
How To: Make Gmail more secure
Are you a Gmail user? Listen up, cause here's a snazzy tip from Tekzilla to help protect your emails.


Are you a Gmail user? Listen up, cause here's a snazzy tip from Tekzilla to help protect your emails.

G-Floor garage floor covering is easy to install and a great way to protect and maintain your surfaces.

This video from Garden Time shows you how to use a cold frame to protect your outdoor plants from the winter months.

How far would you get if you tried to cross a desert on foot? Learn how to prepare for surviving in a scorching environment,including how to substitute a piece of parachute nylon for a headdress! Use what is at hand to protect your eyes.

See how to use a Valley Universal trailer coupler lock to protect your trailer when it's unattached from your vehicle. Then see how this works with a popular trigger style coupler.

Learn how to use the linemen for blocking to protect the quarterback in this team football drill.

Planning to be out of the house for an extended period of time? Dave tells you how to ensure that your houseplants survive your absence.

A quick overview and how-to on using the McAfee SiteAdvisor to protect yourself from malicous web pages.
Are you using the Internet at a school, library, or some other place that blocks or restricts web access? Mom and dad still trying to protect you from online predators, even though you're more than old enough to be one yourself? Learn how to bypass proxy servers that block access to certain websites by watching this how-to video. In this case it's done to access Myspace but this method can be used with any blocked website. Follow along with this video tutorial and never get hindered by restri...

This is a FEMA PSA about what kids should do during an earthquake. Be prepared and stick together. Hide under tables to protect your head.

Get serious, stay calm, pay attention to the teacher. Don't talk. This is a serious thing: fire drills. Be prepared. They warn kids if they are not serious they may kill someone. Well, thank you FEMA-- another PSA and government effort to protect the kids!

Resin mixing is an important part of composite manufacturing. Here's how to do it safely and with an acceptable margin of accuracy. Make sure to wear gloves to protect your hands and skin from the active agents in the resin.

Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet.

Welcome back, my greenhorn hackers! In many cases when a computer, phone, or mobile device is seized for evidence, the system will have graphic images that might be used as evidence. Obviously, in some cases these graphic images may be the evidence such as in child pornography cases. In other situations, the graphic images may tell us something about where and when the suspect was somewhere specific.

G'day, Knuckleheads, and welcome to Episode 20 of my Owner Builder Series! In this Episode, we look at installing the Wall Wrap which goes on before the cladding is installed. It's a vapour membrane that protects the frame and internal linings from moisture damage.

I hate to break it to you, but you're probably here because you were trolled. Thanks to a Photoshopped image making rounds across Twitter, Apple fans were tricked into believing that iOS 8 allowed them to lock individual apps, accessible only through a passcode or fingerprint ID. While that's not technically true, we've got the solution for you.

This is a great tip that will show you how to easily protect your bathroom tub or shower window from rotting out due to water damage.
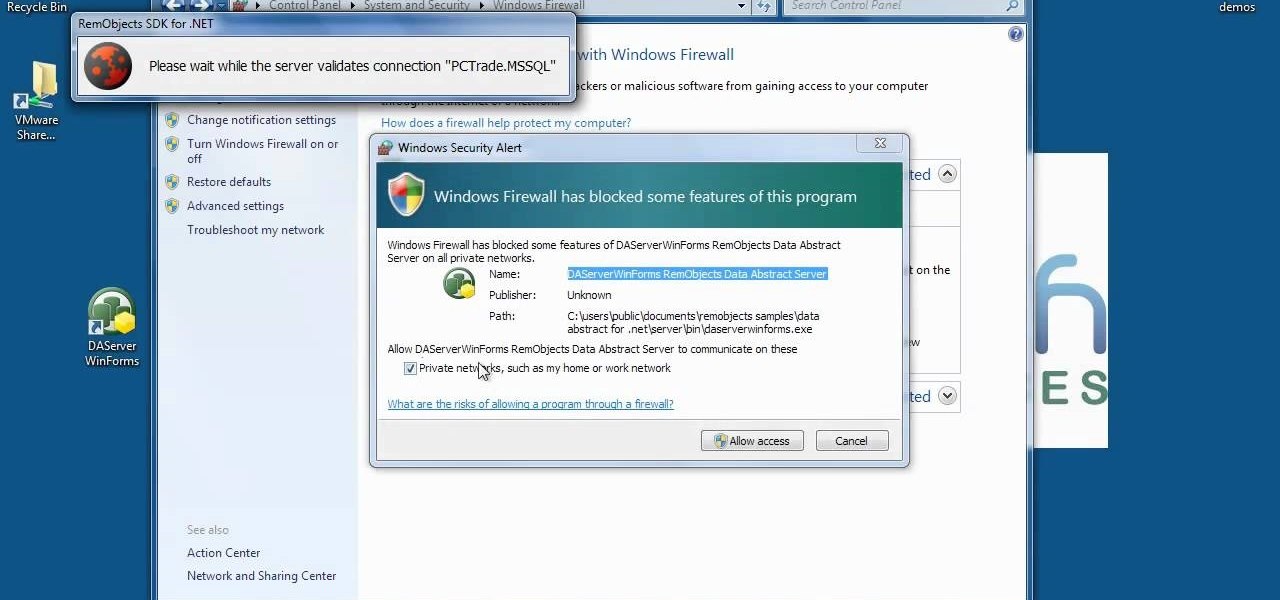
Firewall is necessary to protect a computer network from hostile intrusions. You can easily setup your Firewall setting. This video helps you to do it.

In this web design tutorial we will show you how to protect yourself from losing your work just in case the program malfunctions, computer crashes or you accidentally forget to save document and so on. I highly recommend you utilize this Web Design Tutorial especially if you are working on large websites for clients.

In this how to video, you will learn how to draw Broly. First, start out with an oval shape for the face. Next, add another for the ear. From here, you can add the neck, shoulders, and chest. Next, draw numerous spikes for the hair. The basic outline is complete. Go into the drawing with more detail by adding lines inside the spikes to simulate hair strands. Add the eyebrows, eyes, nose, and mouth. Next, draw in the muscles of the shoulders and chest. Add the outline of the necklace. Now you ...

This video illustrates how to Can Fruits and vegetable from your garden and the illustrations is followed in following steps-

Are you bored with ordinary meals? Why not tap into your adventurous side and try Starfish? Yes, that's right, those cute little fish that you see on the sand - you can eat them! So, if you are interested, check out this video and master the techniques needed to eat these spiny sea creatures.

Use your magic skills to perform this hot trick at your next party. You Will Need

The biceps tendon attaches the biceps muscle to the radius. Learn how to diagnose and treat a biceps tendon tear in this medical how-to video. Usually the area is painful, swollen and bruised.

Tim Carter shares some insights about vapor barriers and how to install them on your next project. This easy-to-understand video will show how to install new water infiltration barriers which will protect your house.

This video lesson introduces a basic philosophy on chicken pickin' or country playing. For country guitar playing, you don't need to use much in the way of effects, just a tiny bit of reverb and compression. Country isn’t dependent on one set of scales, like rock or blues. To play country, you must play over the chords much like a bluegrass or jazz player. It is no coincidence that many country players are also jazz players and vice versa. Every chord has different lines, chord shapes, or rif...

This video shows us the method to make a universal motion alarm to protect your home. You will need a reed switch with an alternating contact, a 9V battery with a battery clip, a switch, a buzzer, a small plastic box and a magnet. When a magnet is brought near the reed switch, it switches to the other contact and the switch is open. If the magnet is removed, the switch is closed and the buzzer starts ringing. Make the circuit with correct polarity for battery and the buzzer. Make a hole in th...

Many acoustical or popcorn ceilings that were put in, in the 1970's, contained asbestos. If you are unsure about the contents of the ceiling take a piece and put it in a plastic bag and send it to a lab for testing. Once you know that the ceiling is asbestos free and you are ready to take it down, start by turning off the power to the room. Next put down a plastic drop cloth to cover the floor and furniture in the room and protect it from the water that you will be using in this process. Tape...
New to Windows? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to protect Windows from viruses without an antivirus software.

Learn how to use a coffee filter for more than making coffee. Discover the versatility of coffee filters by learning all the things they can do besides straining your java.

It is well documented that what you say and do online is tracked. Yes, private organizations do their best to protect your data from hackers, but those protections don't extend to themselves, advertisers, and law enforcement.

The camera punch hole on the S10 has gotten our creative juices flowing more than any notch ever could. First, we saw wallpapers that served to camouflage the cutout or even accentuate it. Now, if you want to go the opposite direction and highlight your S10's camera hole, there's an app that turns it into a circular battery meter.

By default, there aren't many customization options for the notification badges on iPhones — you can either leave the numbered red bubbles there, or turn them off. But thanks to a new jailbreak tweak, you can now give your badges a unique look with new functionality.

Augmented reality is really picking up steam as a tool for marketing departments to pitch their products.
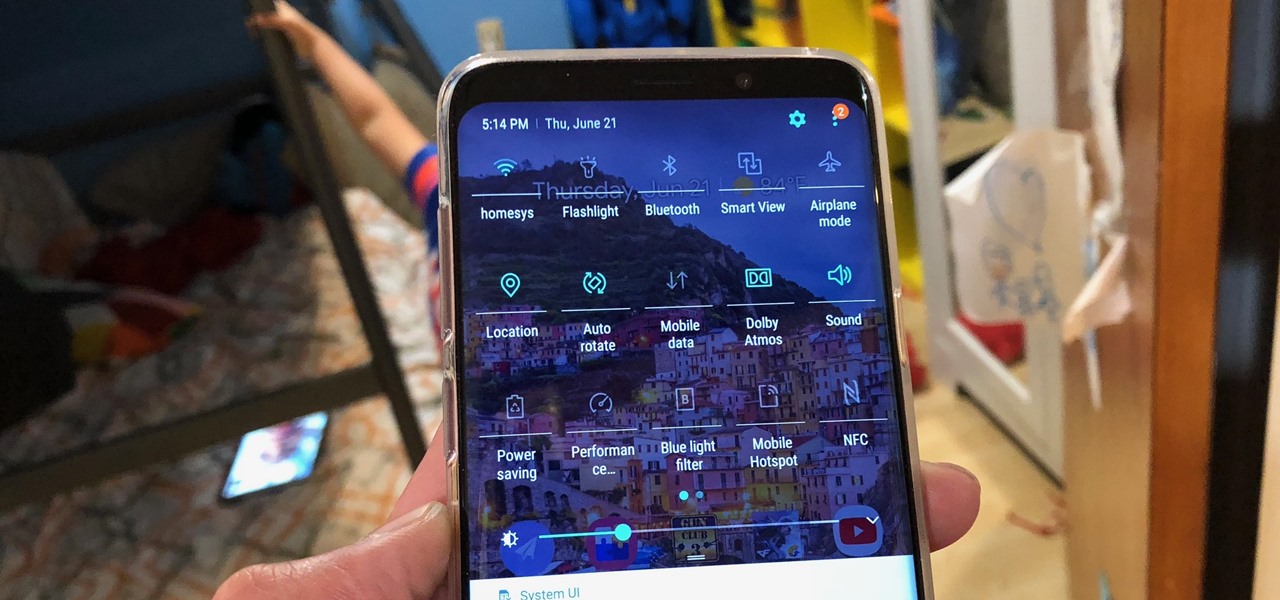
With the re-emergence of Samsung's Good Lock app, you're once again able to tweak parts of your Galaxy's interface with no root or major modifications required. One add-on in particular even lets you fully customize the Quick Settings panel on your S8, S9, or Note 8 in a full spectrum of colors to truly make it your own.

As of 2016, there are approximately 1.85 billion Android smartphones worldwide. This growing popularity has led to an increasing number hacks and cyber attacks against the OS. Unfortunately, Android users need more protection than what is offered by Google. The good thing is that there are a number of options available.

You may have seen news reports over the last two days detailing a major security flaw in virtually all smartphones. The devices that are at risk are not limited to either iPhone or Android — all of us are affected. If you want to make sure your smartphone and its data stay secure, there are a few steps you can take.

When it comes to security, Apple is usually at the top of the pack when it comes to your personal data, minus a few embarrassing flaws here and there. However, a new iOS security concern has been discovered that protects your data less than it did before — and Apple designed it like that.

Welcome back, my tenderfoot hackers! WordPress-based websites are among the most numerous on this planet (maybe other planets too, but I can't vouch for that). According to WordPress's own website, WordPress powers 23% of the top 10 million websites. That's approximately 2.3 million sites using WordPress!

With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...