Apple released iOS 12.1.3 public beta 2 for iPhones on Wednesday, Dec. 19. Yes, that's confusing, since there was no first beta for iOS 12.1.3, but it indicates that it's the actual successor to iOS 12.1.2 public beta 1. Apple dropped iOS 12.1.2 unexpectedly to fix major issues but did not include everything in the beta, so we're picking up right where we left off.

While our time with the Protostar VM from Exploit Exercises was lovely, we must move on to bigger things and harder challenges. Exploit Exercises' Fusion VM offers some more challenging binary exploitation levels for us to tackle. The biggest change is that these levels are all network services, which means we'll write our first remote exploits.

The idea of a dock on any smartphone, be it iPhone or Android, is a fantastic invention. It allows you to stay grounded with a core group of apps that you frequently use. However, sometimes that dock can feel like an obstruction in the face of style — but there's a trick to hiding that translucency behind those core apps at the bottom of your iPhone without jailbreaking.

During our last adventure into the realm of format string exploitation, we learned how we can manipulate format specifiers to rewrite a program's memory with an arbitrary value. While that's all well and good, arbitrary values are boring. We want to gain full control over the values we write, and today we are going to learn how to do just that.

The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnerability allows us to flood a variable with enough input to overwrite the instruction pointer with our own commands.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

While hackers adore the command line, working with the GUI (graphical user interface) of an operating system has some advantages. This is especially true when it comes to post-exploitation. When we can control the mouse and keyboard of a remote computer, we can truly say we have complete control over the device. Today, I'm going to introduce to you the PyAutoGUI module, which does just that, and just how much fun you can have with it!

Earlier this month, Edgybees was the first game developer out of the gate with an augmented reality racing game for DJI drones called Drone Prix AR. Now, as the month closes, they are crossing the finish line with the first gaming app for Epson Moverio BT-300 Drone Edition smartglasses.

Who likes security? I like security. I lock my doors at night, and so should you! That's why it's exciting to me that Samsung has just announced its May security update. It's like getting a brand new, top-of-the-line lock for free, but for your phone.

A new study just out reveals that HIV takes hold in the human body with the help of cells that usually work to heal, not kill.

Each generation of smartphones ushers in a new set of top-of-the-line specs, with processing power, battery size, and display resolution growing by the year. These headlining features get the most press, but there's one unsung hero that has the potential to make the biggest difference when it comes to real-world performance: RAM, or random-access memory.

If we learned anything from Mulan, it's that "the flower that blooms in adversity is the most rare and beautiful of them all." Well, these have been a trying couple of weeks in the US, hence the need for a blooming marshmallow flower.

With the death of Google's Nexus line, the market for phones with top-notch specs at midrange prices is now wide open. OnePlus is apparently ready to fill this void, as they've just announced the OnePlus 3T, an iterative update to their OnePlus 3 flagship only five months after initial release.

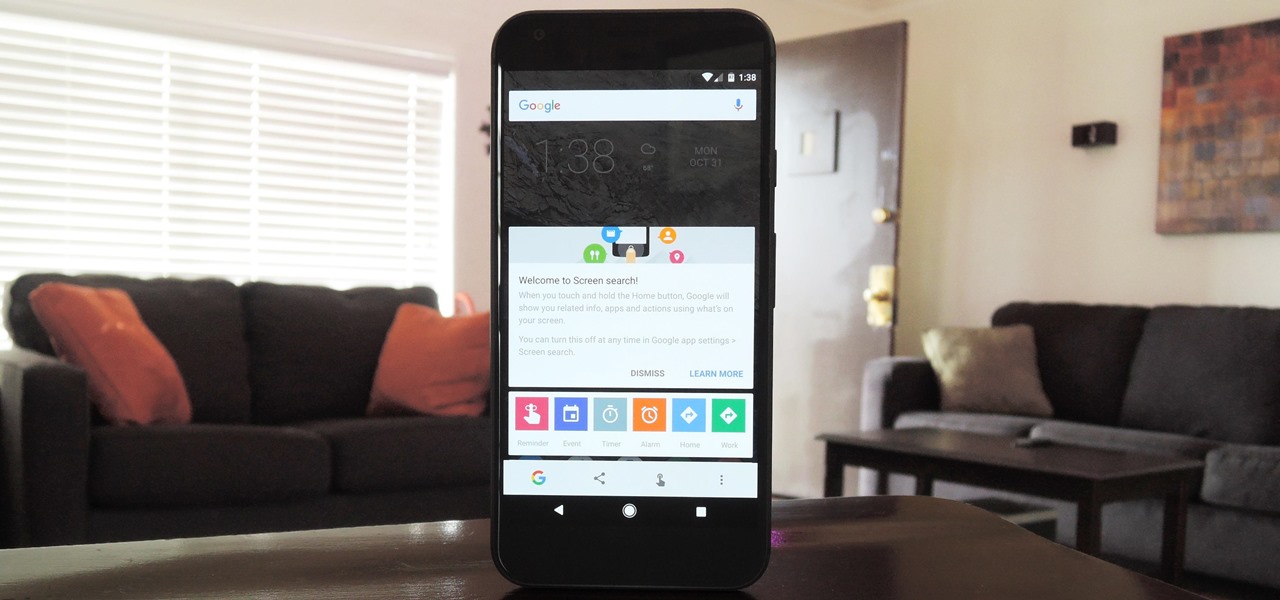
Now that Google Assistant is coming to all devices running Android Marshmallow or higher, roughly one out of every three Android users will no longer be able to access the old Google Now interface. The Assistant, which was previously exclusive to Pixel devices, takes over your home button long-press gesture and completely replaces all of the old Google voice search functionality.

I am back this time showing you guys how to theme your kali linux. Being true kali is good for pentesting but when it comes to looks it is lifeless , maybe the kali rolling could be an exception but even that makes you feel bored after a long time . So in this tutorial I am gonaShoe you how to theme up your kali

Greetings fellow students! I'm currently reading a book called "Violent Python: A Cookbook for Hackers, Forensic Analysts, Penetration Testers and Security Engineers"

Now that smartphones have ensured that we're connected to the internet 24/7, online privacy has become more important than ever. With data-mining apps hoping to sell your information for targeted ads, and government agencies only one subpoena away from knowing every detail of your private life, encryption has become our last line of defense.

Hello NullByte, it's mkilic! This time I'm here with the C.H.I.P from NTC. Although it is not too popular, the C.H.I.P is a brand new micro computer. It is very similar to the Raspberry Pi or Beaglebone Black. The key difference with this particular board is its cost and size. The C.H.I.P only costs $9 and measures 2.5 x 1.5 inches. In addition to this, the C.H.I.P has built in 802.11 b/g/n Wifi and Bluetooth 4.0. Considering these great specs, what could a Hacker use this for? Step 1: The In...

Welcome, in this tutorial we shall we looking at creating a safe(r) way to back up your important files. The contents we will be covering are as follows;

It's truly amazing how far smartphone camera hardware has come in such a short period of time. It took roughly 5 years to advance the image processing capabilities from a pixelated mess to the crisp and clear photos we can take today. This reaches well beyond the megapixel spec race, since camera modules these days sport vastly improved optics, wider aperture, and even larger pixel sensors that capture more light.

So, you want your terminal to be customized with awesome script every time you fire it up, huh?! Well, look no further because I am here to answer this calling!

Developing GUI apps in python is really cool. I ask those who understand the language to help convert some of the command-line or console programs or apps ( I mean programs that are useful to a hacker ) to GUI. I know GUI makes us lazy and not wanna learn but we should all know its fast. Today's tutorial is on p2p chat app I developed last week and decided to share it with the community since its kinda cool.

Firstly let me start by giving credit to Lucid for their guide on Evilzone which inspired this idea, as well as the recent talk of anonymity on here.

First of all, I hope the title makes sense. :D Well, this is basically creating a program that can help with dictionary attacks. Generate possible passwords. It pretty much lies in you knowing the person you want to hack.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

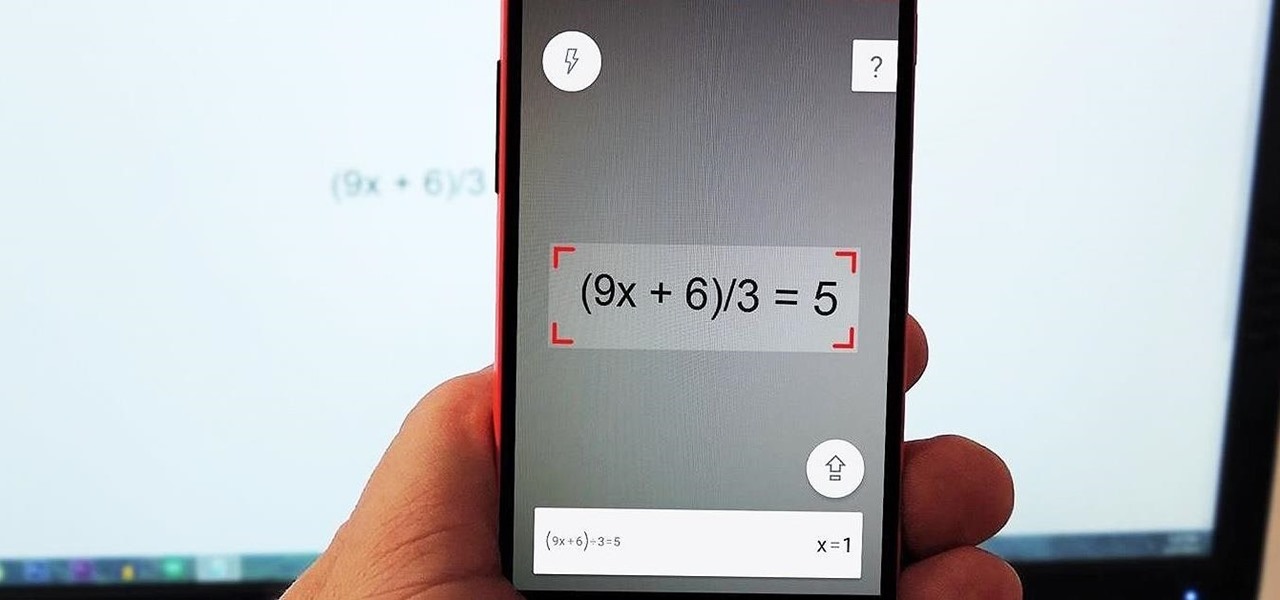
I'm not a fan of this practice, but many developers release their wares on iOS before eventually porting their apps to Android. This was the case for PhotoMath, a popular and very useful app that can solve math problems with your smartphone's camera.

Welcome back, my novice hackers! This is the third installment of my Python scripting series. If you haven't read the previous two articles, take some time now to go back and read Part 1 and Part 2 before you proceed here.

Welcome back, my fledgling hackers! In an earlier tutorial, I introduced you to probably the most popular scripting language for hackers, Python. To become a professional hacker, you need to have some scripting skills and Python is a good choice if you want to master just one. In this latest guide, I will expand your background in Python and offer you a tidbit of Python code to whet your appetite for all of the hacking to come.

Now that it's easier than ever to take pictures using a digital camera or smartphone, more people should brush up on basic composition tips for taking a good photograph.

If you thought the price of Photoshop was outrageous, you'll be thrilled to know that Adobe has found yet another way to grab your hard-earned dollars—but this time, it isn't software. Ready to take your drawings to the next level, the company has created the Adobe Ink and Slide. Together, these products will make drawing on an iPad a whole lot easier.

On June 12th, Samsung introduced their newest tablet series, the Galaxy Tab S line. These are the thinnest and lightest in Samsung's history, measuring in at only 6.6mm in width and weighing 465g (10.5-inch) and 294g (8.4-inch). Additionally, both have a WQXGA (2560x1600) Super AMOLED display giving these screens both richer and crisper colors.

LG's arsenal of screen-off and screen-on tap gestures recently expanded into lock screen territory. Dubbed "Knock Code", this feature allows owners of various LG phones, like the G2 and upcoming G3 to unlock their phone with a series of taps on the screen. The most impressive part is that the screen doesn't even need to be on!

Volume markings on large pots and mixing bowls make life so much easier. They cut out the step of measuring and save you the trouble of washing measuring cups. However, there aren't many containers out there that actually have volume markers in them.

Welcome back, my aspiring hackers! Domain Name System (DNS) is one of those things we seldom think about unless it doesn't work. Then, it can be very frustrating when we attempt to navigate to a website and we get that frustrating error message.

Here are instructions to make origami bat. You will need 383 black, 47 brown, 3 white and 2 red triangles. In the video below you'll see a map.

Just starting to use makeup? Or never found the perfect foundation for your skin tone. We will show you how to pick the right foundation for you.

I want my Halloween costume to take as little effort as possible and be cheap—extremely cheap. That means I don't want to pay 50 bucks for some costume online or spend all day playing with liquid latex, and I most definitely do not want to visit a super crowded costume store in Hollywood.

Obviously, millionaires like me don't really have to worry about an empty wallet, but for the rest of you out there, having no cash when it comes time to paying a bill can be excruciatingly embarrassing.

Check out this video to learn how to do How to Do Black and White Wavy Lines Nail Art Video: .