If I could only eat one food for the rest of my life, it would definitely be potatoes. In fact, when I recently saw The Martian, I didn't feel that badly for Matt Damon. I mean, sure... he was stranded on a hostile planet, millions of miles from home. But he got to eat potatoes all the time! Pretty fair trade, if you ask me.

When using Linux, we often need to install new software, a script, or numerous large files. To make things easier on us, these files are usually compressed and combined together into a single file with a .tar extension, which makes them easier to download, since it's one smaller file.

Welcome back, my novice hackers! One of the most common questions that Null Byte readers ask is: "How can I evade detection by antivirus software on the target?" I have already talked about how AV software works, but to obtain a deeper understanding, what better way is there than opening up and dissecting some AV software?

If you haven't read the last article, feel free to stop by and give it a read, but abstaining from reading it will not, for the most part, be detrimental to your understanding.

Welcome, in this tutorial we shall we looking at creating a safe(r) way to back up your important files. The contents we will be covering are as follows;

Welcome back, my hacker apprentices! A you know, Mr. Robot is my favorite TV show this year, and not just for the realistic hacking. Rami Malek, the actor who plays Elliot, is incomparable in his depiction of a young man with social anxiety who is alienated from a superficial, materialistic society and wants to make a better world. I believe we will see a lot more of this actor in coming years.

I have a personal rule when it comes to an app's interface: If it doesn't follow Android's design guidelines, it was probably written with Apple's iOS in mind first and foremost.

Welcome back, my fledgling hackers! Let's continue to expand our knowledge of digital forensics, to provide you the skills necessary to be a digital forensic analyst or investigator, as well make you a better hacker overall. In your attempts to enter a system or network undetected, it is key to understand what a skilled forensic investigator can learn about you, the alleged hacker.

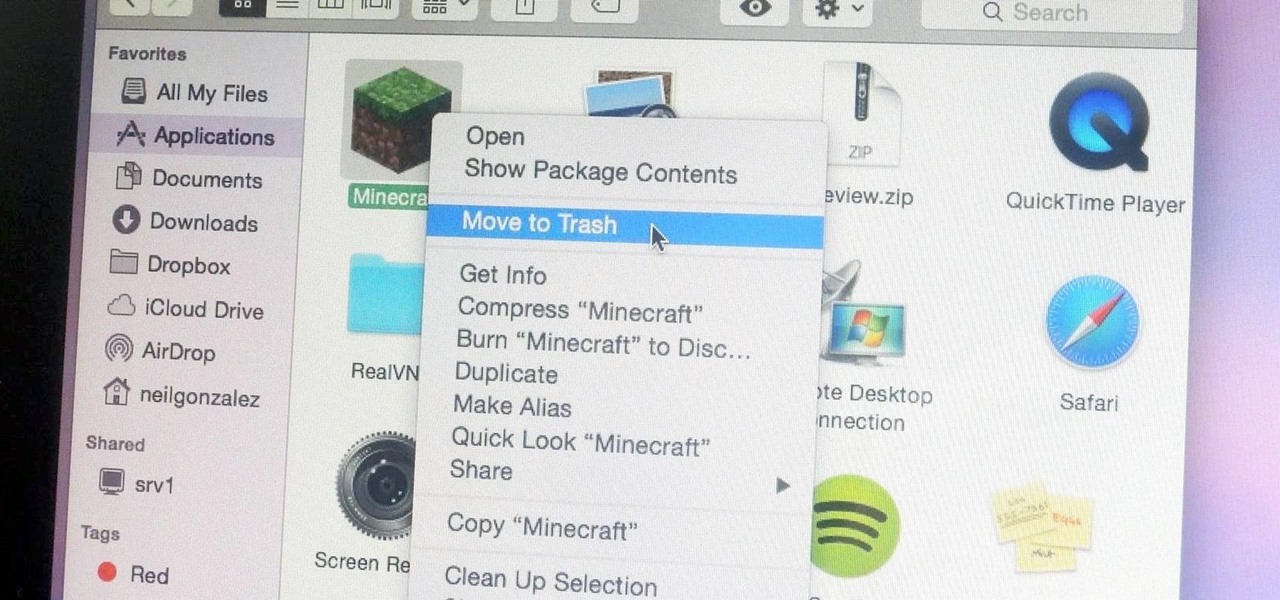
Uninstalling an app on your Mac isn't as straightforward as you would think. When you drag and drop an app into the Trash, then empty it, the main app itself may be gone, but many associated files and folders are left behind. So how do you get rid of them? There are a couple of ways.

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

Welcome back, my aspiring hackers! Although this article may have been better placed first in this series, I doubt that anyone would have read it when just starting out studying Linux. Now, that you are well into your Linux studies and have some familiarity with how it operates, I'd like to take this moment to explain the philosophy around the Linux operating system.

Seldom in recent history has a cyber security event caused so much media stir (maybe because it happened to a media company?) and international relations upheaval. Cyber security breaches seem to take place daily of major corporations, but the Sony hack seems to have captured the American imagination and, for that matter, the whole world's attention.

My years in the restaurant business have taught me many things. Some of those things are best left unsaid and other things require a PhD in vulgarity, but the one thing I learned that I keep coming back to night after night is that you do not have to spend a lot of money to drink excellent wine. This is especially true of champagne...I'm sorry, sparkling wines.

Telemarketers can be as terrifying as a villain from a horror film. Your phone rings with an unknown 800 number, and you immediately fill with a sense of dread. There's no way to get them to stop calling; you imagine the number appearing on your phone at all hours of the day and night, haunting you.

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

We all know that it's important to drink water regularly throughout the day. After all, it has so many benefits, including flushing toxins out of the body and maintaining kidney health and good bowel movements. Turns out that's only part of the story. While being properly hydrated is key to maintaining overall health, it's also a big component of maintaining and even increasing cognitive ability. Plus, drinking enough water regularly can help you lose weight, if you know when to drink it and ...

Welcome back, my novice hackers! The worst thing that can happen to any hacker is being detected by a security admin, the security technologies (IDS, firewall, etc.), or a forensic investigator.

Welcome back, my aspiring hackers! Those of you who've been reading my tutorials for some time now know that I am adamant regarding the necessity of learning and using Linux to hack. There is no substitute, period.

When Google introduced their new launcher alongside the Nexus 5, one of the most innovative features was the "always listening" voice search, meaning that at any time you were on your home screen, triggering a Google search was as simple as saying "Okay, Google."

Welcome back, my hackers novitiates! As you read my various hacking tutorials, you're probably asking yourself, "What are the chances that this hack will be detected and that I'll land behind bars, disappointing my dear mother who already thinks I'm a loser?"

While most people were worried about having the scariest costume when I was younger, I was always more interested in the candy. While everyone wasted time trying to perfect their costume, I was busy mapping out every detail in my city, finding the most efficient way of getting the most candy in my pillowcase(s) before the night ended. Although I'm long retired from the game, it's about time to pass along all of the tips and tricks I've learned from my youth for getting treats. So, here I pres...

Just because a problem is small or superficial doesn't mean it can't annoy the living crap out of you. Others may think you're overreacting, or even have the audacity to roll their eyes, but you're in your own personal hell.

The very first text message was sent on December 3rd, 1992 by Neil Papworth, an engineer for Vodafone, and it simply said "Merry Christmas." He may have jumped the gun on the whole Christmas thing, but you trying coming up with the first text message in history!

First of all, I would like you all to meet my good friend Iggy. There he is, in all his scaly reptilian glory. As you can see, he spends a lot more time on top of his cage than inside of it. You see, Iggy here doesn't deal well AT ALL with confinement. I don't know if it's possible for a lizard to be claustrophobic, but if it is possible, then Iggy definitely is. When his previous owner gave him to me, I tried to keep him in the cage, but I quickly realized that it was a bad idea. When confin...

TouchDevelop is a browser-based programming tool that allows anyone to build your own Windows 8 apps directly from any touchscreen device, including iPad, iPhone, Windows Phone, Android, PC and Macs. Once the script is created and the app proves to work, it can be placed in the Windows Store for free or purchase.

It turns out you CAN have your character in Star Trek Online take a seat in the captain's chair. If you stand on the chair, you can then use an emote in the chat box to have your captain take his seat, just like Picard or Kirk!

Drawing is easy for some, harder for others, but drawing letters is pretty simple for both the pro and novice artist. There's all kind of text styles you could conjure up, and they don't have to be boring fonts. Fire up your imagination to create different styles for drawing numbers and letters of the alphabet, adding individuality and pizzazz to names, messages, greeting cards and decorated items.

In this how-to video, you will learn how to plan an inexpensive wedding. First, you should look online, on television, and in books and magazines for great ideas to save money. You can even ask your friends for input on how to plan a wedding on a budget. First, keep a small notebook for writing down ideas. You will also need a priest or other clergymen for the ceremony. Look for churches or restaurants to have your wedding. Do not be afraid to shop around. Figure out how much you can spend an...

We spend all day on our feet and it doesn’t make it any easier having holes in your socks. Next time your sock has a hole you can have a little fun and fix it yourself. Grab your needles and do something nice for your feet today.

Bird watching is a great activity to do on your own or to spend time with the whole family. Look for the habitat, coloring, behavior and call of this beautiful bird and enjoy its beauty and soft cooing.

Redecorating your home can seem like an overwhelming task but it doesn’t have to be. You don’t need a professional as long as take into consideration the key elements such as your budget, the style you want and a color pattern.

Dry apples for that perfect project by following these steps. Apple aren’t just for eating. You can use sliced dried apples to add a little interest to your next craft project. Making the dried apple slices is half the fun and a great way to spend a lazy afternoon.

If you want to level up on Happy Aquarium, this is the way to do it… cheating. Simply use Cheat Engine to get everything you want in Happy Aquarium. Don't know how? Watch and learn.

A CNC router machine is probably the most useful tool a hobbyist can own, but the price for a CNC machine on the market is way more than the average hobbyist is willing to spend. You can build your own CNC with very basic tools, little knowledge of machinery, mechanics, or electronics, but be warned, these machines are inherently dangerous, so wear the proper protection and use common sense. At the very least, read the instructions and precautions on every tool you use.

Watch a 41 part series on Spore's Space Stage. How will you create the universe? With Spore you can nurture your creature through five stages of evolution: Cell, Creature, Tribe, Civilization, and Space. Or if you prefer, spend as much time as you like making creatures, vehicles, buildings and spaceships with Spore’s unique Creator tools.

There’s a good chance that you’ll be alone in life one day, and no... I’m not talking about a couch-bound, dateless loser with a pocket pussy and a bag of potato chips. I’m talking about alone. In the wilderness. Hungry. Cold. Lost. You can’t stay in one place too long, so it would be nice to have something to carry your belongings in. Maybe it’s post-apocalyptic land where you’re the sole survivor, and all the backpacks and rucksacks in the world are but mere ash. Either way, knowing this si...

There's more than one way to get free credits and discounts in the Google Play Store for apps, games, books, movies, in-app items, and other Play Store content. You may know a few of them — but some of these may surprise you.

When we think about operating systems, we tend to view them from the perspective of a user. After all, most of us have spent a substantial amount of time on our computers, and so we've become more than acquainted with the ins and outs of whatever system we have running on our personal device. But there is one operating system that, while being less commonly used on the user side, is behind a great deal of design and business technology: Linux.

Learning different coding languages can be difficult. You spend so much time mastering one and getting used to thinking along the channels you need for it that learning something new can sometimes be more difficult than starting from scratch. Starting from scratch, notably, is also difficult.