The Fireworks 8 pen tool lets you create straight or curved line segments by placing points. Pen tool creates object lines that can be altered by sub-selecting and modifying one or more control points. In this Fireworks 8 video tutorial you will learn how to use Vector Pen Tool, and adjust its parameters. Make sure to hit "play tutorial" in the top left corner of the video to start the video. There is no sound, so you'll need to watch the pop-up directions. Use the Vector Pen Tool in Firework...
Creating high-quality marketing content for your brand is labor-intensive to the point that it could be a job of its own.

If you have no intention of getting personalized engravings on your AirTags, you don't need to shop on the Apple Store unless you have an Apple Card you want to earn Daily Cash with. Best Buy. Target. Adorama. B&H Photo. All of those places will let you preorder AirTags now but so does Amazon, America's second-biggest retailer, a good choice whether you have Amazon Prime or not.

When you need to type in all caps on a computer, you just press the "caps lock" key. But no such key seems to exist on iOS. The "shift" key appears to work at first but will deactivate once you type one capital letter. Holding down the shift key while you type gets the job done, but it's a pain. While it might not be obvious, enabling caps lock is actually really simple.

The term "hacker" often has negative associations attached to it, yet the world is in dire need of professionals with hacking skills. White hat hackers are ethical computer hackers that use their hacking skills to pinpoint network vulnerabilities and patch them up before they can be exploited by the bad guys.
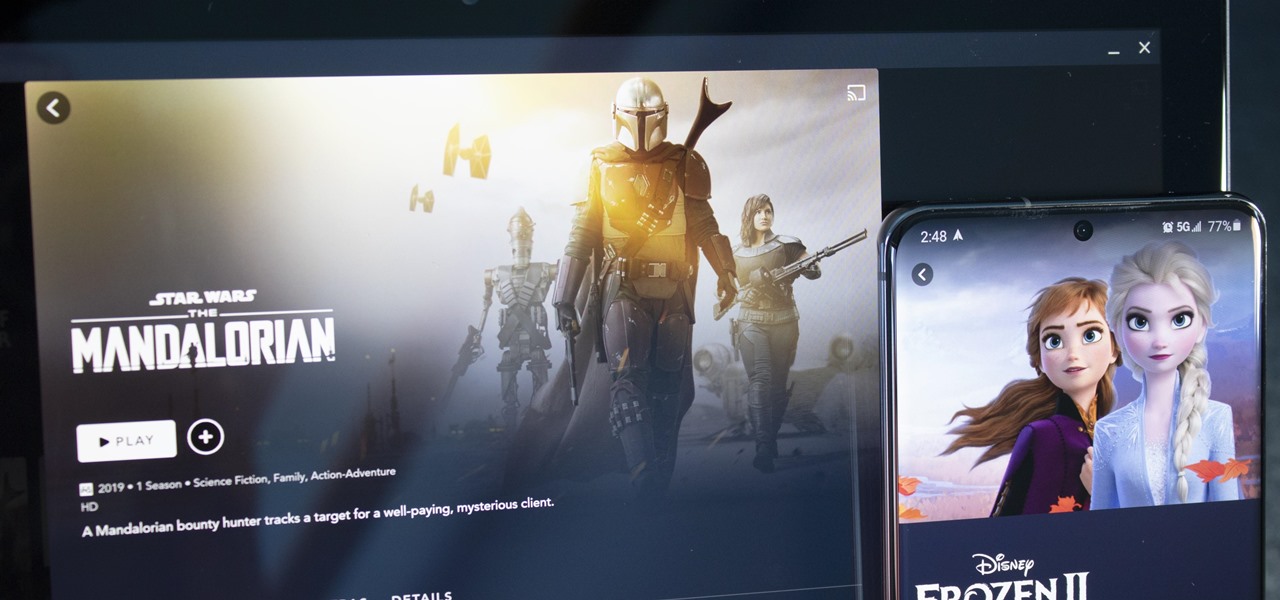
With shows like "The Mandalorian" and movies like "Frozen 2," Disney+ has quickly become a must-have streaming service. However, with Netflix, Amazon Prime Video, and Hulu, adding another subscription-based service can become expensive — but there are ways to trim down the cost.

It's exciting to get that reverse shell or execute a payload, but sometimes these things don't work as expected when there are certain defenses in play. One way to get around that issue is by obfuscating the payload, and encoding it using different techniques will usually bring varying degrees of success. Graffiti can make that happen.

Your S20 has a shortcut for Samsung Pay along the bottom of the home screen. But it tends to get in the way sometimes, especially if you're using the new Android 10 gestures in One UI 2. Besides, if you don't use the feature, you probably don't want that little white line at the bottom of your screen anyway.

Google just released the first version of the next major Android update. Early Android 11 builds will only available as developer previews, so you can't just sign up for the beta program and install the update as an OTA for the first couple months. That said, it's still pretty easy to get.

It's that time again. Snow days, Thanksgiving dinner, holiday presents ... and great Black Friday deals. Starting the Friday after Thanksgiving (or sometimes a few days before), millions of items will go on sale, including your next Android phone.

The mobile augmented reality war for dominance between Apple and its Asia-based rivals is in full effect.

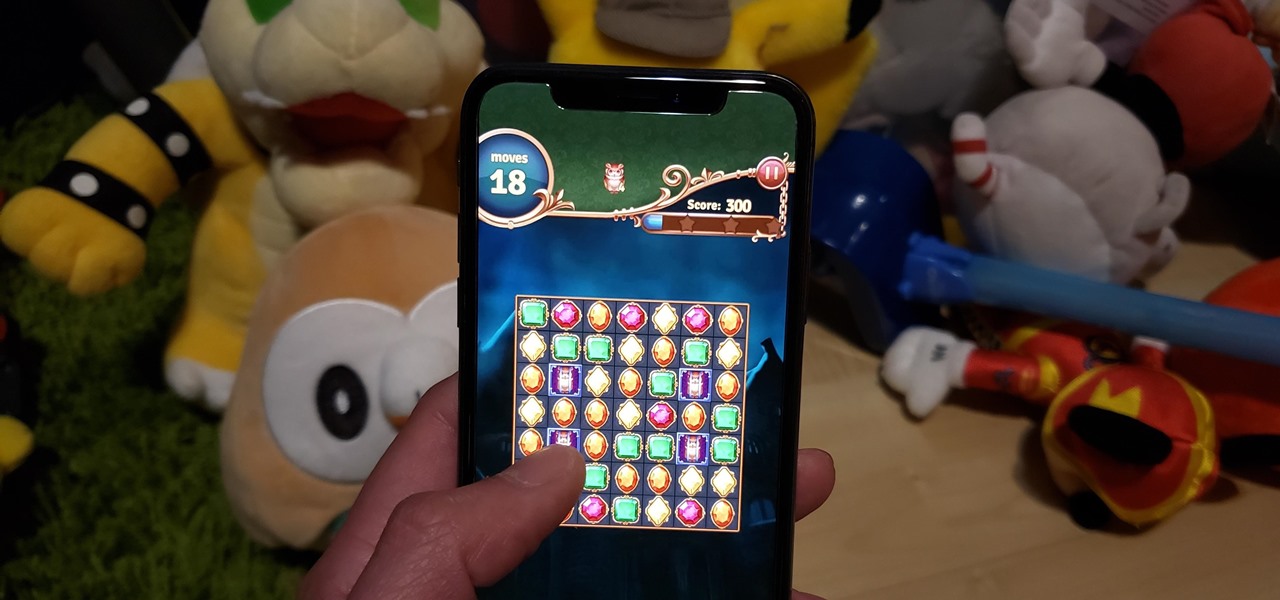
Though not as flashy as other mobile gaming genres like first-person shooters, puzzle games continue to glue players to their phones. Puzzlers are perfect companions while out and about or on a commute, and they're also a great way to stimulate your brain and hand-eye coordination in a fun, relaxing way.

With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. While it won't help find any zero-days, web scanners such as Uniscan will detect common vulnerabilities.

Apple released iOS 12.1.3 public beta 2 for iPhones on Wednesday, Dec. 19. Yes, that's confusing, since there was no first beta for iOS 12.1.3, but it indicates that it's the actual successor to iOS 12.1.2 public beta 1. Apple dropped iOS 12.1.2 unexpectedly to fix major issues but did not include everything in the beta, so we're picking up right where we left off.

It's that time of year again. No, not Thanksgiving. Black Friday. There are a lot deals available this holiday weekend, many of which include flagship Android devices. Whether you are thinking of buying a phone for yourself or looking for a gift for someone else, you can find a little savings to shop smart during the holidays.

In a previous tutorial, we were able to measure horizontal surfaces such as the ground, tables, etc., all using ARKit. With ARKit 1.5, we're now able to measure vertical surfaces like walls!

Have you noticed the many utility ARKit apps on the App Store that allow you to measure the sizes of horizontal planes in the world? Guess what? After this tutorial, you'll be able to do this yourself!

The idea of a dock on any smartphone, be it iPhone or Android, is a fantastic invention. It allows you to stay grounded with a core group of apps that you frequently use. However, sometimes that dock can feel like an obstruction in the face of style — but there's a trick to hiding that translucency behind those core apps at the bottom of your iPhone without jailbreaking.

During our last adventure into the realm of format string exploitation, we learned how we can manipulate format specifiers to rewrite a program's memory with an arbitrary value. While that's all well and good, arbitrary values are boring. We want to gain full control over the values we write, and today we are going to learn how to do just that.

The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnerability allows us to flood a variable with enough input to overwrite the instruction pointer with our own commands.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

While hackers adore the command line, working with the GUI (graphical user interface) of an operating system has some advantages. This is especially true when it comes to post-exploitation. When we can control the mouse and keyboard of a remote computer, we can truly say we have complete control over the device. Today, I'm going to introduce to you the PyAutoGUI module, which does just that, and just how much fun you can have with it!

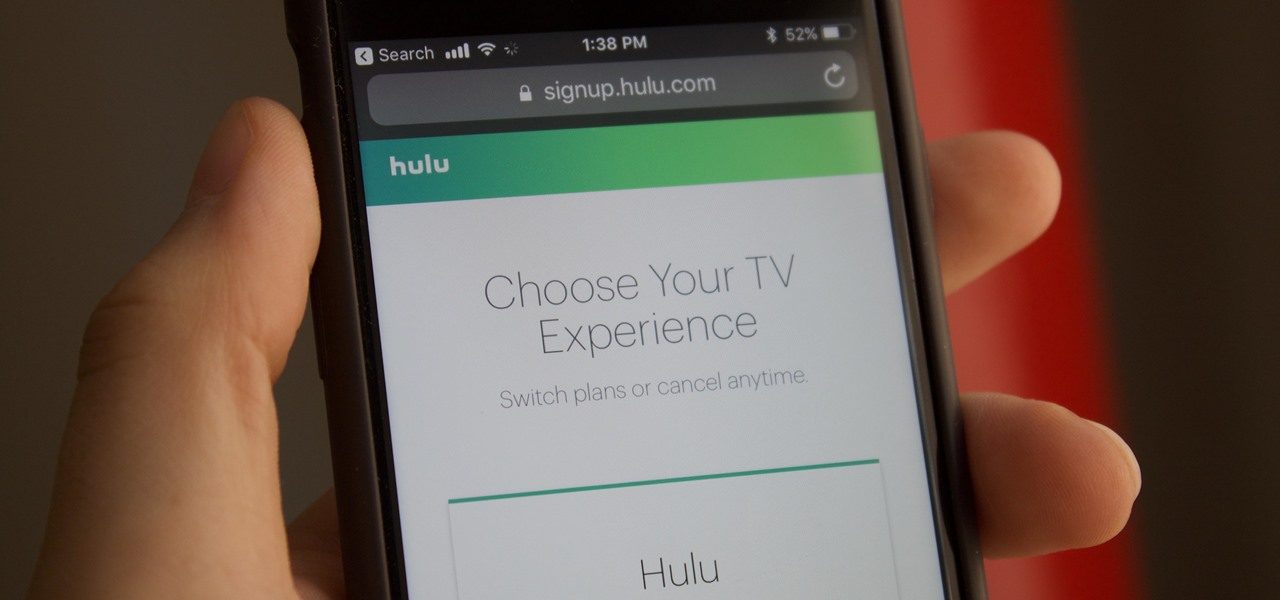
Hulu used to be simple — just a site with all the latest clips and episodes from your favorite shows. Watch some ads, watch some free TV. Easy, right? Not so much anymore. Hulu is no longer free, and on top of that, offers different pricing plans and add-ons.

Earlier this month, Edgybees was the first game developer out of the gate with an augmented reality racing game for DJI drones called Drone Prix AR. Now, as the month closes, they are crossing the finish line with the first gaming app for Epson Moverio BT-300 Drone Edition smartglasses.

Who likes security? I like security. I lock my doors at night, and so should you! That's why it's exciting to me that Samsung has just announced its May security update. It's like getting a brand new, top-of-the-line lock for free, but for your phone.

General Motors Co. (GM) is set to expand their fleet of driverless cars in San Francisco, Detroit, and Scottsdale, according to documents filed by the company.

A new study just out reveals that HIV takes hold in the human body with the help of cells that usually work to heal, not kill.

Each generation of smartphones ushers in a new set of top-of-the-line specs, with processing power, battery size, and display resolution growing by the year. These headlining features get the most press, but there's one unsung hero that has the potential to make the biggest difference when it comes to real-world performance: RAM, or random-access memory.

If we learned anything from Mulan, it's that "the flower that blooms in adversity is the most rare and beautiful of them all." Well, these have been a trying couple of weeks in the US, hence the need for a blooming marshmallow flower.

With the death of Google's Nexus line, the market for phones with top-notch specs at midrange prices is now wide open. OnePlus is apparently ready to fill this void, as they've just announced the OnePlus 3T, an iterative update to their OnePlus 3 flagship only five months after initial release.

Now that Google Assistant is coming to all devices running Android Marshmallow or higher, roughly one out of every three Android users will no longer be able to access the old Google Now interface. The Assistant, which was previously exclusive to Pixel devices, takes over your home button long-press gesture and completely replaces all of the old Google voice search functionality.

I am back this time showing you guys how to theme your kali linux. Being true kali is good for pentesting but when it comes to looks it is lifeless , maybe the kali rolling could be an exception but even that makes you feel bored after a long time . So in this tutorial I am gonaShoe you how to theme up your kali

Greetings fellow students! I'm currently reading a book called "Violent Python: A Cookbook for Hackers, Forensic Analysts, Penetration Testers and Security Engineers"

Now that smartphones have ensured that we're connected to the internet 24/7, online privacy has become more important than ever. With data-mining apps hoping to sell your information for targeted ads, and government agencies only one subpoena away from knowing every detail of your private life, encryption has become our last line of defense.

Hello NullByte, it's mkilic! This time I'm here with the C.H.I.P from NTC. Although it is not too popular, the C.H.I.P is a brand new micro computer. It is very similar to the Raspberry Pi or Beaglebone Black. The key difference with this particular board is its cost and size. The C.H.I.P only costs $9 and measures 2.5 x 1.5 inches. In addition to this, the C.H.I.P has built in 802.11 b/g/n Wifi and Bluetooth 4.0. Considering these great specs, what could a Hacker use this for? Step 1: The In...

Welcome to the Part 2 of the series 'Cryptocurrency'. It has been late because of some errors, where all I typed was lost.

Welcome, in this tutorial we shall we looking at creating a safe(r) way to back up your important files. The contents we will be covering are as follows;

It's truly amazing how far smartphone camera hardware has come in such a short period of time. It took roughly 5 years to advance the image processing capabilities from a pixelated mess to the crisp and clear photos we can take today. This reaches well beyond the megapixel spec race, since camera modules these days sport vastly improved optics, wider aperture, and even larger pixel sensors that capture more light.

So, you want your terminal to be customized with awesome script every time you fire it up, huh?! Well, look no further because I am here to answer this calling!

Developing GUI apps in python is really cool. I ask those who understand the language to help convert some of the command-line or console programs or apps ( I mean programs that are useful to a hacker ) to GUI. I know GUI makes us lazy and not wanna learn but we should all know its fast. Today's tutorial is on p2p chat app I developed last week and decided to share it with the community since its kinda cool.