Two slices of whole-wheat toast with lots of butter. Two eggs, poached to a firm yet custardy texture. The yolks should absolutely not be hard-cooked and the whites should be tender, not rubbery. That's my idea of the perfect breakfast.

Welcome back, my neophyte hackers! I have already done a few tutorials on password cracking, including ones for Linux and Windows, WEP and WPA2, and even online passwords using THC Hydra. Now, I thought it might be worthwhile to begin a series on password cracking in general. Password cracking is both an art and a science, and I hope to show you the many ways and subtleties involved.

Welcome back, my neophyte hackers! Have you ever had a neighbor that you're certain is up to no good? Maybe you've seen him moving packages in and out at all hours of the night? Maybe you've seen people go into his home and never come out? He seems like a creep and sometimes you hear strange sounds coming from his home? You know he's up to no good, but you aren't sure what it is exactly.

Welcome back, my hacker apprentices! Metasploit framework is an incredible hacking and pentesting tool that every hacker worth their salt should be conversant and capable on.

Welcome back, my budding hackers! One of the most time-consuming, but necessary, activities in hacking is reconnaissance. Before we can hack a system, we need to know what operating system it's running, what ports are open, what services are running, and hopefully, what applications are installed and running.

Many people find Steampunk problematic for a whole host of reasons, not least of which is the glorification of an era of Western history that featured institutionalized slavery, racism, sexism, elitism, and many more -isms.

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

Let's say that you've got the look down, and you have your Steampunk props all ready to go. Congratulations! You're a Steampunk!

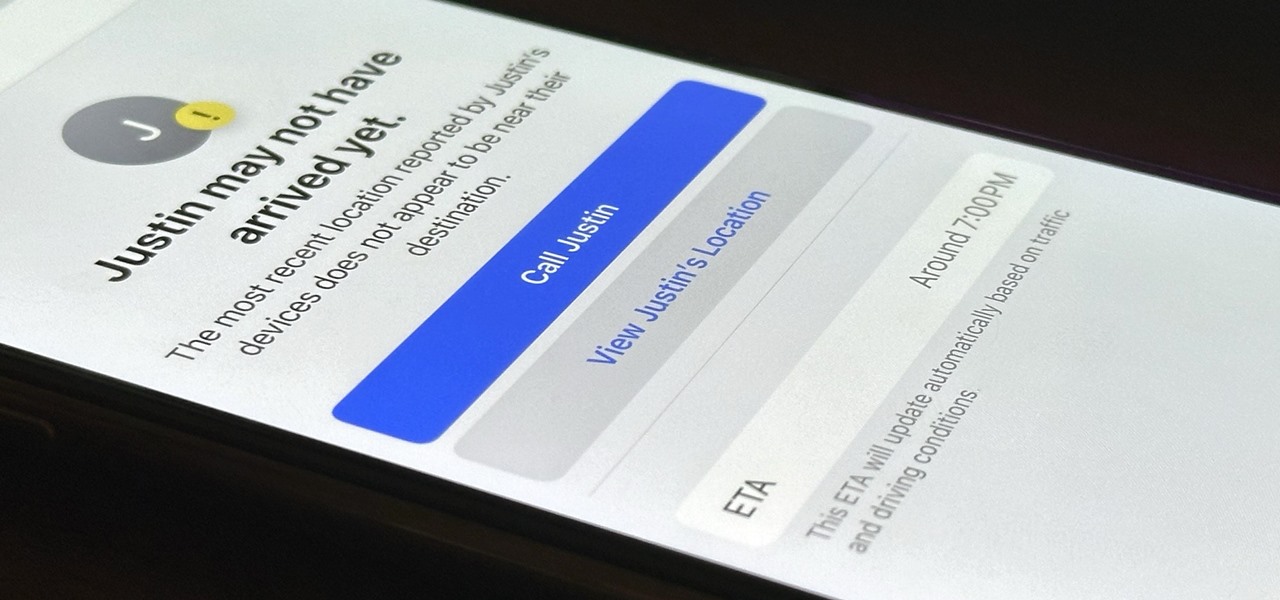
Check In is a new safety feature built into the Messages app that can automatically notify a family member, friend, another contact, or a group the moment you arrive safely at a destination, giving them peace of mind in knowing you're all right. If you never reach your stopping place, it will also send them clues to help them figure out what went wrong.

When you're a writer with work published across various online platforms, building a portfolio of your work can be pretty time-consuming. That's where Authory comes in.

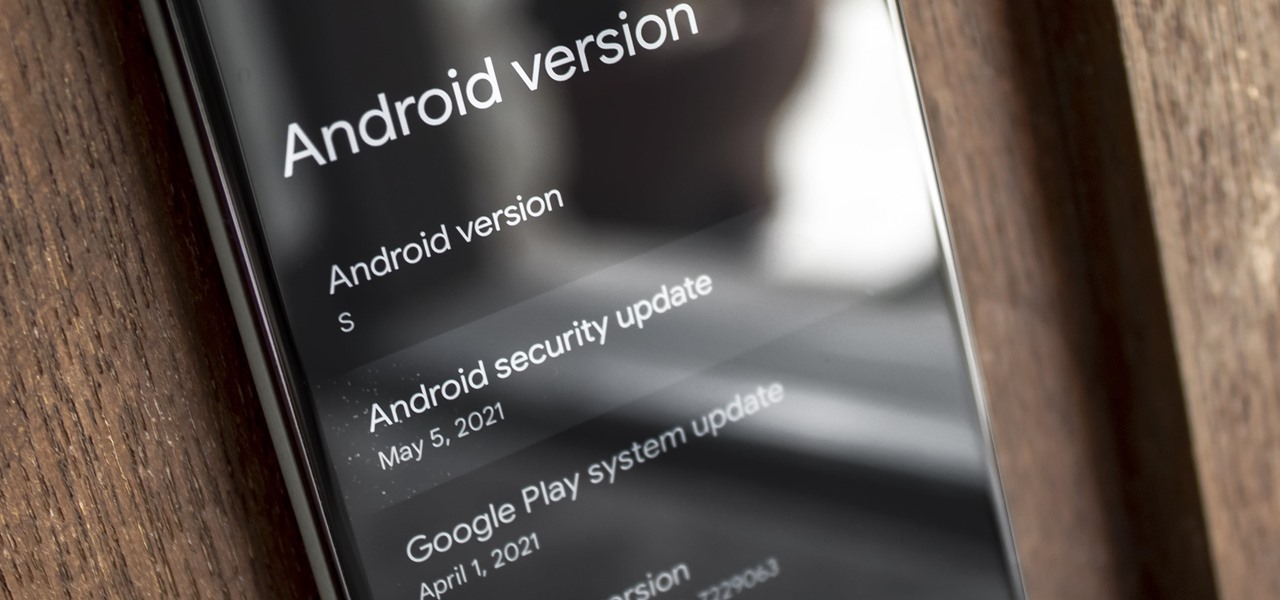
Numerous potential exploits are found for every operating system each month, and Android is no exception. Trouble is, lots of Android devices don't receive timely updates — but many are now getting regular monthly security patches to at least shore up these vulnerabilities.

When an iPhone is lost or stolen, it's imperative to start tracking it via Find My as soon as possible, whether that's from a computer, tablet, or someone else's phone. However, if it's stolen, there's a good chance the thief or robber turns on Airplane Mode, blocking all communication with the iPhone. If this is a scary thought, you can prevent thieves from accessing Airplane Mode altogether.

The race for the future of AR wearables gained steam this week with several pivotal developments. First, Apple, the subject of numerous reports and rumors regarding its purported AR headset, is reportedly eyeing an in-person unveiling of the device for later this year, rather than introduce it at its upcoming virtual Worldwide Developers Conference, which would usually be as good a time as any to make a big AR hardware announcement.

Just as the augmented reality industry grows, so too does the segment dedicated to creating experiences for the tools becoming available.

Google switched to gestural navigation in Android 9, and in removing the back/home/recents buttons, they were able to greatly reduce the size of the navigation bar at the bottom of the screen. However, there's still a white line, aka "The Pill," taking up space to show you where to start your gestures.

Google's version of Android is best described as AOSP with extra features. But while the Pixel's UI is rightfully praised for its simplicity, those "extra features" aren't as numerous as they are on other OEM skins like Samsung's One UI. Case in point, there's no real system-wide audio EQ.

For enterprise augmented reality platform makers, remote assistance apps represent one of the greatest opportunities to show off the power of immersive computing. These apps enable experts to guide front-line workers or customers with AR prompts and other content in the field of view of their smartphones or smartglasses.

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

Thanks to numerous smartwatch deals this holiday season, many people are receiving their first one. But what exactly can they do? In regards to fitness, quite a lot. With a growing list of sensors and software updates, these small devices can be the very thing you need to ultimately reach your fitness goals.

A good smartphone can be the perfect workout companion. You have music for motivation, videos for pushing through boring cardio sessions, GPS to keep you on course, and even an array of sensors for gathering data about your workout. But not all phones are created equal when it comes to helping you stay fit.

Imagine being able to play a video instantly on hundreds of thousands of devices across the globe. It's totally possible, as long as all of those devices have a Chromecast plugged in. When Chromecasts are left exposed to the internet, hackers can use add them to a botnet that can play YouTube videos at will. The "attack" is made even easier thanks to a simple Python program called CrashCast.

The music and sound effects that play in the background of any videos you edit helps set the tone, so it's essential to get it right. Enlight Videoleap, an extremely powerful and popular mobile video editing tool for iOS, lets you quickly and easily add audio from your iPhone and the cloud, but things can still get a little confusing when you have a timeline full of clips.

Whether we like it or not, our personal information and smartphones are tied together at the hip. The former needs the latter to deliver a personalized experience that matches our individual needs. This personal data, however, makes your phone a prime target for thieves of all sorts to turn your privacy into illicit profit.

Stories are everywhere in social media today, but that wasn't always the case. In 2013, Snapchat introduced the world to these temporary windows into our daily lives. Since then, stories have infiltrated other popular apps. However, to stand out, you can't solely rely on the app where the story will be posted. Instead, you need a suite of apps that can turn your story into something special.

These days, using Reddit on your iPhone is just as good, if not better, than Redditing on a desktop browser. While there's an official Reddit app for iOS, there are plenty of third-party clients that have similar features as well as custom perks to enhance the experience. But figuring out which Reddit client is best for your daily use can be a lot of work — work that we can make easier on you.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for a birthday, Christmas present, or other gift-giving reason, these also make great gift ideas.

People say that money makes the world go 'round. And it's no different in the world of augmented reality.

The iPhone XR offers a discounted experience compared to the expensive iPhone XS and XS Max. However, that lower price tag comes with some caveats, such as "Haptic Touch" in lieu of 3D Touch. If you think these two "touch" features are the same, think again. Before you get an iPhone XR, you'll want to know all the excellent features 3D Touch you might miss. Can you go without them?

The transcribing app can be an invaluable tool, especially if you're a student or are in a profession that relies on audio journals or interviews. These apps can convert important recordings like lectures and meetings into text for you to carefully read through to better comprehend.

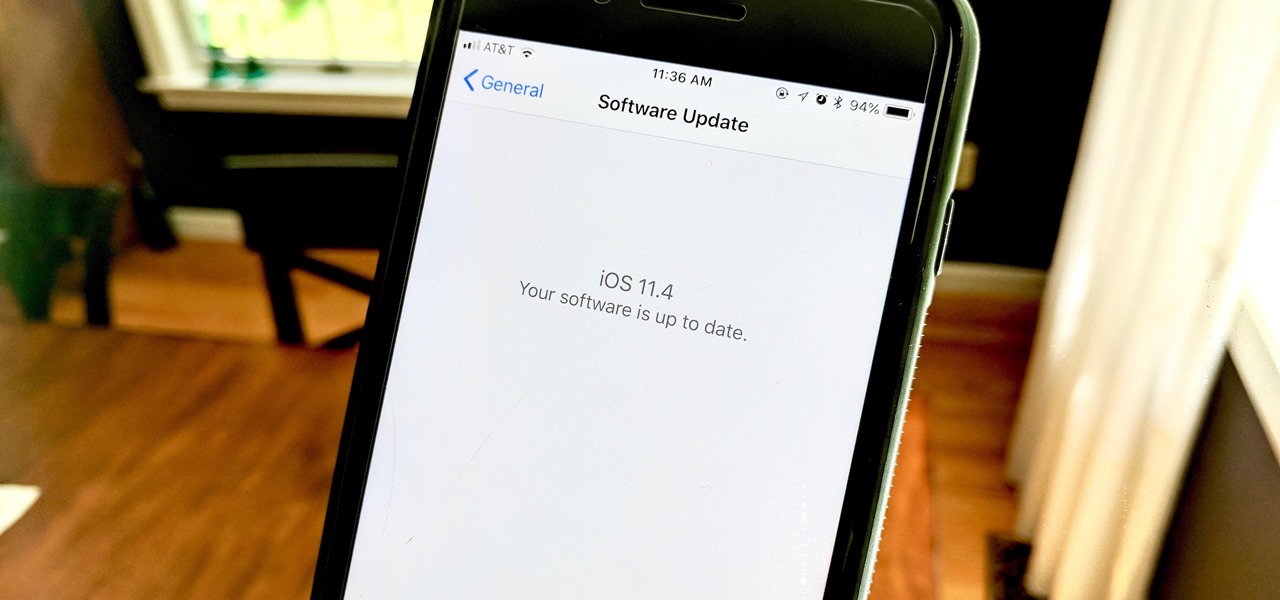
While there are at least five cool things coming in iOS 11.4, they may not be enough to get you to install the iOS 11.4 beta on your iPhone. Since its initial beta release at the start of April, there have been plenty of known issues and user-reported bugs to deal with. While bugs are to be expected with a beta, you may want to read these before installing this one on your iPhone.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

They're finally here — Samsung has officially revealed the Galaxy S9 and S9+, which run Android Oreo out of the box. Since we've spent plenty of time with the Oreo beta for the Galaxy S8, we already know about some of the best new software features coming to the Galaxy S9. Like previous updates, Samsung has enhanced its software with a fresh look and brand new functionality.

During a penetration test, one of the most important aspects of engaging a target is information gathering. The more information you have coming into an attack, the more likely the attack is to succeed. In this article, I'll be looking at SpiderFoot, a modular cross-platform OSINT (open-source intelligence) gathering tool.

Fight me all you want, but it ain't a party without alcohol—whether it's a Halloween party, Christmas party, dinner party, or even a damn wedding. (If you think that people will stick around after dinner for a dry wedding, then you're sorely mistaken.)

Right now is that magical time of year when the general public decides to embrace their inner fattie and get baking in the kitchen. Hello, pies and cakes and cookies and everything carbs. Goodbye, diets—see you in the next year, when you cripple us with unbridled guilt and longing.

Greetings all. Today I intend to append a new series to my mini-collection of posts. This series will consist of informative guides for the purpose of depicting certain aspects of the White Hat profession that I believe are of profound importance. Furthermore, I will keep this series simple for everyone to follow, regardless of your tech level. So without further ado, let's get right into it.

Windows 10 is officially here, and frankly, there's a ton of new features in Microsoft's latest operating system. From the return of the Start menu to the new Edge browser, Windows 10 can take some getting used to.

Did you know Kali 1.0.8? You probably did, and you probably know about the EFI boot option that has been added.