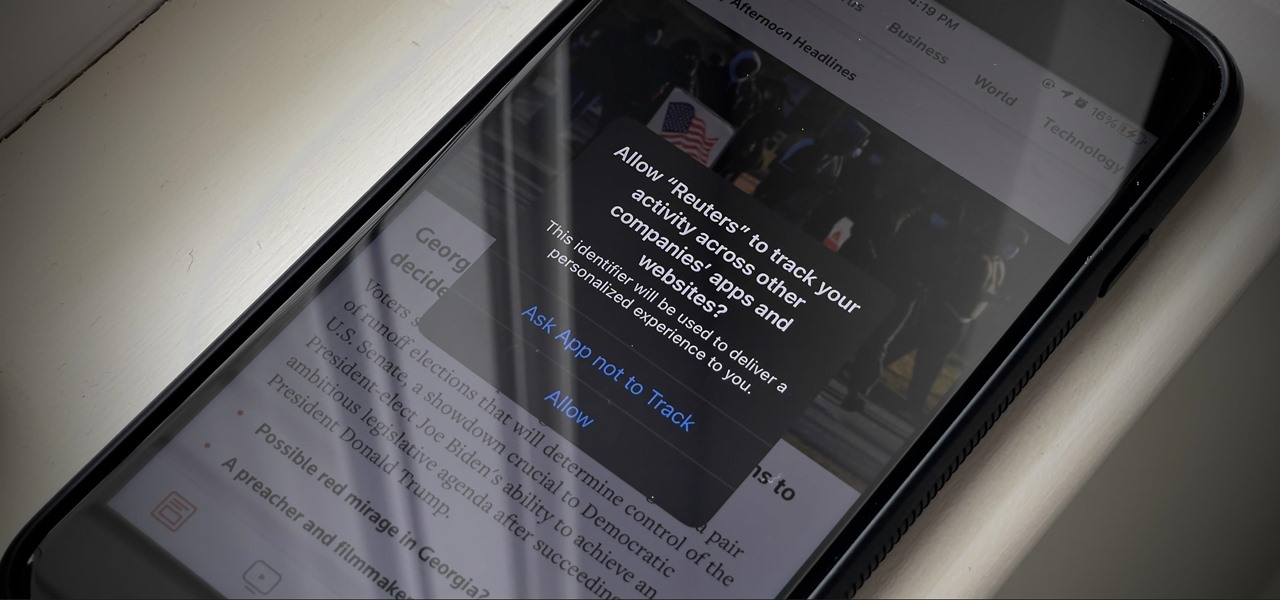
If you're like me, you're not too keen on being tracked. So when an app asks you if it can track your iPhone activity across other programs and websites for ads or data brokers, the answer is pretty much always "no." If you're tired of choosing "Ask App Not to Track" over and over again, there is a way to stop apps from even being able to ask in the first place.
In the battle for best stock Android flagships, there are really only two choices: Google Pixel phones and OnePlus phones. Although the latter isn't true stock Android, it is impressively close and usually paired with more impressive hardware than the Pixel lineup. The latest is the OnePlus 6T, which will be a bit controversial for fans this year.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

The dark web is an intimidating place for a newbie hacker, but it's a powerful tool once you've learned to navigate it safely. To help you out with that, this guide will cover some need-to-know information for traversing the dark corners of the internet while keeping your identity and data safe. (Hint: Using Tor is not enough.)

After a long hiatus, we shall once again emerge from the shadowy depths of the internet to build an exploit. This time, we'll be looking at how to defeat a non-executable stack by using the ret2libc technique — a lean, mean, and brilliant way of exploiting a stack overflow vulnerability.

The latest software update for iPhone has a few new features you should know about, including an enhanced security feature to protect your Apple ID account from phishing and other attacks. Keep reading to see everything new that's included with iOS 16.3 for iPhone.

As we've seen with other tools and utilities, administrators typically use certain things to do their job more efficiently, and those things are often abused by attackers for exploitation. After all, hacking is just the process of getting a computer to do things in unexpected ways. Today, we will be covering various methods to perform banner grabbing to learn more about the target system.

SQL injection is a type of code injection that takes advantage of security vulnerability at the database level. It's certainly not the easiest form of hacking, but if you're serious about turning a website upside down then this is the way to do it.

Motion can be studied in different dimensions. Study of motion of a body in a straight line is called motion in one dimension. A falling body can be called as motion in one dimension. Things can also move sideways when they fall at the same time. This is also called as projectile motion and it is a study of motion in two dimensions. When studying projectile motion we can neglect one dimension of the motion and study the other dimension obtaining the results of motion in that dimension. If a b...

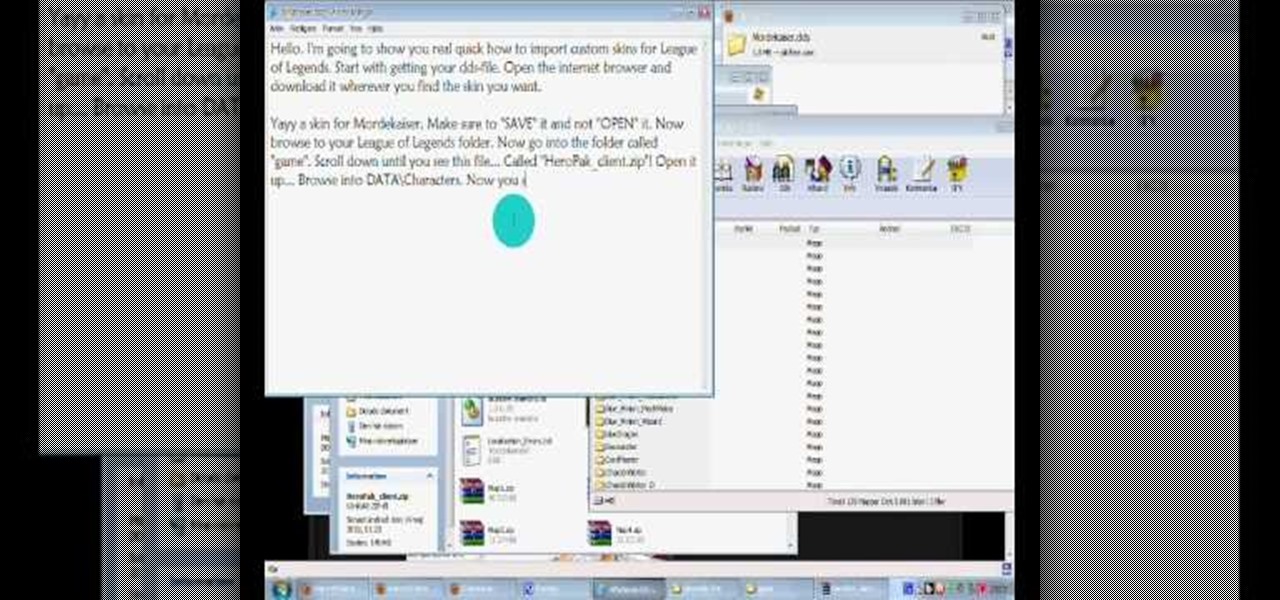
Give your League of Legends champion a new look! Alter the .dds files in the game directory so you can import custom skins. This video walks you through the process for obtaining and installing custom skins. Be aware that this will only change the way champions appear to you.

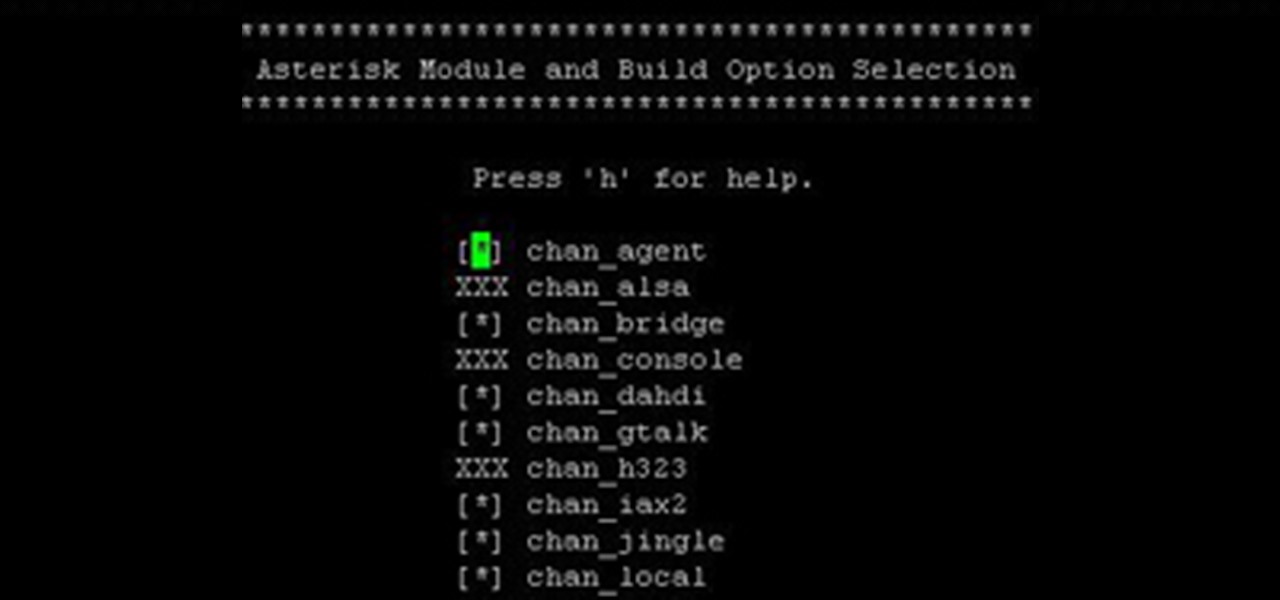
Over the years, I have enjoyed playing with Asterisk. I have found Asterisk to be extremely powerful and fun to play with. There are several books and many scattered how to articles out there, but most are outdated and the information required to build Asterisk from beginning to end can be a bit daunting. I wanted to combine all the steps into a single article and share my experience with everyone. If I have left out any steps please let me know.

The resume is an essential tool for getting freelance work assignments. A well written article is not enough when trying to secure a freelance or staff position as a writer. Publishers want to see a resume. It gives the writer an outstanding opportunity to introduce themselves and it gives the editor a general idea of who you are, where you've been, and the work you've completed.
On Sunday U.S. Secretary of Defense Leon Panetta said the United States is “ready from a military perspective’’ to attack Iran under the guise of preventing it from obtaining nuclear weapons.

Did you know there is hidden data in your digital pictures? Well, there is, and that data might be a security risk to you. Think back at all of those pictures you're in and are connected with. I'm sure some of those you'd like to distance yourself from. And surely you wouldn't mind checking out the metadata in a few of those images. In this article, we'll be going over how to do just that.

The genius of the U.S Constitution is that it spreads the power of government both within the national government and between the federal government and state governments.

I got hooked on origami sometime after Math Craft admin Cory Poole posted instructions for creating modular origami, but I had to take a break to finish a quilt I've been working on for a while now. It's my first quilt, and very simple in its construction (straight up squares, that's about it), but it got me thinking about the simple geometry and how far you could take the design to reflect complex geometries. Below are a few cool examples I found online.

Robots are great for performing tasks that are otherwise too dangerous for man (e.g. dead body extraction bot). BeetleCam is a cute little bot that takes all the danger out of wild life photography. Controlled remotely from a Range Rover about 50 yards away, BeetleCam ventures where no sane photographer dares to go (at the feet of a charging elephant, say). "We thought that Elephants would be an easy subject for BeetleCam’s first outing. We were wrong… we quickly learned that Elephants are wa...

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. Missed the other guides? Click on the links!

As you progress in the world of information security, you'll find yourself in situations where data protection is paramount. No doubt you will have files to hide and secrets to share, so I'm going to show you how to use the GNU Privacy Guard (GnuPG or GPG for short) to encrypt and decrypt as you need. GPG is a great open-source version of Pretty Good Privacy (PGP), a similar application used for encryption, but licensing and patent problems led to the development of GPG in its wake.

It's a question I've been pondering a lot lately. Technically, children under the age of 13 are not allowed to join Facebook. But according to a Consumer Reports in May, 7.5 million children 12 and younger are already on the site. Currently, federal law prohibits websites from collecting personal data from children without parental permission. The Children's Online Privacy Protection Act, or COPPA, as it is more commonly known, has been in effect since 1998, but has not been updated since.

If you're a frequenter of Null Byte, I bet you have at least some interest in information security. Furthermore, you have a hobby that if applied in certain ways, will get you arrested. I've received quite a few messages from the community here about federal cybercrime law and how it applies to them, so I decided to get together with my lawyer to come up with some answers.

We are embarking upon a new year. As usual, some of us will make "resolutions." There isn't anything wrong with setting goals for the year. It's actually a good idea. It may help focus the energy we bring to life.

So, you scratched up your $500 Adobe CD and now it's unreadable. You could go buy a new one, but you already purchased it! Searching The Pirate Bay and downloading some Adobe software can usually be easy enough, but what should you watch out for?

Welcome to Minecraft World! Check out our advanced tutorials and come play with us on our free server.

Welcome to Minecraft World! Check out our advanced tutorials and come play with us on our free server.