
How To: Build a Fully-Automated Melon Farm
Firstly, let me say a few quick things: Once built, this is a lazy (one button) way to harvest melons, but this is going to be a complex and lengthy build.


Firstly, let me say a few quick things: Once built, this is a lazy (one button) way to harvest melons, but this is going to be a complex and lengthy build.
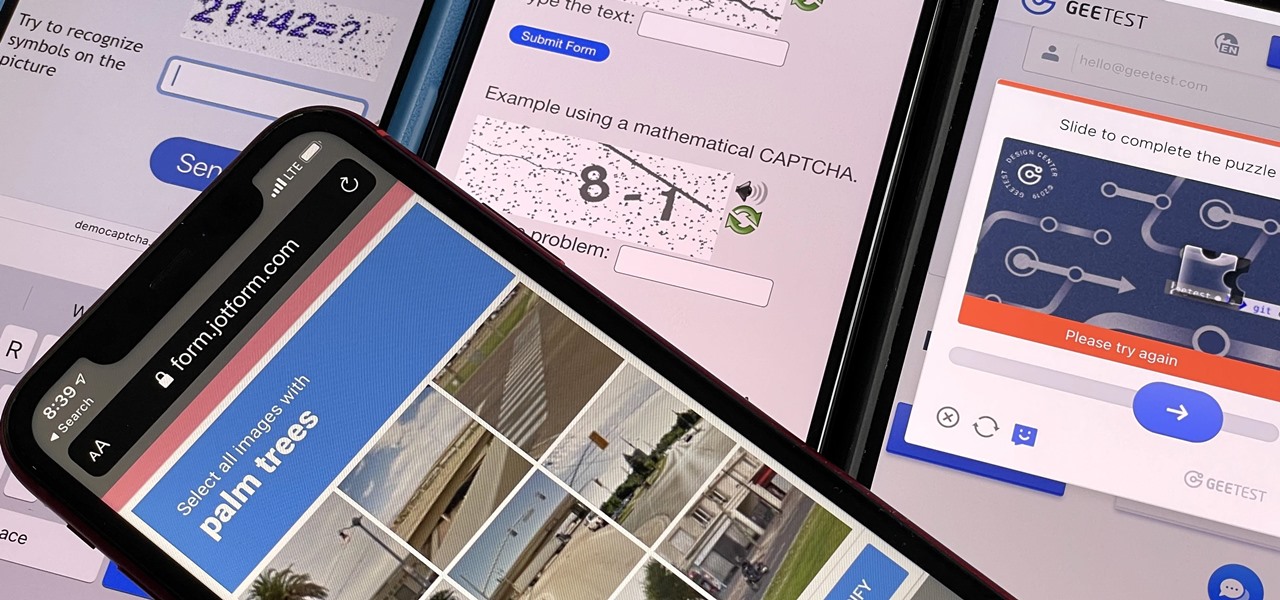
Some websites require you to perform a verification task so they know you're human and not a bot. It helps websites curb spam, abuse, unauthorized access, and cyberattacks but also adds an obstacle for anyone trying to visit their content. If you find it more of a nuisance than a necessary evil, there's an easy way to reduce the number of human verification prompts you receive on your iPhone, iPad, and/or Mac.
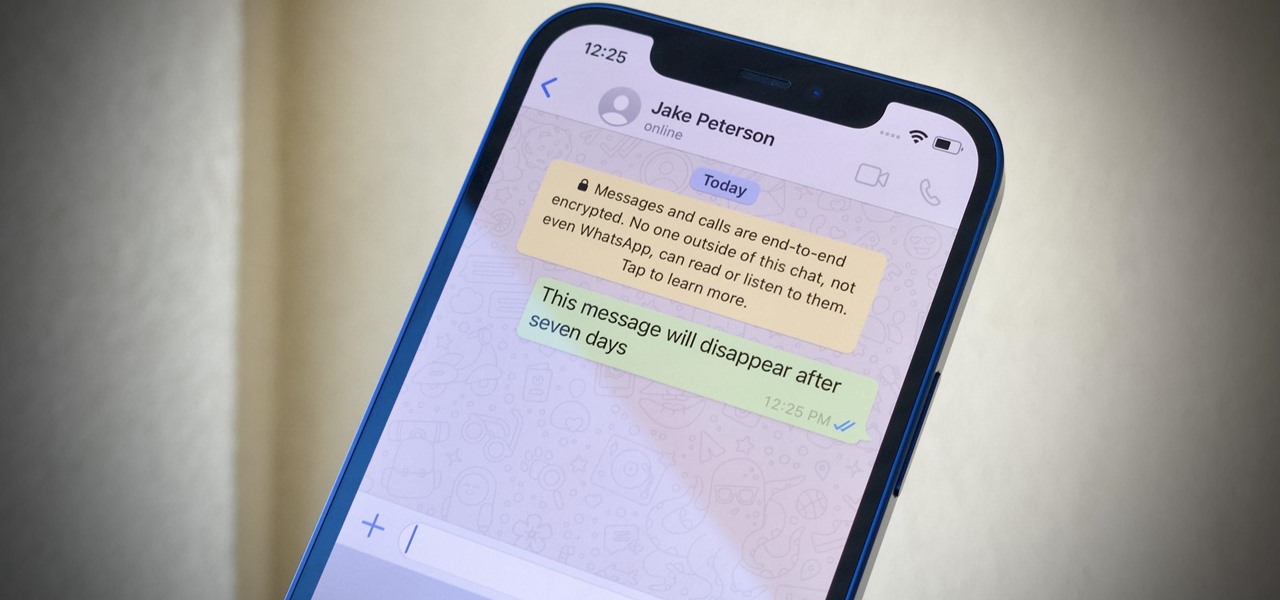
Sometimes, keeping every message comes in handy. Maybe you want to relive fun conversations from months or years ago, or perhaps you need to recall a piece of data such as an address, name, or link. However, not all chats need to stick around forever. Whether you're concerned about privacy or just keeping your threads clutter-free, WhatsApp's "disappearing messages" may be what you're looking for.

It's common knowledge these days that Apple puts great cameras into their iPhones. So, it probably comes as no surprise to learn that the iPhone 12, 12 mini, 12 Pro, and 12 Pro Max sport some excellent shooters. What you might not know, however, is that these cameras are quite literally capable of Hollywood-quality video. So don't be surprised to see one of these filming a Netflix series.

Does TikTok scare you? Trust me, I get it. It's a strange, unfamiliar place to those of us not accustomed to its ways, populated by teenagers and college students with their own subcultures, memes, and humor. But here's the thing: TikTok has something for everyone, you included.
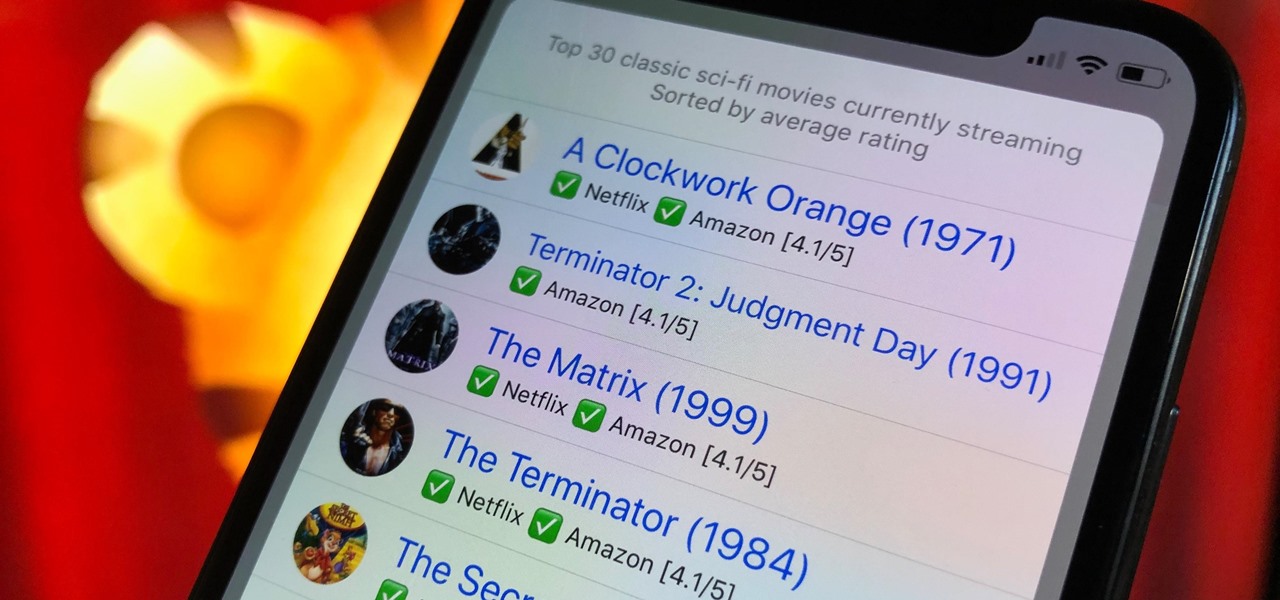
Choosing a movie to watch at home can be incredibly difficult when you don't already have one in mind. But there's a shortcut for your iPhone that can make it easier to browse your streaming media services for something good to play. More specifically, it lets you browse Netflix and Amazon Prime at the same time.

So you want to know what that person who is always on their phone is up to? If you're on the same Wi-Fi network, it's as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a phone is running in real time.

Black Friday is upon us. Whether you prefer to duke it out in stores or calmly shop online, there's no doubt you'll find great deals on the items you're looking for this holiday season. It's the perfect time of year to buy something expensive, like a good pair of AirPods, Beats, or Bose, at a much more opportune price.

It's finally out. After months of testing, iOS 13 is available to install on your iPhone, which means over 200+ new features you can use right now. The update, released on Sept. 19, can be installed over the air or from a restore image using iTunes in macOS Mojave and older or Finder in macOS Catalina. Ditto for the 13.1 update issued on Sept. 24.
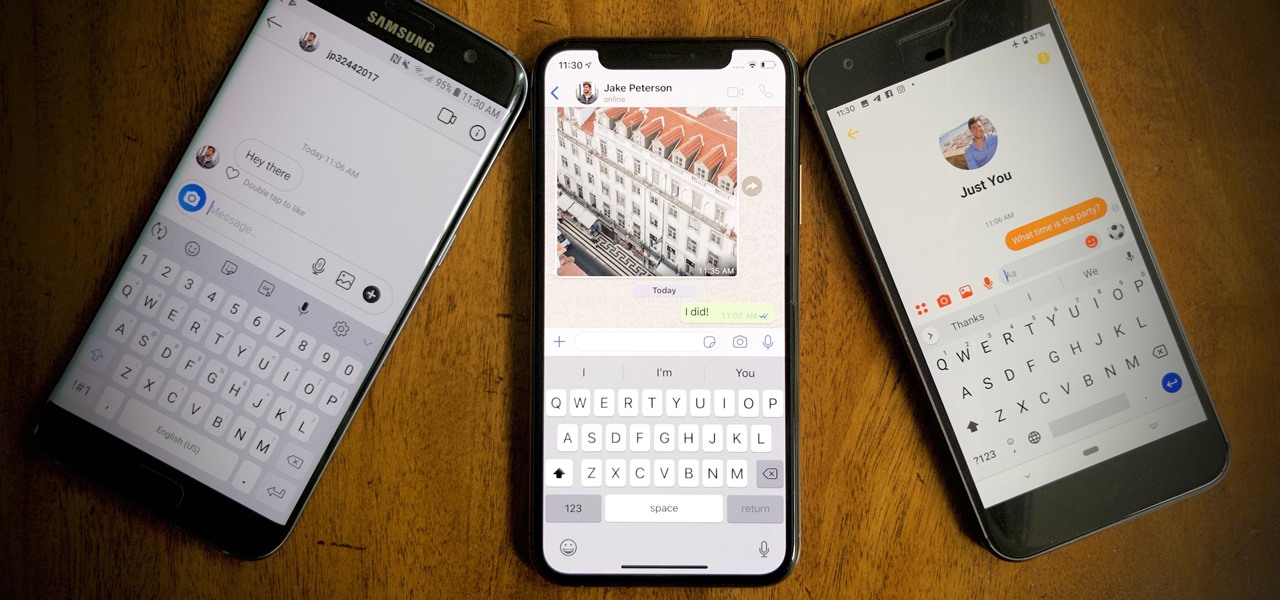
You're in constant communication with your friends and family. The only issue? Nobody uses the same app. Messenger, Instagram, WhatsApp — you have contacts spanning all three, and the resulting balancing-act to keep in touch can be overwhelming. That's why Facebook — who owns all three apps — is coming out with a way to call and message friends across all three platforms from one place.

Whenever a new, category-defining Apple product is in the works, we usually get a series of creative concept designs to accompany the rumors swirling around the prospective launch.

You can almost detect the collective breath-holding of the augmented reality industry as it waits for Apple's inevitable entry. A new Apple wearable built with augmented reality technology is likely the device that will finally make the smartphone take a backseat.

Smartphones are now indispensable when traveling. Domestic and overseas travel alike require food, navigation, translation, and so much more to make work or vacation successful. Gone are the days of lugging multiple tourist books around with you everywhere you go — you need to let your smartphone handle the dirty work.

One of the best things about Android is the ability to customize every aspect of your device to make it your own. However, unless you have prior knowledge or experience with every single setting available to you, you might have missed a few critical features without even knowing it. Some settings are easy to find, while others might be tucked away in another menu of their own.
With Unc0ver, Pwn20wnd was the first to jailbreak an iPhone and iPad running iOS 12 versions. While it initially couldn't work on all devices, it's an entirely different story now. Unc0ver currently works up to iOS 13.5 for most A7 to A13-powered devices. Plus, Chimera, another jailbreak tool, supports a similar range of models on iOS 12 to 12.3 and iOS 12.4.

We recently set out to find the best phones for people whose primary usage revolves around social media apps like Facebook and Instagram. Samsung, Apple, and Google were the three brands that made our top five, and while the latter only had one finalist, the two bigger OEMs had a pair of phones each. What struck us, however, was that Samsung's phones edged out Apple's not once, but twice.
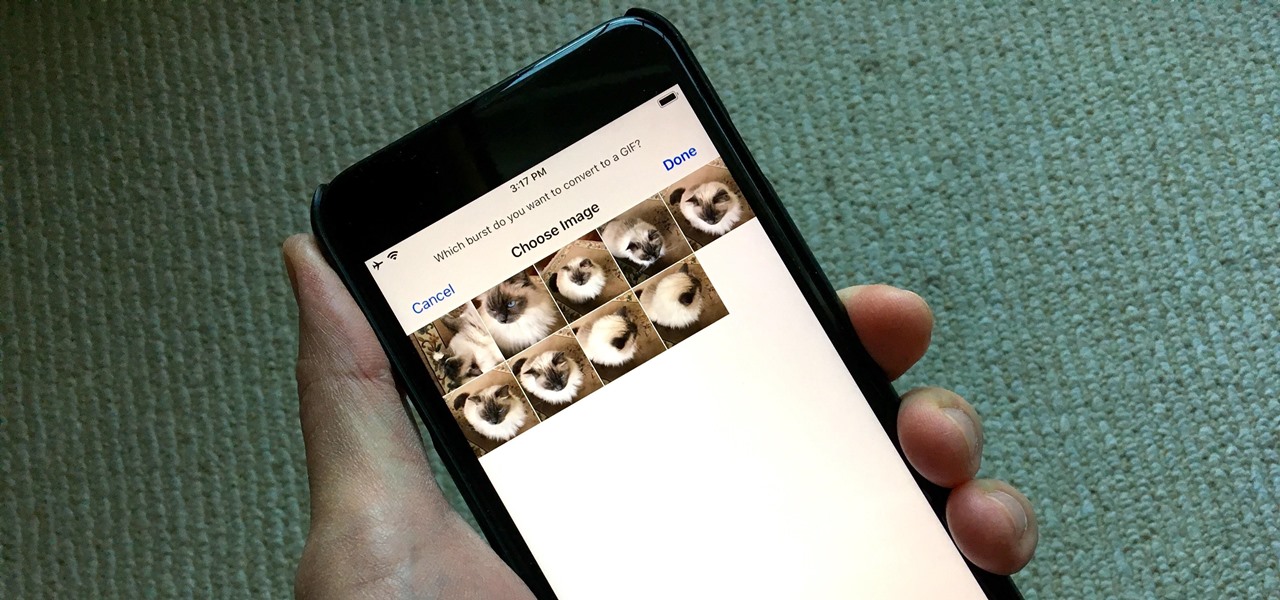
Creating GIFs of your own burst images has been possible for a while with third-party iOS apps, some of which cost money or include in-app purchases to utilize the full potential. Fortunately, with Shortcuts, Apple's automation workflow app, there's finally a native way to achieve this without spending any cash.
No matter how good a display is, the idea of perfect color calibration is subjective — some prefer warmer more saturated colors, while others prefer the calmer cooler side of the color spectrum. It is almost impossible to create a single color calibration that everyone can agree on out of the box. The display on the Pixel 2 XL was specifically calibrated with a more realistic color profile in mind.

A burner number isn't just for criminals and cheating spouses. In this digital world, with many of our interactions being conducted online, a throwaway phone number acts as a buffer — it lets you enjoy the web without having to give out your personal information, such as real name or phone number.

Single sign-on (SSO) lets users login across different sites without having to manage multiple accounts. I'm sure most of us appreciate the convenience of seeing "Sign in with …" buttons that let us login with a single username. Hackers, however, see a possible avenue for exploitation, and you'll soon learn how an attacker can exploit a SAML vulnerability to assume another user's identity.

Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

Koadic allows hackers to monitor and control exploited Windows systems remotely. The tool facilitates remote access to Windows devices via the Windows Script Host, working with practically every version of Windows. Koadic is capable of sitting entirely in memory to evade detection and is able to cryptographically secure its own web command-and-control communications.

The threat of an evil access point has been around for a long time, and with the rise of open public Wi-Fi, that threat is often overshadowed by how comfortable we are using third-party Wi-Fi hotspots at coffee shops and public spaces. While we've shown an evil twin attack using the Aircrack-ng suite of tools, MitmAP is a Python tool to configure custom APs for many types of wireless attacks.

Threats to your privacy and security are everywhere, so protecting your data should be the highest priority for anyone with a smartphone. However, one threat many people overlook is the company who supplies the operating system your Android phone runs — Google.

In our previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when an MS Word document is opened. Because Microsoft built DDE into all of its Office products as a way to transfer data one time or continuously between applications, we can do the same thing in Excel to create a spreadsheet that runs malicious code when opened. The best part is, it will do so without requiring macros to be enabled.

Ransomware is software that encrypts a victim's entire hard drive, blocking access to their files unless they pay a ransom to the attacker to get the decryption key. In this tutorial, you'll learn how easy it is to use the USB Rubber Ducky, which is disguised as an ordinary flash drive, to deploy ransomware on a victim's computer within seconds. With an attack that only takes a moment, you'll need to know how to defend yourself.

Due to the overnight success of smartphones, millions of people are connecting with others. Currently, over 15 million text messages are sent every minute worldwide. Most of this communication is happening in the open where any hacker can intercept and share in the discussion unbeknownst to the participants. However, we don't need to communicate insecurely.
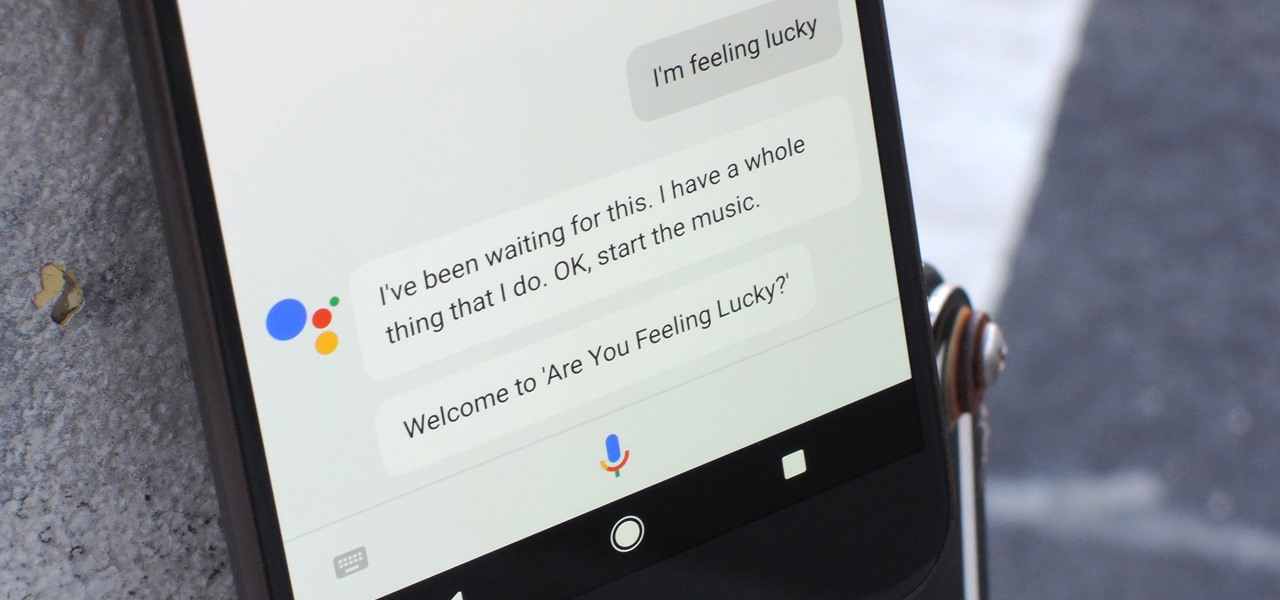
Despite a rocky start with plenty of feature disparity, the Google Assistant now provides a pretty consistent experience regardless of what device you're using it on. Be it Android, iPhone, or Google Home, the AI behind the Assistant is virtually identical — including its quirky commands and funny responses.

Signal Private Messenger is famous for its end-to-end encryption, but you can't even use the messaging app without having a real phone number attached to it. Luckily, there is a way around this limitation, so you can use Signal even if you don't have a valid SIM card in your smartphone.

Kuru is called the shaking disease, its name derived from the Fore word for "to shake." Caused by an organism that infects the part of the brain that controls coordination, people afflicted with kuru shake uncontrollably.

After enabling disk encryption, creating encrypted disk images, installing KeePassX and iTerm2, and using Git with local repositories, the next step to getting your Mac computer ready for hacking is setting up a package manager that can install and update open-source hacking tools. There are multiple options to choose from, but Homebrew has a slight advantage.

There's a common saying that separates cooks from bakers: baking is a science, while cooking is an art. When baking, one little misstep can alter the texture, taste, and consistency of any recipe.

I'm an Android user. Over the course of the past seven years, I've owned ten different smartphones—all of them powered by Android. This isn't due to some blind trust in Google or some unfounded hate for Apple, either, because I've always made sure to get my hands on each iPhone iteration along the way to see what it had to offer.

When a headache strikes, I reach for the nearest painkiller. Forget closing my eyes, laying down, or even applying an ice pack—I seek the quickest and most immediate relief possible, and normally that comes in the form of pills. However, fast relief can be found from another, more natural source: herbal beverages. So if you're tired of popping pills when you have aches and pains, try some of these herbal drinks out instead.

Welcome back, everybody. In the previous article, we covered the ideas and concepts of well-known ports and trust exploitation in order to evade a firewall. Today, we'll be building the shell, the part that receives commands, executes them, and sends the output back to the attacker.

Most of us lead busy, work-filled lives, often clocking in a 9-to-5 five days a week. And when that clock signifies the hour to leave, the last thing on anyone's mind is: "Time to go to the grocery store to pick up more fresh produce!" (Well, to be fair... maybe more people are psyched about this, but I know with certainty that I am not one of them.)

If you haven't read the last article, feel free to stop by and give it a read, but abstaining from reading it will not, for the most part, be detrimental to your understanding.

We are most certainly not machines. We all need some downtime every once in a while to set our sanity scales back in balance, which in turn, makes us more productive workers. This is a premise that several forward-thinking employers fully understand, but these types of companies are few and far between in corporate America.

My bathroom is like my own private arcade room. Whenever I'm seated comfortably on the toilet, no one is going to disturb me, so I can play anything I want on my smartphone. You probably do it, too — and your parents, kids, friends, colleagues, and boss — so don't be afraid to admit it.

One of Android's biggest strengths, when compared to other mobile operating systems is its open file structure. Google introduced a built-in file manager with Marshmallow that provides basic file management, but like with most apps on Android, there are alternatives. Third-party file managers are readily available, providing deeper access and control of all your files.