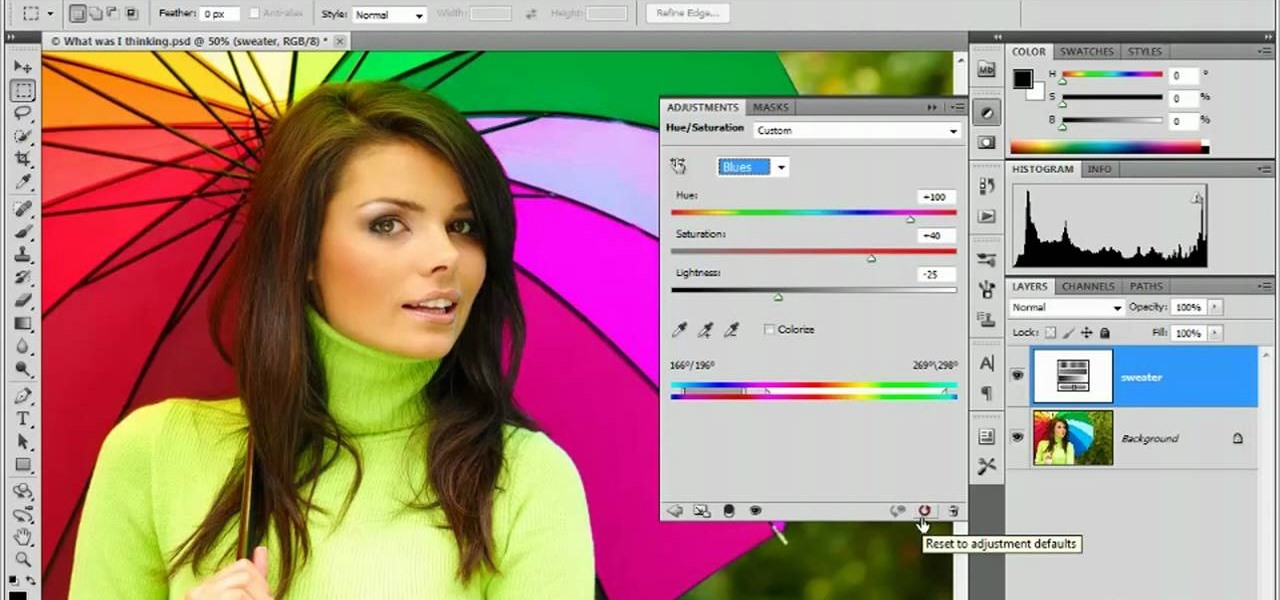
Learn how to use the Target Adjustment feature in Adobe Photoshop CS5. Whether you're new to Adobe's popular image editing software or a seasoned graphic design professional just looking to better acquaint yourself with the unique features of Photoshop CS5, you're sure to find something of value in this free video tutorial.

This video explains how to throw a football like a quarterback. With your elbows bent at a 90-degree angle, hold the ball in front of your chest with the fingers of your throwing hand across the laces of the football.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.
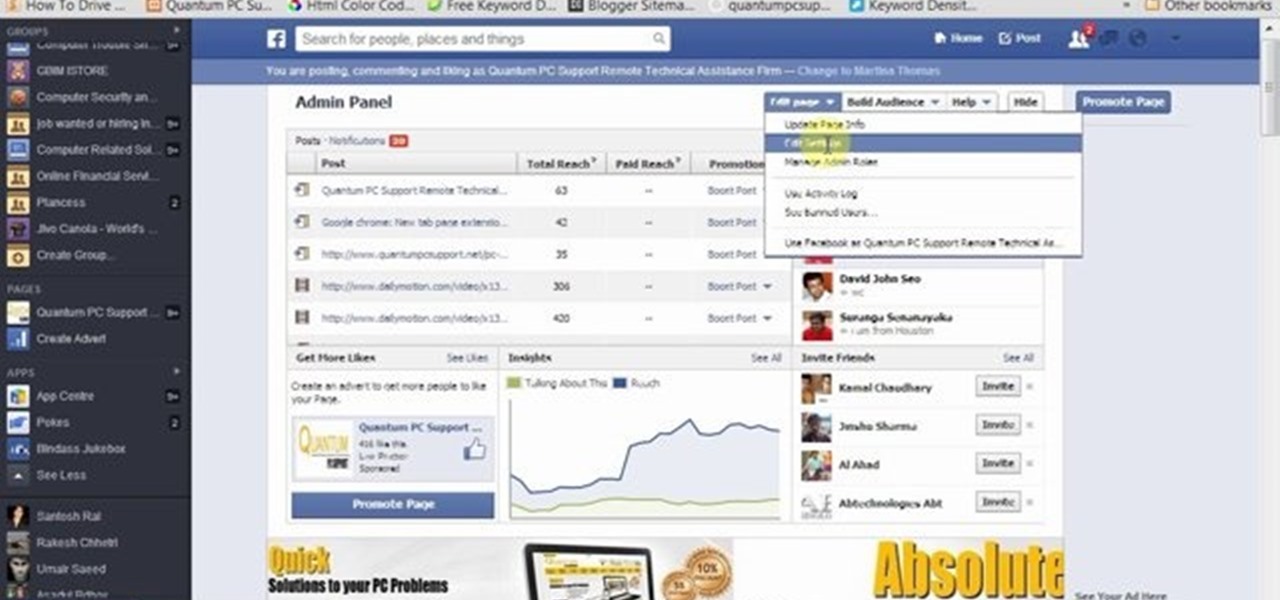
This video will show how to target your facebook post for a specific audience. With this tutorial video you could target a set of audience who has interest about the post.

It's a real challenge to create exploding targets that can be set off by low velocity projectiles, yet remain safe to handle without risk of ignition during construction.

This how to video shows you how to catch a football properly with Vinny. This will be useful if you always drop your catches when tossing a football around. First, you will want to keep your eye on the ball. Next, extend your arms towards the ball. From there, make a target for the thrower. This will make it easier for them to throw the ball to you. Next, tuck and run once you catch the ball. Practice these steps all together until you can catch the football each time you are thrown one. This...

In this video we are shown a workout that targets your stomach and helps you to lose belly fat and tighten your lower abs.

Take a look at this instructional video and learn how to fit a projected image onto a target surface with Johnny Chung from Carnegie Mellon University. Typically, you'd need to use a screen to be directly in front of the projector and at a very specific orientation to get an undistorted image. What this tutorial is trying to accomplish is to place a screen at any location that is convenient and then calibrate the projector onto the target surface. This technique is used to automatically disco...

The object is to pass to ball between the cones in as few shots as possible, watch and learn how to do this target passing soccer drill.

All-American Skeet Champion Todd Bender explains the safety "does and don'ts" of shooting clay targets. He shows how everyone in the family can enjoy the game and still use proper gun handling techniques.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

Popping a shell is often the main goal of a hacker, and it can be exciting when executed properly, but sometimes they do have their limitations. Metasploit's Meterpreter probably needs no introduction, but this powerful, dynamic payload can offer a leg up over normal shells. To prove it, we'll show how to take a normal command shell and elevate it to a Meterpreter session.

Let's face it, iPhones are expensive. With the latest iPhone XS Max reaching as high as $1,449, our wallets could all use a little support. That's where Black Friday comes in, supplying us with deals and discounts on iPhones of all kinds. If you're looking for a new iPhone this holiday season without having to break the bank, you've come to the right place.

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

Starting Nov. 1, 2018, Google got a lot tougher with Android app developers. New apps being uploaded to the Play Store already had to target Android 8.0 Oreo or higher as of August, but now, every update to existing apps has to do the same. It may seem like a simple rule, but it will have some serious repercussions.

Our smartphones have outlived the Walkman, iPod, and even stereo systems, to some degree. So it makes sense to treat your iPhone or Android device to a quality pair of headphones, whether you're a hardcore audiophile or just an everyday music lover. This doesn't come cheap, of course, so why not buy them on Black Friday?

Greetings dear null byters, today we start a new series, we will start to attack users using social networking that are popular such as Facebook, Skype, and much more, and in part 1 of the series will engage users of Skype.

Welcome back, my fledgling hackers! Sometimes, for a variety of reasons, we can only get a command shell on our target system. For instance, with Metasploit, it's not always possible to get the all powerful Meterpreter on our target system. In other cases, we may be able to connect to a command shell via Netcat or Cryptcat.

In this tutorial, we learn how to unlock the Tank Dropper achievement in Halo 3. This is an easy achievement that you will do when you first start out in the level. This is where you have to drop a tank onto someone and kill them. To do this, you need to stand up on a higher area and find your target. Once you do this, you will be able to grab the tank and then drop it onto the target you have found. After this, you will get the achievement and you will be able to continue on. If you miss, ju...

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

On August 1, Google Play started requiring new app submissions to target at least Android 8.0 Oreo's API. Then, as of November 1, all updates to existing apps were required target the same API. While at first glance, this change may mean little to you, it will have a profound impact on Android. Now, your favorite apps will be getting better.

Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to inject a meeting or event into a target's Google Calendar and use it to exploit them.

Dating websites allow you to see a person in a very intimate context, framing their successes and accomplishments in life to an important audience. The information contained in these profiles often can't be found elsewhere, offering a unique look into the personal life of the user.

Welcome back, my greenhorn hackers! Before we attempt to exploit any target, it is wise to do proper reconnaissance. Without doing reconnaissance, you will likely be wasting your time and energy as well as risking your freedom. In previous guides, I have demonstrated multiple ways to perform reconnaissance including passive recon with Netcraft, active recon with Nmap or hping3, recon by exploiting DNS or SNMP, and many others.

Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely dampened Target's Christmas sales, reputation, and stock price (the company's value has fallen by $5B).

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

When it comes to web-based augmented reality, 8th Wall has emerged as one of the leading platform providers, and the company just cranked up its capabilities another notch for AR marketers.

There are many ways to attack a Wi-Fi network. The type of encryption, manufacturer settings, and the number of clients connected all dictate how easy a target is to attack and what method would work best. Wifite2 is a powerful tool that automates Wi-Fi hacking, allowing you to select targets in range and let the script choose the best strategy for each network.

This year's holiday shopping season is shaping up to be fertile ground for augmented reality to show its worth, as both Walmart and Target have crafted immersive experiences designed to engage shoppers in the coming weeks.

Virtual reality headsets aren't new, but they may be something you or someone on your holiday shopping list hasn't experienced yet. If you're going to dive into the world of smartphone-based virtual reality, the best time to do it is during Black Friday when all the good sales are going on.

Black Friday is fast approaching, and just like every other day-after-Thanksgiving, there will be too many tech deals you won't want to pass up. If you've been saving up all year just for this sometimes-chaotic shopping holiday, we'll help you figure out the best tech sales to take advantage of and when, whether it's Black Thursday, Black Friday, or Black Friday weekend.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Looking to work on your form? Try this free video golfing lesson for size. In short: When putting, to be able to release the putter down the line to your target, the club must travel slightly inside the target line. For a complete overview of how to become a better putter, watch this video guide.

A lot of time can be wasted performing trivial tasks over and over again, and it's especially true when it comes to hacking and penetration testing. Trying different shells to own a target, and testing out privilege escalation commands afterward, can eat up a lot of time. Fortunately, there is a tool called One-Lin3r that can quickly generate shells, privesc commands, and more.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.