Correctly identifying the underlying technologies that run on a website gives pentesters a considerable advantage when preparing an attack. Whether you're testing out the defenses of a large corporation or playing the latest CTF, figuring out what technologies a site uses is a crucial pen-tester skill.
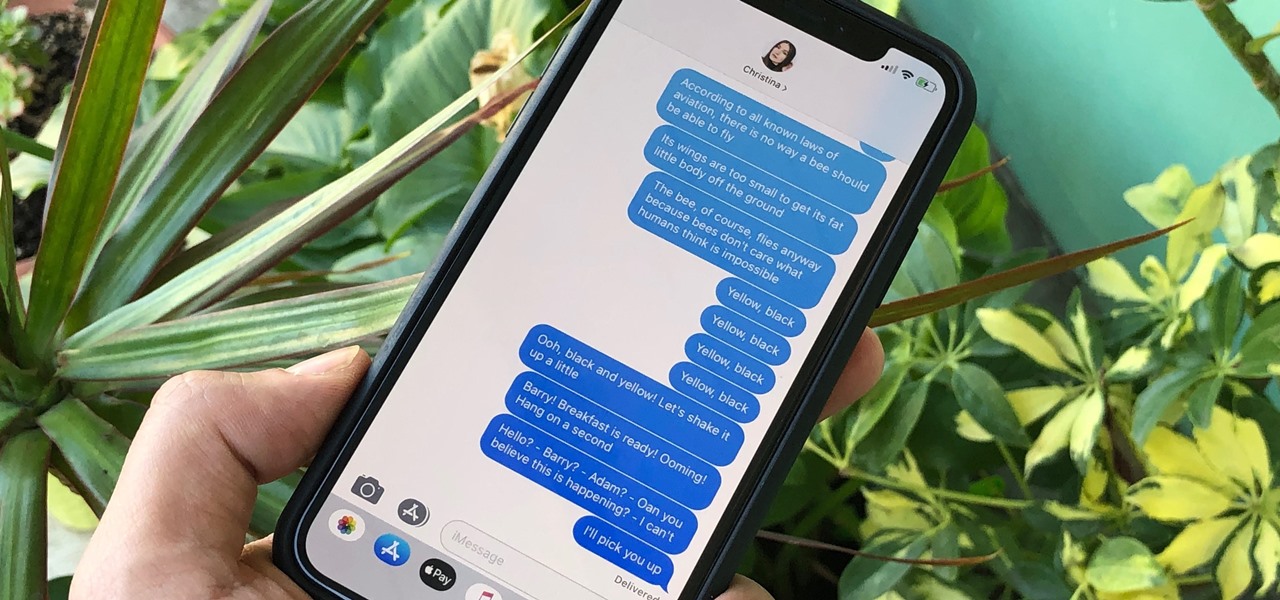
Back in its infancy, the App Store was filled with text bomb apps that allowed users to send a barrage of text messages to friends, family, and foes. It was a fun way to annoy people, but Apple quickly scrubbed the apps because of technical issues. Although text bombs are still banished, you can now use a Siri Shortcut to send text bombs through iMessage on your iPhone.

When it comes to the athletic footwear retail game, it's just not enough to just sell shoes anymore.

Because of its ability to place digital content into the real world, augmented reality lends itself well to artists and creatives.

A lot of people still trust their web browsers to remember every online account password for them. If you're one of those users, you need to adopt a more secure way of managing passwords, because browser-stored passwords are hacker gold mines. With a USB Rubber Ducky and physical access to your computer, they can have a screenshot of all your credentials in their inbox in less than 60 seconds.
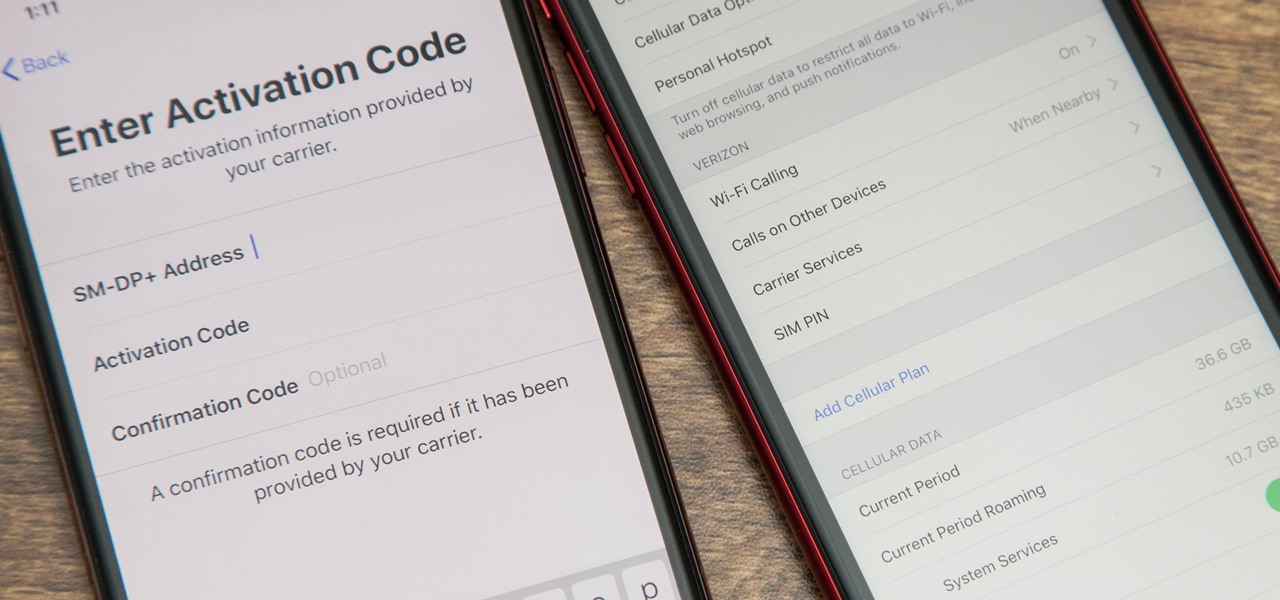
With an iPhone that includes a digital eSIM option aside its standard Nano-SIM card, you can have two cellular service accounts. One can be your primary line with your main wireless carrier, and the other can be from your main carrier or another provider. The eSIM account can be prepaid or postpaid as well as data-only, which is great for traveling. But which wireless providers support eSIM?

In a previous tutorial, we were able to measure vertical surfaces such as walls, books, and monitors using ARKit 1.5. With the advent of vertical plane anchors, we can now also attach objects onto these vertical walls.

After a district judge approved the $85 billion merger between AT&T and Time Warner, we knew AT&T would be quick to reap the rewards of capturing Time Warner's media properties. Today, we get our first look at this with two cellular plans from AT&T. What makes these plans unique is they include a new cord-cutting service called WatchTV.

This time last year, computer vision company uSens introduced a stereo camera module capable of hand tracking. Now, uSens can achieve the same thing with just a smartphone's camera.

After a long hiatus, we shall once again emerge from the shadowy depths of the internet to build an exploit. This time, we'll be looking at how to defeat a non-executable stack by using the ret2libc technique — a lean, mean, and brilliant way of exploiting a stack overflow vulnerability.

Sure, emojis are all the rage, but there's not an emoji for every emotion or feeling just yet. That's where emoticons come into play, emoji's older typographical sibling. Unfortunately, emoticons can be hard to type out, easy to forget, and ASCII art, in general, can be pretty time-consuming to create from scratch — but there's an easy way to forgo all these issues — make keyboard shortcuts.

Karen Gillan must have had an absolute blast chewing the scenery as Nebula in Guardians of the Galaxy Vol. 2, seeing as how Nebula is a ball of pure, seething fury pretty much 24/7. Combine that larger-than-life personality with her iconic blue and silver cyborg look, and you have a guaranteed hit for cosplay or Halloween.

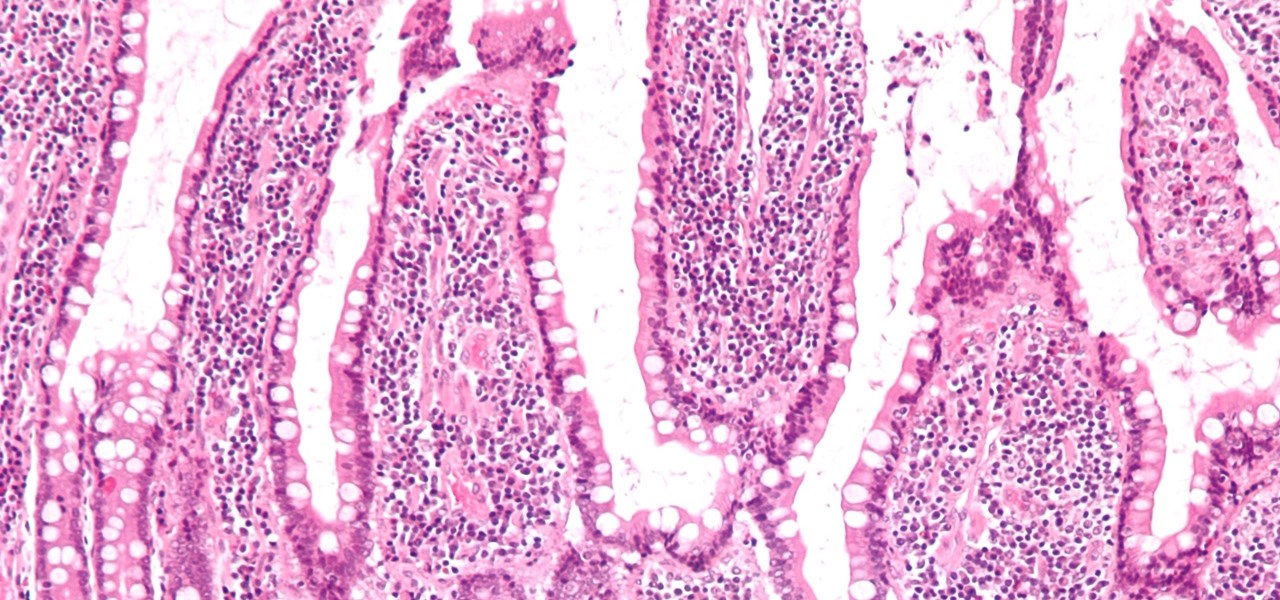
If the all the fingerlike projections in our gut were flattened out, its surface area would be 100 times bigger than our skin's. It's so large that the actions of just a small part of it can impact our health. A new research study has found that enterochromaffin cells in the intestinal lining alert the nervous system to signs of trouble in the gut — trouble that ranges from bacterial products to inflammatory food molecules.

Several recent research studies have pointed to the importance of the microbes that live in our gut to many aspects of our health. A recent finding shows how bacteria that penetrate the mucus lining of the colon could play a significant role in diabetes.

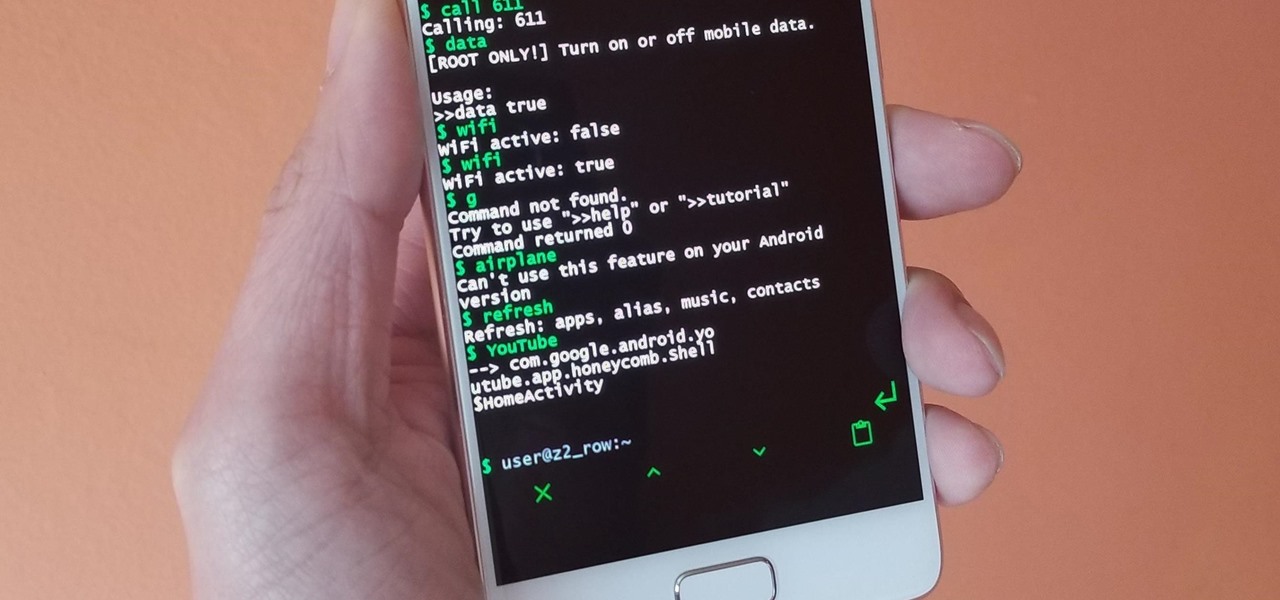
Running commands on Linux seems so complicated for the layman that it may as well be a foreign language. But for the die-hard terminal users, or for those who are just curious about the Linux experience, there's a new Android launcher that gives your home screen a command line makeover.

How can bacteria that lives in the throat of 10%–35% of people—without causing an infection—cause life-threatening meningitis and sepsis in others?

Specialized cells in the lining of the gut may provide a key to preventing an infectious brain disease caused by misfolded proteins.

Apple just unveiled the new iPhone 7 and 7 Plus at their September event, which means we're inching closer to traffic jams, parking lot fights, and day-long lines at Apple Stores, as well as those inevitable, dreaded words: "sold out."

Virtual, mixed, and augmented reality all provide different but compellingly immersive experiences that draw us in through sight and sound. But what about our other senses? A few strange inventions are already exploring the possibilities.

A loop knot can be used to attach most fishing lures and all hooks and flies. A loop allows greater action of the lure or fly and always ensures the line will pull straight down the shaft. With knots that cinch tight agains the eye of the hook, the may move off to one side causing it not to pull straight.

It is never to early to start making Christmas cards, after all its the most magical time of the year and there is nothing worse then leaving everything until the last minute!.. like me!! In this project I show you how I make this stunning Christmas card, and explain about using a cutting knife, I also show you how I use the cutting knife, I wanted to make it easy for you to see what I do when cutting out a pattern however it seems I make it look too easy, so practice on straight lines until ...

A sphere of clear gelatinous goo may not sound all that appetizing. But to food fad fans on social media, the raindrop cake—a soft and lightly flavored edible blob—has gone insanely viral.

Mobile data is expensive. The internet connection that comes with your cell phone plan is generally limited to a certain amount of gigabytes that can be downloaded before your monthly cap kicks in, at which point you run the risk of incurring costly overage fees.

It has been a while since my last Raspberry Pi tutorial , but now I am back with another tutorial. This one I should note isn't your typical tutorial, but as always lets boot up our Pi and wreck havoc.

Welcome back! Sorry I've been gone for so long, but if anyone has been keeping up with these articles, you'll know that when I get quiet, something is cooking under the surface. In other words, I've been working on a project lately, so I haven't had much time!

Hello again, reader! In this post, we are going to cover some data types and how to declare variables. It shouldn't be too hard so just sit back, relax, grab some popcorn and enjoy the ride (while you still can!).

Welcome back, reader! In this tutorial, we will be covering our first program! So let's get to it. We all know the unspoken tradition of the first program when learning a language and of course, here we will respect and complete it. Fire up your favorite text editor (be it vim, emacs, gedit, it's all the same to me, no h8) and try to keep up.

This cardmaking tutorial shows you how to make a floral Christmas card that is complete with embossing using a die cutting machine. This is a very pretty card and once you have seen the tutorial you will see how easy it is to make. I also show you how I get the embossed lines around my cards to add the pearl drops using a box embossing board.

There are few things more satisfying than fulfilling a craving with instant gratification. Companies like Pillsbury and have made this possible with the introduction of their famous Ready to Bake Cookies line: just rip open the package, break off the cookies along the creased lines, place on a cookie sheet, and bake.

Greetings all. Before I get into the tutorial, I would like to mention that I am fairly new to Null Byte (been lurking for some time though), and what really appeals to me about this place is its tight, family-like community where everyone is always willing to help each other and the constant search for knowledge that inhabits this subdomain is a driving motivator for me to join in. I'm glad I arrived at the right time. Anyway, wipes tears (not really)...

Beginners, get a salon like manicure NOW! * Check out this No Tools Nail Art - 5 Halloween Nail Designs for Beginners!

Welcome back, my hacker novitiates! There are many ways to hack databases, and most of these techniques require SQL injection (SQLi), which is a way of sending SQL commands back to the database from a web form or other input. In this tutorial, we will use SQL injection to get access to the underlying server. So instead of getting access to the database and its data, we will use the database as an intermediary to gain access to the underlying server.

In the last iteration of how to train your python, we covered basic string manipulation and how we can use it to better evaluate user input. So, today we'll be covering how to take user input. User input is very important to scripting. How can we do what the user says if we can't tell what the user wants? There are multiple ways to take input, we can give the user a prompt and take input from them directly, or we could use flags/switches, and take their input before the script is even execute...

G'day, Knuckleheads, and welcome to Episode 22 of my Owner Builder Series. In this video we look at cutting and setting up Verandah / Decking Posts. It's really important that you get thuds right as nothing looks worse than badly set up posts. Check it out and let me know what you think!

I found this cool idea how to get crazy nails for Halloween! The video is in German, but I still was able to follow it. Beside the technic she used, I also used a straw. They looked amazing in the end!

Hi there, Crackers, Welcome to my 7th post (Part-1), this tutorial will explain about the basics of Batch Scripting.

Many of Google's stock Android apps are some of the best options out there—especially now that they've all been made over with Material Design. But generally, as these are pre-installed system apps, they cannot be used on non-Nexus devices.

Laminate floor planks look beautiful and add elegance to a home. However, if a plank gets damaged, it detracts from the beauty of the flooring. Do you call in a professional and pay tons of money to replace the plank? Thankfully, no. There actually is an easy way to replace a damaged laminate plank if you are ready to spend some time and have a little bit of patience.

Welcome back, my amateur hackers! Over the course of the next year, we will be developing our own zero-day exploits. In my first article in this series, I introduced you to buffer overflows, which are the source of some of the most lethal exploits, particularly the "remote code execution," so we are focusing our exploit development here on a buffer overflow.