The race for the future of the automative world has never been tighter, with reports earlier this week that Tesla is now almost as valuable as Ford. The neck-in-neck companies are focused on the same next big step for automobiles: the driverless car.

Dynasty Warriors has finally been unleashed on the world of mobile gaming. The latest installment in the popular series is called Dynasty Warriors: Unleashed, and it sends you rampaging through armies using a variety of devastating attacks, all while collecting and upgrading over 80 unique characters from the Dynasty Warriors series. Each offer their own unique abilities, which lets you create the ideal team to take on the seemingly endless hordes coming your way with cold, cruel efficiency.

Disney Chairman and CEO Bob Iger has out and out rejected Virtual Reality (VR) as a component of any Disney Theme park. While Knott's Berry Farm, why-hasn't-this-chain-shut-down-yet Sea World (seriously, RIP Tillikum), and Six Flags have all invested in VR to help spice up their parks in this theme park depression period, Iger has "ordered his team not to even think about it." Iger instead is very much onboard the Augmented Reality (AR) train.
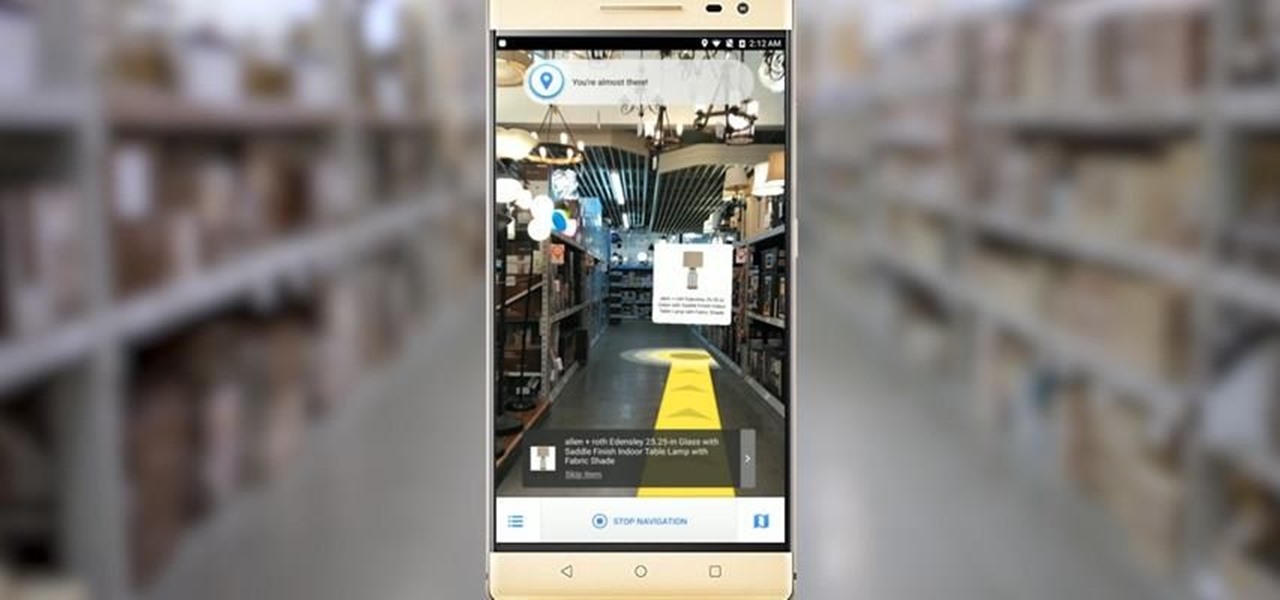
Lowe's Home Improvement laid another brick in their augmented reality foundation with today's announcement of a new app for Tango-enabled smartphones.

Not only has there been difficulty finding consensus on a name for driverless, autonomous, self-driving, or automated vehicles, there is also the issue of what we actually mean when we say a vehicle is self-driving, automated, and so on.

Google's Gboard is by far the most popular keyboard available right now. Gboard lets you search almost anything—from regular Google searches, to emojis, and even GIFs—just by using your keyboard. The app even lets you share search results, saving you a great deal of time, which would've otherwise been spent juggling between apps and programs.

The Huawei Nexus 6P was released a little over a year ago, but despite doing moderately well in sales, the device has had more than its fair share of issues. When first released, there were numerous reception and memory management difficulties that left users extremely frustrated, though, those problems were solved with updates pushed by Google.

Kazendi, a London-based HoloLens development and rapid prototyping studio, just released a new iOS app in Apple's App Store that lets developers stream HoloLens applications live from the headset to an iPad or iPhone. It's called HoloStream, and is the first iOS/HoloLens crossover app we've seen so far.

If we learned anything from Mulan, it's that "the flower that blooms in adversity is the most rare and beautiful of them all." Well, these have been a trying couple of weeks in the US, hence the need for a blooming marshmallow flower.

Koji is a culture made up of a certain fungus (mold) called Aspergillus oryzae, which has been used to ferment rice and soybeans in Japanese, Chinese, and Korean kitchens for centuries. Koji can actually have other involved fungi, but Aspergillus oryzae is the most common, and therefore the names can be used interchangeably. Its end purpose is to enhance the flavor of items like soy sauce, sake, and miso.

New Android versions have always been released on a fairly regular schedule—in late Fall, Google debuts a new Nexus device, while simultaneously publishing the next iteration of the world's leading mobile operating system. But things are different this year, as we now have numerous indications that Android Nougat could be released as early as August or September.

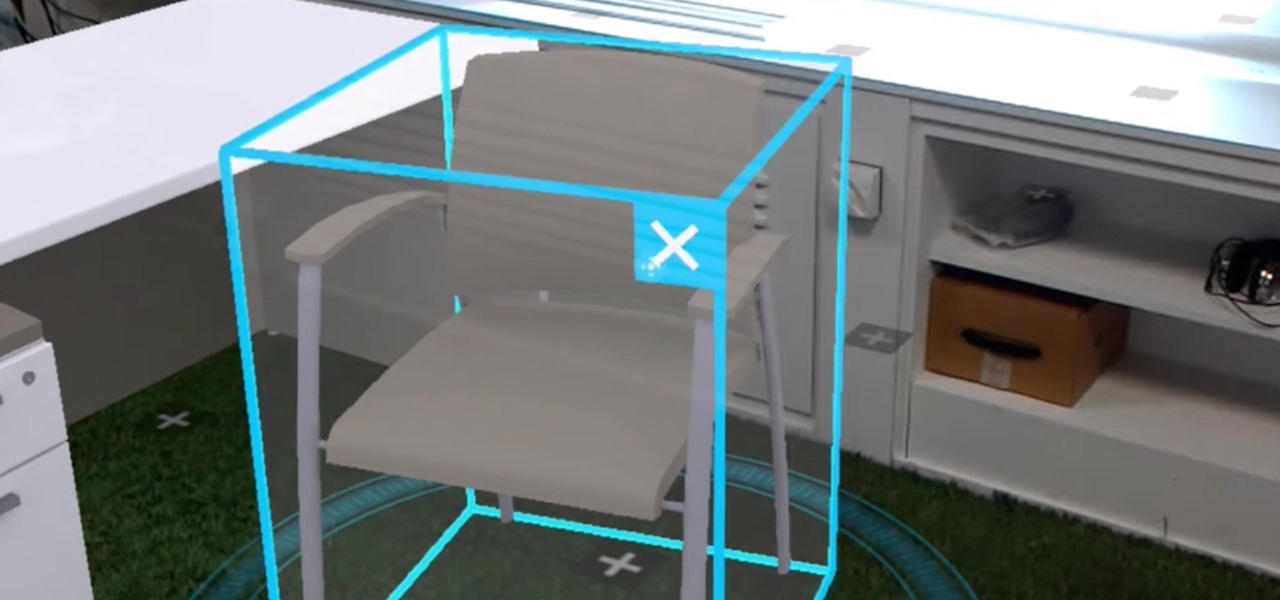
When figuring out how to arrange your furniture in a new room, you traditionally have to measure everything and use your imagination. HoloPlanner has a better idea: just place holographic furniture in the room so the Microsoft HoloLens can imagine it for you.

It's no secret that cauliflower is good for you—but not nearly enough people know that the best part about cauliflower is its insane versatility. Because its cooked flavor is so mild, it can be incorporated into a crazy amount of dishes and preparations.

Welcome back, my budding hackers! In this series, I have been trying to familiarize you with the many features of the world's best framework for exploitation, hacking, and pentesting, Metasploit. There are so many features, and techniques for using those features, that few pentesters/hackers are aware of all of them.

Welcome back, my hacker novitiates! Often, to hack a website, we need to connect to and exploit a particular object within said website. It might be an admin panel or a subdirectory that is vulnerable to attack. The key, of course, is to find these objects, as they may be hidden.

If you're a developer looking to get some exposure for your high-quality app, or if you're a user hunting for new apps and would like a chance to win a paid app at no cost, then Jack Underwood's new Promo Codes app may get you there, which you can install for free from the Google Play Store.

Welcome back to another episode of Java Tutorials, In today's tutorial, we'll be learning about what methods are, proper syntax when writing Methods, and why they are beneficial in a program's code.

I was fortunate enough to be visiting one of my college classmates in Columbus, GA last spring and saw two large bags of onions in his kitchen... but not like the ones you get at the grocery store. Two standing 50 lb. bags!

Simmering or poaching food is a total pain sometimes. The problems are numerous: a layer exposed to air often dries out and creates a gross skin that can ruin the texture of the sauce, the poaching liquid evaporates too quickly and causes the poached protein to burn, and so on.

This is my first tutorial on this website. So, if you think anything to be wrong, just place it in the comments.

Salad spinners are one of the more divisive kitchen tools out there. On one hand, they're incredibly easy, efficient, and useful. On the other hand, they're a single-use tool that takes up a lot of space.

Welcome back, my amateur hackers! With Halloween right around the corner, I thought you could have a little fun with your newfound hacking skills using a hack that is guaranteed to freak out your boss, teacher, coworker, friend, etc.
Hello Null-Byte community. First off: this my first post here on Null-Byte. Some of you may have already seen me in the comment section, to all others: Hi, I'm the new guy.

Welcome back, my greenhorn hackers! As all you know by now, I'm loving this new show, Mr. Robot. Among the many things going for this innovative and captivating program is the realism of the hacking. I am using this series titled "The Hacks of Mr. Robot" to demonstrate the hacks that are used on this program.

Here's a fact that everyone knows: avocados are delicious in guacamole, salads, and sandwiches. Here's a fact that's less commonly known: avocados are delicious in desserts, too.

Welcome back, my greenhorn hackers! One of the most important issues any hacker must address is how to get past security devices and remain undetected. These can include antivirus software, intrusion detection systems, firewalls, web application firewalls, and numerous others. As nearly all of these devices employ a signature-based detection scheme where they maintain a database of known exploits and payload signatures, the key is to either:

When you think about it, YouTube may actually have one of the largest music collections on the planet. This is why, at $10 per month, Google's new YouTube Music Key subscription is a solid value for many users, especially with its inclusion of Google Play Music.

I'm a firm believer that a sandwich is the ultimate food. It's filling, but not heavy; it has carbs, protein, veggies, and sauces; and it's easily customizable. Add that all up and you've got the absolutely perfect lunch.

For all that money spent on a new Watch, Apple could've given us more than just a charger and its case. I mean, the case is nice and all, but what realistic use is there for it? In all honesty, it'll probably find its way onto a shelf high above in the closet—but it doesn't have to.

Welcome back, my neophyte hackers! In previous tutorials, we learned how to steal system tokens that we could use to access resources, how to use hashdump to pull password hashes from a local system, and how to grab password hashes from a local system and crack them.

There are lots of great reasons for going out to a fantastic coffee shop for a cuppa. Coffee shops have a lovely ambiance, are a perfect place to meet with friends or do some work, and are a great excuse to get out of the house. Seeking out a perfect cup of coffee, however, shouldn't be one of the reasons that you hit up your local café.

Welcome back, my hacker novitiates! In an earlier tutorial, I had introduced you to two essential tools for cracking online passwords—Tamper Data and THC-Hydra. In that guide, I promised to follow up with another tutorial on how to use THC-Hydra against web forms, so here we go. Although you can use Tamper Data for this purpose, I want to introduce you to another tool that is built into Kali, Burp Suite.

Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world!

Apple's iPhone is one of the most popular, most expensive smartphones in the world, yet with a broken Home or Sleep/Wake button, it might as well be a doorstop. There are many different DIY ways to fixing a busted Home button, but the Sleep/Wake button (aka Power button) is a little more averse to DIY trickery.

For $35, there's hardly a better value in the online media player market than the Chromecast. Taking that sentiment a step further, if you factor in the promotions Google likes to offer with it, Chromecast practically pays for itself.

During class or while at work, it can take an immense amount of self-control to resist navigating over to Reddit. The link-aggregator and meme-warehouse makes it too easy to kill time... most of which you should be spending on various other tasks.

Most of you already know that a zero-day exploit is an exploit that has not yet been revealed to the software vendor or the public. As a result, the vulnerability that enables the exploit hasn't been patched. This means that someone with a zero-day exploit can hack into any system that has that particular configuration or software, giving them free reign to steal information, identities, credit card info, and spy on victims.

Add-on smartphone lenses are nothing new, but they have definitely gotten better as time goes on. Case in point: the Olloclip series of lenses for iPhones and Samsung Galaxy devices (the S4 and S5 only at the moment).

With all of the different websites we use in our day-to-day lives, keeping track of our numerous login credentials can start to become a hassle. This has created a market for password managers that aim to centralize these account credentials and generally streamline the process of logging into our favorite sites.

We've already told you how the Japanese pioneered growing specially shaped watermelons (including square, heart, and Godzilla egg). Now it turns out an organic farmer just north of Los Angeles is doing them one better.