False eyelashes scare many girls, but trust us when we say that it's more due to fear of the unknown than because these false eyelashes are actually difficult to apply. Break your false eyelash virginity by checking out this makeup tutorial.

The Talismoon Whisper Legacy is one of several fan upgrades available for the XBox 360 that can help mitigate the console's extreme cooling issues. This video will show you how to install this model of fan upgrade in your console. Trust us, you console will work better and be nearly immune to the Red Ring of Death.

Garmin is a popular and trusted brand of GPS devices. In this video, learn how to enter destinations and perform other basic tasks with a Garmin Nuvi 750. This video shows you the Nuvi 750 but all of the instructions should also work with other Garmin models. GPS is fantastic for traveling to new destinations, getting out of a lost situation and finding unknown places faster.

Pole dancing is a great way to feel sexy and get in shape. In this how to video learn to trust the pole and do the basic pole slide.
Here, you'll hear all about the materials needed to teach English as a foreign language. This guy knows. Trust me.

Today's word is "xenophobic". This is an adjective which means being fearful of, or showing distrust or hatred towards foreigners and strangers.

Watch this video to learn how to make delicious restaurant meals in your own kitchen. In this episode learn to bake peach cobbler with Scott Hargrove. Trust me... it's really great!

This is actually a really easy and fun prank to pull off. What it does is simply switch the right click on your mouse, to the left click, and switch the left click, to the right click. Confused yet? Follow these simple instructions to test it out yourself, and enjoy your victims reactions when they get this prank pulled on them, trust me, it's funny!

While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of built-in graphical X forwarding for SSH.

While other devices are moving away from fingerprint scanners (cough, iPhone X), for many, a fingerprint scanner provides the best balance between security and speed. Typically, the rear fingerprint scanner on the LG V30 is quick and accurate, but every so often the phone will not recognize a registered fingerprint.

Hello, everyone. Stealth is a large part of any successful hack; if we don't get noticed, we're much less likely to be caught. In these next few articles, we'll be building a shell based on keeping us hidden from a firewall. There are many ways to stay hidden from a firewall, but we'll only be incorporating a couple into our shell. This article will outline and explain these evasion concepts and techniques.

Of course, if it were a perfect form of currency, it would have become the standard by now. But it hasn't. Wanna know why? The story begins with the advent of agriculture, when humans had settled down under groups as units called villages, over 10,000 years ago.

With all of the personal data that's stored on our smartphones, it's of vital importance that we have some sort of lock screen security enabled. One of the Galaxy S5's killer features is obviously the fingerprint scanner. It makes the process of dealing with a secure lock screen a bit easier than typing in a password or PIN.

If you've ever connected your iPhone to a computer before, you know iOS prompts you to "Trust" the computer and enter your passcode to confirm. According to Apple, trusted computers can "sync with your iOS device, create backups, and access your device's photos, videos, contacts, and other content." That's a lot of permissions to hand off, especially if the computer's not your main laptop or desktop.

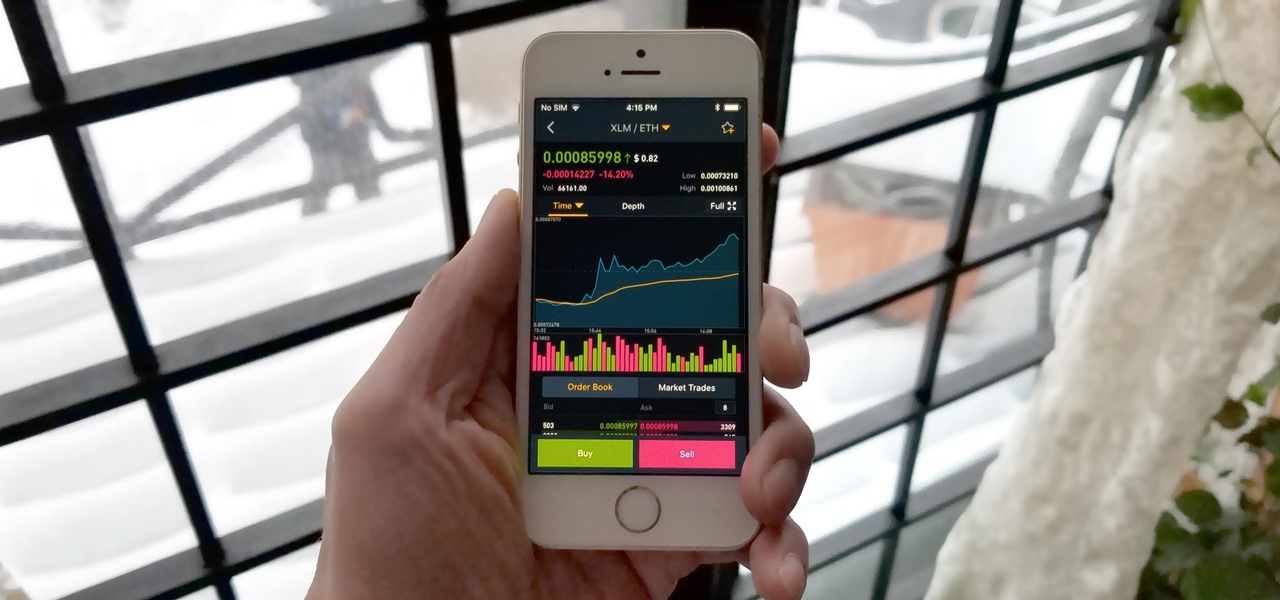
Binance, a China-based cryptocurrency exchange, is rapidly gaining popularity thanks to the sheer selection of digital currencies you can purchase — Ripple (XRP), Tron (TRX), IOTA, and Stellar (XLM), to name a few — using both Bitcoin (BTC) and Ethereum (ETH). Binance has an iOS app, and there are a couple ways to install it. Either way, you can trade cryptocurrency from your iPhone today.

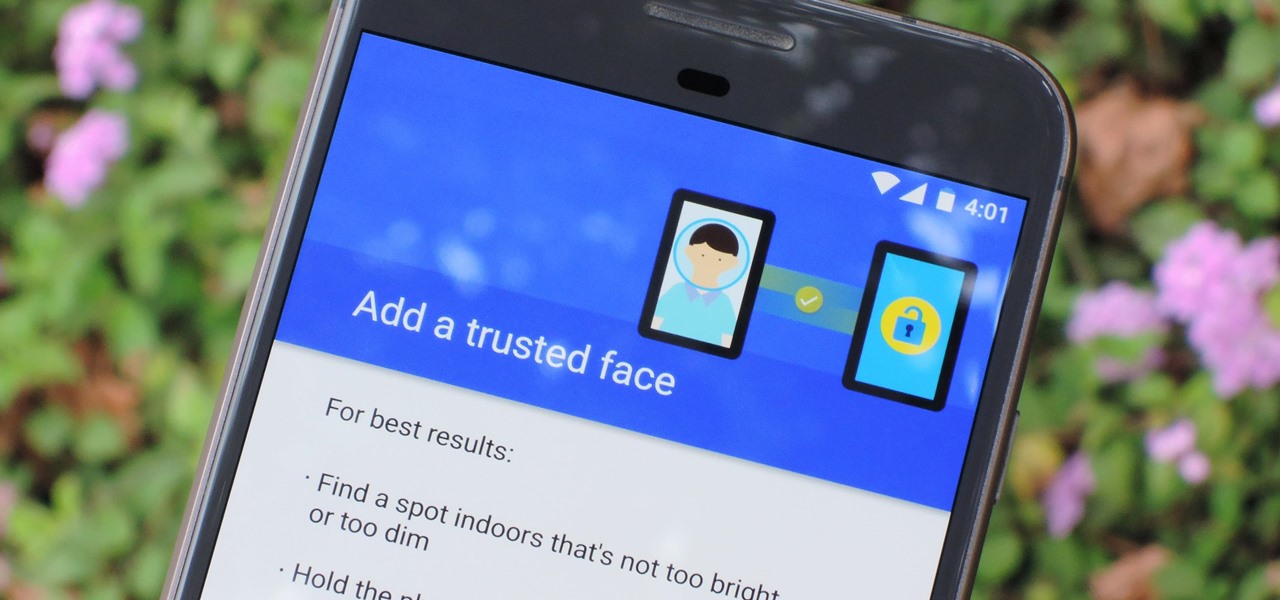
The iPhone X has a new unlocking mechanism called Face ID, which replaces the old Touch ID system since the phone no longer has a fingerprint sensor. The way it works is simple — you just look at the phone, it recognizes your face, then the system unlocks — so Apple deserves the praise they're getting for it. But did you know you can get almost this exact same feature on any Android device right now?

The original implementation of Android's face unlock feature was a mess. It took too long to unlock (when it worked), brought up a huge interface that overpowered the lock screen, and maybe most egregiously, was able to be "hacked" by someone holding up a picture of your mug.

I think it's safe to assume that most of us appreciate a little privacy and security when it comes to our mobile devices, which is exactly why we have lock screens that require unique passwords, patterns, or PINs. Although someone can discretely peer over your shoulder to see what your password is, it's much more difficult for them to duplicate your face to unlock the device.

Imagine this: You're driving on the freeway in Canada, enjoying the view and sipping Tim Horton's, when all of the sudden you see something out of the corner of your eye. You expect it to be a moose, obviously, but instead you see a robot with his thumb hitched up. So, after insuring that you didn't accidentally take some hallucinogens a few miles back, do you pick it up?

Worried about a zombie apocalypse? Of course you are, we all are! This tongue in cheek video divulges the steps you'll need to take should zombies begin roaming the earth. Using clips from horror movies, this video shows you the right way to hide from zombies and even explains who you can trust. Learn what weapons work on zombies and how to cripple them and most importantly, destroy their brain! Nobody wants to get bitten by a zombie, learn how to escape, travel and even how to recognize if o...

Ever tried to sign up for auto-insurance, or some other thing that required your VIN number, and ran around trying to find it in frustration? Well frustrate no more good people! This video will show you all of the various places that you can locate your VIN number! Trust me, there's a lot....

Hanging out with the folks can be fun. Really, trust us. This video gives tips on how to obtain a better relationship with your parents.

Learn how to kickbox from the trusted folks at Expert Village. Strap on your gloves and get in shape with some simple tips and workouts. This video is a culmination of moves that you can learn individually as well.

A great many S8 and S8+ users have undoubtedly spent quite a bit of time figuring out ways to unlock their new Galaxy in as few steps as possible. One of the most endearing features of previous Galaxy models was the ability to unlock the phone by pressing the home button and momentarily leaving your finger there for the sensor to do its job, almost instantaneously opening the device — all without having to pick up the phone.

This could happen when you trust a guy to hang out wet clothes. Ladies, beware, guys simplify housework simply because they don't care of it's a chore they just don't want. Watch and learn to be creative about the ways you spice your every day chores up. Most of all, laugh your head off.

If you're not one to trust you digital SLR camera's automatic focus options, then the only thing you have to do is go to manual mode. With the Canon EOS 7D, select the Manual AF Point Selection and take control. It allows you to pick the area you want to focus on.

Learn how to bake a scrumptious apple crisp with this cooking video. This apple crisp recipe is brought to you by Sarah Bacon on How2Heroes. Search How2Heroes on WonderHowTo for more cooking videos.

By far the most significant development for AR in the coming months and years — the development that will drive AR adoption — will be our reliance upon the AR cloud.

The OnePlus 5T was just released, and it's packing several new useful features. While many OnePlus 5 buyers are feeling frustrated with the quick release cycle, lots of fans are still clamoring to buy the new device. Aside from the larger screen, most of the buzz around the 5T has centered around the new face unlock method. Thanks to a clever hack, you can now get this feature on almost any phone!

Steer clear from empty flattery and malicious social engineering with these tips on how to avoid a player.

Keep your possessions safe from thieves with these tips. You Will Need

Discovering your partner's affair can be devastating, but it doesn't have to mean the end of the relationship.

A macOS computer can reveal a lot of information about the owner, including which Wi-Fi network they have permission to access. With an Arduino-based attack, we'll use a five-dollar setup to inject a rogue Wi-Fi network and steal the list of trusted Wi-Fi networks, allowing us to see where the computer has been.

So it's 2017 and there are no flying cars and teleportation devices around, but there might be holographic smartphones sometime soon. As cool as that sounds, should we trust a holographic smartphone from a company that has never made smartphones before?

Things aren't looking good for Uber after its driverless experiment in Pittsburgh soured relations with local authorities. Surprised? Me neither.

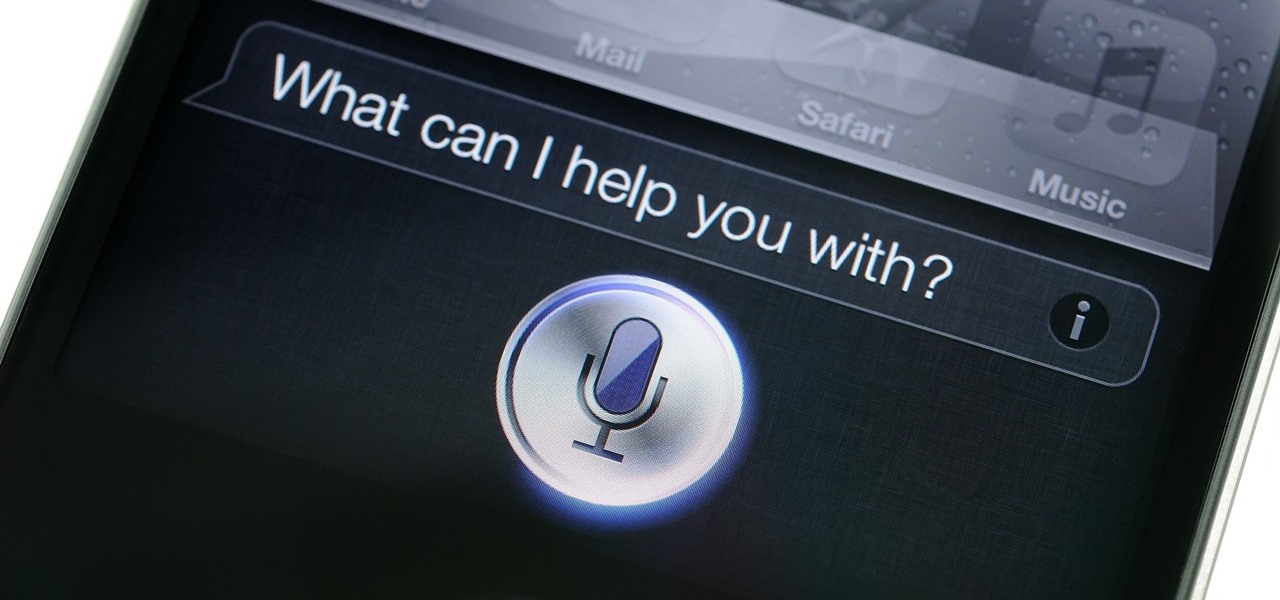
If you follow tech, you're probably familiar with Siri, Apple's personal voice assistant, which has been integrated heavily into iOS ever since iOS 5. But you might not have known that Siri is capable of performing some tasks when the iPhone is in a locked state. The default state of iOS is to allow access to Siri from the lock screen, most likely for the convenience of hands-free access to the phone.

These days, that pocket-sized computer we call a smartphone is home to your entire digital life. But with the onset of mobile payments and online banking, the line between your virtual world and the physical realm is becoming increasingly blurred.

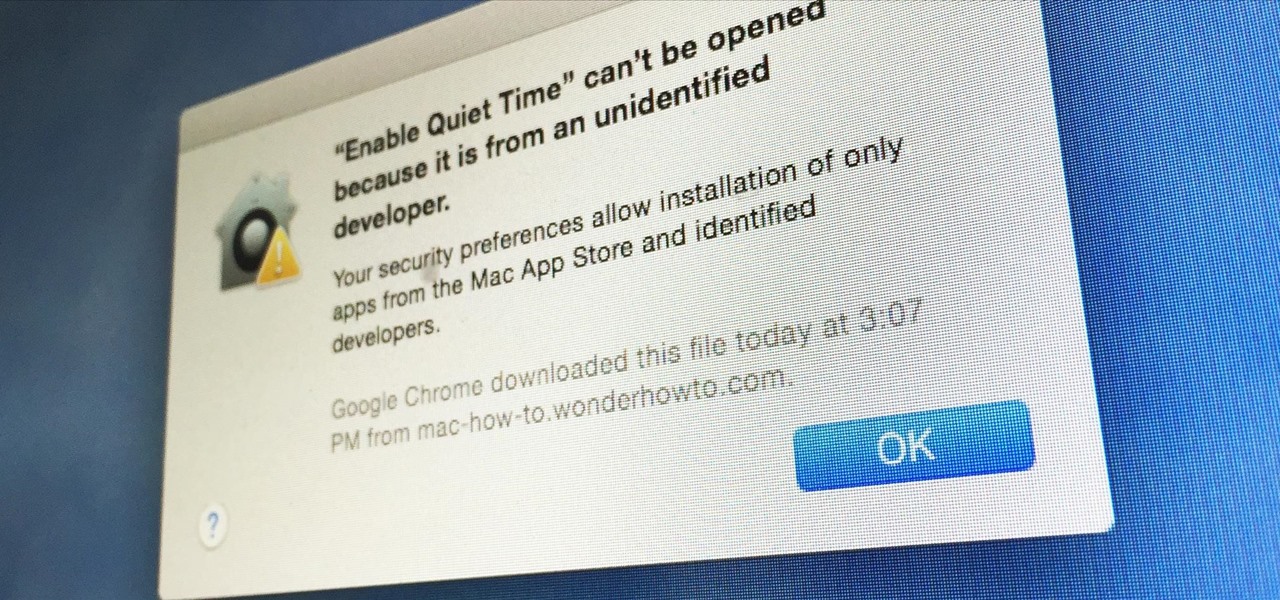
Apple has a built-in way to protect you from opening up potentially malicious apps on your computer in Mac OS X Lion, Mountain Lion, Mavericks, Yosemite, El Capitan, and macOS Sierra. This setting, named Gatekeeper, will never stop you from installing apps from the Mac App Store, but it could from anywhere else. If it's an app you're sure you want to install on your system, here's how to do it.

Leaving your Wi-Fi radio "on" allows your smartphone to auto-connect to trusted wireless networks in lieu of using cellular data, but it also consumes battery power while it's constantly network hunting.

If you were born with skinny, thin lips, then lip plumpers are probably your best friend. We get it: Plump, pillowy soft lips are gorgeous, but at the same time we don't know if we trust all those gnarly ingredients that most lip plumpers contain.