When I was a kid, the 4th of July was my favorite holiday for one simple reason...the joy of making things go BOOM! Somewhere along the line that fun was taken away by politicians. It's time to put the fun back in celebrating freedom. From your friends at America's favorite podcast, Anarchy-X.

See how to avoid rejection on the singles scene! When it comes to putting the moves on someone, no one can make themselves rejection-proof. But you can increase the odds of a good outcome.

Want to see whether your PC is being accessed by hackers? Netstat (network statistics) is a command-line tool that displays network connections (both incoming and outgoing), routing tables, and a number of network interface statistics. It is available on Unix, Unix-like, and Windows NT-based operating systems. This video tutorial presents a basic introduction to working with the netstat tool. Determine whether you've been hacked with this how-to.
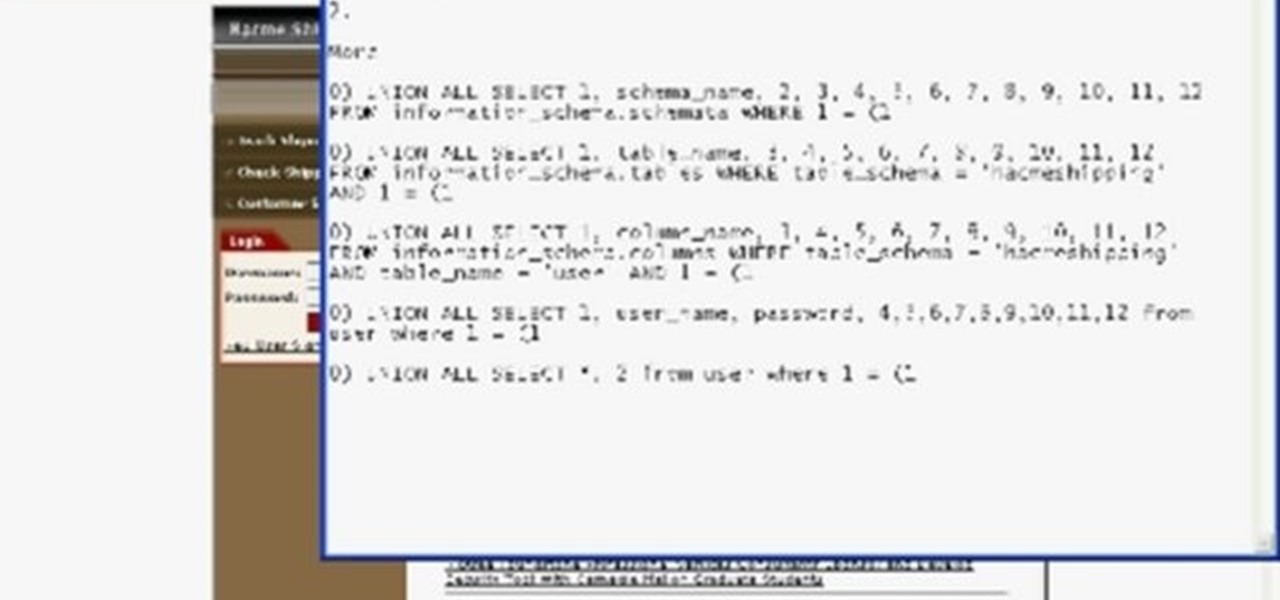
Foundstone Hacme Shipping is a web-based shipping application developed by Foundstone to demonstrate common web application hacking techniques such as SQL Injection, Cross Site Scripting and Escalation of Privileges as well as Authentication and Authorization flaws and how they are manifested in the code. Written in ColdFusion MX 7 using the Model-Glue framework and a MySQL database, the application emulates the on-line services provided by major shipping companies. This video will get you st...

The Professor of Silliness returns with some paper. Watch this instructional video to make a tall tree out of newspaper. You need an old newspaper, masking tape, and scissors. Simply lay out the newspaper pages from end to end and tape them together. Then roll it up at a diagonal, starting from one corner, and pack i it into a compact tube. Use tape to keep the tub intact Use the scissors to cut vertical lines half way down the newspaper tube. Pull out the inner most layer and turn your recyc...

In this human anatomy video tutorial, you learn how to dissect a human cadaver to get a better look at the nasal cavity and sinuses. You'll see the paranasal, which is alongside or near the nose, and the paranasal sinuses are the mucosa-lined air cavities in the bones of the skull, communicating with the nasal cavity.

If your looking for a break from monopoly and checkers, try your hand at the ancient Chinese board game Go. Go is a strategic board game in which you must try to surround a vacant point on the board with your stones and avoid getting your stones tied up by your opponent.
Welcome back, my neophytes! Many of you might have a personal diary and might think Why do I spend so much time to write in the damn diary? or Why waste money on the diary, even though you would be wanting it? It's time you found out a solution!

For a wearable blue makeup look, you will need the following: a base makeup, a brush, a blue pot eye makeup, a darker blue shadow, and a light blue shadow, a very dark matte nave blue eye shadow, liquid blue eyeliner, a light cream eye shadow, a blending brush, a soft brown shadow, mascara, and concealer.

Learn how to get Moroccan eyes with fold and brown shades. - Apply a base.

Gathering the materials is probably the most challenging part of the project, though it's great fun.

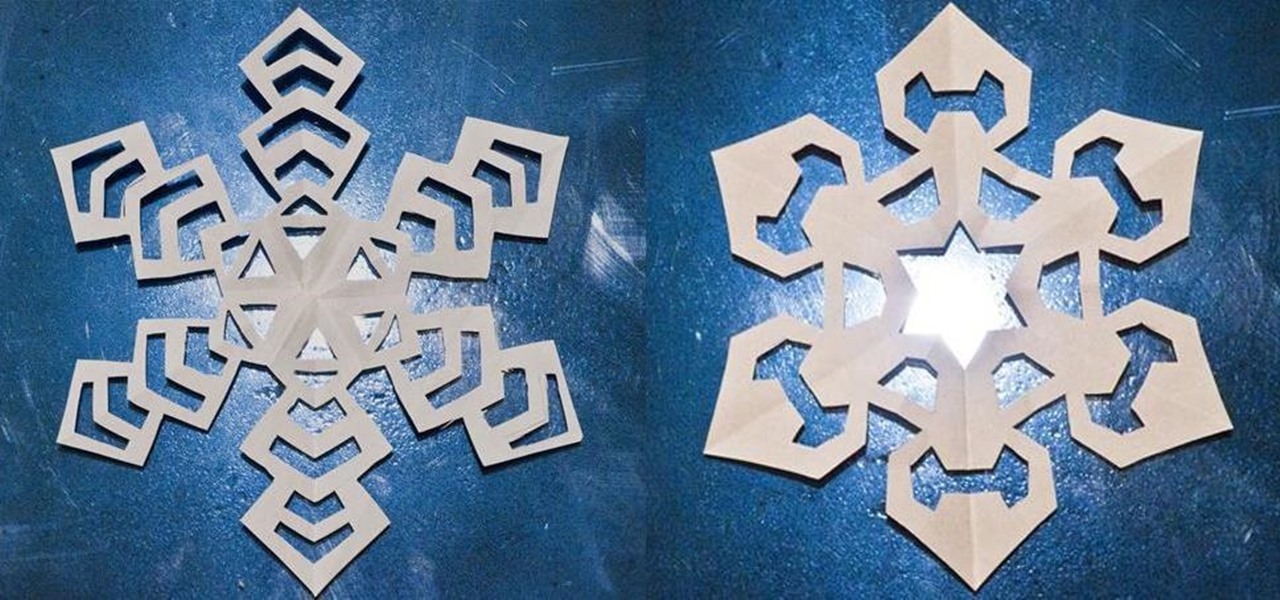
We've all made them. I remember making hundreds of paper snowflakes when I was in elementary school. You take a piece of paper and fold it in half, then fold it in half again. You now have a piece that is one fourth the size of the original. Now you fold it in half diagonally. You then cut slices out of the edges of the paper, and unfold to find that you have created a snowflake. The resulting snowflake has four lines of symmetry and looks something like this: If you fold it in half diagonall...

For anyone who's ever wondered why people are swatting an odd-looking object back and forth across a net, here's the lowdown. Watch this video to learn how to play badminton.

Hello, my name is Nicole Valentine and on behalf of Expert Village, I'm here to talk to you about how to coordinate birthday games for a birthday party. We're going to now talk about how to play the game think fast. This is a very simple game. Just use a ball that you have at home, go to your kids room, go to the toy box and choose an easy ball and you would like to line the guest of the party in a circle. Choose a theme. If it's a boy's party, you might want to go with Power Rangers, or spor...

It feels like every few months, some new feature is discovered in the Pixel's Camera app. By taking advantage of machine learning and the high-quality camera, Google continues to add hidden functions that improve your life even if they're a little niche.

Picture-in-picture mode on Chromebooks is almost identical to the one found on Android phones. Once activated, it transforms your video into a small window so you can do other things while watching. But the Chrome OS version is actually a bit better thanks to the addition of an Android 11 feature.

Imagine being able to play a video instantly on hundreds of thousands of devices across the globe. It's totally possible, as long as all of those devices have a Chromecast plugged in. When Chromecasts are left exposed to the internet, hackers can use add them to a botnet that can play YouTube videos at will. The "attack" is made even easier thanks to a simple Python program called CrashCast.

Beloved toy maker Lego is returning to the realm of augmented reality, this time with an experience that explores supernatural fun.

In a previous tutorial, we were able to measure horizontal surfaces such as the ground, tables, etc., all using ARKit. With ARKit 1.5, we're now able to measure vertical surfaces like walls!

While we've seen Snapchat apply sky segmentation to AR content, the makers of the Blue Sky Paint app have applied similar capabilities to create and share airborne art.

Project Fi, Google's MVNO, is running a new promotion on the latest and greatest from LG. From July 16 until the 29th, whenever you order and activate the LG G7 ThinQ or LG V35 ThinQ, you will receive a $300 service credit. When you do the numbers, that equals a minimum of three free months of service.

Note-taking apps are a dime a dozen on the Play Store. However, due to their inability to sync across devices, many can't compete with Google Keep. Mozilla decided to throw their hat in the ring with Notes by Firefox, and unlike others, their notes app syncs easily with one of the most popular browsers, plus it's encrypted.

Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than others, and a little Python could be used to brute-force any weak hashes to get the passwords they were created from.

Have you noticed the many utility ARKit apps on the App Store that allow you to measure the sizes of horizontal planes in the world? Guess what? After this tutorial, you'll be able to do this yourself!

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

While hackers adore the command line, working with the GUI (graphical user interface) of an operating system has some advantages. This is especially true when it comes to post-exploitation. When we can control the mouse and keyboard of a remote computer, we can truly say we have complete control over the device. Today, I'm going to introduce to you the PyAutoGUI module, which does just that, and just how much fun you can have with it!

The fourth and final beta version of Android O just made its debut, and the biggest change is what appears to be a new code name. When you access Android 8.0's version number Easter egg, you'll be greeted by ... a cartoon octopus.

Usually, the mucus lining of the female genital tract presents a barrier that helps prevent infections. But, somehow, the bacteria that causes gonorrhea gets around and through that barrier to invade the female genital tract.

Crayon, a free 3D drawing application by the mysteriously named arkalian, showed up in the Windows Store recently, so I gave it a try like I do all new apps for Windows Holographic. Truthfully, I loaded it up not expecting much, but wow, was I wrong. It's a simple idea, but it's executed well enough to make it a truly great experience on the HoloLens.

Even though the 88th Academy Awards have come and gone, there's a good chance you still haven't seen all the films that were nominated—or even those that won big.

Hello friends! This tutorial will teach you how to build a local pentesting lab on your Linux machine which will enable you to easily install common web applications so you can practice locating and exploiting their known vulnerabilities (or discover new ones!). In particular, this is an excellent way to learn how to hack Wordpress, Joomla, and Dupral plus many more!

Sony's Xperia line of smartphones are beautifully crafted and have many great features. But considering the fact that Sony has evolved into a media company over the last two decades, it's their media-related apps that stand out the most.

We all have those moments where we're bored or lonely, and in those times, just having anyone to talk to would be awesome. But maybe your friends are all busy, or everyone you know is at work and nobody's responding to your text messages.

One of Android's biggest strengths relative to iOS was the ability to switch to a third-party keyboard. While Apple has finally included this feature in its latest OS and leveled the playing field a bit, the variety of options still pales in comparison to what's available on Android.

In today's world, we're constantly switching back and forth between all of our internet-connected devices. A PC may be great while you're at your desk, but the living room couch is tablet territory, and nothing beats the portability of a pocket-sized smartphone while you're on the go.

So you just bought a fancy new Nexus 6 complete with its gorgeous and gigantic display—now what? Unlike Samsung's TouchWiz, stock Android doesn't sport any cool split-screen features, so how do you really take advantage of all that screen real estate?

At $349 off contract, the Nexus 5 has always been one of the best bang-for-your-buck smartphones on the market. In order to keep the price that low, however, Google had to pass up on some of the minor features that other flagship phones offer.

Since the release of the Galaxy S5 back in April, the process of converting older models, like the Galaxy S4, to replicate the look and feel of the newest S-family member was inevitable. Galaxy users didn't want to be left out, and for good reason. The revamped interface of the S5 introduced a new color palette that was a definite improvement from the flat boring colors on older models.

Want to get even this Halloween? Want to scare somebody with nothing but a few lines of code? Here's how it can be done...

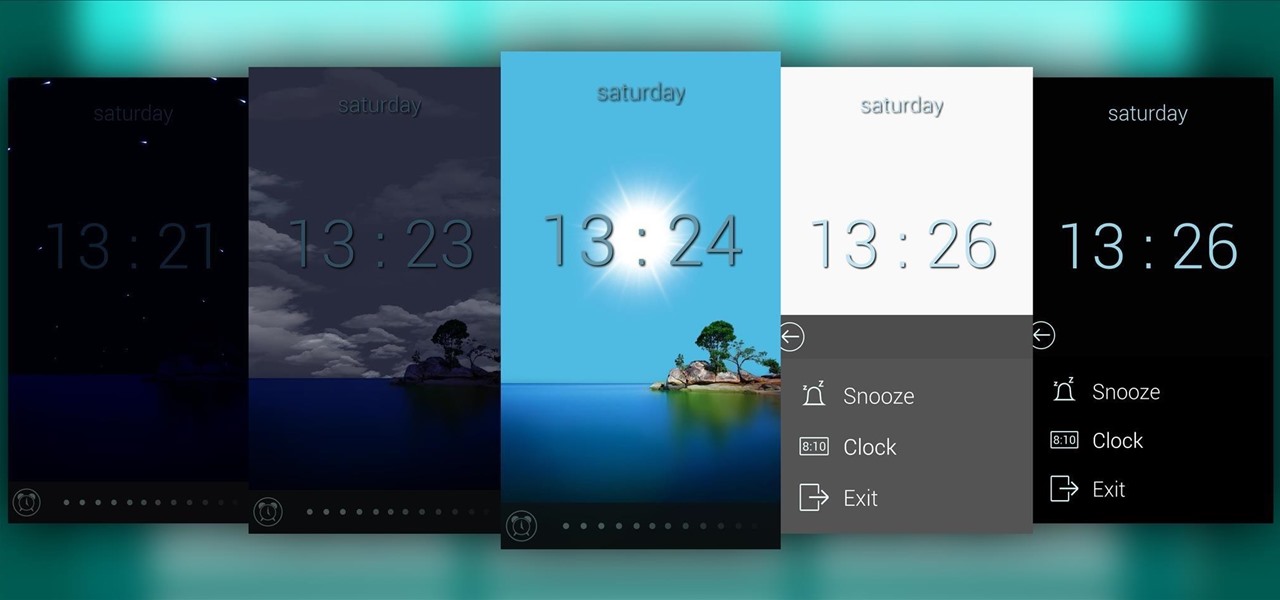
Most alarms just make noise to wake you up, and it can be a bit jarring coming off of a deep sleep to suddenly being woken up by a blaring sound. On the flip side, if you're a heavy sleeper, this might not even be enough stimuli to snap you out of your 8-hour coma.