You don't have to wait for the carnival to come around. You can make this special treat any time you like at home. It takes a little bit more time than at the fair but will be worth the look on party guests’ faces when they realize you've just made this counterintuitive dessert.

It feels like every few months, some new feature is discovered in the Pixel's Camera app. By taking advantage of machine learning and the high-quality camera, Google continues to add hidden functions that improve your life even if they're a little niche.

It's exciting to get that reverse shell or execute a payload, but sometimes these things don't work as expected when there are certain defenses in play. One way to get around that issue is by obfuscating the payload, and encoding it using different techniques will usually bring varying degrees of success. Graffiti can make that happen.

Google just released the first version of the next major Android update. Early Android 11 builds will only available as developer previews, so you can't just sign up for the beta program and install the update as an OTA for the first couple months. That said, it's still pretty easy to get.

It's that time again. Snow days, Thanksgiving dinner, holiday presents ... and great Black Friday deals. Starting the Friday after Thanksgiving (or sometimes a few days before), millions of items will go on sale, including your next Android phone.
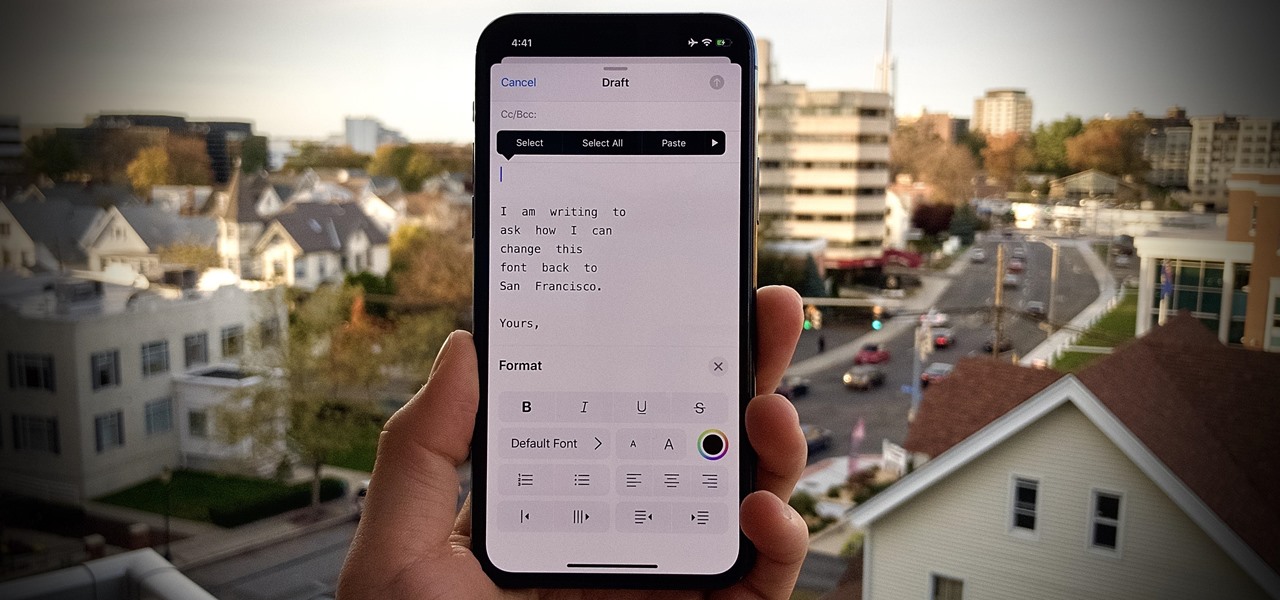
One of iOS 13's coolest features is the ability to download, install, and choose fonts in select apps like Pages and Mail. However, you might notice an issue when writing an email with a custom typeface: there's no option to return to the default font. What gives?

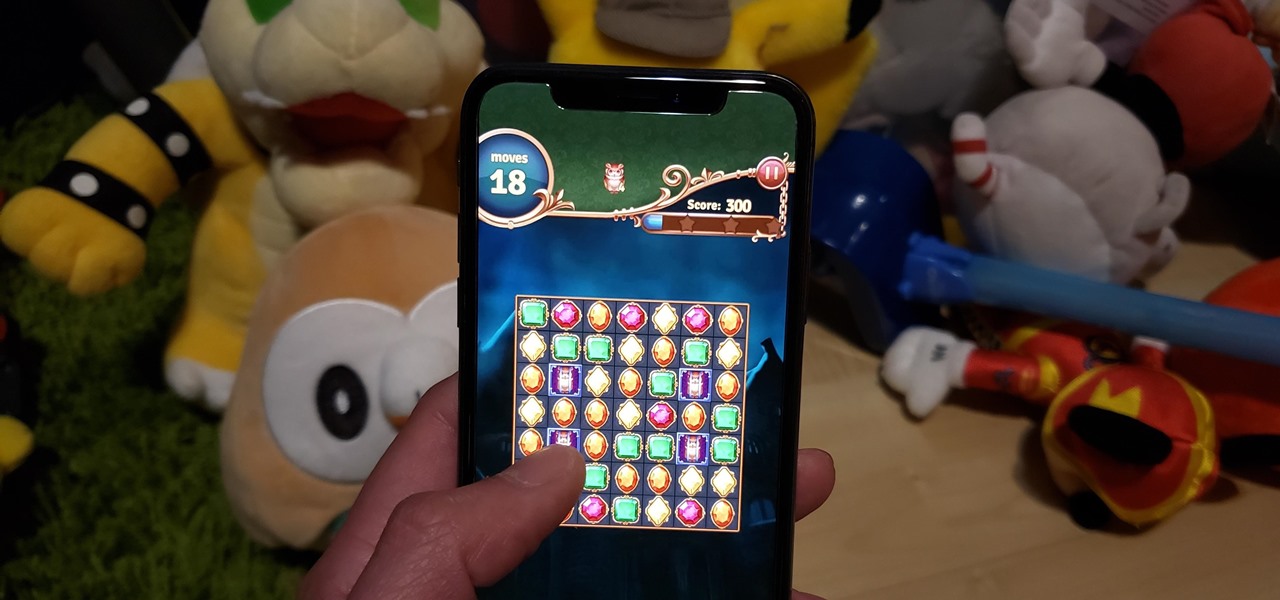
Though not as flashy as other mobile gaming genres like first-person shooters, puzzle games continue to glue players to their phones. Puzzlers are perfect companions while out and about or on a commute, and they're also a great way to stimulate your brain and hand-eye coordination in a fun, relaxing way.

While Gucci is among the most recognizable brands in fashion, you would be excused for not realizing that the company makes sneakers as well.

With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. While it won't help find any zero-days, web scanners such as Uniscan will detect common vulnerabilities.

It's that time of year again. No, not Thanksgiving. Black Friday. There are a lot deals available this holiday weekend, many of which include flagship Android devices. Whether you are thinking of buying a phone for yourself or looking for a gift for someone else, you can find a little savings to shop smart during the holidays.

In a previous tutorial, we were able to measure horizontal surfaces such as the ground, tables, etc., all using ARKit. With ARKit 1.5, we're now able to measure vertical surfaces like walls!

While we've seen Snapchat apply sky segmentation to AR content, the makers of the Blue Sky Paint app have applied similar capabilities to create and share airborne art.

Project Fi, Google's MVNO, is running a new promotion on the latest and greatest from LG. From July 16 until the 29th, whenever you order and activate the LG G7 ThinQ or LG V35 ThinQ, you will receive a $300 service credit. When you do the numbers, that equals a minimum of three free months of service.

Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than others, and a little Python could be used to brute-force any weak hashes to get the passwords they were created from.

Have you noticed the many utility ARKit apps on the App Store that allow you to measure the sizes of horizontal planes in the world? Guess what? After this tutorial, you'll be able to do this yourself!

The idea of a dock on any smartphone, be it iPhone or Android, is a fantastic invention. It allows you to stay grounded with a core group of apps that you frequently use. However, sometimes that dock can feel like an obstruction in the face of style — but there's a trick to hiding that translucency behind those core apps at the bottom of your iPhone without jailbreaking.

To promote Star Wars: The Last Jedi, Disney and Lucasfilm released virtual porgs into the wilds of Snapchat via a Sponsored Lens on Sunday.

There aren't many people who will believe that a prosthetic zipper face or gunshot wound to the eye (disgusting as they are) are real, but greyscale from Game of Thrones? That'll really unsettle people for awhile because it totally looks like an actual, honest-to-God infection that someone in 2017 could conceivably have. Which makes it very effective come Halloween, whether it's for a full-on Princess Shireen, Jorah Mormont, or Stone Man costume, or to just infect a completely different chara...

The first wave of iPhone X preorders, the ones with a delivery date of Nov. 3, sold out in ten minutes. You can still preorder one and skip the lines next week at Apple Stores across the country, but if you want that bezel-less beauty in your hands ASAP, brick and mortar might be the way to go.

You can pinch yourself, but you're not dreaming. Sprint is actually offering a year of (mostly) free, unlimited service for anyone who switches to the carrier. The only stipulation is that you must bring your phone with you, and it has to be one of the 27 eligible devices.

New York City may not be the friendliest city, but with the apps Via and Curb now letting users ride-share in the city's yellow taxis, New Yorkers can expect to snuggle up close in the back of a cab next to complete strangers. That's right, get ready to feel the love.

Usually, the mucus lining of the female genital tract presents a barrier that helps prevent infections. But, somehow, the bacteria that causes gonorrhea gets around and through that barrier to invade the female genital tract.

Each generation of smartphones ushers in a new set of top-of-the-line specs, with processing power, battery size, and display resolution growing by the year. These headlining features get the most press, but there's one unsung hero that has the potential to make the biggest difference when it comes to real-world performance: RAM, or random-access memory.

Now that Google Assistant is coming to all devices running Android Marshmallow or higher, roughly one out of every three Android users will no longer be able to access the old Google Now interface. The Assistant, which was previously exclusive to Pixel devices, takes over your home button long-press gesture and completely replaces all of the old Google voice search functionality.

Greetings fellow students! I'm currently reading a book called "Violent Python: A Cookbook for Hackers, Forensic Analysts, Penetration Testers and Security Engineers"

As most of you know, I am a strong advocate for using Linux for hacking. In fact, I would go so far as to say that you cannot be a hacker without knowing Linux well. I laid out various reasons for this in my "Why Every Hacker Should Know & Use Linux" article, and I even have a lengthy, continuing series on Linux Basics to help those new to Linux master it.

Hello NullByte, it's mkilic! This time I'm here with the C.H.I.P from NTC. Although it is not too popular, the C.H.I.P is a brand new micro computer. It is very similar to the Raspberry Pi or Beaglebone Black. The key difference with this particular board is its cost and size. The C.H.I.P only costs $9 and measures 2.5 x 1.5 inches. In addition to this, the C.H.I.P has built in 802.11 b/g/n Wifi and Bluetooth 4.0. Considering these great specs, what could a Hacker use this for? Step 1: The In...

Hello friends! This tutorial will teach you how to build a local pentesting lab on your Linux machine which will enable you to easily install common web applications so you can practice locating and exploiting their known vulnerabilities (or discover new ones!). In particular, this is an excellent way to learn how to hack Wordpress, Joomla, and Dupral plus many more!

The Cheshire Cat isn't like other famous cartoon cats: he's brilliantly purple and hot pink, ever smiling and entirely unnatural. However, he makes for a perfect Halloween costume, with his bright, neon appearance and mysterious nature.

Welcome, in this tutorial we shall we looking at creating a safe(r) way to back up your important files. The contents we will be covering are as follows;

It's truly amazing how far smartphone camera hardware has come in such a short period of time. It took roughly 5 years to advance the image processing capabilities from a pixelated mess to the crisp and clear photos we can take today. This reaches well beyond the megapixel spec race, since camera modules these days sport vastly improved optics, wider aperture, and even larger pixel sensors that capture more light.

Developing GUI apps in python is really cool. I ask those who understand the language to help convert some of the command-line or console programs or apps ( I mean programs that are useful to a hacker ) to GUI. I know GUI makes us lazy and not wanna learn but we should all know its fast. Today's tutorial is on p2p chat app I developed last week and decided to share it with the community since its kinda cool.

Firstly let me start by giving credit to Lucid for their guide on Evilzone which inspired this idea, as well as the recent talk of anonymity on here.

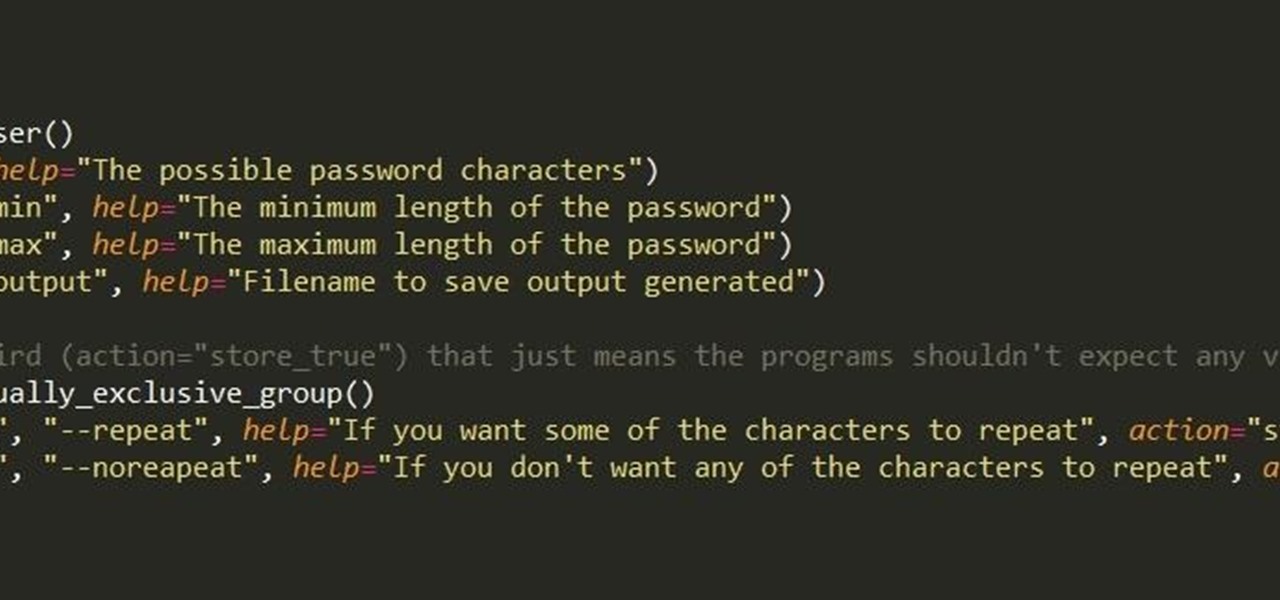
First of all, I hope the title makes sense. :D Well, this is basically creating a program that can help with dictionary attacks. Generate possible passwords. It pretty much lies in you knowing the person you want to hack.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

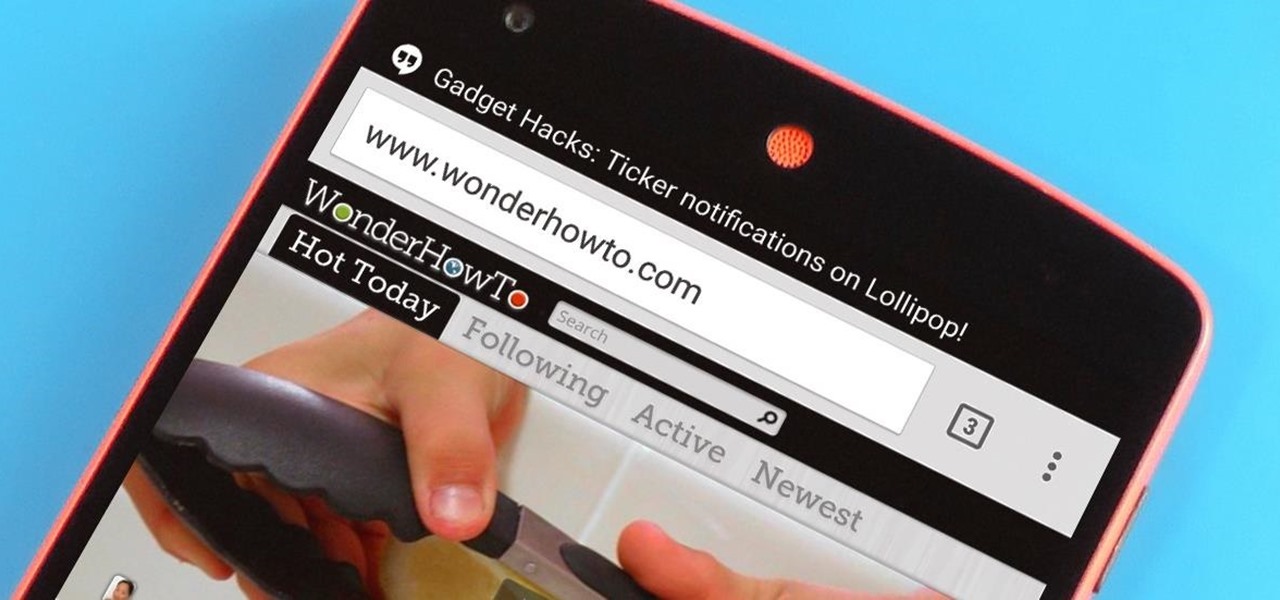
With Android 5.0, Google introduced a new "Heads Up" notification system for incoming calls and messages. While the new incoming call interface seems to be a rousing success, the rest of the Heads Up system has been met with much less enthusiasm from users.

Welcome back, my novice hackers! This is the third installment of my Python scripting series. If you haven't read the previous two articles, take some time now to go back and read Part 1 and Part 2 before you proceed here.

Welcome back, my fledgling hackers! In an earlier tutorial, I introduced you to probably the most popular scripting language for hackers, Python. To become a professional hacker, you need to have some scripting skills and Python is a good choice if you want to master just one. In this latest guide, I will expand your background in Python and offer you a tidbit of Python code to whet your appetite for all of the hacking to come.

Want to get even this Halloween? Want to scare somebody with nothing but a few lines of code? Here's how it can be done...

LG's arsenal of screen-off and screen-on tap gestures recently expanded into lock screen territory. Dubbed "Knock Code", this feature allows owners of various LG phones, like the G2 and upcoming G3 to unlock their phone with a series of taps on the screen. The most impressive part is that the screen doesn't even need to be on!