This week, saw two companies leaning on AR to prop up their financial futures. On one hand, Apple made quite a bit of AR-related news ahead of its quarterly earnings report next week. On the other hand, Vuzix launched a pre-order program for its Blade smartglasses and closed the largest financing deal in the company's history to fuel its ongoing headset production.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

A top executive from Baidu's telematics division believes the company will become the word leader in driverless by 2020, according to a report in today's South China Morning Post.

Cruise Automation follows Waymo's and Uber's lead with its debut of a beta version of an app-based driverless ride-hailing service for its employees in San Francisco, ahead of a possible launch of a full-fledged commercial offering within four years.

Ex-Uber CEO and founder Travis Kalanick's bad and likely illegal behavior aside, his vision of not wanting to pay "the other dude in the car" has lead to a ground-breaking driverless test fleet.
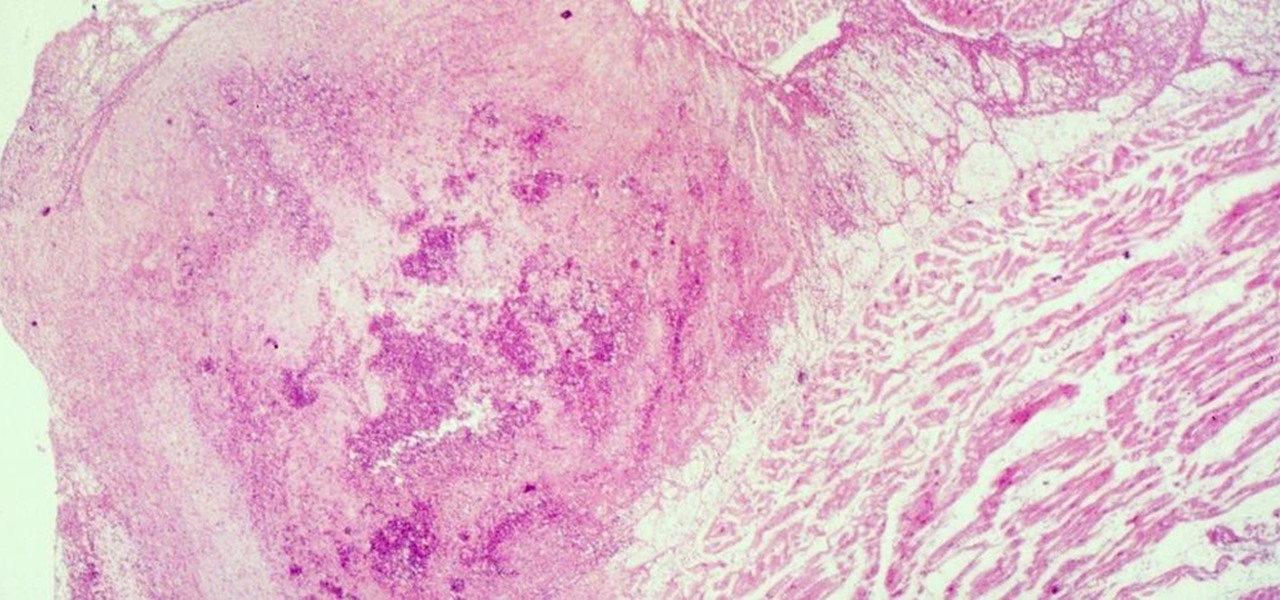
Four million Americans misused prescription opioid painkillers in 2014. Those who do are 40 times more likely to inject heroin or other drugs than other people. Now, the Centers for Disease Control and Prevention (CDC) are blaming that misuse for a 12-fold increase in endocarditis, an infection of the heart valves.

The Chinese government's tight restrictions on gathering data by foreign firms for 3D mapping, the lifeblood of machine-taught driverless systems, could at least slow down access to the market by Waymo, Tesla, General Motors (GM), Ford, and other players hoping to make inroads there.

Waymo and Lyft have remained highly secretive about their driverless car programs, but may be forced to reveal a lot about their plans after a judge in a US federal court granted Uber's request to review documents about Waymo and Lyft's partnership.

Ok, I have to admit, I drop my phone around 2–4 times a week. I'm horrible at protecting it and I've gone through my fair share of cracked phones. Most of the time, once the phone is cracked it's just easier to get an entirely new phone, rather than have to fight your phone provider for a fix.

Uber and Waymo's lawsuit is starting to pan out. Following a ruling on Monday, May 15, Judge Alsup, who called Waymo's patent infringement claims "meritless," ordered Uber to perform a series of actions and duties for Waymo. Without further ado, here's what Uber must do to begin to put this lawsuit behind them (well, maybe):

Uber's year is going from bad to worse, and they may be subject to a potential criminal probe in the ongoing Waymo legal battle.

Sepsis is not only a gross sounding word but also a deceptively dangerous and fatal infection. Which is why more than 40 hospitals nationwide are coming together to a new collaboration to help reduce sepsis mortality, named Improving Pediatric Sepsis Outcomes (IPSO).

Crayon, a free 3D drawing application by the mysteriously named arkalian, showed up in the Windows Store recently, so I gave it a try like I do all new apps for Windows Holographic. Truthfully, I loaded it up not expecting much, but wow, was I wrong. It's a simple idea, but it's executed well enough to make it a truly great experience on the HoloLens.

Greetings aspiring hackers. I have observed an increasing number of questions, both here on Null-Byte and on other forums, regarding the decision of which USB wireless network adapter to pick from when performing Wi-Fi hacks. So in today's guide I will be tackling this dilemma. First I will explain the ideal requirements, then I will cover chipsets, and lastly I will talk about examples of wireless cards and my personal recommendations. Without further ado, let's cut to the chase.

Hello fellow gray hat hackers, I wrote a program in python that helps me to fill up my proxychains.conf file, so I don't have to manually enter in the proxies. I figured I will give a little how-to of how I did it and maybe I could help some of you(hackers) out there to stay anonymous.

The first time you launch any type of file, Windows 10 will usually prompt you to select an app to open it with. Occasionally, though, this "Open with..." screen doesn't show up, and instead Windows will use a pre-installed system app to launch the file without ever giving you a choice in the matter.

Hello my anxious hackers, the week has started and here we begin a new series that I think will help many here and not only, for those that have the opportunity to follow our tutorials but they are not yet part of the community.

Hello, fellow grey hat hackers and aspiring coders. I'm back again with another python tutorial. Just that this one is gonna be a lot cooler ;-). We gonna make an encryption program, that well you know encrypts all the files on your pendrive or hdd or whatever you want....Also lots of thanks to DrapsTV. They have helped me a lot with Python and making awesome programs. The video is here:

If you've switched ROMs before or flashed quick mods on your Android device, you've probably used TWRP or another custom recovery to install them. But another great purpose for flashing through a recovery is to install your own custom .zip file filled with everything a fresh ROM needs—namely, all your apps.

Well, this is my first article so if it sucks tell me...lol!! Story Time
Hello, Hackers/Viewers! My name is nullf0x, and I have 4 years of experience as a hacker. You might see everyday that one of your friends or acquaintances get a new virus in their computer. You might think, How cool would it be if I made a virus? or How cool would I be if i could remove viruses from others computers for money or free?

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Sideloading apps on Android is incredibly easy—you just have to enable "Unknown sources" in your device's Security settings, then you're free to run an APK installer file to get the app installed.

Back in the '80s, recording live radio was as simple as popping a cassette tape into your boombox and pressing the record button. While we've come along way with regard to accessing radio stations thanks to websites and apps that stream live broadcasts over the internet, it's no longer quite as easy to record.

The oven is arguably our most essential kitchen appliance (right alongside the fridge, freezer, and yes, even the microwave). But even though we've been using them for a few millennia, many of us know so little about our ovens that our cooking or baking can feel like a roll of the dice sometimes.

Welcome back, my amateur hackers! Over the course of the next year, we will be developing our own zero-day exploits. In my first article in this series, I introduced you to buffer overflows, which are the source of some of the most lethal exploits, particularly the "remote code execution," so we are focusing our exploit development here on a buffer overflow.

Welcome back, my fledgling hackers! With this first article, I am initiating a new series intended to convey to my readers the skills necessary to develop your own exploits.

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.

Apple has acknowledged a problem with the sleep/wake key, better known as the power button, on a certain number of iPhone 5's manufactured through March 2013. As a result, the company has announced the iPhone 5 Sleep/Wake Button Replacement Program, which will replace the power button mechanism, free of charge, for certain iPhone 5 models.

Currently in its alpha stage, Facebook has pushed forward a redesigned mobile app for Android users that provides a flat user interface and rearranged navigation tools.

What you watch in the privacy of your own home should be no one's business but yours. That was the case until Prime Minister David Cameron decided that there was too much porn available to minors in the United Kingdom.

Let's just say it's been a pretty bad year for spies and government agencies and an even worse one for the privacy of U.S. citizens. Edward Snowden blew the lid off the NSA's spy program, and the FBI was recently discovered to have the ability to access your webcam any time they want—without triggering the "camera on" light. Yeah, that means those Justin Bieber lip sync videos you recorded weren't just for your private collection.

If you're marginally inclined towards computers, you've probably been approached at some point by a family member who wants you to "fix" their system during a visit home. With the holidays coming up, these opportunities (or ambushes) are even more likely.

Whether or not you believe that the government is snooping around in our private emails, texts, and phone calls, it wouldn't hurt to protect ourselves a little better in the digital realm.

Welcome back my fellow hackers! In my last few articles, I've concentrated on what is called a listener, which is basically the same thing as backdoor and rootkit, only "listener" sounds much less malevolent than the other two terms.

Like a computer, your brain can store and process large amounts of information. It can remember names, solve math problems, and save tips that you might need at a later time.

This guide will explain how to configure a USB Flash Drive / Memory Stick so that you can run a keylogger within just a few seconds of plugging it in any computer.

If you're creating a document and with Adobe's InDesign and would like to learn how to number your pages, look no further. This video will show you what to do to make sure you get the numbers you want, where you want them. Though this seems like a simple task, it can prove frustrating to someone unfamiliar with the program. This how-to clears up some of the mystery and lets you get your 1,2,3 on. Adobe InDesign can be an impressive document or presentation tool and this tip will help you get ...