In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

Hey readers! This tutorial will be the entry point for the introduction of buffer overflows. Something like requesting user input is a very common place for vulnerabilities to pop up and we will definitely have fun while trying to make programs crash. But for now, let's start with how we can get input from a user.

Why I split it into two articles: I love images and I'm sure lots of us do. I decided to put in a lot of images as examples rather than have paragraph upon paragraph of boring text. Also, I don't think any of us like overly long articles; but if you think it's better to have it all in one article, let me know

If you prefer glow sticks over candles during a power outage, then this how-to is for you! Although glow sticks are used as temporary light sources, there are other applications for them. Divers use them for night diving, fisherman use them to catch swordfish, and the military uses them for light markers, along with infrared versions used in conjunction with night vision devices. But with all these handy uses for glow sticks, the most popular is — recreational use, like dancing at raves, some...

Titlibo Nihaan shows us how to make Bo Kho(Vietnamese Beef Stew,in this video. The ingredients for this are,500 grams of beef,3 chopped shallots,1 small onion, thinly sliced,soy sauce,nuoc mam sauce,a bunch of fresh basil,2 red chillies,3 cloves of garlic,1 tablespoon lemon grass,1 tablespoon of turmeric powder,1 tablespoon of curry powder 1 tablespoon of brown sugar,4 star anise and a beef stock cube.In a small pan dry roast the star anise for 5 minutes.When cooled,gring them in a coffee gri...

To make a lotus out of a single sheet of paper, use a colored, square paper sheet with a different center color (optional). With the colored side facing outwards, fold the sheet diagonally in half creating a center crease. Open up and repeat the step with the other corner to obtain a center point. Carefully fold the 4 corners towards the center point to form a smaller square. Repeat the same procedure with this square. Flip over and repeat the same procedure over again. The next step is optio...

Karen Solomon shows how to make bacon. You need 2 1/2 to 3 pounds of pork belly with no skin or bone. Rinse the belly with water and pat really dry. Mix ingredients for cure which includes 1/2 cup sugar, 1 tablespoon blackstrap molasses, 1 teaspoon freshly ground pepper, 2 tablespoons kosher salt and 1 teaspoon curing salt. Curing salt may be obtained at local butcher shop or online at Sausage Maker. Curing salt helps preserve the color of the bacon and ensures no spoilage. Mix ingredients un...

Aluminum nitrate nonahydrate is a crystalline hydrate - a salt of aluminum and nitric acid - Al(NO3)3·9H2O. It's used for a variety of things such as antiperspirants, corrosion inhibitors, and petroleum refining, or… glow-in-the-dark powder. Watch this science video tutorial from Nurd Rage on how to make aluminum nitrate nonahydrate with Dr. Lithium.

This is chemistry at its best! Europium is the chemical element (Eu) which was named after Europe. Dysprosium (Dy) is a rare earth element of a metallic silver luster. Watch this science video tutorial from Nurd Rage on how to make europium and dysprosium nitrate salts with Dr. Lithium.

Farkle hacks, cheats, glitches. How to hack Farkle. Watch this video tutorial to learn how to play Farkle and Farkle Pro on Facebook. Learn about scoring and gameplay in Farkle. What's you highest score?

Watch this science video tutorial from Nurd Rage on how to get lithium metal from an Energizer battery. They show you how to get Lithium Metal from an Energizer Ultimate Lithium battery.

A light meter can prove to be an invaluable tool on any film set, allowing you to quickly and efficiently set lights and know the correct exposure values of those lights. Light meters were initially designed for still photographers and cinematographers can easily calibrate them to a given film stock speed for shooting film. But what about today’s digital cinematographer? I’m glad you asked. In this video tutorial you'll see how you can use a light meter to quickly and efficiently light a scen...

XSS Shell is a cross-site scripting backdoor into the victim's browser which enables an attacker to issue commands and receive responses. During a normal XSS attack an attacker only has one chance to control a victim's browser; however, the XSS Shell keeps the connection between the attacker and the victim open to allow the attacker to continuously manipulate the victim's browser. XSS Shell works by setting up an XSS Channel, an AJAX application embedded into the victim's browser, that can ob...

Magic Leap CEO Rony Abovitz doesn't engage in tweetstorms often, but when he does, those tweets are bold, exceedingly confident, and there's usually a strong takeaway regarding what the company is or isn't doing. But on Thursday, Abovitz's latest tweetstorm sent an unusually flustered message: We promise, the magic we're telling you about it better than anything you've seen on video.

Just days before the release of the first image of the Magic Leap device, the company's CEO, Rony Abovitz, knew that the biggest moment of his life was about to unfold the following week. But instead of hunkering down in the Florida-based confines of the company's skunkworks, he instead decided to deliver a speech to the public about, what else, the future.

So cute, so furry, and so chock full of parasites. While raccoons are fun to watch, they are neither friendly nor clean — and they can make you sick in more ways than one.

Puzzle games are a great way to kill time and exercise your brain in one fell swoop. They challenge you to think strategically and plan ahead, whether that's to create killer chain combinations for maximum points, or to plain old keep from getting killed.

This is a video tutorial for all of you people who don't know how to cut and fold zines, which are short magazines, especially a fanzine, or webzine. It's not brain science here. You basically just print, cut and fold. That's it.

Dr. Parris Kidd explains how the dietary supplement GPC (GlyceroPhosphoCholine) can benefit the brain health of people of all ages, from children to adults. It can also help those recovering from brain damage.

http://www.iHealthTube.com

The Central Processing Unit, or CPU, is the electronic brain of your computer. Learn how how to install a CPU in a desktop PC. To get started use a flat workbench or desk, and don't forget to ground yourself.

Some Chinese dishes that sound healthy are surprisingly fat-laden. These tips will help you avoid diet land mines.

Increase your odds of meeting Mr. Right with these tips. Learn how to meet men if you are single. You Will Need

Building a DIY Alarm System: The Concept So, you want to protect your property, or maybe a room, car, or even your backyard. The concept of an alarm system is to notify the "alarm administrator" that there is an intruder entering the previously designated boundaries. The triggers for this boundary could be as simple as a pressure sensor, or as complicated as a laser network. They all do the same thing, but some work better than others.

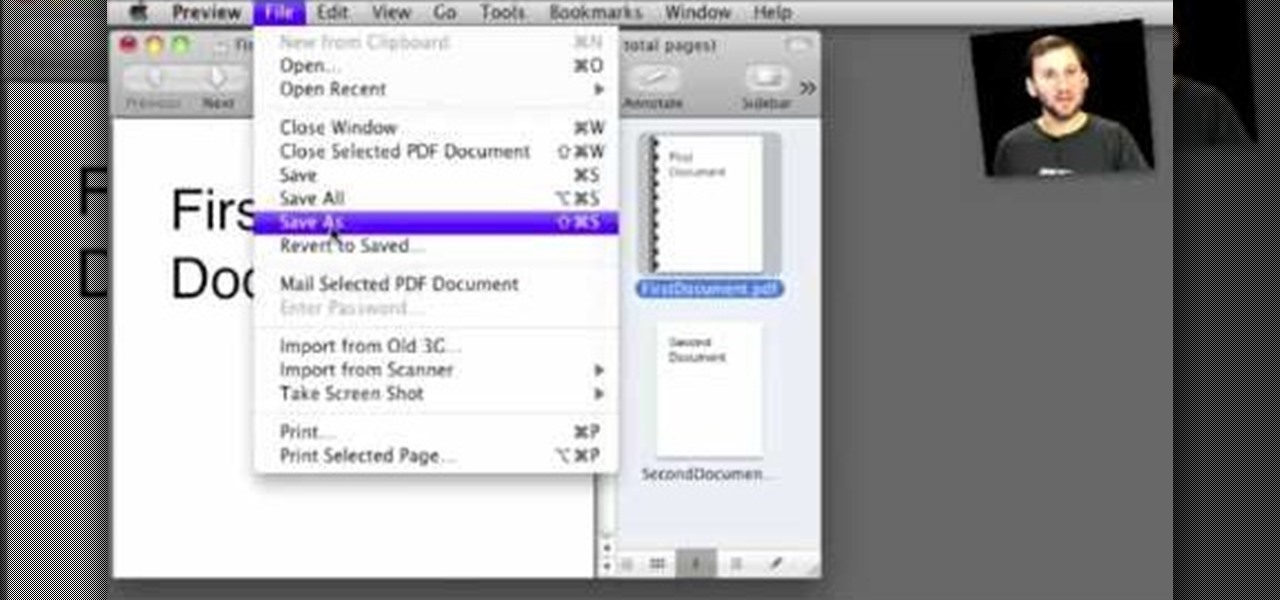
PDF is a Portable Document Format, which is a popular format to represent documents and pass it over the internet. You can merge different PDF documents to obtain a single document. You can do this on your Mac, using the preview option. Preview does a lot more than the name suggests. You can actually merge PDF's and also rearrange pages inside the documents. There are some changes in the functionality in preview feature between the leopard and snow leopard versions. To use this first you will...

This video is provided by "Betty Sell" from AAA travels. In this video she tells about the international travel and also about the important documents to be carried while carrying out an international travel, that is the international driving permit, commonly called as an IDP. It's very important to carry an IDP while traveling overseas because an IDP acts as an important recognizable form of photo identification which helps us to communicate with foreign authorities. To get more information ...

Smash glow? What the heck is that? That's exactly what you'll find out… watch this science video tutorial from Nurd Rage on how to make smash-glow crystals (triboluminescent crystals) with Dr. Lithium.

Pixel Perfect is the "perfect" show to help you with your Photoshop skills. Be amazed and learn as master digital artist Bert Monroy takes a stylus and a digital pad and treats it as Monet and Picasso do with oil and canvas. Learn the tips and tricks you need to whip those digital pictures into shape with Adobe Photoshop and Illustrator. In this episode, Ben shows you how to apply light sources to 3D models in Photoshop.

There are many password-cracking tools out there, but one of the mainstays has always been John the Ripper. It's a powerful piece of software that can be configured and used in many different ways. Metasploit actually contains a little-known module version of JTR that can be used to quickly crack weak passwords, so let's explore it in an attempt to save precious time and effort.

Augmented reality plays a key role in the evolution of adjacent technologies, such as 5G connectivity and brain-control interfaces (BCI), and the business news of the week serves up proof points for both examples.

The art of privilege escalation is a skill that any competent hacker should possess. It's an entire field unto itself, and while it's good to know how to perform the techniques involved manually, it's often more efficient to have a script automate the process. LinEnum is one such script that can be incredibly useful for privilege escalation on Linux systems.

In recent weeks we've talked about the growing trend of smartglasses makers moving the brains of their devices to smartphones, and now a veteran of the space has joined that movement.

Publicly, things have been pretty quiet over at Meta, the augmented reality headset and software startup based in Silicon Valley. But that doesn't mean that the company doesn't have a few strong opinions about the state of AR in 2018.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

How can a drug used to treat cancer be effective against viruses, too? The answer lies in the drug's shared target — specifically, cellular components that control the activity of genes. A new research study showed that one such type of drug, histone methyltransferase inhibitors used in cancer clinical trials, has activity against herpes simplex virus, too.

Foodborne infections often occur through the contamination of equipment, food-prep tools, and unsanitary surfaces. A recent report from the Centers for Disease Control and Prevention (CDC) reminds us that breast pump parts are part of the food-delivery chain — and they can become contaminated too.

The ability of one microbe to adapt is giving it a whole new career as a sexually transmitted disease. Usually content with the back of the throat and nose of those who carry it, the dangerous pathogen Neisseria meningitidis has adapted to cause an illness that looks a lot like gonorrhea.

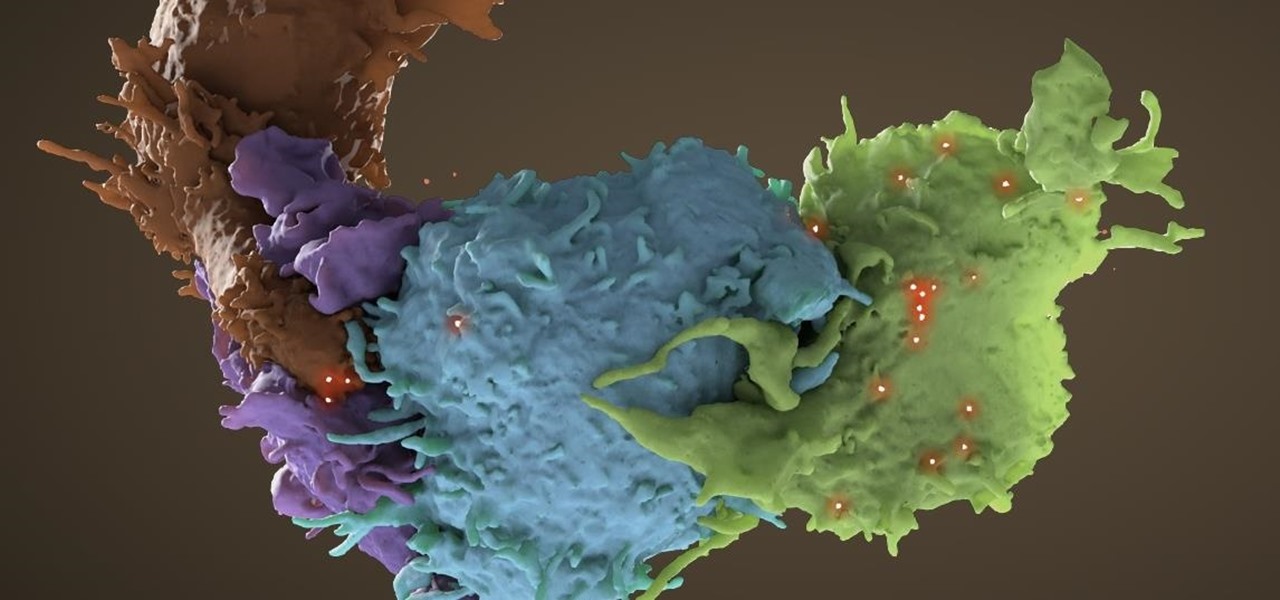
Tremendous strides have been made in the treatment and outlook for patients infected with HIV, the human immunodeficiency virus. Treatment with a combination of antiretroviral drugs can keep patients with HIV alive for decades, without symptoms of the infection. The trouble is, if HIV-infected people stop taking their medications, the virus takes over in full force again—because the virus hides out quietly in cells of the immune system, kept in check, but not killed by the treatment.

The culprit probably wasn't what doctors were expecting when a 57-year-old man in Hong Kong came to the hospital. The patient was admitted to the intensive care unit in critical condition. A clue to the cause of the infection would lie in the man's profession—he was a butcher.

Maternal infection with genital herpes, or other pathogens, during early pregnancy could increase risk of autism, or other neurodevelopmental disorders, says a new study.