
Macramé: The Art of Creative Knotting (Book Review).
The book that started it all (published in 1967). When Virginia Harvey wrote this book, she remarked that macramé was almost a lost art...


The book that started it all (published in 1967). When Virginia Harvey wrote this book, she remarked that macramé was almost a lost art...
Multitasking has traditionally been one of Android's strengths. As the first mobile operating system to introduce true multi-process management, it even took things a step further after version 4.0 by dedicating a button to your recently-used apps.

After lots of anticipation and leaks, the LG G3 has been unveiled. Sporting a gorgeous 5.5" Quad HD display, the first of its class for smartphones, this flagship device is ready to put some scare into Samsung and HTC. It's currently available for purchase from AT&T and Sprint, and for preorder at T-Mobile and Verizon Wireless.
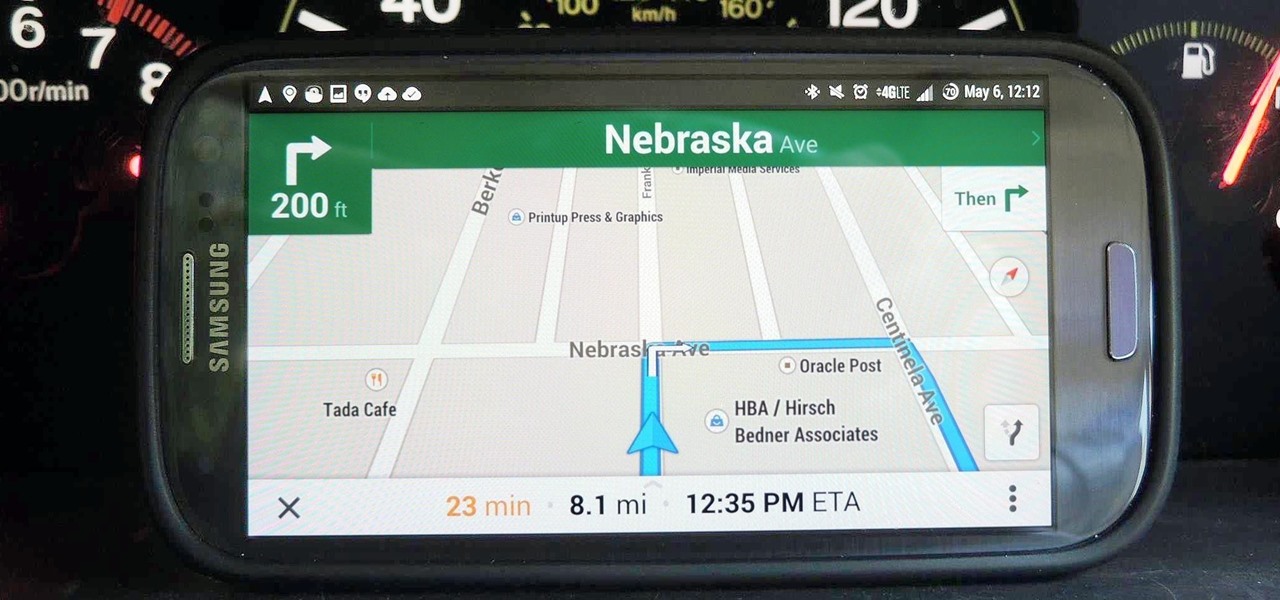
This week, Google sidestepped their usual "Update Wednesday" strategy by dropping a huge update to their Maps app for both Android and iOS. We're accustomed to seeing new features and bug fixes to their stable of apps on Wednesdays, but today's Maps update was presumably big enough to get its own release day (it's Tuesday, folks).
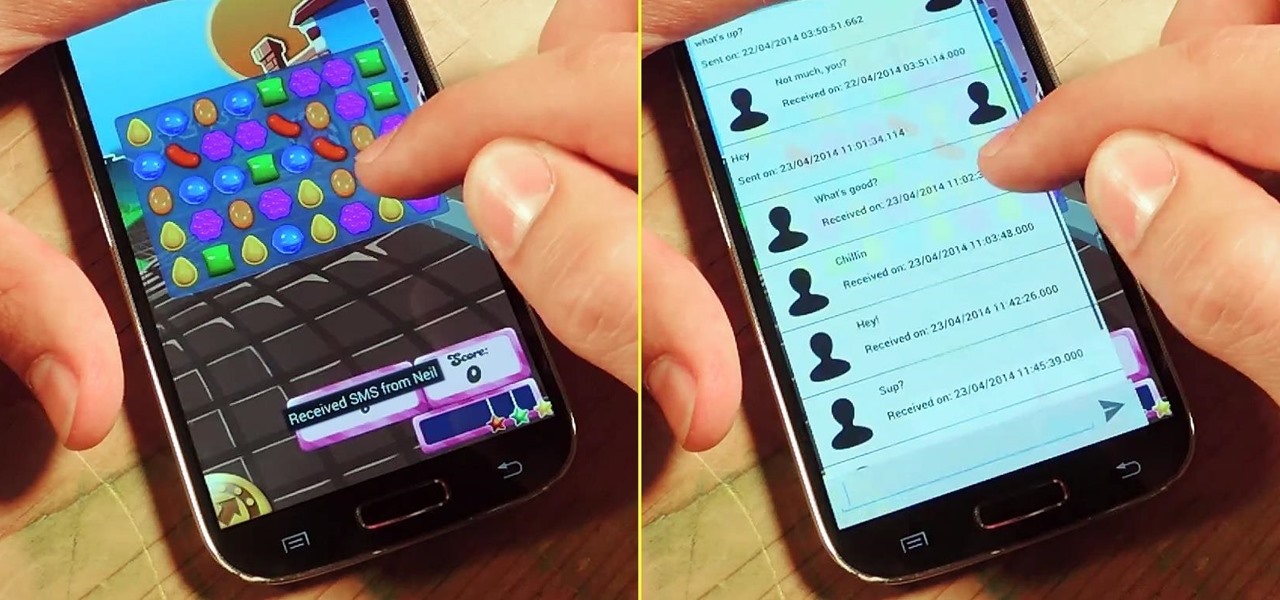
I'm a textaholic, as I've said many times before, but even textaholics forget to respond sometimes. When I'm watching a YouTube clip or devouring delicious snacks in Candy Crush Saga, I'll often ignore incoming texts and forget to respond later.

Google's new camera, aptly named Google Camera, has been all the rage since it was released onto Google Play last Friday. The main reason is the amazing Lens Blur feature that adds depth-of-field Lytro effects to photos, without the use of any expensive accessories or extra hardware, like on the new HTC One M8. The camera does this by utilizing a depth map through the processing of multiple images. Frame your photo, move the camera (phone) in an upward tilt or motion, and the software capture...

April Fools may be over, but any day is a good day to prank someone, and the best time to do it is when everyone's eyes are glued to the television.

Welcome back, my greenhorn hackers! In my continuing effort to demonstrate to you how to hack the ubiquitous Windows 7, we will going after that notoriously vulnerable Adobe Flash that is on nearly every client Windows system (you are not likely to find it on servers).

Seemingly lost in the fanfare of the numerous features and specs of the Nexus 5 were a few highly innovative and handy add-ons—a low-power step detector and step-counting sensor—useful for tracking fitness data.

The Academy Awards, commonly referred to as The Oscars, are airing this weekend. If you're a movie buff or just want to watch the dimes walking on the red carpet, The Oscars is not to be missed.

Welcome back, my budding hackers! As you know, I firmly believe that to be a true professional hacker, you need to be proficient in Linux. This is for a number of good reasons.

Welcome back, my greenhorn hackers! In a previous tutorial on hacking databases, I showed you how to find online databases and then how to enumerate the databases, tables, and columns. In this guide, we'll now exfiltrate, extract, remove—whatever term you prefer—the data from an online database.

Welcome back, my aspiring hackers! One of those areas of Linux that Windows users invariably struggle with is the concept of "mounting" devices and drives. In the Windows world, drives and devices are automatically "mounted" without any user effort or knowledge. Well, maybe a bit of knowledge. Most Windows users know to unmount their flash drive before removing it, but they usually think of it as "ejecting" it.

Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensics. In other words, what can a network forensic investigator learn about the attacker during an investigation and how.

Automation applications bring the future a little closer. If you've seen Minority Report or other futuristic sci-fi movies, the intrigue of having your electronics work independently is something we can all appreciate.

Overall, I love the Nexus 7 tablet, but one thing that I truly dislike about it is having to press the Power/Lock key to lock my screen.

With over a million apps available in the App Store, you'd think that Apple would have come up with a better way to organize them on your iPhone.
I remember how fast my Nexus 7 was the first time I turned it on. Boy, do I miss it. Now my tablet is pretty buggy and crashes happen frequently, and I'm sure that goes for many of your Nexus 7s as well. Even if you upgrade to the new Nexus 7 next week, it will eventually develop similar issues.

Welcome back, my hacker wannabees!

Welcome back, my eager hackers! In recent blogs, I've demonstrated how to grab password hashes remotely using Metasploit's meterpreter and pwdump. Once we have the Windows passwords from the SAM file, we can then crack these hashes using tools such as Cain and Abel.

Welcome back, my neophyte hackers! Several of you have written me asking how to crack passwords. The answer, in part, depends upon whether you have physical access to the computer, what operating system you are running, and how strong the passwords are.

So, you've finally converted from an iPhone to a Samsung Galaxy S3 smartphone. Great. Only now you're overwhelmed with the unfamiliar look and feel of the Android operating system.

Welcome back , my fledgling hackers! Lately, I've been focusing more on client-side hacks. While web servers, database servers, and file servers have garnered increased protection, the client-side remains extremely vulnerable, and there is much to teach. This time, we'll look at inserting a listener (rootkit) inside a PDF file, exploiting a vulnerability in Adobe's Reader.

When was the last time you bought a CD? Most of us listen to music through a number of digital channels—MP3s, Internet streaming services like Pandora and Spotify, and satellite radio, to name just a few.

SNAP. That's the sound of your Samsung Galaxy S3's camera going off. Not that big of deal, unless you're trying to take some top secret pics or some candid shots of your friends. The shutter sound gives you away, and the next thing you know, you're deleting pictures. On most other smartphones, if the users turns the phone on silent or vibrate, the shutter sound is killed. If that doesn't do the trick, usually muting the shutter sound itself in the settings will do the trick. But for some of y...

Every year, Black Friday gets a little more insane. People get up at ungodly hours, wait in lines forever, and get into some of the most ridiculous fights you've ever seen. All in the name of saving some cash. Everyone loves saving money, but without a game plan, you could end up missing all the good deals and going home with nothing. Luckily, the Internet is here to take some of the stress out of holiday shopping. With these sites and apps, you can find out about all the best deals before yo...
There's been a lot in the news lately about tracking devices, and it's been pretty much all bad. They can be useful if your car gets stolen, but if you weren't the person who installed it, chances are you don't want it there. Just type "GPS tracking device" into Google and on any given day you'll find an article about someone who got busted by one of these things. Even if you don't have to worry about getting into trouble, you still don't want people following you. Here's how to make sure you...

It's summer, which means vacations, barbeques, and, most importantly, no school. But that doesn't mean you can't learn something while you lounge by the pool. Schools and organizations all over the country are offering online courses taught by real professors—for free.

Review these simple steps to fold your own origami fancy box. These visual guidelines will help you through some of the more difficult folds, but you may want to look at an instruction booklet as well. There are many versions of the traditional Japanese origami fancy box.
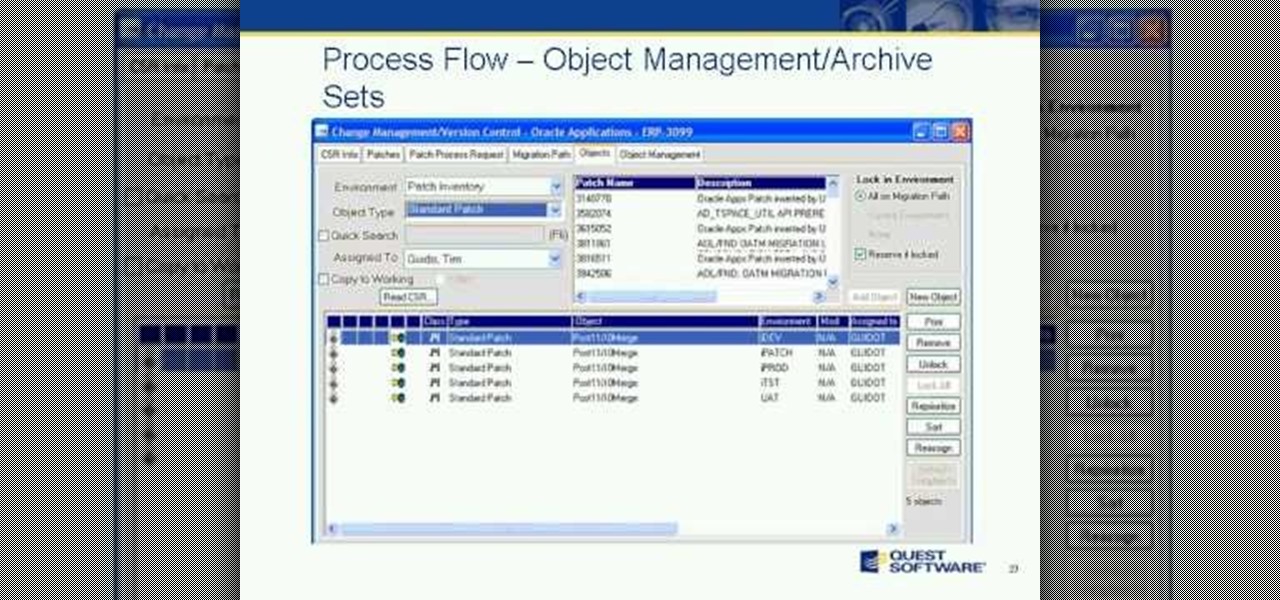
Join us and guest speaker, Cary Pochek - ERP Project Manager at Curtiss-Wright Corporation, as we discuss the importance of change lifecycle management when dealing with Oracle E-Business Suite implementations and upgrades. We will focus on best practices around:

In the aftermath of the unindicted police killings of Michael Brown and Eric Garner, we've been told that the system worked as intended. When our legal system's outcome is at conflict with what a majority of Americans believe is just, it's clear that some changes are needed. But what specifically needs to change? And what can an average citizen with a moral and just cause do to prevent these kinds of tragedies from repeating themselves again and again?

I am an English major physically allergic to all algebraic formulas, so you're unlikely to get any help from me when it comes to solving any expressions. But in the glorious technological age we live in, there are plenty of apps that actually make math and problem solving fun, even a little bit addictive.

Greg French talks to us about the different ways to reboot a computer to resolve issues in the computer. The first way is by pressing F8 key while startup after rebooting the system. When you insert a wrong driver for video card or something, sometimes when you boot the computer, it gives a black screen. Now he says you can resolve this problem by rebooting the computer and pressing the F8 key while startup. This will take you to a menu selection where you should select 'Safe Mode' and hit en...

In this video, watch as film studies graduate and movie critic Amy Wallace teaches how to be a movie critic. Learn how to research films, how to watch movies at home and in theaters with care, how to take notes during a film, how to reflect on a movie, the importance of honesty, the of positive, and the art of negative in movie reviews, and how to deal with reviewers' remorse. All good art needs good critics to survive, grow, and improve. Watch these videos and start improving the art of movi...
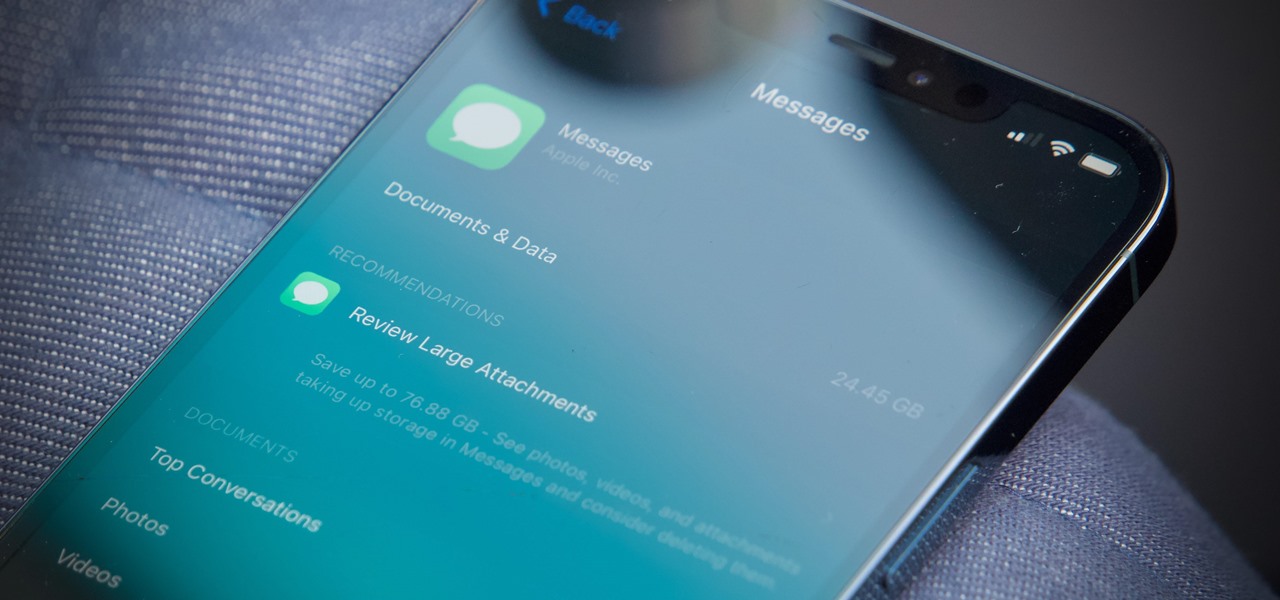
When iOS starts barking at you that you've run out of iCloud or iPhone storage, a quick trip to your settings to see what the culprit is may show that Messages is one of the worst offenders. But if deleting message after message doesn't free up your storage much, it's likely because "Messages" doesn't really mean messages.

Having found success in video games and a hugely popular Netflix series, The Witcher franchise is now on the hunt for the coin Pokémon GO has earned in location-based augented reality mobile games.

Apple has an excellent reputation for its privacy and security policies. That said, it isn't a perfect reputation. Take Siri, for example. The helpful iOS assistant isn't just communicating with you — Apple saves and listens to a history of your Siri interactions. If you don't want Apple storing your Siri history forever, there's something you can do about it.

Quietly, while the rest of the world was engaged in pandemic and political concerns, a few weeks ago Facebook casually upgraded its Spark AR platform with what it calls Unified Effect Publishing.

When Facebook launched its first hardware products last year, the Portal and Portal+ smart displays, the company mostly touted its video-calling features as it faced off against Amazon and its Echo Show.

The worlds of augmented reality and virtual reality are closely linked in many ways. That means it's smart for AR insiders to keep a close on new developments in VR. If you have been paying attention, you know that Oculus CTO John Carmack is one one of the most important thinkers in the VR space.