Welcome back, my hacker novitiates! In an earlier tutorial, I had introduced you to two essential tools for cracking online passwords—Tamper Data and THC-Hydra. In that guide, I promised to follow up with another tutorial on how to use THC-Hydra against web forms, so here we go. Although you can use Tamper Data for this purpose, I want to introduce you to another tool that is built into Kali, Burp Suite.

Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world!

Most of you already know that a zero-day exploit is an exploit that has not yet been revealed to the software vendor or the public. As a result, the vulnerability that enables the exploit hasn't been patched. This means that someone with a zero-day exploit can hack into any system that has that particular configuration or software, giving them free reign to steal information, identities, credit card info, and spy on victims.

If you struggle with deciding which wine you should buy for an intimate dinner, or the type of beer with the highest alcohol content that doesn't taste like tree bark, then check out some of these great alcohol-friendly apps to make better booze decisions.

With all of the different websites we use in our day-to-day lives, keeping track of our numerous login credentials can start to become a hassle. This has created a market for password managers that aim to centralize these account credentials and generally streamline the process of logging into our favorite sites.

Welcome back, my amateur hackers! Many of you here are new to hacking. If so, I strongly recommend that each of you set up a "laboratory" to practice your hacks. Just like any discipline, you need to practice, practice, and practice some more before you take it out to the real world.

Sometimes, it helps to be prepared before jumping into a new relationship; look before you leap! To have a healthy relationship with someone who has an STI, it is advisable that you enter the relationship knowledgeable about sexually transmitted infections and what your risks might be.

Welcome back, my tenderfoot hackers! I have written many tutorials on hacking using Metasploit, including leaving no evidence behind and exploring the inner architecture. Also, there are my Metasploit cheat sheets for commands and hacking scripts.

Welcome back, my greenhorn hackers!

Welcome back, my greenhorn hackers! Although we have focused primarily on technical hacks here, social engineering can sometimes be especially effective. This one requires a bit of technical skill, but not too much. In addition, it's limited by how specific a target you can choose—but it will work.

Welcome back, my hacker apprentices! To enter the upper echelons of hackerdom, you MUST develop scripting skills. It's all great and well to use other hacker's tools, but to get and maintain the upper hand, you must develop your own unique tools, and you can only do that by developing your scripting skills.

After much hype and even more leaks, the HTC One M8 has finally been unveiled at the company's New York release announcement.

Welcome back, my tenderfoot hackers! I recently began a new series on digital forensics to help tenderfoot hackers from being detected and ultimately, incarcerated. In this installment of that series, we will look at recovering deleted files. This is important to hackers because you need to know that even when you delete files on your computer or on the victim's computer, a forensic investigator can usually recover them.

The space on your phone is extremely valuable, so getting the most out of your screen real estate can help you out when multitasking or for just making your device feel bigger. One thing that is often overlooked when it comes to saving space on the screen is the keyboard.

If you've been using Google's hidden App Ops to lock down and prevent some of your Android applications from exposing your privacy, then think twice before updating to the new Android 4.4.2 software.

Welcome back, my novice hackers! My recent tutorials have been focused upon ways to NOT get caught. Some people call this anti-forensics—the ability to not leave evidence that can be tracked to you or your hack by the system administrator or law enforcement.

Welcome back, my tenderfoot hackers! In some of my past articles, I've shown numerous ways of embedding a listener/rootkit on a remote system, including buffer overflows of the operating system, getting the victim to click on a link to our malicious website, and sending a malicious Microsoft Office and Adobe Acrobat file.

Yes, you read that right—you can now get Google Maps back on your iPhone again. It may not be officially replacing Apple's notorious Maps app, but it sure is a sight for sore eyes.

All of my hacks up to this point have been operating system hacks. In other words, we have exploited a vulnerability usually in an operating system service (SMB, RPC, etc.) that all allow us to install a command shell or other code in the target system.

Your first bank account can be exciting and confusing at the same time. Check out this video and learn how to manage your money and accounts so you don't wind up in the red. You don't have to earn an MBA to make good financial decisions; this video offers plenty of suggestions to keep your accounts on track.

Think of your brain like a muscle, if you train it correctly and diligently, it will perform at its top capacity. The retention of information is a skill like any other that can be improved with some practice and even rest when appropriate.

When you're a writer with work published across various online platforms, building a portfolio of your work can be pretty time-consuming. That's where Authory comes in.

We all know Google keeps a history of everything we do on our phones unless we say otherwise. However, you might not realize just how detailed it is until you check it for yourself — even the actions you do in each app are tracked by default.

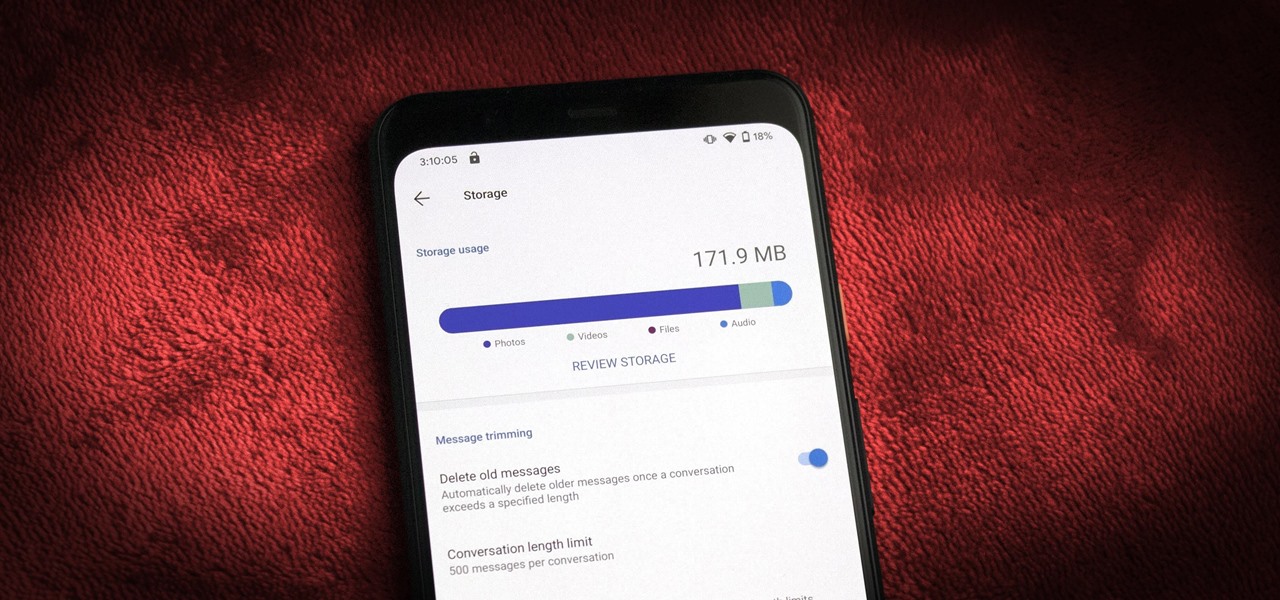
Thanks to backups, Signal conversations can span over multiple years and multiple phones. These archives can get rather large as you share photos, videos, and other files with friends. But between the other apps and large files on your phone, you might not be able to afford to keep all those messages.

After stealing the show at the HoloLens 2 launch and starring in Qualcomm's unveiling the Snapdragon XR2, holographic video conferencing app Spatial has landed a leading role in Magic Leap's second act with the enterprise segment.

As the stigma of online dating fades and swiping potential suitors on your phone becomes the new norm, one very real issue that you may have to deal with is catfishing: the act of being deceived by a fictional online persona. Although dating apps do their best to weed out fake accounts, a few of them slip through the cracks and take advantage of innocent people just looking for a connection.

In a world where augmented reality is becoming the hero of the movie marketing, Universal Studios has decided to use the technology to reinvent the traditional movie trailer, a time-tested tactic of film promotion, in support of the forthcoming Robert Zemeckis film, Welcome to Marwen.

With HoloLens and its enterprise-focused software offerings, Microsoft continues to make an impression on companies looking to adopt augmented reality, with Toyota Motor Corporation among the latest.

Facing mixed reviews for the Magic Leap One, Magic Leap has already returned to the lab to improve on the device's successor.

With the arrival of iOS 12, Do Not Disturb has received long-overdue enhancements to make the feature more user-friendly. Among these changes is a subtle but incredibly convenient feature that helps ensure you remain undisturbed for short periods of time to more focus on your task at hand — without having to worry about turning it off manually or messing with complicated settings.

Samsung emphasized its goal of streamlined user experience with the unveiling of the Galaxy Note 9, highlighting the flagship's capabilities of seamlessly connecting with other devices. The Note 9's DeX mode makes it easier than ever to interface with a wide array of displays and monitors.

Augmented reality experiences created in Lens Studio now have a permanent home in the Snapchat app. On Tuesday, Lens Explorer will begin giving users access to a scrollable screen full of a variety of new Lens Studio creations.

Kings of Soccer recently soft launched in the Netherlands and a few other countries, garnering positive reviews from the mobile gamers who've experienced it. With the 2018 FIFA World Cup now in full swing, we wanted to let you in on a little secret: You can play Kings of Soccer right now ahead of everyone else, regardless of where you live.

With developers chomping at the bit to play with ARKit 2.0, Unity has updated its ARKit plugin to enable access to the new augmented reality superpowers of the toolkit.

With the announcement of ARKit 2.0 at WWDC 2018, Apple is bringing some powerful new capabilities to mobile augmented reality apps this fall.

Augmented reality headset maker Meta Company unveiled Meta Viewer, its first software application, during its keynote at the Augmented World Expo in Santa Clara on Wednesday.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

During Snap Inc.'s quarterly earnings report, released on Tuesday, the company disclosed that it snagged a revenue total of $230.8 million for the first quarter of 2018, an increase of 54% compared to last year, largely fueled by its augmented reality offerings and other advertising products.

The business of enabling the development of augmented reality experiences appears to be as lucrative as AR app development itself.