While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

With EA chief executive Andrew Wilson stating the official mobile version of Apex Legends won't arrive until the 2021 fiscal year, fans have to wait at least another year to enjoy their favorite battle royale game on the go. But for those who can't wait, there are ways to play the game on iPhone and Android right now.

If you store important, sensitive information on your iPhone in Notes, you'll want to be more careful. When Notes syncs across your iPad and Mac via iCloud — devices that family members or coworkers may share — you run the risk of having your notes read, edited, and deleted by other people. Such a catastrophe is easily avoided.

In the Android community, there's a lot of discussion about how display notches should be used. For some, hiding the notch is more appealing, but others feel that hiding it wastes screen real estate. Well, Essential just provided another solution that should satisfy both sides.

Apple has introduced a special edition iPhone 8 and 8 Plus to bring attention to the ongoing worldwide battle against AIDS. As the second iPhones to carry the (PRODUCT)RED name, these rare iPhones may quickly sell out when preorders open up on Tuesday, April 10, at 5:30 a.m. (PDT), so we'll go over some tips to help you secure a red iPhone before it's gone.

It seems like each day new rumors and leaks come out for Huawei's upcoming P series devices. Everything from its name change to its specs has been leaked, sometimes with contradicting rumors. One of the biggest leaks is the inclusion of triple rear cameras, a first for smartphones.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.

Put yourself in Google's shoes: You know that business is becoming increasingly mobile, but the mobile operating system you maintain is wide open by design, and it's garnered legions of loyal fans that love to explore and exploit every aspect of it. There's a clear conflict of interest developing.

Apple just unveiled a red iPhone and iPhone 7 Plus, dubbed the iPhone 7 (PRODUCT)RED Special Edition, to commemorate the ongoing global fight against AIDS. Apple fans the world over are sure to swarm in and gobble up the initial stock shortly after the new color is released at 8:01 a.m. (PDT) on March 24, 2017, so we'll go over some tips to help you secure a red iPhone before it's sold out.

Bitcoin continues to make chaotic waves in the finance industry, with one bitcoin currently worth about $1,250 as of this writing. What's great about bitcoin is that you don't need to shell out rent money to get in the game, because bitcoins can be bought in increments—basically, whatever you can afford.

And so it begins... CES 2017 is upon us! This is a very exciting time for those who are looking out for the newest innovations and releases from the world of technology. I said this was going to be a fun week, and here we start it with a bang from smartglasses developer Osterhout Design Group (ODG).

"It just ticked me off," he said. In March 2011, Neil Singh paid $50 to back the Hanfree iPad stand on Kickstarter. The project was funded at $35,000, but production stalled, and the delivery estimates kept getting pushed back.

Good day to everyone, today I will present some basic and advanced concepts that targets sophisticated attacks on the social basis, also I will write about some steps that can prevent this attacks from occuring, basically we will examine Social Engineering from the angle of attacker and victim, some people who are interested in security and work for middle-sized companys can learn and use something interesting from this post.

Smartphones have been a hot button issue around school campuses for several years now—some schools allow them, others confiscate them on sight. But the fact of the matter is, when used correctly, a smartphone can be just as much of a learning tool as a textbook or school-issued laptop.

Smartphone cameras are so good nowadays that there's almost no reason to own a point and shoot. Once the megapixel spec race was finally settled (hint: more isn't always better), manufacturers started focusing on the quality of their camera sensors, which has led to a huge jump in color accuracy, dynamic range, and image clarity.

Smartphones are almost always connected to the internet, so it stands to reason that they can be hacked remotely. Or perhaps a jealous boyfriend or girlfriend got hold of your device physically, in which case they could've potentially installed a keystroke logger, a virus, or any other type of tracking app to spy on you.

In 1987, two brothers, Thomas and John Kroll, began work on an image editing software, which was eventually acquired in 1988 and released to the world in 1990 by Adobe. That software was Photoshop 1.0, initially exclusive for the Macintosh platform. Over the years, Photoshop became a great wizard of image editing and gained application rockstar status.

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

I may be in the minority when I say this, but I love leftovers. Whenever I'm cooking for less people than the recipe calls for, I cook the full yield anyway. And when I go to a restaurant, I order whatever I want—regardless of how much I can actually eat in one sitting.

Locking your keys inside of your car is frustrating, to say the least, especially if you're in a hurry to get somewhere. You can always call AAA roadside assistance or a locksmith, but you'll probably have to fork over some money, as well as wait for them to get to you. You might even get towed.

When a stuffy nose hits, it feels like breathing clearly and easily may never come again. Allergies, colds, and even changes in weather can leave our sinuses blocked, with medicine seeming like the only option. But don't break out the medication just yet — relieving the pressure of a stuffy nose, a stuffy head, and stuffy ears can be as easy as touching a pressure point.

Welcome back, my greenhorn hackers! As hackers, we often take for granted that nearly all of our hacking tools and operating system are free and open source. I think it's important to examine a bit of background on how we arrived at this intriguing juncture in the history of computer software. After all, we pay for nearly all of our other software (Microsoft, Adobe, etc.) and nearly everything else we use in life, so how is it that Linux and all our hacking tools are free?

If you've already read the first part exploring what geniuses actually eat as opposed to what the rest of us are told to eat for brain health, you've noticed that there are some big discrepancies. Instead of favoring healthy, wholesome foods high in antioxidants, lots of high-achieving types tend to go for caffeine, sugar, and processed foods. One notable health habit practiced by many: eating breakfast.

"The best season for food is the worst season for cooking." These words, spoken by food blogger Dave Klopfenstein of Dave's Kitchen, couldn't be more true.

While landing a job isn't the easiest thing in the world, you can probably blame your résumé for a number of lost opportunities. Writing up a cover letter and résumé is frustrating and time-consuming, but if you spend the time to get them right, the effort will drastically increase your chances of getting employed.

One thing almost every Android launcher has in common, from stocks to skins, is the way they handle organizing and launching apps and widgets. Tap an app icon to open the app. Drag apps together to create a folder. It's simple, it works, and it's what we know.

In these martial arts training videos, learn the basic principles behind Jeet Kune Do, using no way as way, and having no limitation as limitation. Our teacher will guide you in some beginning movements and techniques, including how to do a simple ready stance and how to combine kicks and punches for a powerful advantage in combat.

Lose weight, watch what you eat, connect with others; learn to use the Daily Website in this free video and find out how to be healthy and lose weight while sharing your ideas on diet and nutrition.

One of iCloud Photo's biggest perks is its ability to store large video files taken with your iPhone, so you can fill up your iPhone's storage with other items. That said, when you play back those videos, you may not be watching the footage in its original quality. Instead, they may be low-res versions. To view the high-quality originals — or to make sure that's what you see — just follow this trick.

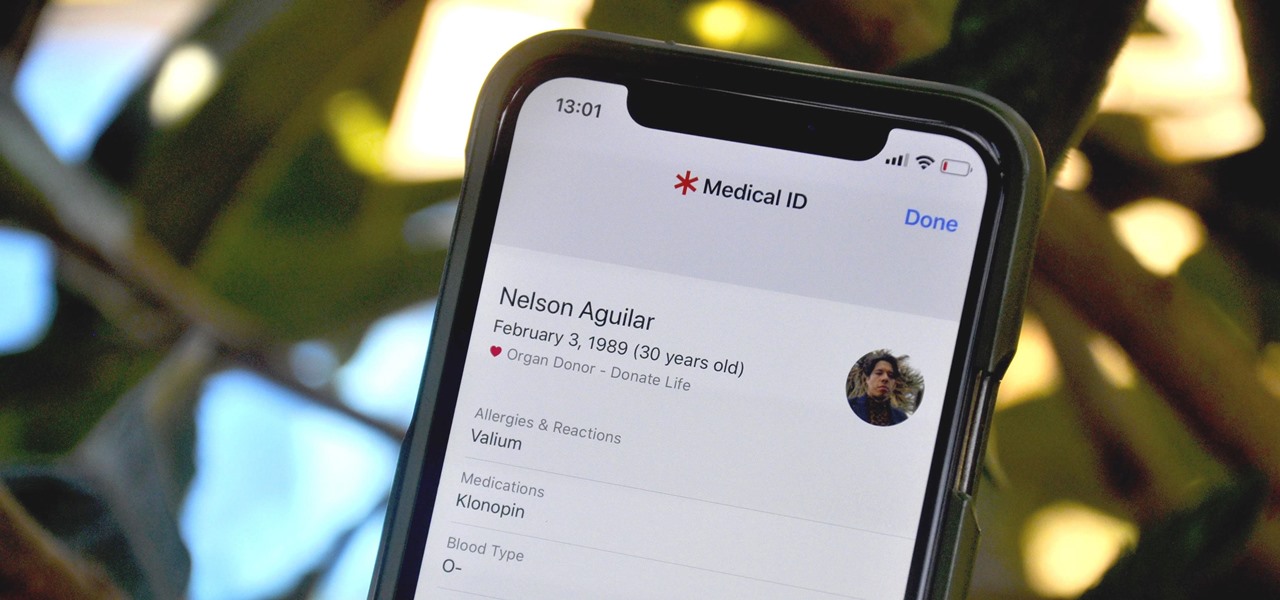
You can't predict the future, but you can prepare for it. On the off chance that you get hurt in a car accident, take a nasty tumble, fall down a cliff, have a seizure, or get struck by lightning, it's always good to carry up-to-date information about your health in case you can't speak for yourself. A physical medical ID wallet card or bracelet can provide the information, but so can your iPhone.

The USB Rubber Ducky is a famous attack tool that looks like a USB flash drive but acts like a keyboard when plugged into any unlocked device. The Ducky Script language used to control it is simple and powerful, and it works with Arduino and can run on boards like the ultra-cheap Digispark board.

The rise and fall of Meta, the Silicon Valley-based augmented reality startup that looked to challenge the likes of Microsoft's HoloLens, and others, took just six years.

Over the years, Magic Leap's long-cultivated shroud of mystery led some onlookers to buy into the company's dream before even trying the device, while for others, the secrecy seems to have stoked the kind of resentment and overcorrecting critique usually reserved for the mighty Apple.

As you're surely aware, your phone can be used against you. Thanks to our cameras and microphones, a clever hacker can obtain access to your device and invade your privacy. But spying isn't limited to just these two sensors — gyroscopes, proximity sensors, QR codes, and even ads can be used to paint a very clear picture about who you are and what you're currently doing.

We're all aware that Google collects a notable portion of our data. Thanks to the increasing awareness, Google has added a number of privacy controls to limit data collection. But Google doesn't just collect personal data for no reason — many of your favorite apps will use this info to improve their services and add new features.

As smartphone users, we live in dangerous times. The value of phones continues to rise, making them prime targets for thieves. In 2015, the FCC estimated that one million phones are stolen each year, and with several devices starting to hit the $1,000 mark now, these numbers are sure to rise. But what do you do if you fall victim to phone theft?

There are more than 2 billion Android devices active each month, any of which can be hacked with the use of a remote administration tool, more commonly known as a RAT. AhMyth, one of these powerful tools, can help outsiders monitor a device's location, see SMS messages, take camera snapshots, and even record with the microphone without the user knowing.

By combining years of web search advancements, natural language processing, and even DeepMind's artificial intelligence, Google Assistant hopes to change the way you interact with your devices. If you're familiar with Google's previous services, Google Assistant is like Google Now, Voice Search, and Now on Tap rolled into one service, with an extra layer of personality added on top. The end result is one central location for all of your Google needs, be it web search, screen search, playing m...

For people that like to get things done, Android's home screen widgets are almost indispensable. Rather than packing your launcher with a bunch of icons, you can utilize widgets to get quick information in a beautiful package or provide one-tap access to a particular functionality within your apps.

Welcome back, my tenderfoot hackers! As hackers, we often are required to get past antivirus (AV) software or other security measures. To do so effectively, we need to have some understanding of how AV software works. In this tutorial, we will take a cursory view of how AV software works so that you can better strategize on how to evade detection by it.