Welcome to another Community Byte announcement! For the past few Community Bytes, we coded an IRC bot, and hacked it. Then, we created a web-based login bruteforcer! This week we are going to start something a bit different. We are going to start going through the missions at HackThisSite one-by-one each week, starting with the basic missions.

Welcome to Minecraft World! Check out our advanced tutorials and come play with us on our free server.
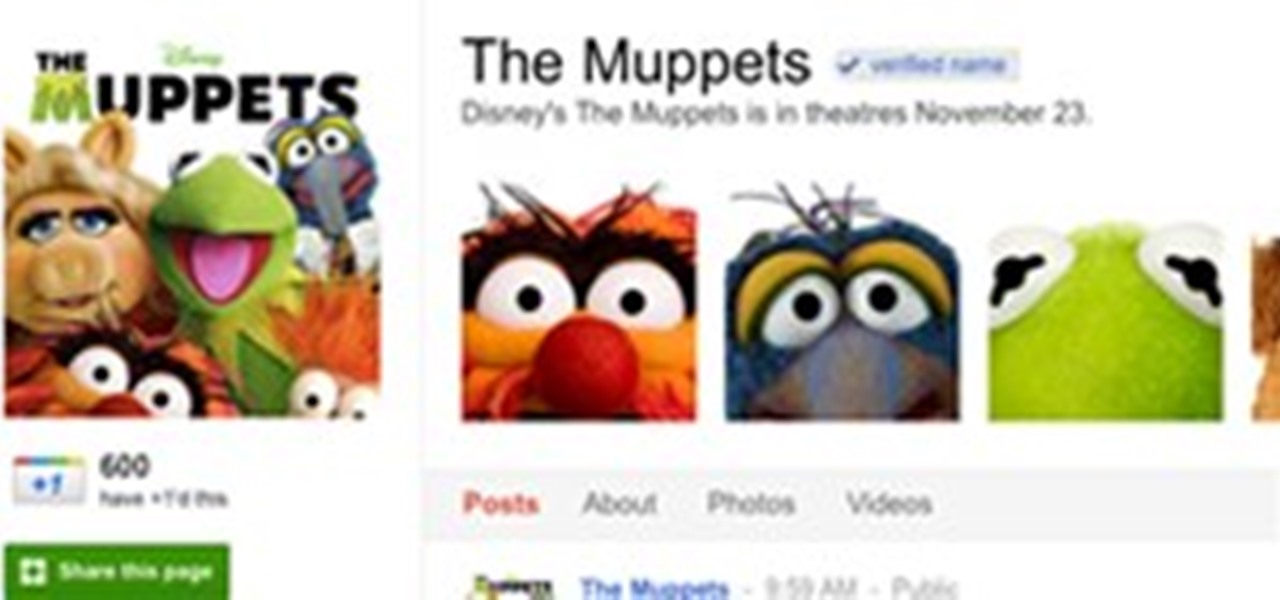
Many companies were disappointed when Google+ rolled out and banned the creation of accounts specifically for businesses and brands. Fortunately, today, Google began rolling out Google+ pages, for them to start connecting with customers and followers. For an example of what a Google+ Page looks like, check out the one for the +The Muppets:

It's another Monday, which means once again, it's time to highlight some of the recent community submissions posted to the Math Craft corkboard. Additionally, I thought we'd take a look at the Mobius Strip.
Stan Parker StanDP~"Avid PC Enthusiast Since 1982..."

Our mission for this week's Community Byte was to create a Python program to crack web-based passwords, like the ones you would see on an email or router login. I wanted it to be universal in the sense that it could be easily modified and adapted to another website just by changing a few variables. That was a success! Even though people weren't on time to the coding session, everything went well.

Welcome to Minecraft World! Check out our advanced tutorials and come play with us on our free server.

Nearly every game takes strategy to win, but when it comes to games like Scrabble and Words with Friends, you've also got to have a lexically inclined mind full of wonderful and weird words. Most start out by learning all of the two-letter words in the Scrabble dictionary, then work their way up to three-letter words. But where do you go from there?

"Google+ is dead." How many times have you read that in the past few weeks? It seems like I can't get away from this notion that Google+, as a social network, is a total failure. Don't feel too sorry for them, though. +Bradley Horowitz isn't worried. In an interview with VentureBeat, he explains, “Six months from now, it will become increasingly apparent what we’re doing with Google+. It will be revealed less in what we say and more in the product launches we reveal week by week.” Indeed, som...

Andrew Lipson builds sculptures based off of Mathematical objects using standard Lego bricks. He has built models of knots, Mobius strips, Klein bottles, Tori, Hoberman spheres (using Lego technic pieces), and recreations of M.C. Escher works.

This is Null Byte's fourth part in a series about fully securing our computers (Part 1, Part 2, Part 3). In our last Null Byte, we went over how to encrypt an entire operating system to protect our data, however, this doesn't fully protect us. In the case of legal extortion, the government can actually make you give up your cryptographic key to your computer so that they can look through it.

The clock is ticking! Pick up some bokeh tips or buy an app—whichever method you choose, you have until Monday, November 7th, 11:59pm PST to participate in this week's Giveaway Tuesdays Photo Challenge. Below, 50 beautiful bokeh photographs to inspire your entry.

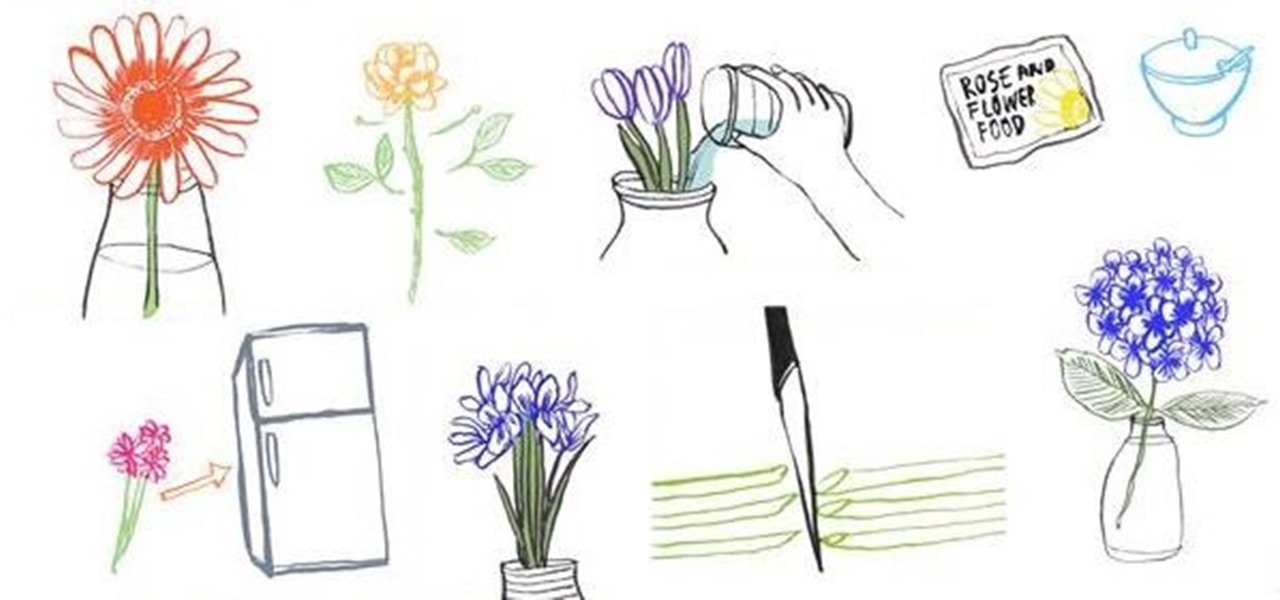
Someone just gave you a bouquet of freshly cut flowers... how do you enjoy them for as long as possible before they start wilting and drooping?

Welcome to Part 3 in my series on protecting your computer from prying eyes (Part 1, Part 2). In today's segment, we will be going over drive encryption using the TrueCrypt program on Windows OS. Drive encryption is a technique that masks your data with a cryptographic function. The encryption header stores the password that you have entered for the archive, which allows the data to be reversed and read from. Encrypted data is safe from anyone who wants to read it, other than people with the ...

In light of this week's Giveaway Tuesdays Photo Challenge, we've posted a thorough guide to experimenting with bokeh photography. Most of the resources require a DSLR camera, and an intermediate understanding of some of the more technical components of photography.

How to use trendlines in Excell 2007 In this tutorial I will show you how to use trendlines in microsoft excell 2007. Trendlines can only be used for certain types of charts.

There's no how-to here, but I think anyone can figure this out. Great idea. I will probably make one for myself.

Torus knots are beautiful knots formed by wrapping a line around a torus and tying the ends together to form a loop. The resulting knot has a star-like appearance when viewed from above. The 36 examples with the least number of crossings can be seen at the Knot Atlas's page on torus knots.

There is a near-infinite amount of ways a computer can be broken into. But that does not mean that there isn't a reason to secure our computers as best as we possibly can. It's like the principles of a secure house. Which are the most secure houses? The ones with locks and advanced alarms, obviously, but not for the reasons people normally think.

Password strength and encryption are important things when it comes to computers. A password is the entire security of your computer, and OS passwords are not hard to break. Most users believe that if you have a password on your computer via the OS, that you are safe. This is not true at all, sadly.

Welcome to Minecraft World! Check out our advanced tutorials and come play with us on our free server.

Why buy a beaded candle holder at the store when you can make one at home? Use this crafty idea to turn your favorite votive candle holder (or shot glass!) into a beautiful, eye-catching, colorful display!

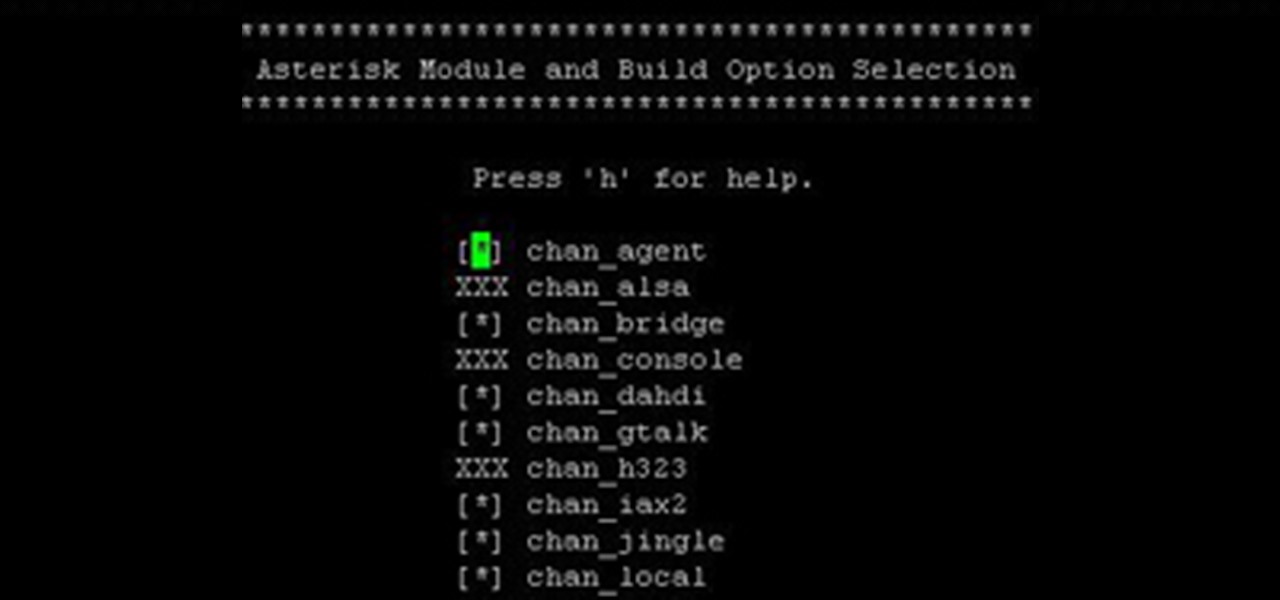
Over the years, I have enjoyed playing with Asterisk. I have found Asterisk to be extremely powerful and fun to play with. There are several books and many scattered how to articles out there, but most are outdated and the information required to build Asterisk from beginning to end can be a bit daunting. I wanted to combine all the steps into a single article and share my experience with everyone. If I have left out any steps please let me know.

This is a tutorial on making a dos-à-dos book by recycling a thin junk cardboard box (dos-à-dos means back-to-back). In the video, you'll see how a cardboard box that has four sides the same size will make a triple-book in one. To make a double-book, just take away one side. To make more than a triple-book, add more boxes to the mix. They're great, fun homemade journals!

Visit the charming historical town of Quimper in Northwestern France. Enjoy ancient architecture, cobblestone streets, a stunning cathedral, and world-famous crepes..

Once you have learned how to do ribbing on double-pointed needles, you will have to learn how to bind off on double-pointed needles. It's really quite easy. Just follow the steps below.

Welcome to Minecraft World! Check out our advanced tutorials and come play with us on our free server.

File recovery on Linux is a bit different than Windows. It requires different software than the Windows counterparts because every OS has their own file system. Windows uses NTFS, or FAT file systems, while on the other hand, Linux uses ext-based file systems. I personally use ext4 file system because it's the latest and greatest ext-journaling system and supports a large level of directory recursion and file sizes, but most installations still use ext2 or ext3. When files are deleted from a ...

I'll admit it, yes, I support protesting. It doesn't matter what my opinions are about any individual protest—overall, it is a human right and the only way to avoid tyranny. We can't deify Ghandi and demonize American protesters. That shows a silly shortsightedness that we can't afford to dabble in.

ZEPHYRS n sing. ZEPHYR gentle breezes 74 points (24 points without the bingo)

In mathematics, a knot is a closed circle in a three-dimensional space that crosses itself multiple times. Since it is closed, it has no ends to tie, meaning you can't actually create such a knot. However, if you tie the ends together after you create a knot in the standard way, you will have something that is close to the mathematical description. In this post, we will explore the creation of mathematical knot sculputures using copper tubing and solid solder wire.

Everyone has deleted a file or folder on accident before. Sometimes people even delete stuff on purpose, only to find out that they needed the files after all. If you're experiencing one of these mishaps, don't worry, file recovery is possible in most cases!

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.

I know, I've used this one, but it looks so creepy!

Welcome to another Community Byte announcement! In the past two sessions, we have coded an IRC bot in Python capable of issuing commands. Since it can issue commands and most of you are new to programming, that project will stay idle for a while. Other commands such as voice and half-op can be easily hacked in via common sense, even if you weren't there for that session.

SHAITAN n pl. -S an evil spirit 60 points (10 points without the bingo)

Welcome to Minecraft World! Check out our advanced tutorials and come play with us on our free server.

It's another Monday, which means it's once again time to highlight some of the recent community submissions posted to the Math Craft corkboard. Additionally, I thought we'd take a look at the process of stellation and make some stellated polyhedra out of paper.Rachel Mansur of Giveaway Tuesdays posted a video from animator Cyriak Harris, which zooms into fractal hands, where each fingertip also has a hand and fingers. A few more details can be found here, as well as some other really cool pic...

Garlic is a great addition to many delicious recipes but it can often be a very time consuming process even just to peel. This article will show you a great trick that will make peeling garlic fast and easy.