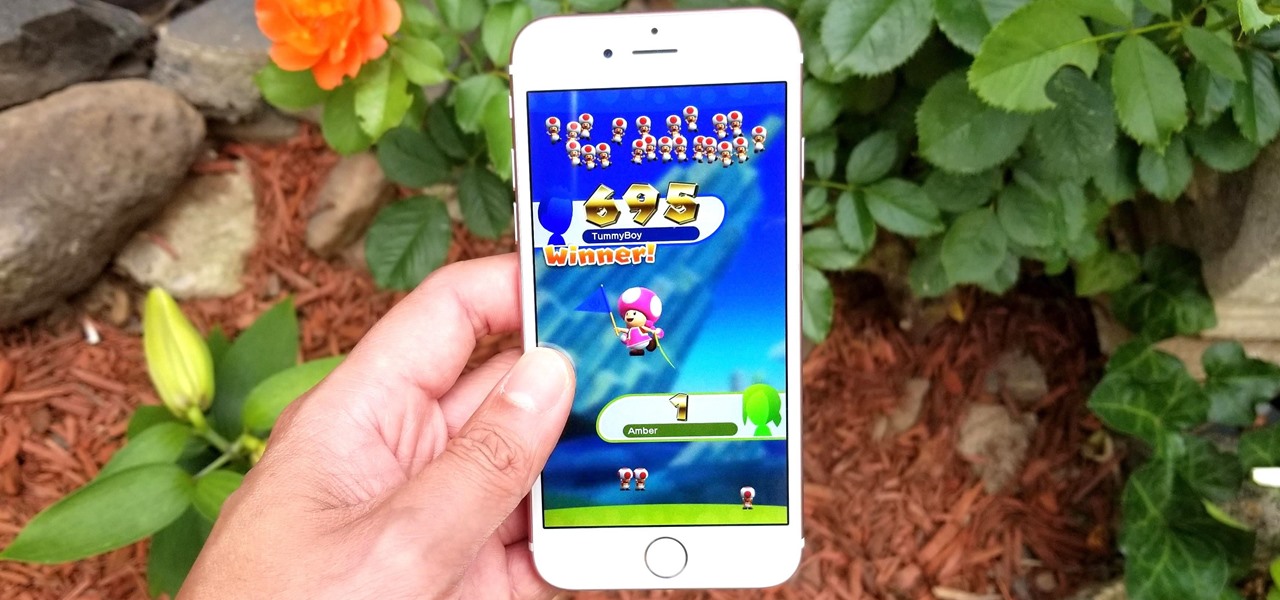
One of the best features in Super Mario Run is a multiplayer race that lets you test your skills against other players. Toad Rally, as it's called, pits you against other players in a battle for Toads. The more Toads you collect, the easier it is to build your kingdom and collect more rewards on your Android or iPhone.

We continue to field stories underscoring the strong trends of Investment in augmented reality in various sectors. This week, one company strengthens their offerings to the enterprise sector, while two other companies capitalize on the promise presented by augmented reality to consumers – specifically, in gaming.

A few years ago, the Hilton hotel group unrolled the Digital Key, a feature of the Hilton Honors app that allows you to unlock your hotel room with your smartphone.

The new battlefield AR game announced by Skyrocket Toys today is similar to the childhood game "Tag", except the stakes are much, much higher.

Snapchat announced today that you can now design geofilters in-app, making it easier than ever to customize your snaps. This new feature incorporates a mobile creative studio, so you no longer have to use your computer to create your custom masterpiece.

Winter is coming for Amazon. It looks like the company is having another go at the smartphone world with its release of new smartphones branded as "Ice".

The Augmented World Expo (AWE), the biggest event for augmented, virtual, and mixed reality companies, developers, customers, and connoisseurs, is happening right now. You know what that means for us here at Next Reality? Companies presenting and exhibiting at AWE are releasing news like crazy.

All Galaxy S8 models apparently weren't created equal. According to numerous user reports, it appears that Snapdragon-powered Galaxy S8 variants are using an older flash storage standard than what Samsung was originally advertising.

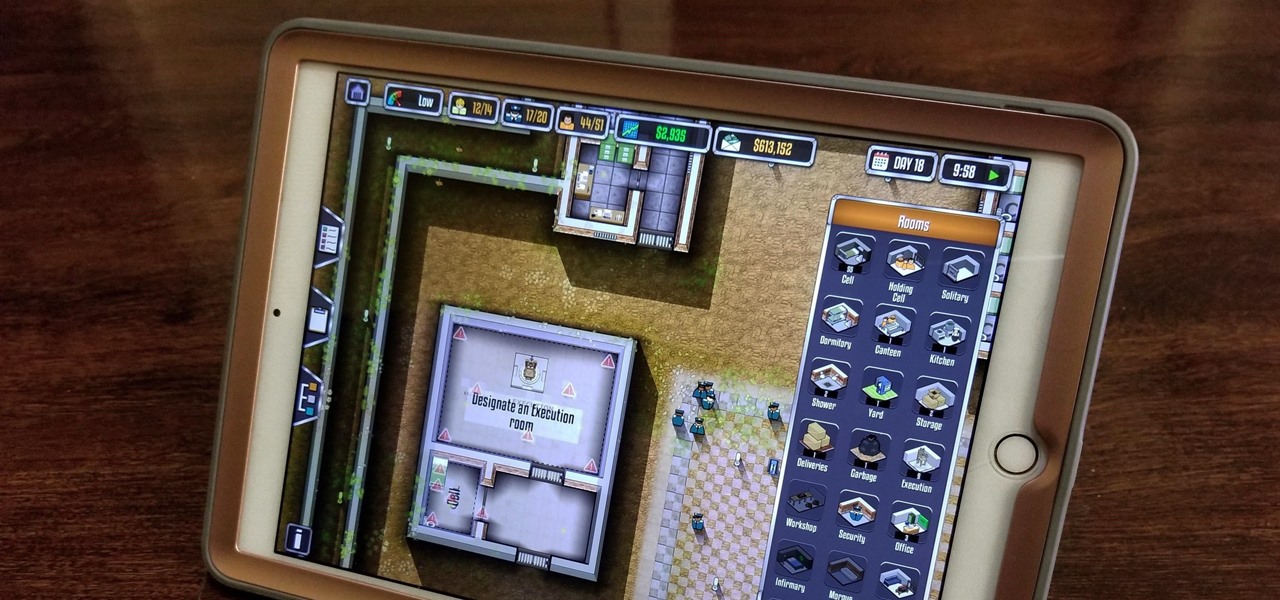
Prison Architect, the BAFTA winner for the Best Persistent Game in 2016, has finally soft launched on iOS. Originally a PC game, Prison Architect lets you build and maintain a maximum security prison. Comparable to running a small city, the game has you manage an ever-expanding correctional facility and contend not only with violent offenders and ever-present prospect of a chaotic riot, but also more mundane affairs like balancing the prison's budget and employee payroll. In addition to the s...

A 'superbug' fungus is currently running riot in the hospitals of New York and New Jersey. This outbreak of Candida auris has contributed to 17 deaths in NYC, according to recent reports.

We've all been hit by inopportune screen rotations at some point or another. Having the display orientation suddenly go from portrait to landscape when reading an interesting article in bed is one of the biggest irritations that come with using a smartphone (at least, for me). Thankfully, there are apps out there for your Android to help alleviate this inconvenience.

Dynasty Warriors has finally been unleashed on the world of mobile gaming. The latest installment in the popular series is called Dynasty Warriors: Unleashed, and it sends you rampaging through armies using a variety of devastating attacks, all while collecting and upgrading over 80 unique characters from the Dynasty Warriors series. Each offer their own unique abilities, which lets you create the ideal team to take on the seemingly endless hordes coming your way with cold, cruel efficiency.

Not only has there been difficulty finding consensus on a name for driverless, autonomous, self-driving, or automated vehicles, there is also the issue of what we actually mean when we say a vehicle is self-driving, automated, and so on.

The Huawei Nexus 6P was released a little over a year ago, but despite doing moderately well in sales, the device has had more than its fair share of issues. When first released, there were numerous reception and memory management difficulties that left users extremely frustrated, though, those problems were solved with updates pushed by Google.

Koji is a culture made up of a certain fungus (mold) called Aspergillus oryzae, which has been used to ferment rice and soybeans in Japanese, Chinese, and Korean kitchens for centuries. Koji can actually have other involved fungi, but Aspergillus oryzae is the most common, and therefore the names can be used interchangeably. Its end purpose is to enhance the flavor of items like soy sauce, sake, and miso.

New Android versions have always been released on a fairly regular schedule—in late Fall, Google debuts a new Nexus device, while simultaneously publishing the next iteration of the world's leading mobile operating system. But things are different this year, as we now have numerous indications that Android Nougat could be released as early as August or September.

It's no secret that cauliflower is good for you—but not nearly enough people know that the best part about cauliflower is its insane versatility. Because its cooked flavor is so mild, it can be incorporated into a crazy amount of dishes and preparations.

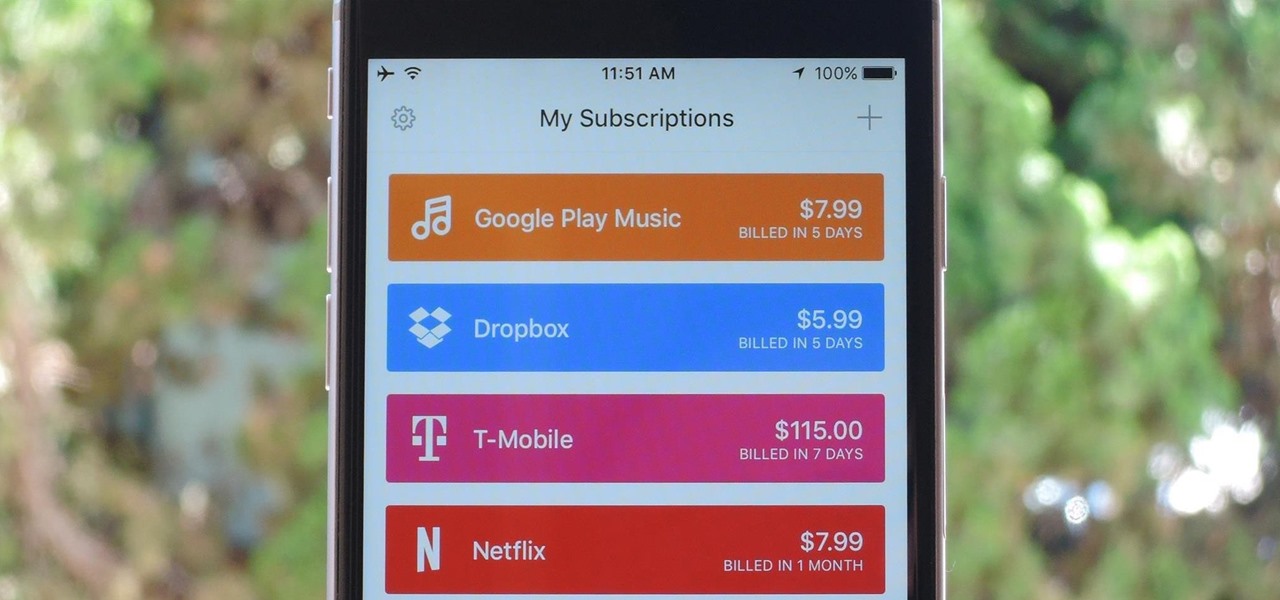
As the internet continues to become a bigger part of our day-to-day lives, we slowly but surely start to rack up a bunch of web-based subscriptions. These internet subscription services—Netflix, Hulu, and Amazon Prime, just to name a few—may seem innocuously cheap individually, but when combined, they actually comprise a significant portion of our monthly bills.

Welcome back, my budding hackers! In this series, I have been trying to familiarize you with the many features of the world's best framework for exploitation, hacking, and pentesting, Metasploit. There are so many features, and techniques for using those features, that few pentesters/hackers are aware of all of them.

Welcome back, my hacker novitiates! Often, to hack a website, we need to connect to and exploit a particular object within said website. It might be an admin panel or a subdirectory that is vulnerable to attack. The key, of course, is to find these objects, as they may be hidden.

Welcome back to another episode of Java Tutorials, In today's tutorial, we'll be learning about what methods are, proper syntax when writing Methods, and why they are beneficial in a program's code.

I was fortunate enough to be visiting one of my college classmates in Columbus, GA last spring and saw two large bags of onions in his kitchen... but not like the ones you get at the grocery store. Two standing 50 lb. bags!

Simmering or poaching food is a total pain sometimes. The problems are numerous: a layer exposed to air often dries out and creates a gross skin that can ruin the texture of the sauce, the poaching liquid evaporates too quickly and causes the poached protein to burn, and so on.

This is my first tutorial on this website. So, if you think anything to be wrong, just place it in the comments.

Salad spinners are one of the more divisive kitchen tools out there. On one hand, they're incredibly easy, efficient, and useful. On the other hand, they're a single-use tool that takes up a lot of space.

Welcome back, my amateur hackers! With Halloween right around the corner, I thought you could have a little fun with your newfound hacking skills using a hack that is guaranteed to freak out your boss, teacher, coworker, friend, etc.

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

Welcome back, my greenhorn hackers! As all you know by now, I'm loving this new show, Mr. Robot. Among the many things going for this innovative and captivating program is the realism of the hacking. I am using this series titled "The Hacks of Mr. Robot" to demonstrate the hacks that are used on this program.

Here's a fact that everyone knows: avocados are delicious in guacamole, salads, and sandwiches. Here's a fact that's less commonly known: avocados are delicious in desserts, too.

Welcome back, my greenhorn hackers! One of the most important issues any hacker must address is how to get past security devices and remain undetected. These can include antivirus software, intrusion detection systems, firewalls, web application firewalls, and numerous others. As nearly all of these devices employ a signature-based detection scheme where they maintain a database of known exploits and payload signatures, the key is to either:

I'm a firm believer that a sandwich is the ultimate food. It's filling, but not heavy; it has carbs, protein, veggies, and sauces; and it's easily customizable. Add that all up and you've got the absolutely perfect lunch.

Welcome back, my neophyte hackers! In previous tutorials, we learned how to steal system tokens that we could use to access resources, how to use hashdump to pull password hashes from a local system, and how to grab password hashes from a local system and crack them.