While installing the new Android 9.0 Developer Preview is fairly easy if you're using a Windows machine, it's a little trickier if you want to use macOS instead. To help you get the latest Android OS on your Google Pixel phone, we'll break down the whole process so using your Mac can be as simple as Windows.

Many guides on Null Byte require using the Secure Shell (SSH) to connect to a remote server. Unfortunately for beginners, learning to use SSH can become a confusing mix of third-party programs and native OS support. For Chrome OS users, using SSH is even more difficult. We'll fix this by using the Chrome Secure Shell to establish an SSH connection from any device that can run a Chrome browser.

Apple has been in hot water ever since the news that the company slows down iPhones with older batteries. The iPhone maker is now in damage control, offering customers a large, $50 discount on battery replacements. The question for you, though, is does your iPhone need a battery replacement in the first place?

The threat of an evil access point has been around for a long time, and with the rise of open public Wi-Fi, that threat is often overshadowed by how comfortable we are using third-party Wi-Fi hotspots at coffee shops and public spaces. While we've shown an evil twin attack using the Aircrack-ng suite of tools, MitmAP is a Python tool to configure custom APs for many types of wireless attacks.

Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary flash drive, to deploy ransomware on a victim's computer within seconds. With an attack that only takes a moment, you'll need to know how to defend yourself.

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

Signal Private Messenger is famous for its end-to-end encryption, but you can't even use the messaging app without having a real phone number attached to it. Luckily, there is a way around this limitation, so you can use Signal even if you don't have a valid SIM card in your smartphone.

RouterSploit is a powerful exploit framework similar to Metasploit, working to quickly identify and exploit common vulnerabilities in routers. And guess what. It can be run on most Android devices.

The Galaxy S8 has finally touched down, and it's an absolutely gorgeous device. Samsung's brand new flagship comes jam-packed with new features — some refined, and some that aren't. Luckily, we've compiled some major features to help you get started as quickly as possible so you can go about the rest of your day and show off your shiny new S8 to friends and coworkers.

After months of leaks and rumors, Google has finally unveiled the Pixel 2 and Pixel 2 XL. If there were such a thing, the Pixel would be the one "true" Android flagship — so even if you don't plan on buying a Pixel 2, you'll want you learn more about this milestone device.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

It's been little over a month since the official release of LG's latest flagship phone, the LG V20. Despite a few minor hiccups, the V20 has been attracting attention from all over for being an amazing phone. But like with most Android phones, there's no better feeling than rooting and taking complete ownership of it.

Every year, tech companies use April 1st as a means to prove that they have a sense of humor. Sometimes their jokes are good for a chuckle, other times the gags backfire disastrously. For the most part, however, we'd be better off without the bulk of these annual antics.

When you hand your unlocked iPhone to somebody so they can use the internet real quick, check out some cool photos, or do whatever, there's a possibility that they could snoop around where they don't belong. If you have some secret recipes, login credentials, intellectual property, or other sensitive information in your notes, you'll want to add some protection to them.

The sheer variety of Android devices on the market is staggering—one report suggests there are well over 24,000 distinct phones and tablets floating around out there. When you consider that each manufacturer adds a few tweaks to the Android code base here and there, that makes for a lot of software variations, which in turn means there needs to be many different root methods to match this variety.

Hello null_byters, after some time out here we are again with another tutorial, continuing our beautiful series, today we will write our first real world bash script.

Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks.

In case you didn't know, Android has an awesome hidden settings menu called "Developer options" that contains a lot of advanced and unique features. If you've ever come across this menu before, chances are you just dipped in for a minute so that you could enable USB debugging and use ADB features.

Unruly customers. Crazy exes. Horrible bosses. When you need proof of insanity or just want it for your records, recording a phone call is a must. Problem is, it's not the easiest thing to do on an iPhone — but it's completely possible.

It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).

While the Apple Watch does have up to 18 hours of battery life each day on a full charge, your results will vary depending on how often you use it and what you're actually doing with it.

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.

Heartbleed, move over. There's a new bug in town, and this time it's also affecting Mac and Linux computers. It's called Shellshock (its original official title is CVE-2014-6271), and it's currently got a 10 out of 10 severity rating over at the National Cyber Awareness System. While some updates have been issued to fix this bug, they were incomplete, and your system is probably still vulnerable, as it has been for the last probably 20 years.

Canvas fingerprinting is the web's trickiest privacy threat, but it's not impossible to stop. With all the media attention it's gotten lately, it's time we lay out exactly how to detect and prevent this invasive tracking technique.

The microwave oven is a monumental technological achievement that's saved college students and single people from starvation for decades. Almost 97% of all American households have one, which makes it the most-owned kitchen appliance in US homes right after the refrigerator.

Jailbreaking gives you root access to the iOS file system, allowing you to install third-party apps and tweaks on your iPhone that aren't available in the App Store. It opens up a whole new realm for what your device can do, but it can also cause instability across the system and can dissuade you from getting future updates from Apple that have important features, bug fixes, and security enhancements.

Do you have an Alfa AWUS036NH Wi-Fi adapter that claims it can go to 2000 mWs, or some card that can supposedly transmit power over 1000 mW? If so, you may have run into problems setting your card's TXPOWER higher than 30 dBm, which is about 1000 mW. Well, I will show you how to break that barrier and go as high as you want!

Need to clear you cache? This guide details how on any web browser (Chrome, Internet Explorer, Firefox, Opera, Safari, Internet, and Dolphin) for any platform (Windows, Mac OS X, iOS, and Android). What Is the Cache Exactly?

I admit, when the new iOS 5 update for Apple devices was coming out, I had iTunes open all morning with my iPhone 4 attached... waiting... waiting... waiting until finally the new version of iOS was available for download. I stopped everything I was doing and quickly initiated the process of updating my device. After two excruciating hours, my iPhone 4 was finally ready to go and I couldn't be anymore happy. Who needs an iPhone 4S when you've already got iOS 5?

Use this safe and easy technique next time you need to replace a shattered light bulb. You Will Need

In this online video you'll get tips for recognizing signs of drug & alcohol addiction from a former addict. John DePalma explains how drugs can affect the brain and the long-term affects of addiction on the body. He explains the symptoms of several types of drug use, from alcohol and marijuana, to harder drugs like cocaine, crystal meth and heroin, and warns of the dangers of abusing prescription drugs like pain killers and anti-anxiety drugs as well. He then explains how to approach an addi...

The Reminders app is a simple yet powerful task manager, and it does a great job of reminding you to start an errand, alerting you to a project that's supposed to be done, or prompting you about a recurring chore. But with the latest Reminders update, the dates and times you set for tasks can act more like due dates thanks to the new early reminders feature.

Apple just released its iOS 16.6 update for iPhone on July 24. When you install the new software, it may look like there's not much to it since Apple doesn't include any features in the release notes beyond "important bug fixes and security updates," but a few new features are hiding within.

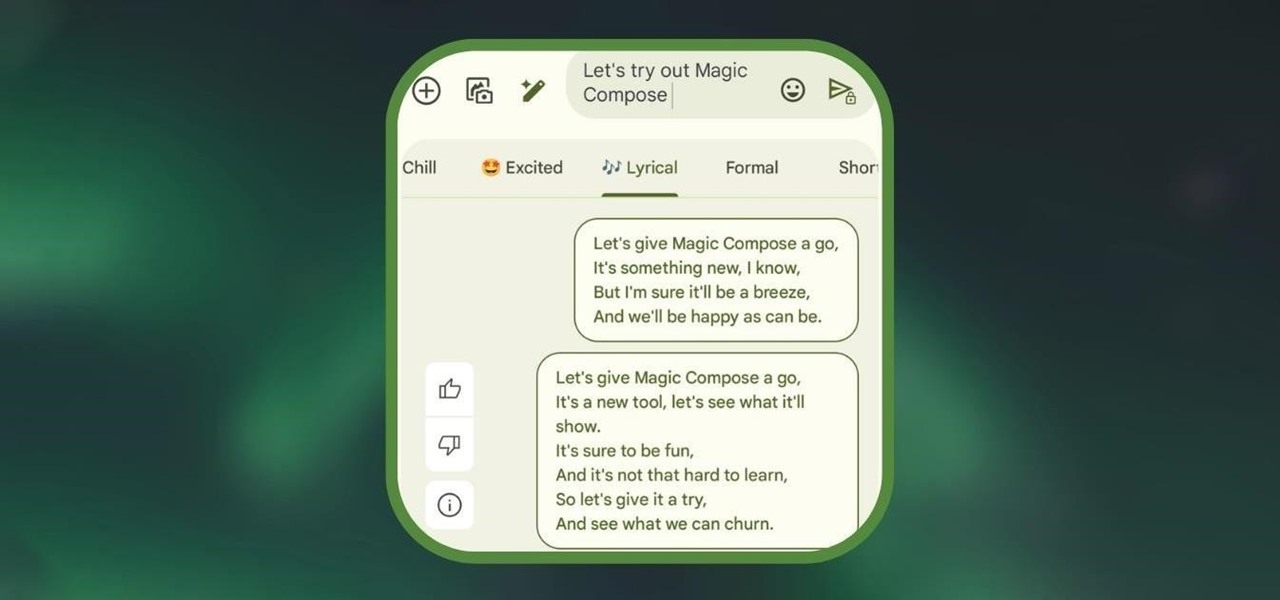
Text messaging is a core component of the mobile experience, and Google has added several AI-fueled features to help you text better, such as Smart Reply for quick response suggestions. But Messages by Google's newest AI-powered tool is possibly the best one yet, giving you improved response suggestions and your own personal copyeditor to fix all your message drafts.

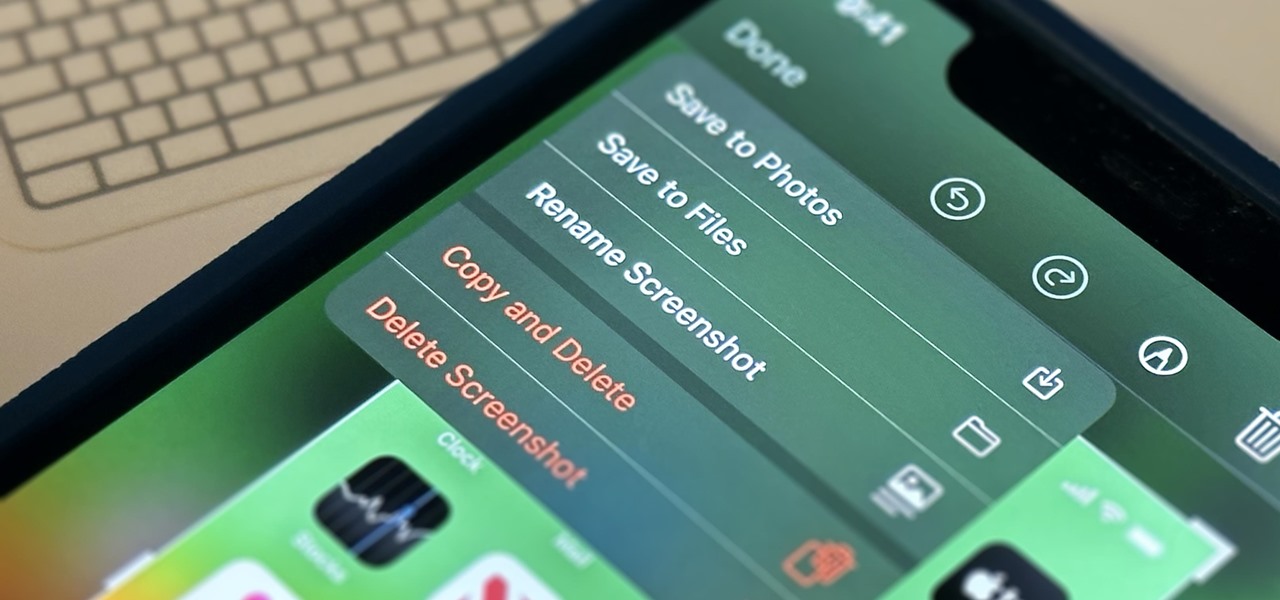
Apple's screenshot feature is a near-perfect tool for saving images of your iPhone's screen to keep for yourself or share with others. But iOS is missing one thing that would make it almost flawless: a way to rename your screenshots from their original IMG_1234.PNG file name.

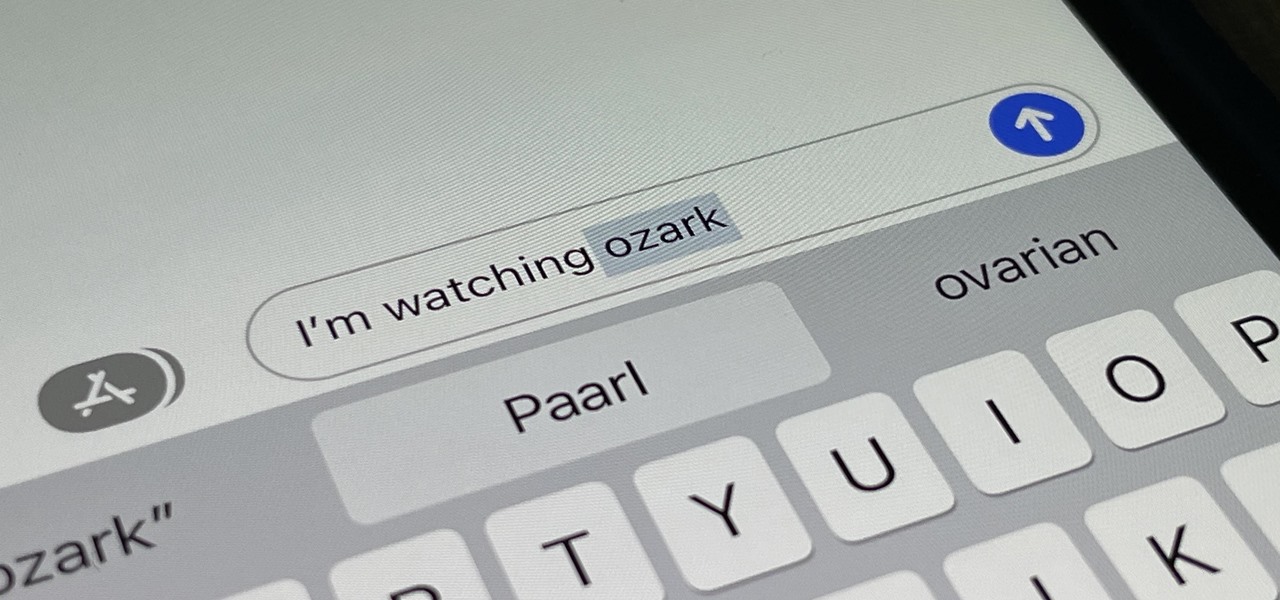
Auto-Correction only improves with time, but after 15 years of continuous development by Apple, it's still nowhere near perfect on the iPhone. However, a few hidden features in iOS can help avoid or mitigate future autocorrect failures, one of which warns you every time it's about to make a word change.

Apple is known for its dedication to design, attention to detail, and for its apparent belief that its products are half device, half art. If you've ever felt similarly about that latter point, or had a desire to hang your iPhone on the wall, Grid Studio might just have the piece for you.

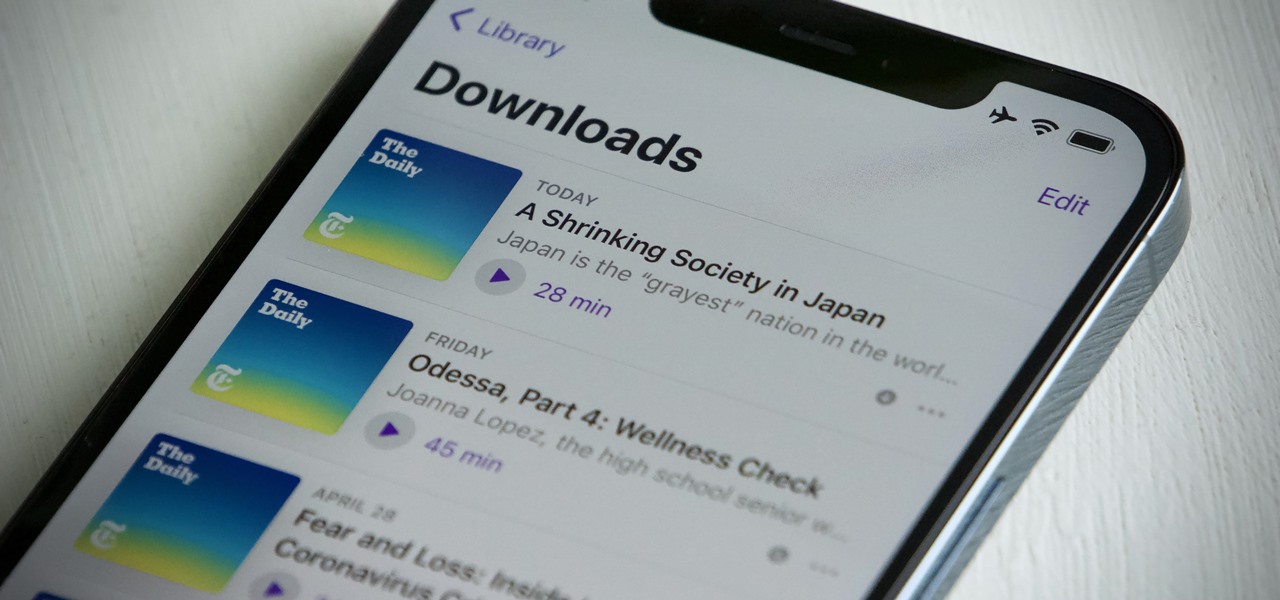
Apple's iOS 14.5 overhauled the Podcasts app, combining new aesthetics with smart and efficient features. While you might find the app better at playing your favorite podcasts than past versions, you might also find something negative about the update on your iPhone: it may be eating up your storage.

Many of us choose to use an iPhone — as well as other devices in the Apple ecosystem — because of the company's dedication to user privacy and security. If you need more proof of that commitment, look no further than iOS 14.5, released April 26, which adds new tools to protect our data while browsing the web and more control over the data installed apps collect on us.