
News: 3D Laser Scanner from Trash
This brilliantly simple tutorial explains how to make a 3D laser line scanner from old junk parts. Follow along and you will be loading objects into your hard drive in no time!


This brilliantly simple tutorial explains how to make a 3D laser line scanner from old junk parts. Follow along and you will be loading objects into your hard drive in no time!

Today's guide is on creating a password protected folder on Windows 7 without any additional software. Yes, you heard that right. No extra software at all! This guide is intended for beginners. But please note, this method should not be used to store financial or otherwise highly confidential material. It might be a good place to hide a planning document for a family member's birthday party or similar occasion where you need to keep something secret temporarily.

Have you ever wondered how credit card numbers work? I mean, how they really work? How do they come up with the numbers? Credit cards actually follow a very specific pattern. Let's take a look at how they're set up.

Much more complex than I had to make it- that's why I posted it. I think it looks cool...

I thought this one was interesting. Long exposure while zooming out. All of the bright spots from the guitar became streaking lines. Maybe not that scary but I thought it was an interesting technique with an interesting result. Probably would have worked a lot better in a better location! My classroom isn't that interesting.
For more than a decade, Interplay was arguably the best video game publisher in America. Their list of games is a who's-who of the most creative and forward thinking games of the '90s, including everything fromOut of This World to Alone in the Dark to Earthworm Jim to Descent. They've been around since 1983, but have fallen on hard times since 1997, when they became a public company. They were acquired by a French publisher who then went bankrupt. They were forced to close their internal deve...

hi im quite new to palmistry and was just wondering what my lines mean ......... also what does that mole mean

The indie game scene is constantly expanding, but in 2008, Minecraft, Braid and Angry Birds had not been released, along with all of the other indie games that established the financial viability of the format. Indie games were the all-but-exclusive purview of free Flash game sites and the proud users of TIGsource.com. The Independent Gaming Source is a massive forum for indie game developers to share their projects with like-minded individuals, while seeking help and approval of their games.

These firework went off at Dogwood Dell in Richmond, VA. We watched them from Byrd Park, which is right beside the Dell. I though the lines of the explosion looked like lightning bolts or electrical charge off.

Pariah Movie Poster and Trailer.

Captured with my iPhone this past weekend in Tribeca. Clearly staged for some kind of shoot, lots of passerbyers took photos (including me!)

Wow. I'm not much of an MW or BF player but the first 12 minutes of the game are visually impressive, probably the best graphics and animations I've ever seen. Lots of game has great graphics but if the animations are not up to par (The Witcher 2), the game suffers considerably.

I am more excited for this indie gem from Supergiant games than I am for any other 2011 release. The gameplay, visual style, music, and unique narration all look focused and stimulating.

Not every DIY project is as executable as, say, making a potato gun. Occasionally, we observe a quixotic project that is just plain wonderful. Consider rich guy Philip Anschutz and his eponymous Anschutz Entertainment Group (AEG). His ambition to bring an NFL team to Los Angeles is a Fitzcarraldo-sized DIY project that, if the stars align, might happen in time for the 2016 season.

Todd Cole directed this beautifully shot (DP Matthew Lloyd) and art directed preview of the Rodarte Spring '11 line. The visual execution of this ostensibly simple concept is flawless; there are no extraneous colors whatsoever. Clarity of vision and preproduction certainly paid off.

Vince Vaughn and Kevin James in The Dilemma... hoo boy. Ron Howard hasn't tried a comedy like this since 1999's disastrous Ed TV. Mike's got another film lined up for ya though...

How Deep Is your Love ? ! Great one for Lovers .. or maybe not !
These are the best and worst clothing companies based on human rights, the environment, labor, etc. See for yourself. Can you spot your favorite clothing line amongst the list?
"twinkle twinkle little staar.............." mmhhh.." how u wonddd"... mmhhh.. scratching the head wondering what is the next line...ohh..the sweet voice with broken language is the best song we can hear ever...

Choreographer Willi Dorner's curiously charming “human sculptures” invade New York City as part of the French Institute Alliance Française’s Crossing the Line festival. More images of Dorner's Bodies in Urban Spaces at the Wall Street Journal photography blog.

Exactly how did Sly manage to collect all our favourite 80s action stars in one super-movie? And why couldn't such a movie come out IN the 80s?

Not that those of us living in California need this primer, but you know, sometimes those lines are just too damn long!

Who says zines are dead? This is a challenge along the lines of National Novel Writing Month. In the month of July, this site challenges you to create a 24 page zine in 24 hours. No preliminary planning. What sort of zine would you create?

The Fan Sheep was released today. Make sure you fan the sheep's facebook page and get yours within the next 20 days!

How to make balloon animals the easy way. Anyone can learn how to make balloon models it's all in the hands,twisting and imagination. Be the hit at the party even make money out of it yoursel! Bernie's easy to follow balloon workshop videos on line on youtube at mujawooja

lol. Use the strait line! From the guys at Penny Arcade.

For an ivy league freshman in 1973, it was simply a rite of passage to take a date to a foreign film. I would pretend (oscar worthy effort by yours truly) to adore each film...for the simple purpose of maybe getting lucky with an ivy league female. By accident, I actually enjoyed this insane film. Border-line pornography, it made excess an art form.

Writing is everything when it comes to good copy. Here is a video collection of some of the classic lines from the now over television show THE WIRE. Never could get into the show, but the bits and pieces put together are classic. Here is the sequel Part 2
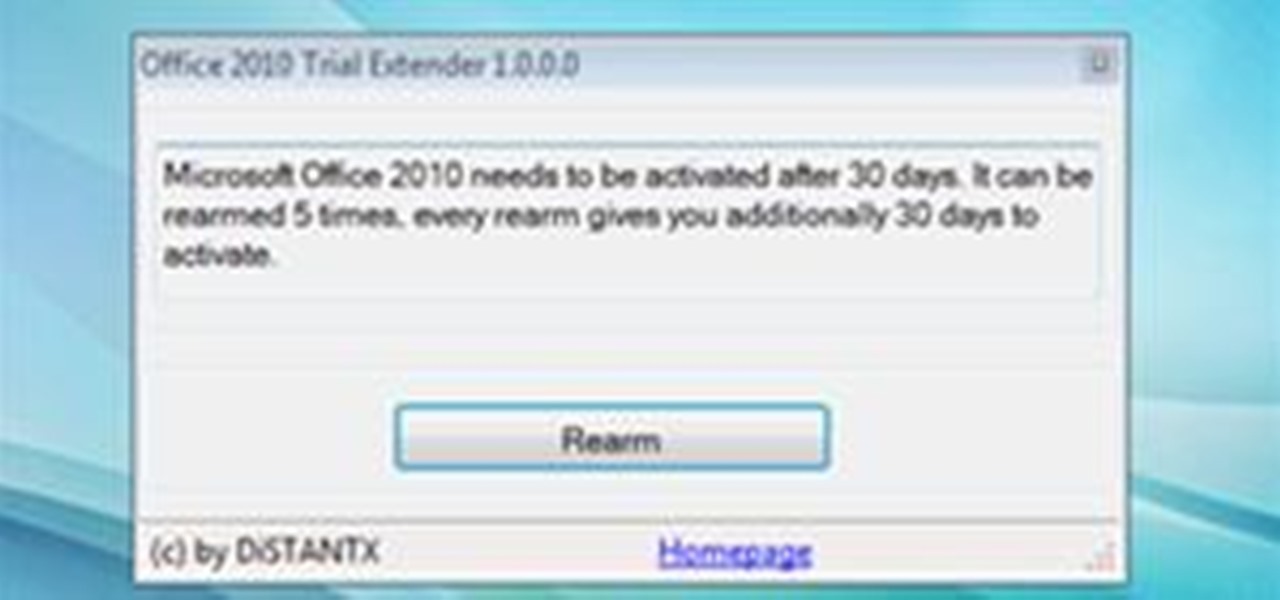
via LifeHacker Windows: If you want to squeeze all the use out of Office 2010 before you're required to pony up for a license, free utility Trial Extender will extend the free trial period up to 6 months, no command-line work required.

Photographer Owen Silverwood's Beat Maps. / phil collins / ...air tonight /

Check out these videos by P+S Technik, they are very informative about setup and the basics for using these unique type of dollies.

Aside from the bizarre fascination with being able to see celebrity homes in Malibu (see the Streisand Effect: http://en.wikipedia.org/wiki/Streisand_effect), the CCRP is a great place to check out local surf spots up and down the Coast:

As if the title does say enough they have the tag line, "Story of a Nympho"

When playing hard to get, there's a fine line between making yourself desirable and being perceived as unattainable. Tracey Cox talks about the delicate art of playing hard to get. Tell if 'playing hard to get' works.

To many Photoshop beginners the pen tool is a hard-to-grasp mystery. What they do not know is that pen tool offers the most flexible way to manipulate lines and images. This video tutorial will try to demystify the infamous Pen tool. Get started with Photoshop's pen tool.

Anyone who has used Linux long enough is familiar with sudo. Short for superuser do (or substitute user do, depending on who you ask), it allows users to run commands as either root or another user on the system. From a hacker's point of view, sudo is often all that stands between them and root access. We'll be exploring an older vulnerability in sudo that allows a user to run commands as root.

Downloading third-party screen recording apps can be dangerous. The primary function of these apps is being able to record everything on one's display, so it's easy to see how a malicious developer could exploit this for their own gain. That's why the addition of Android 10's built-in screen recording is so impactful.

We may or may not see Apple's long-awaited take on AR smartglasses this year, but the company is more than getting its practice swings in with its current wearables business, which hit record revenue in 2019 according to financial results released this week.

Investment in augmented reality remained robust in 2019. For the third consecutive year, we looked back on the biggest funding deals in the AR industry this week, and a familiar name came out on top.

They say it is always darkest before the dawn. If that's the case, then perhaps there's a light ahead for Magic Leap after more unfavorable news in the form of executive departures.