
How To: Play a boogie woogie bass line on the piano
Learn how to play this basic boogie woogie left hand bass riff one the piano or keyboard.


Learn how to play this basic boogie woogie left hand bass riff one the piano or keyboard.

In this video learn to play some left hand blues bass lines and riffs on the piano or keyboard with this beginner blues lesson.

This video will teach you how to backstick with your drumsticks whether you're playing on a drum kit or in the drum line at your high school. Backsticking is mainly triplets, and a valuable trick to learn for any drummer.

This tutorial shows you how to use the retopo feature in Blender to surface drawn lines.

USB flash drives are great for moving files on and off of a linux server, but how do you do it? This quick tutorial shows you how easy it is!

Tim Carter, of Ask the Builder, demonstrates how easy it can be to make a level line across an entire room in your house.

When working in a network, you can't always see the connection lines if you are too zoomed out. This tutorial shows you how you can quickly connect nodes in Houdini.

Here, see the Evans Gambit Opening book lines with possible variations. The video includes a match of Bobby Fischer's that highlights the use of the gambit. So, play like Bobby and be a master -- soon.

This is a look at the book lines for the Scandinavian Defense played by Black, exploring variations, and also including a grandmaster game between Karpov and Larsen for illustration.

The Danish Gambit opening allows for rapid attack development for White. This video explores the book line moves, along with possible counter-play by black.

Matt covers some lines with a black ...Bg4. He found the first game with analysis on the Kenilworth Chess Club site. Most of the analysis he gave for this game is taken verbatim, but he does mention a couple side variations that you should be curious about. So watch!

This is a discussion of a tricky line against the Stonewall, the Horowitz Defense (2...Nf6 3.Bd3 Nc6). White allows Black to spend three moves capturing the light squared Bishop and bringing White's pawn from c2 to d3, preventing a ...Ne4 invasion. This makes for very dynamic play.

The Glo Bug Yarn Egg. Tie it. Then it's hook, line, and sinker. This pattern is a standard for steelhead, salmon, and trout

Create a 2-axis chart in Excel 2007 combining a column chart and line chart
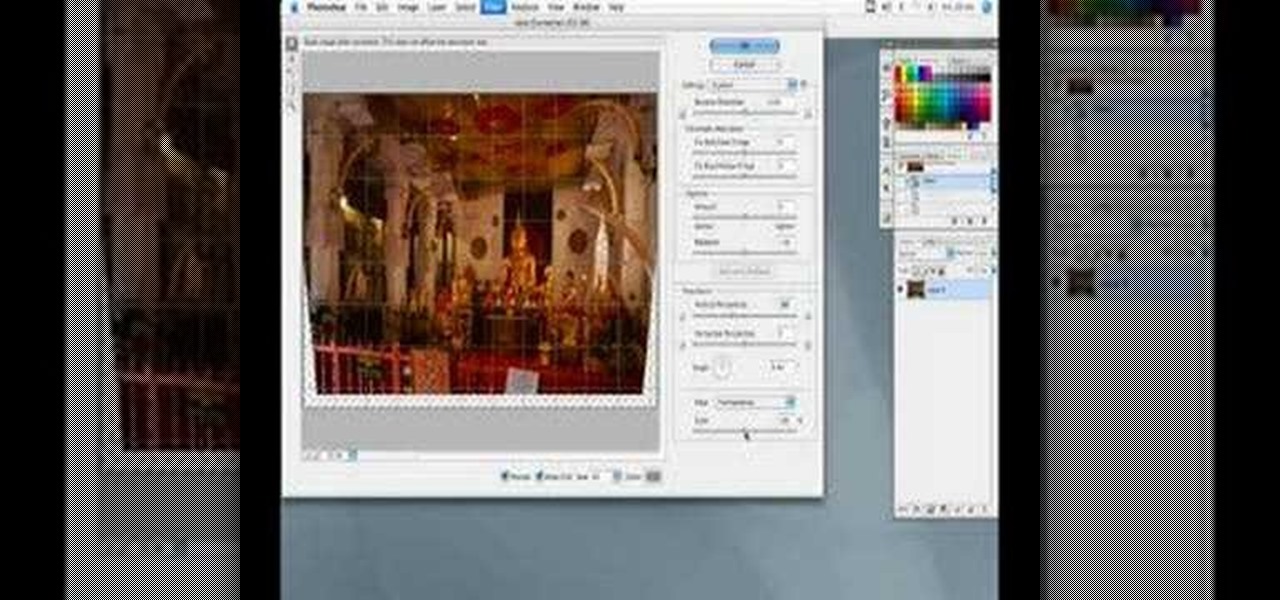
This tutorial shows you how to correct converging vertical lines (extreme perspective) or surface edges on photos using Photoshop tools.

Learn how to do add a bass line while beatboxing.
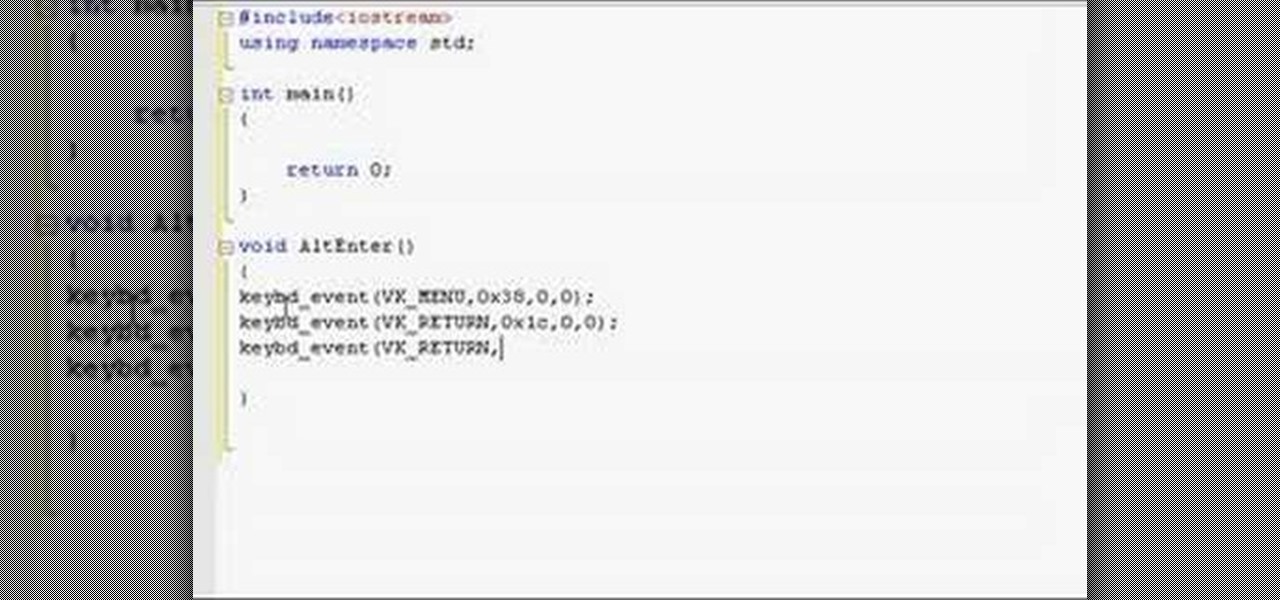
This C++ programming tutorial goes through the use of functions, pointers, how to make fullscreen, and changing colors per line.

It is very hard to see the blood line in a dark toenail. This video will show you how to trim or cut a dark toenail without hurting the rabbit or bunny.

Learn how to use this v-cut passing drill in order to help your players improve their passing skills on the basketball court.

Learn how to explode from half court to the three point line and practice your three point shots in this 3 point shot off the fast break basketball drill.
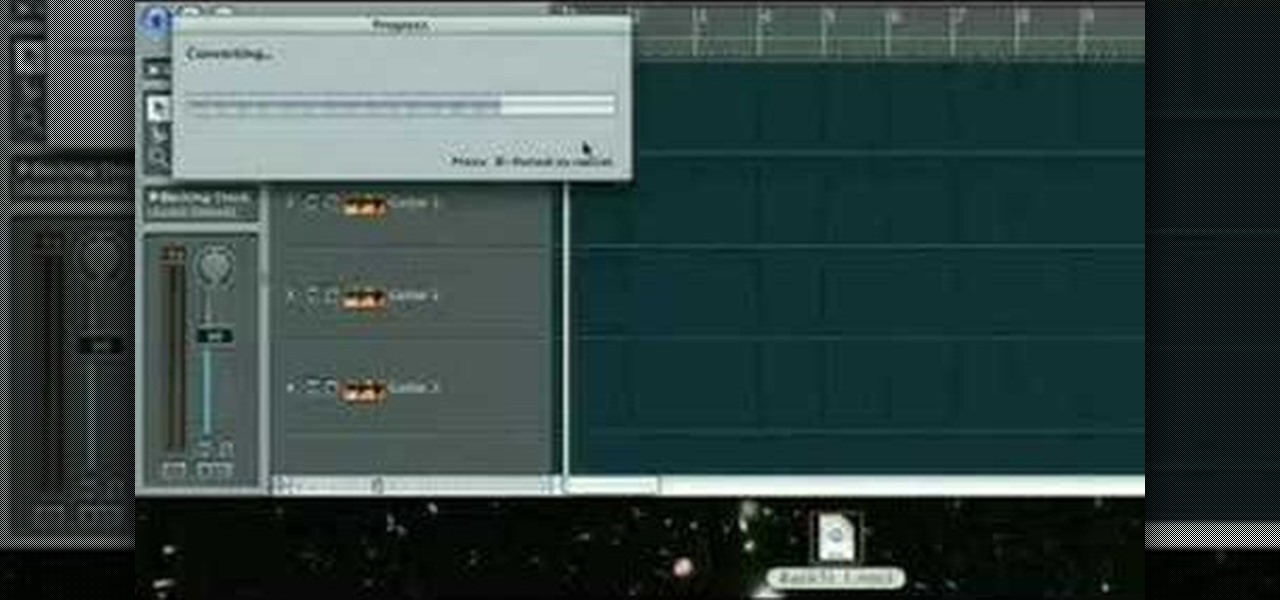
Practice your soloing skills and record melodic lead lines over your favorite song or backing track by importing pre-recorded tracks into Logic.

Develop your technique and learn how to get your lead lines to come through clean and strong using rockin' Minor Pentatonic fingering exercises.

Learn some basic plumbing skills. Watch this video to learn how to glue PVC joint pipes together to form your drain lines.

This video shows you the proper technique to draining the engine fluids from the radiator and connected hoses before removing the engine for disassembly. Explains the process for using your specific engine repair manual to label all of the wiring, vacuum lines and hoses so that installation later will be smooth.

This video demonstrates how to perform the overturned back sacada. This move is one that the follower does and the key points for success are to focus on the spiral energy of the step and stretch the step. The leader should pay close attention to the line taken.

With any drawing tool you would expect to be able to create lines with arrowheads. In this tutorial Terry White will not only show you how to do it in Illustrator, but he will also show you how to give your arrows a little flare by reshaping them with the Pencil Tool. That's right, he's found a great use for the tool that no one likes to use.

A very important thing to keep in mind when you're creating images from scratch or even putting things into existing images is the concept of perspective. Bert goes back to basics to teach this concept, starting with a horizon line and adherence to the rules of mother nature.

You can learn how to create an impossible shape out of paper. All you need is a piece of paper and scissors. First, you cut along the 2/3 lines of the paper. Then you flip one half of the paper over, and you have created an impossible shape.

You can practice skating backwards. There is a drill you can do. Set up five to ten sticks in a straight line and begin to c cut thrust down the length of the ice.

Personification of the Infinite Consciousness. Lord of Hosts. Master of the Universe. These are just three of the hundred-odd titles of the Hindu god Ganesha. Luckily, drawing the Hindu deity Ganesha isn't so complicated.

First of all take the clay and make a roll. Now keep rolling to form a roll that has one end large and the other end smaller at the tip. Now bend the roll upwards from the middle. Now take a match stick. Now use this to make a hole to make the mouth. Use to fingers to make the corners of the mouth round in shape. Make the mouth wide and open. Now make the eyes by using a matchstick to pierce the sockets. Now take a little clay and then make a roll of it. Now make a leg out of it by making the...

Wash your face and make sure there are no oils or lotions. Use a toner or a makeup primer which you can purchase at drug store. Pull your hair off of your face with a headband. No hair should be near your face, ears or nape of neck. This is the oil undercoat for use with the 'Kabuki Oshiroi' Shiro-Nuri (Doran) face paint. It is softened in the hands and then rubbed over the entire face or other areas to prepare the skin for the white face makeup. This is the stiff wax used to flatten out faci...

The new navigation gestures in Android 10 let you ditch the three buttons along the bottom edge for a truly full screen experience. In the buttons' place, you now get an inconspicuous little line, but even that can be hidden with a setting in One UI 2.

Search engines index websites on the web so you can find them more efficiently, and the same is true for internet-connected devices. Shodan indexes devices like webcams, printers, and even industrial controls into one easy-to-search database, giving hackers access to vulnerable devices online across the globe. And you can search its database via its website or command-line library.

The drag on your fishing reel is what keeps big fish from breaking your line. Properly setting the drag could prevent you from losing that trophy fish.

Welcome back, my tenderfoot hackers! As you should know from before, Snort is the most widely deployed intrusion detection system (IDS) in the world, and every hacker and IT security professional should be familiar with it. Hackers need to understand it for evasion, and IT security professionals to prevent intrusions. So a basic understanding of this ubiquitous IDS is crucial.

Hello fellow training hackers. I do not know if many of you are familiar with ruby, but since it is a useful scripting language, that hasn't been covered too much here on Null Byte, I thought why not do some How-tos about it now and then.

See how to make homemade "ice" candles out of taper candles (or wax flakes). Cut up the taper candles, heat them until melted, then pour into a container lined with ice (chipped ice, not cubes) with the wick dangling in from above. The ice will create an interesting design in the candle.

Step 1: Draw Horizontal Lines for Uniform Size Overall Hi, This is a tutorial video to write your name in Graffiti.

Easy Square Knot Bracelet with beaded lines. To make this bracelet you only need to know how to make a square knot. This is a good bracelet for beginners in macrame.