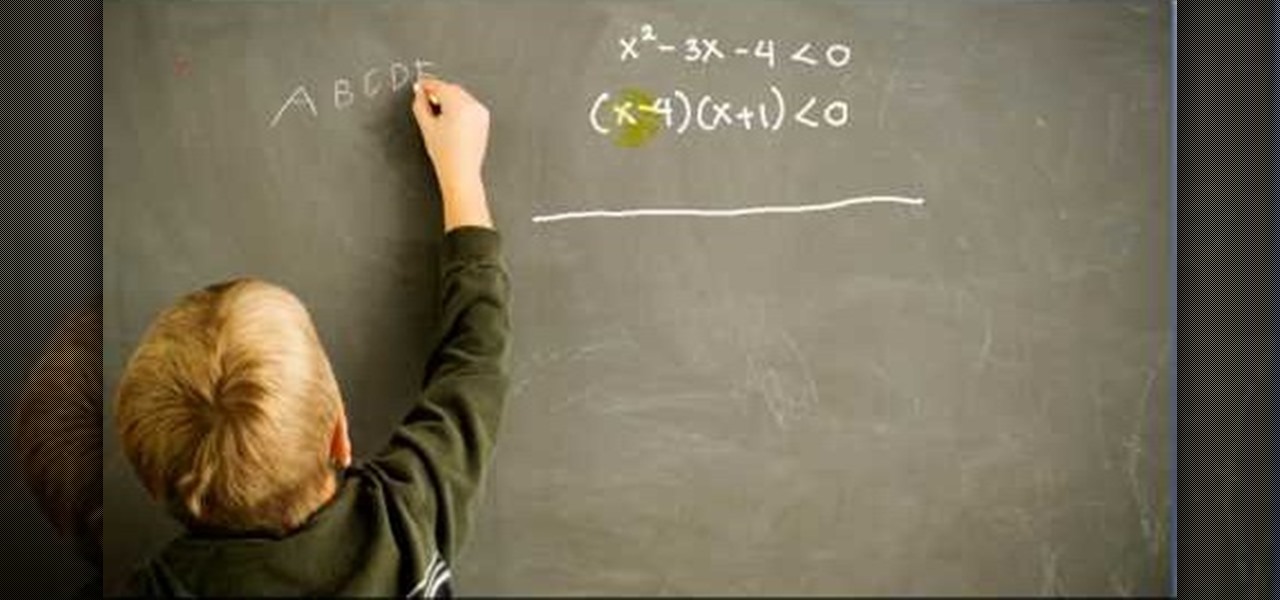This makeup tip is perfect for a glittery eyeshadow for New Year's as inspired by the cover of Sephora's magazine. First, apply a semi-dark gray eyeshadow along your eyelid and on the outside corners of your eyes. Using a fluffier brush, apply a lighter white-silver eyeshadow and then use dark black eyeliner along the line of your eye. Use silver glitter along your eyelids in a few layers and black layer on the outside of your eyelids for that perfect festive New Year's look.

This tutorial teaches you how to do the same nail design as Ke$ha from her video "Tik Tok" had her nails done. First you apply a base polish to protect your nails. Apply a gold polish all over the nail, about three solid coats and then let them dry. Paint on a rich wine color to the corner of each nail end. Use a dotting tool and clean polish to pick up the rhinestones. Apply a little bit of nail glue on the seam of the two colors to help the Rhine stones stay put. Take a fine tip brush with ...

For people who would like to learn how to make a professional tattoo, this is the tutorial to watch. For making a basic arm tattoo, the subject should be seated upright in a military position. You should apply some alcohol and then some antiseptic to the area to disinfect the area and place the stencil over the area. It is suggested that the subject shave his or her arm in order to get the best effects. The tattoo stencil should be placed over the center line of the arm and align it properly,...
Creating a motion tween in Flash CS4, which is moving one image from one position to another position.

Get that very "right now" green smoky eye with some help from the professionals at Smashbox Cosmetics. By starting with cream liner Midnight Green and applying little smudges along the line, go back to smudge with your brush to create a smoky effect. Stand our this fall with vivid color and this soft, not-so-innocent makeup look.
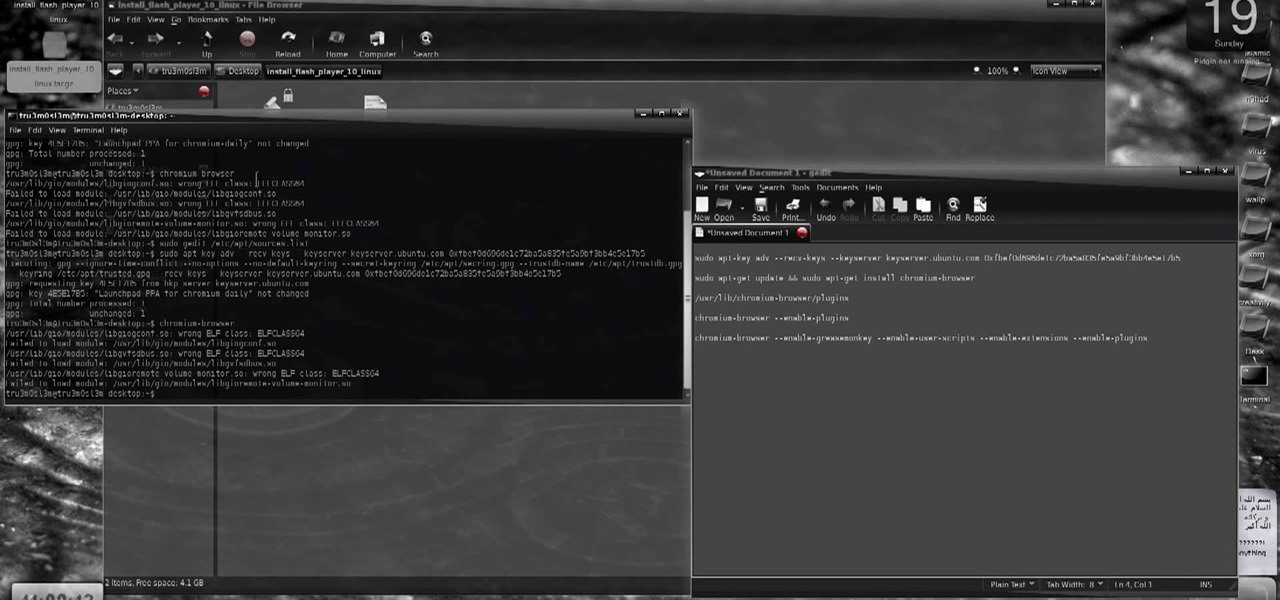
New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install and enable Flash for Chromium on Ubuntu Linux.

Calculus can be a bit tricky, but don't worry, Watch Math is here to help you out. Watch this math video lesson to learn how to solve quadratic inequalities in calculus. There's no better way to learn mathematics than from an advanced mathematician, like this PhD.

When I was a kid, the 4th of July was my favorite holiday for one simple reason...the joy of making things go BOOM! Somewhere along the line that fun was taken away by politicians. It's time to put the fun back in celebrating freedom. From your friends at America's favorite podcast, Anarchy-X.

See how to avoid rejection on the singles scene! When it comes to putting the moves on someone, no one can make themselves rejection-proof. But you can increase the odds of a good outcome.

Want to see whether your PC is being accessed by hackers? Netstat (network statistics) is a command-line tool that displays network connections (both incoming and outgoing), routing tables, and a number of network interface statistics. It is available on Unix, Unix-like, and Windows NT-based operating systems. This video tutorial presents a basic introduction to working with the netstat tool. Determine whether you've been hacked with this how-to.

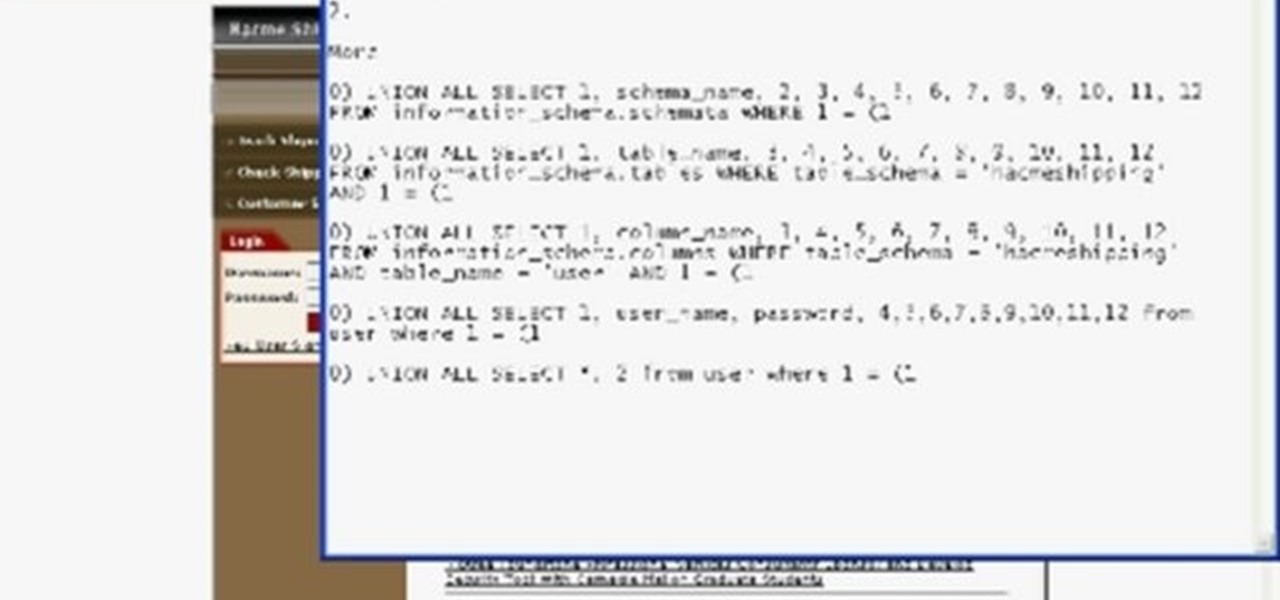
Foundstone Hacme Shipping is a web-based shipping application developed by Foundstone to demonstrate common web application hacking techniques such as SQL Injection, Cross Site Scripting and Escalation of Privileges as well as Authentication and Authorization flaws and how they are manifested in the code. Written in ColdFusion MX 7 using the Model-Glue framework and a MySQL database, the application emulates the on-line services provided by major shipping companies. This video will get you st...

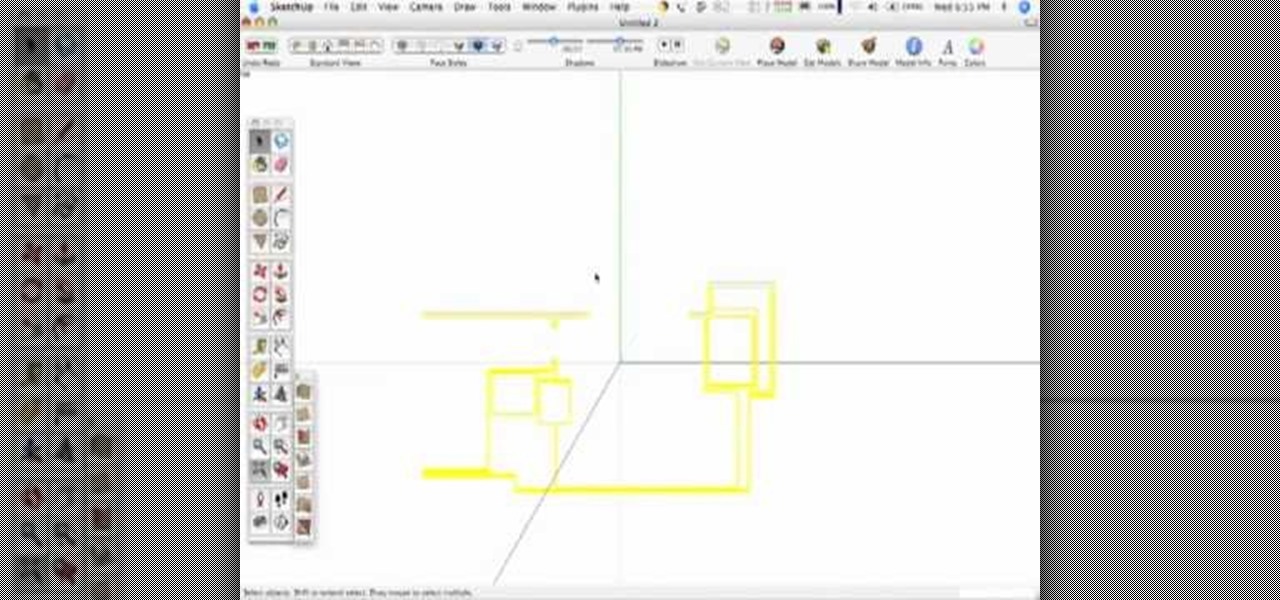
SketchUp 5 and up has a Sandbox. But there are a few rules to know before you're allowed to play. In this episode of The SketchUp Show, Alex leads you in creating a landscape from scratch, and a second way to model terrain from existing contour lines using the sandbox tools. Landscapers will love learning to use the sandbox tools in this episode!

The Professor of Silliness returns with some paper. Watch this instructional video to make a tall tree out of newspaper. You need an old newspaper, masking tape, and scissors. Simply lay out the newspaper pages from end to end and tape them together. Then roll it up at a diagonal, starting from one corner, and pack i it into a compact tube. Use tape to keep the tub intact Use the scissors to cut vertical lines half way down the newspaper tube. Pull out the inner most layer and turn your recyc...

In this human anatomy video tutorial, you learn how to dissect a human cadaver to get a better look at the nasal cavity and sinuses. You'll see the paranasal, which is alongside or near the nose, and the paranasal sinuses are the mucosa-lined air cavities in the bones of the skull, communicating with the nasal cavity.

When we think about operating systems, we tend to view them from the perspective of a user. After all, most of us have spent a substantial amount of time on our computers, and so we've become more than acquainted with the ins and outs of whatever system we have running on our personal device. But there is one operating system that, while being less commonly used on the user side, is behind a great deal of design and business technology: Linux.

It feels like every few months, some new feature is discovered in the Pixel's Camera app. By taking advantage of machine learning and the high-quality camera, Google continues to add hidden functions that improve your life even if they're a little niche.

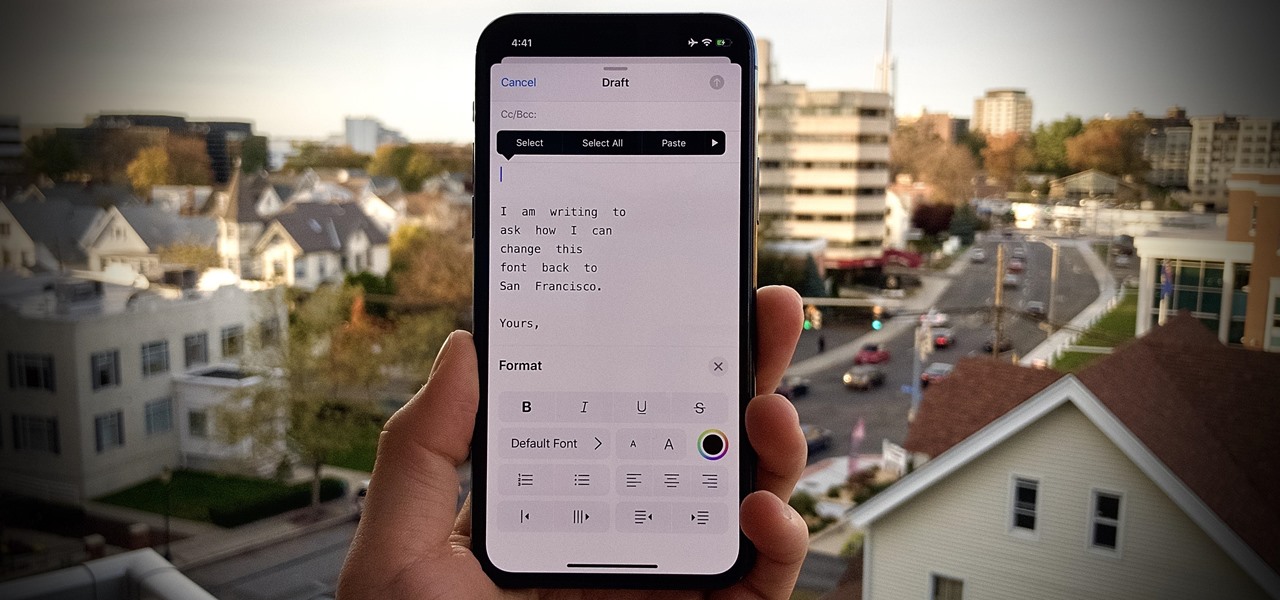
One of iOS 13's coolest features is the ability to download, install, and choose fonts in select apps like Pages and Mail. However, you might notice an issue when writing an email with a custom typeface: there's no option to return to the default font. What gives?

While Gucci is among the most recognizable brands in fashion, you would be excused for not realizing that the company makes sneakers as well.

This week, Next Reality published profiles on the leaders in augmented reality hardware industry, with Magic Leap CEO Rony Abovitz topping the list. So, it should be no surprise that two app makers want to align themselves with Magic Leap's flagship product.

While we've seen Snapchat apply sky segmentation to AR content, the makers of the Blue Sky Paint app have applied similar capabilities to create and share airborne art.

Project Fi, Google's MVNO, is running a new promotion on the latest and greatest from LG. From July 16 until the 29th, whenever you order and activate the LG G7 ThinQ or LG V35 ThinQ, you will receive a $300 service credit. When you do the numbers, that equals a minimum of three free months of service.

Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than others, and a little Python could be used to brute-force any weak hashes to get the passwords they were created from.

While everyone was marveling at the latest drama over at Magic Leap involving employees last week, a major rumor listed in one of the reports, related to the company's flagship device, was mostly overlooked.

To promote Star Wars: The Last Jedi, Disney and Lucasfilm released virtual porgs into the wilds of Snapchat via a Sponsored Lens on Sunday.

There aren't many people who will believe that a prosthetic zipper face or gunshot wound to the eye (disgusting as they are) are real, but greyscale from Game of Thrones? That'll really unsettle people for awhile because it totally looks like an actual, honest-to-God infection that someone in 2017 could conceivably have. Which makes it very effective come Halloween, whether it's for a full-on Princess Shireen, Jorah Mormont, or Stone Man costume, or to just infect a completely different chara...

The first wave of iPhone X preorders, the ones with a delivery date of Nov. 3, sold out in ten minutes. You can still preorder one and skip the lines next week at Apple Stores across the country, but if you want that bezel-less beauty in your hands ASAP, brick and mortar might be the way to go.

There is an Indian story called the Legend of Paal Paysam, and while it doesn't seem like it at first, it has a lot to say about what motivated Paul Travers in the augmented reality space.

You can pinch yourself, but you're not dreaming. Sprint is actually offering a year of (mostly) free, unlimited service for anyone who switches to the carrier. The only stipulation is that you must bring your phone with you, and it has to be one of the 27 eligible devices.

Usually, the mucus lining of the female genital tract presents a barrier that helps prevent infections. But, somehow, the bacteria that causes gonorrhea gets around and through that barrier to invade the female genital tract.

Google's former Self-Driving Car project, now graduated from Alphabet's X division as Waymo, has found a collaborator and potential new partner in Honda. This is an interesting turn of events given traditional automakers' reluctance to work with driverless-car startups over the years.

As most of you know, I am a strong advocate for using Linux for hacking. In fact, I would go so far as to say that you cannot be a hacker without knowing Linux well. I laid out various reasons for this in my "Why Every Hacker Should Know & Use Linux" article, and I even have a lengthy, continuing series on Linux Basics to help those new to Linux master it.

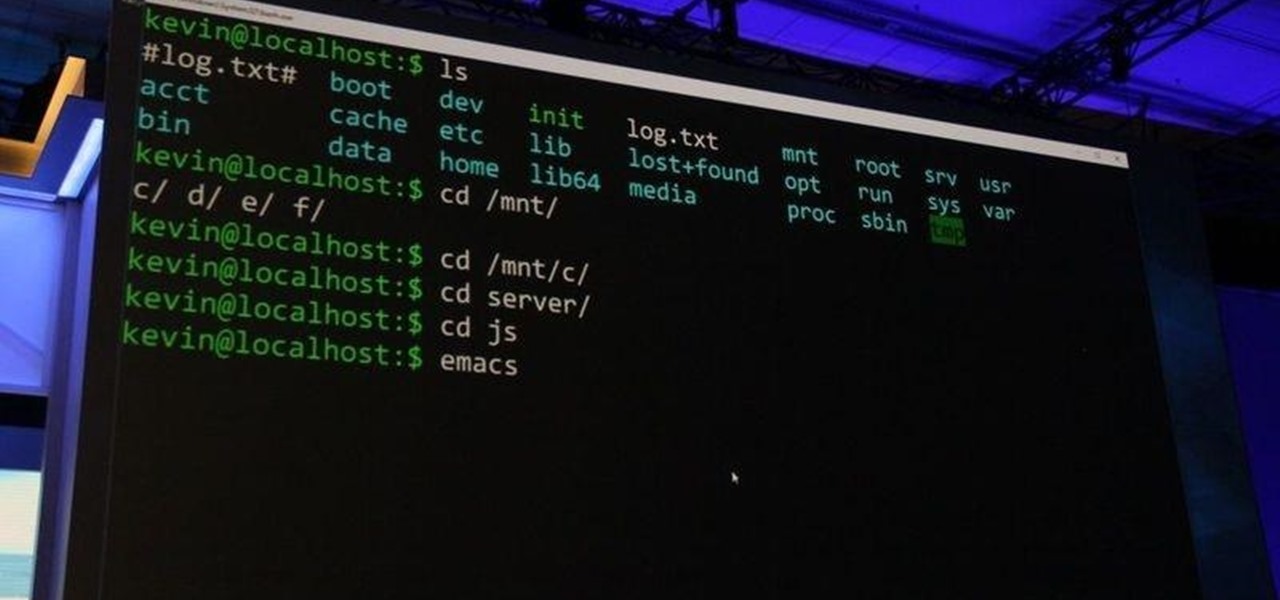
Hello friends! This tutorial will teach you how to build a local pentesting lab on your Linux machine which will enable you to easily install common web applications so you can practice locating and exploiting their known vulnerabilities (or discover new ones!). In particular, this is an excellent way to learn how to hack Wordpress, Joomla, and Dupral plus many more!

In many programs on Linux, you'll come across programs which allow you to specify additional arguments instead of just simply running the program by itself. If you've used the Kali distribution, I'm more than certain you'll have come across these with the command line tools, else if you have been following these tutorials, we have already come across three tools which also use the same technique, i.e. gcc, gdb and wc. How do we do this with C? Let's find out.

The Cheshire Cat isn't like other famous cartoon cats: he's brilliantly purple and hot pink, ever smiling and entirely unnatural. However, he makes for a perfect Halloween costume, with his bright, neon appearance and mysterious nature.

As Android's de facto virtual assistant, Google Now lets us speak directly to our phones in plain English to answer our questions and perform many basic tasks. With the app open, just say "Okay Google," then wait for the beep, and ask almost any question.

With Android 5.0, Google introduced a new "Heads Up" notification system for incoming calls and messages. While the new incoming call interface seems to be a rousing success, the rest of the Heads Up system has been met with much less enthusiasm from users.

Want to get even this Halloween? Want to scare somebody with nothing but a few lines of code? Here's how it can be done...

The video for Robin Thicke's "Blurred Lines" got its fair share of attention due to the three topless models who star in it. In the second version, they're covered up, but just barely. Both the song lyrics and the lack of clothing sparked plenty of debate, controversy and even parodies.

"Ahoy-hoy." If telephone titan Alexander Graham Bell had his way, we'd all be answering phones like Mr. Burns. Thankfully, frienemy Thomas Edison had enough sense to realize we weren't always on the briny. He preferred "hello" as our standard telephone greeting, which he is credited with coining in 1877. Fellow American pioneer Davy Crockett actually used it as a greeting first in 1833 (as compared to an exclamation)—but in print, not over the phone.

If you're like me, the words 'monostable circuit' mean nothing to you. Until just recently, I had no idea what a monostable circuit did, or why anyone would ever need to use one.