
How To: Download and Install the Minecraft 1.8 Pre-Release
Update 2: 1.9 Version3 is currently out. Click here to download and install 1.9 Version 3. Update: 1.8 is now officially out! It'll prompt you to update the next time you launch.


Update 2: 1.9 Version3 is currently out. Click here to download and install 1.9 Version 3. Update: 1.8 is now officially out! It'll prompt you to update the next time you launch.

What if your fridge knew your food and expiration dates? What if your fridge could tell you which ingredients are missing and where you can get them the cheapest?
For more than a decade, Interplay was arguably the best video game publisher in America. Their list of games is a who's-who of the most creative and forward thinking games of the '90s, including everything fromOut of This World to Alone in the Dark to Earthworm Jim to Descent. They've been around since 1983, but have fallen on hard times since 1997, when they became a public company. They were acquired by a French publisher who then went bankrupt. They were forced to close their internal deve...

I'm a desert island pizza person, meaning, I pretty much never get sick of pizza. When it comes to other favorite cuisines, I operate in cycles - indulge often, grow tired of them, take a break and re-visit in time. But when it comes to pizza, I could eat it every night of the week. I typically practice enough self-control to override this desire, but luckily for me, I made a special concession this past week while creating this article.

Jim Lahey's no-knead pizza dough is more time consuming than Jamie Oliver's "cheat's pizza", but it's quicker and simpler than the more traditional dough recipes. The rise time is only two hours, and the kneading is minimal. I still prefer Jamie's pizza, but I sense this is because I haven't quite mastered Lahey's recipe yet.

Today's segment of Making Art on Your iOS Device takes us into the third dimension. The below apps are suitable for beginners looking to venture into the world of 3d modeling, as well as pros who simply want the basics of Maya in their pocket.

Although circles are Google+'s answer to the problem of social network relationship management, that's not the only thing it's good for. People on Google+ are using circles for all sorts of creative activities, some of which aren't obvious as first glance.

Making a video game requires an incredible amount of work. It requires people skilled in many disciplines to work together for thousands of hours merging visual art, computer programming, game design, sound design, and music composition into a fun game. The Indie Stone is a Scottish indie development studio started, like so many others, by industry vets who were tired of corporate restrictions and wanted to make the crazy games they had always imagined.

A few weeks ago I wrote about Atomic Web as the best web browser for iOS devices, and while I believe it is a superior option, Atomic Web is not the only alternative web browser you can use on your iOS device. There are three more—Dual Browser, iCabMobile, and iSwifter—that are all great options because of their unique features. Let’s check them out.

Do you know how you are perceived by your peers? In real life and online? In the physical world, you could be seen as intelligent, thoughtful and hard-working, but on the Web you could be looked at as irrational, selfish and slothful. There's just something about the Internet that takes away a person's judgement and replaces it with impulsiveness—especially when it comes to Facebook.

Making bread from scratch is extremely difficult. Painstakingly following instructions does not necessarily guarantee successful results. Baking delicious homemade bread takes practice, skill, and frankly, a level of real culinary artistry.

In the wake of the recent tragedy in Japan, Southern Californians have been hyper alert to any news regarding dangerous levels of nuclear radiation drifting over from Fukushima. At this time, official statements from the California Department of Public Health and the EPA are assuaging the population that there is nothing to fear. While there has been some detection of radiation in the air, the current levels recorded are "thousands of times below any conservative level of concern". But despit...

While a lot of internet threats are rather over-hyped, there are some serious things to be cautious of when going online. Probably the biggest risk to the average internet user is malicious software. Commonly knows as "malware," this term refers to any program that exists solely to do harm. This may include damaging your computer or accessing your data without you knowing. Viruses, trojans, and spyware are all forms of malware. Now, malware can seriously mess up your system, and the idea of s...

Note: Little Brother is available as a free ebook download. Warnings

Hi OLers read the following article to gain some great insight into the mischevious advertising ways of food labels. Thanks to the New York Times for this great article below. Happy Eating6 Meaningless Claims on Food LabelsAlthough food labels are supposed to tell us exactly what’s in the food we’re buying, marketers have created a language all their own to make foods sound more healthful than they really are.Today’s “Consumer Ally” column on AOL’s WalletPop site explores misleading food-labe...

Despite the recent problems with the 1.04 update for PlayStation 3 gamers, Call of Duty: Black Ops remains a juggernaut for Activision in the gaming community, and its sales alone prove it.

I keep Pico De Gallo around all the time. I find it is very versatile and can be used for any meal. My youngest son loves to cook and it was one of the first things I taught him to make. As you read my writings about food I've made, you will find a lot of references to the pico. I've made up this little recipe to give you a smile as well as the ingredients and method.

Preparation When creating a new lawn it is essential that the soil is prepared properly to ensure a satisfactory outcome when laying turf or sowing lawn seed. Whether you decide to lay turf or seed, the preparation is the same.

Make Beautiful Cherry Blossoms Out of IcingDecorating a cake or cupcake with cherry blossoms is easy - I'll show you how. First gather what you need:

Learning Style What kind of learner are you? There are three different ways people learn:

We have no control on the weather yet it is a part of our lives which influence what we do, what we eat, what we wear and many times where we live. How did people predict the weather before there was the Internet, television, radio or the weatherperson with all of their gadgets?
How To Stop The Weirdness Lag, Pauses Etc...In FaceBook/ Zynga Games Via Flash! How-To Topics » Facebook, games, facebook games, online games, zynga

If your PS3 is YLOD (flashing the Yellow/Red/Green Light Of Death), try sticking it in the oven. Why does this work? Instructables user formulajake88 explains what causes YLOD and why the oven re-flow method will (likely) work:

If you love to watch something straightforward and dry, this tutorial is perfect for you. This is a very basic video and not that much fun to watch, but you will learn how to navigate pdf documents, if you are an absolute beginner in the world of computers. But we're warning you, there's no sound, small font, and you might get fatigued during the viewing. (We did) Navigate PDF documents in Acrobat Reader.

So, if you are interested in buying copper luster, you should take some time to watch this video series. Sue Shea offers her expertise in the world of antique collecting. Sue shows you the different types and colors of copper luster. She also warns you of the signs of discoloration and restoration. Collect copper luster - Part 1 of 17.

A Self-Protection Guide 1) You can help protect yourself from violent crimes.

We've talked about the deep web before, but we never really covered the details of what's out there. It occurred to me that a nice list of resources would be very helpful to all of you anons out there. Think of this like a helpful brochure to the hidden web.

With the mass arrests of 25 anons in Europe and South America, and the rumors of an FBI sweep on the east coast of America floating around, times look dicey for hackers. Over the past few days, a lot of questions have been posed to me about removing sensitive data from hard drives. Ideas seem to range from magnets to microwaves and a lot of things in-between. So, I'd like to explain a little bit about data forensics, how it works, and the steps you can take to be safe.
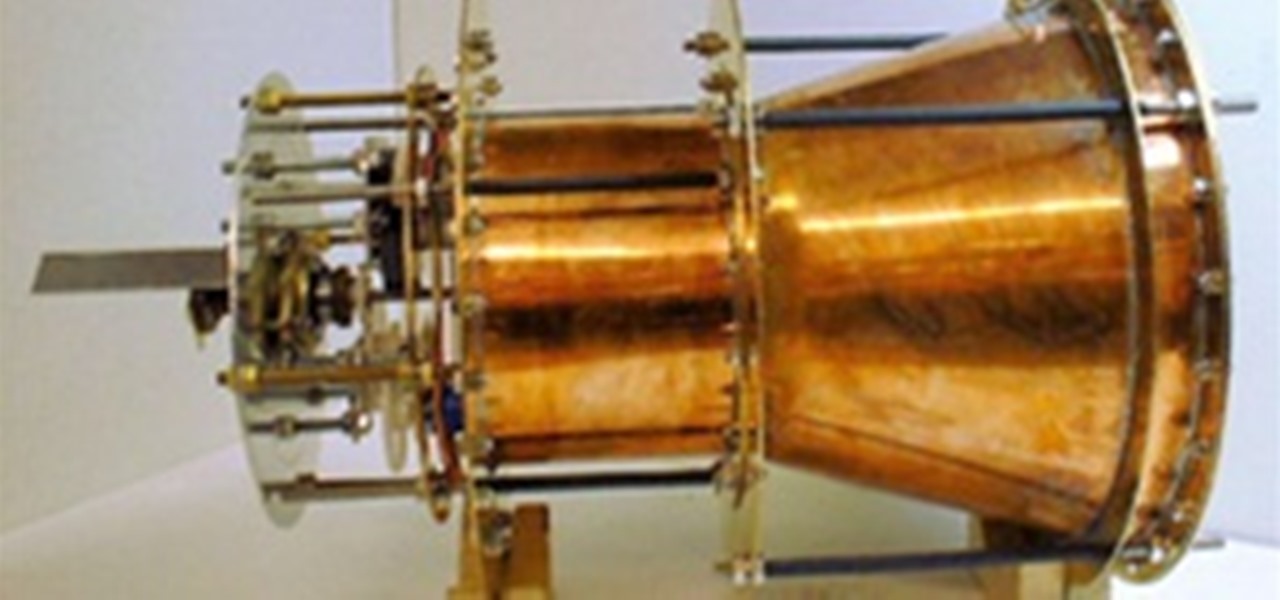
Welcome to Microwave Energy—the next part of my Making Electromagnetic Weapons series. For the Electromagnetic Pulse Generator, check out the last three articles (One, Two and Three).

Hello and welcome to another InfoSecurity World tutorial. The intent of this article is to teach one how to encrypt sensitive files. When set up correctly with a strong password, it would be almost impossible to hack. Even the FBI have had issues decrypting this software. I'm here to teach you how to create a general encrypted container—not the complex hidden TrueCrypt volume.

Yes, you read the title correctly. GameStop has problems, and if you're lax in morals, you can take advantage of them for free games and cash. I'm bringing you all yet another exclusive Null Byte that falls into the fascinating category of life hacking.

Microsoft has had a pretty bad wrap with their Xbox 360 gaming console. Right from the start, the console has suffered a multitude of different hardware failures and design flaws. These problems cause the parts to get too hot and become faulty. I'm sure everyone who's had an Xbox 360 has gotten at least one Red Ring of Death or E74 error.

Cinderella, Little Red Riding Hood and Sleeping Beauty are some of the most horrific fairy tales ever written, but over the course of nearly 200 years they've become watered down and sugar coated for innocent children everywhere. The original tales by the Brothers Grimm are virtually opposites of how we know them today, because they were never really intended for unsullied youngsters. The folk tales came from storytellers across the German countryside, recounting the terrors they've heard ove...

This week seems to have gone by in a flash. Maybe it was the three day weekend, but I don't think it accounts for the flurry of activity I've been seeing on Google+. Updates, debates, and new initiatives are unfolding every day, and the best part is that most of them are coming from outside of Google. People love Google+ so much that they want to evangelize to others about it. What more could Google+ ask for?

Before jumping right into becoming the next James Neely or Moose Peterson, you're going to have get situated with your new digital SLR. No matter if you purchased the Canon EOS 5D Mark II body and lens separately or together, you've got everything you need to get started except the CompactFlash (CF) card. If you plan on shooting in RAW or capturing HD video, I suggest getting an 8GB or larger CF card. If you can afford it, maybe even opt for a high-speed UDMA card.

Shadows of the Dammed (360/PS3) is a polarizing game. It's not shy of being crass and crude. Go ahead and judge the game by the following examples (click to enlarge):

Although Google+ has solved many of our problems with social networking, it's not perfect, and we all wish they'd be a just a little bit faster with the improvements. In the meantime, you can stave off your hunger with useful Google Chrome extensions that improve upon Google+.

Dropbox continues to make headlines with their recent programming blunder which left the accounts of its 25 million customers wide open during a four-hour time span. During the duration, anyone in the world could access any Dropbox profile by typing in any password. And seeing as this wasn't the first security failure, everyone, including the most loyal users are considering dropping the Dropbox.

Dangers abound in the world of srteet art, however one danger stands out as increasingly dangerous. Gangs around the country use graffiti to mark their terriotory and do not take kindly to street artists. In several parts of los angelos gang members will stop you in the middle of the street and ask you if you have spray paint if you are wearing a backpack or a messenger bag. If you answer in the affirmitive (or if they take your bag and find spray paint or markers) its very likely they will s...

Hey editor Mike here from thesubstream and I would like to welcome our newest contributor to the site, our tweens 'n' teens cinema specialist, my little sister Amanda. We're going to make her go watch all the movies that we don't want to see ourselves and then make her tell us and you about them. Up first: the Zac Efron vehicle Charlie St. Cloud.