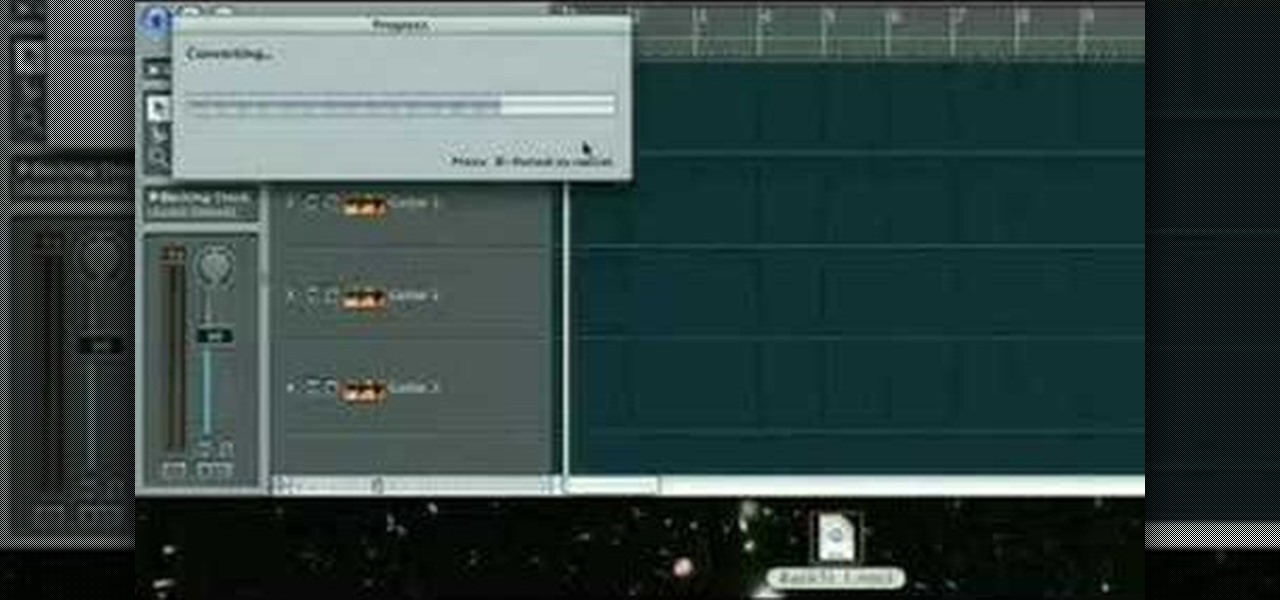
How To: Record over a backing track in Logic
Practice your soloing skills and record melodic lead lines over your favorite song or backing track by importing pre-recorded tracks into Logic.


Practice your soloing skills and record melodic lead lines over your favorite song or backing track by importing pre-recorded tracks into Logic.

Develop your technique and learn how to get your lead lines to come through clean and strong using rockin' Minor Pentatonic fingering exercises.

Learn some basic plumbing skills. Watch this video to learn how to glue PVC joint pipes together to form your drain lines.

This video shows you the proper technique to draining the engine fluids from the radiator and connected hoses before removing the engine for disassembly. Explains the process for using your specific engine repair manual to label all of the wiring, vacuum lines and hoses so that installation later will be smooth.

This video demonstrates how to perform the overturned back sacada. This move is one that the follower does and the key points for success are to focus on the spiral energy of the step and stretch the step. The leader should pay close attention to the line taken.

With any drawing tool you would expect to be able to create lines with arrowheads. In this tutorial Terry White will not only show you how to do it in Illustrator, but he will also show you how to give your arrows a little flare by reshaping them with the Pencil Tool. That's right, he's found a great use for the tool that no one likes to use.

A very important thing to keep in mind when you're creating images from scratch or even putting things into existing images is the concept of perspective. Bert goes back to basics to teach this concept, starting with a horizon line and adherence to the rules of mother nature.

You can learn how to create an impossible shape out of paper. All you need is a piece of paper and scissors. First, you cut along the 2/3 lines of the paper. Then you flip one half of the paper over, and you have created an impossible shape.

You can practice skating backwards. There is a drill you can do. Set up five to ten sticks in a straight line and begin to c cut thrust down the length of the ice.
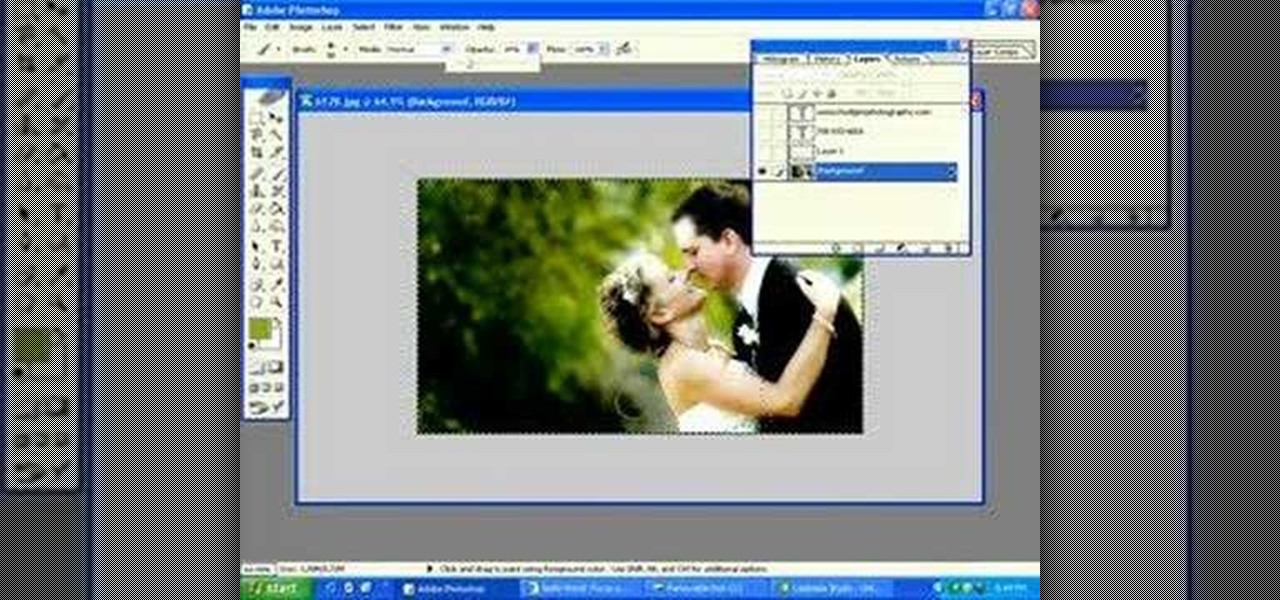
Learn how to easily create business cards in Photoshop.

There's a seemingly endless list of downsides that come with the coronavirus pandemic — ranging from canceled trips abroad and sunny days spent inside to limited communication with friends and family. But one of the undeniable upsides is that there's simply never been a better time to start your own online business since most people will be working from home for the foreseeable future.

Data analytics is one of the hottest fields around. With so much data at our fingertips, top companies are seeking experts to put all of this information to real-world use.

Augmented reality plays a key role in the evolution of adjacent technologies, such as 5G connectivity and brain-control interfaces (BCI), and the business news of the week serves up proof points for both examples.

Search engines index websites on the web so you can find them more efficiently, and the same is true for internet-connected devices. Shodan indexes devices like webcams, printers, and even industrial controls into one easy-to-search database, giving hackers access to vulnerable devices online across the globe. And you can search its database via its website or command-line library.

The Google Phone app is one of the best dialers for Android today, especially with all of the unique and exciting features it brings to the table. Unfortunately, without owning a Pixel phone, you are unable to officially download the app, making a modified version your only option. However, this version of Google Phone is missing a few key features, such as spam protection and business search.

Signaling a new direction forward for the company, Magic Leap shook up its executive suite by re-assigning to top leaders to new advisory roles. Meanwhile, a new startup backed by Hollywood executives, tech venture firms, and notable angel investors plans to bring new life to AR for marketing entertainment properties.

This week, inside sources divulged details of how Apple nearly acquired Leap Motion, twice. Otherwise, companies offering or working on augmented reality technology had more successes than failures to talk about.

A week after the L.E.A.P. Conference, our cup of Magic Leap news continues to floweth over, with the company's content chief giving us some insight into the company's strategy, and Twilio sharing what its virtual chat app looks like.

In what's becoming something of a regular occurrence, Magic Leap has yet another internal, unforced error on its hands. Thankfully, this time it's not about legal skirmishes or theft, but a rather unusual break from company protocol that has been quickly swept under the rug.

The drag on your fishing reel is what keeps big fish from breaking your line. Properly setting the drag could prevent you from losing that trophy fish.

Welcome back, my tenderfoot hackers! As you should know from before, Snort is the most widely deployed intrusion detection system (IDS) in the world, and every hacker and IT security professional should be familiar with it. Hackers need to understand it for evasion, and IT security professionals to prevent intrusions. So a basic understanding of this ubiquitous IDS is crucial.

Hello fellow training hackers. I do not know if many of you are familiar with ruby, but since it is a useful scripting language, that hasn't been covered too much here on Null Byte, I thought why not do some How-tos about it now and then.

See how to make homemade "ice" candles out of taper candles (or wax flakes). Cut up the taper candles, heat them until melted, then pour into a container lined with ice (chipped ice, not cubes) with the wick dangling in from above. The ice will create an interesting design in the candle.

Step 1: Draw Horizontal Lines for Uniform Size Overall Hi, This is a tutorial video to write your name in Graffiti.

Easy Square Knot Bracelet with beaded lines. To make this bracelet you only need to know how to make a square knot. This is a good bracelet for beginners in macrame.

Welcome back, my greenhorn hackers!
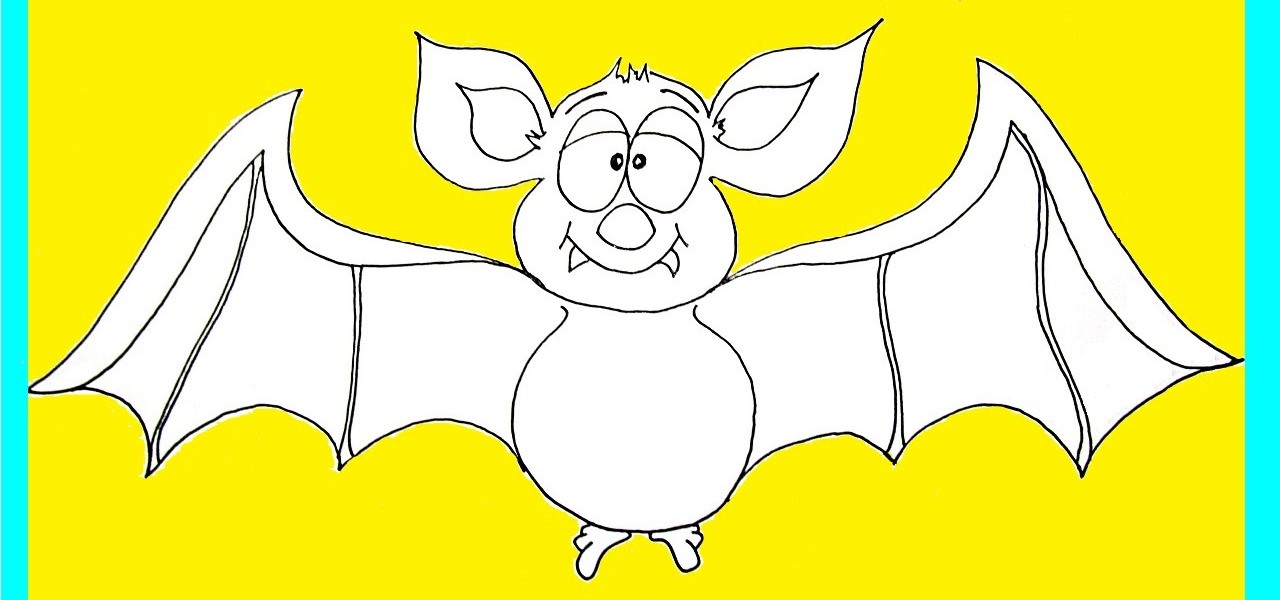
If you're a beginner artist, it's best to start off with simple line drawings at first, like this one! In the following video, I show you how to draw a slightly sleepy-looking cartoon bat. He's pretty easy to create - give it a go and see for yourself! :-)

This is a simple drawing tutorial, in which I show you a super easy way to draw a cute cartoon owl! It's a basic line drawing, so it's perfect for beginner artists - enjoy! :-)

How to make Criss-cross lines, Friendship Bracelet Tutorial. This Bracelet looks interesting from both sides. Not hard to make and suitable for beginners.

This bracelet is easy to make and it looks really interesting. To make this bracelet you only need to know one simple knot..

Today we show you how to use a derma roller. Derma Rollers are good for acne scars and for fine lines. Using a derma roller is So Easy a Guy Could Do It!

Welcome back, my fledgling hackers! The database is the hacker's "pot-of-gold," as it contains information that is very valuable to both the business and the hacker. In this, the second of my series on hacking databases, we're on the "hunt" for Microsoft's SQL Server. Although far from the most commonly used database (Oracle hold's that title), Microsoft's SQL Server is very often found in small-to-medium sized businesses. Even a few big businesses use it.

Henry shows you how to install a 3 tab asphalt shingle roof in this video. This video covers everything from the type of roofing felt to use, making the starter strips, layout with chalk lines right through to making and installing the ridge caps.

Installing trusses requires some important steps to ensure they are centered and lined up correctly. Henry shows you how to do this and make sure your trusses are spaced correctly and level.

This Professional Website design Tutorial will show you how to place text on a curve using the line tool. However you can put text on the outline of shapes and other objects.

Video: . Step 1: The Face Shape

While we admit the Wobble isn't the most sophisticated name for a dance, in practice its actually very sexy and infinitely bootylicious. If you've ever seen a Beyonce music video - or really any R&B/hip hop video with girls in booty shorts and low-cut tank tops - then you've witnessed the glory of the Wobble. Part Hustle and part gyrating, this dance will not only make you look like a goddess, but will also help sculpt your midsection and lower body into tightened perfection.
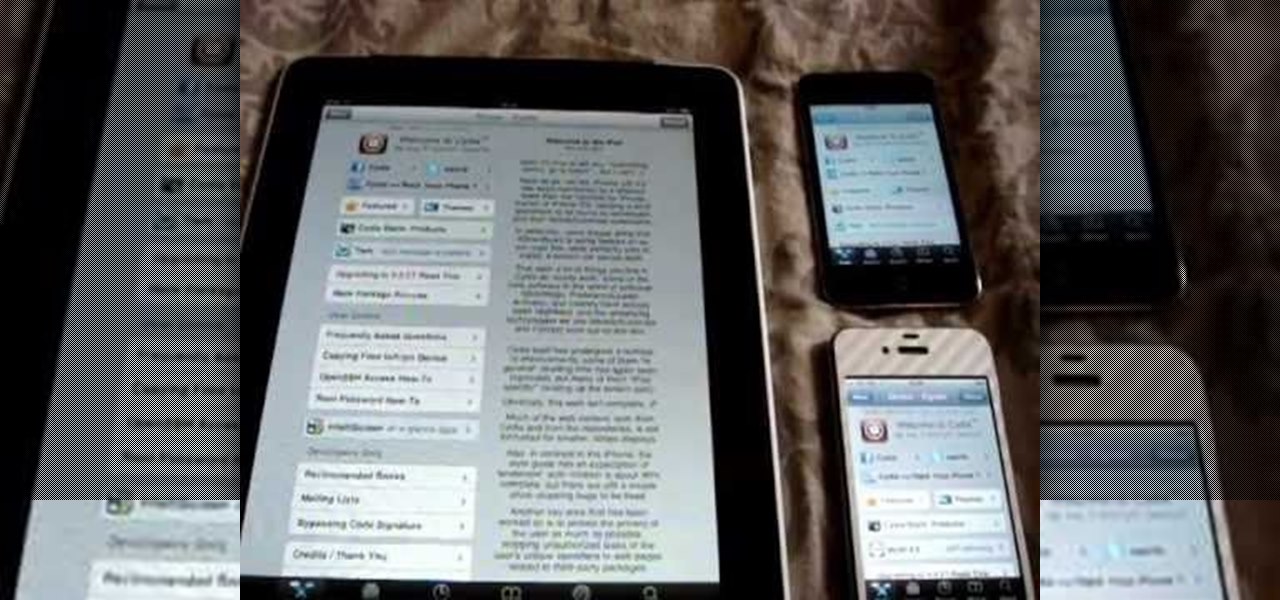
If your iPad, iPhone 4 or iPod Touch is already on a tethered jailbreak, this is the tutorial on the new Redsn0w release for all you experienced users. An untethered jailbreak is a type of jailbreak where the device does not require rebooting with a connection to an external jailbreak tool to power up the iDevice. Jailbreaking allows users to get root access to the command line of the operating system, to download otherwise unaccessible extensions and themes, or install non-Apple operating sy...
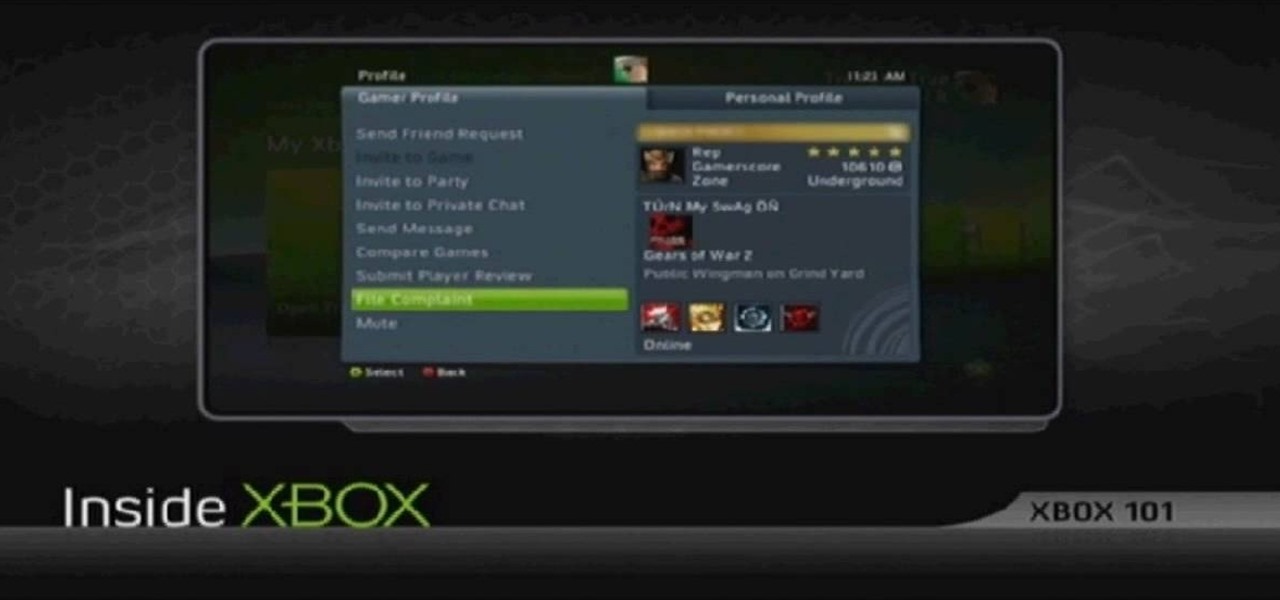
In this tutorial, we learn how to file a player complaint with Microsoft (Xbox 101). There is no tolerance for file complaints, cheating, rude remarks, and anything of that nature. The file complaint feature should only be used if someone really violated the code of conduct. When you feel someone has crossed the line, you will tap the guide button, then select friends. From here, choose the person from the group and identify the complaint. View the profile of that person, then you will be fin...

In this tutorial, we learn how to draw different types of anime/manga hair. Different types of hair can completely change the look of a character. For example, if you are going to draw hair on a girl manga character, you will want to make it curly and long. Use long lines with bangs to make this hair look more realistic. For guy manga characters, you will want to add a lot of triangles to the hair to make it look like spikes all over and give him short bangs as well. Give each of these your u...