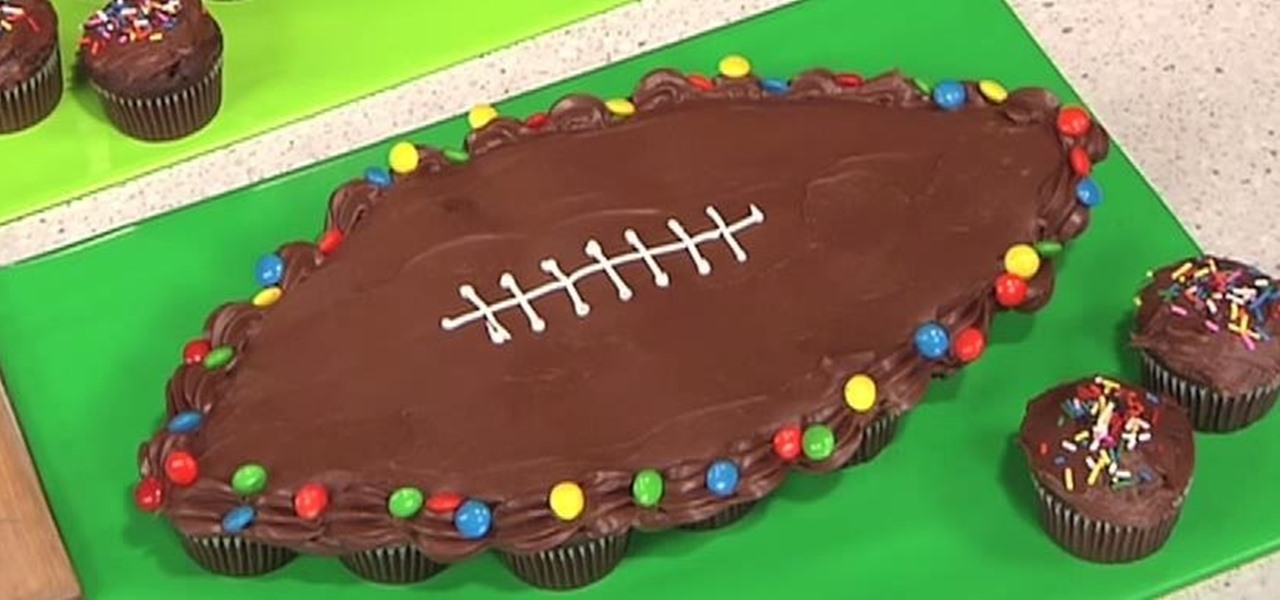Got to be convince someone or a few innocent, young by-standers that the world is ending. Could maybe have a small group of student in an interview situation, maybe in a waiting room. Then you could play reports on news brodcast of mass casualties and disasters happening across te globe. Then after being exposed to that for maybe 10-20 mins they could cause a earthquake and outside there could be building crumbled. Pretend car crashes and causualties outside and smoke machines blowing red smo...

This is a kind of ode to the yellow snowcone. First you need a popsicle, take the wrapper off and the stick and what not. It also could be funnier if the person who's eating the poo popsicle eats the real one, kind of like a before and after shot. Then you need someone to take a poo (its not very hard cause you guys get paid to do it). Pick the poo up, put it on the stick and put the wrapper on it and try to mold it into looking like a real popsicle. Then put it in the frezzer and leave it th...

Use any kind of pickup truck and fill the truck bed with soapy water. I will be the driver and will pull up to a parking space on a visible spot of Rodeo Drive in Beverly Hills near the shopping district. I will be offering $2 baths to the homeless in the back of the truck.Ryan Dunn, Dave, and Ehren will be dressed as bearded homeless guys and walk up to me wanting a bath. They will briefly argue about having to pay because they're homeless but will eventually pay the two bucks, undress down ...

Collaboration is available in many different Apple apps, from Notes and Reminders to Photos, Freeform, and even Files. Now you can add to the list Apple Music, which will let you collaborate on playlists with friends.
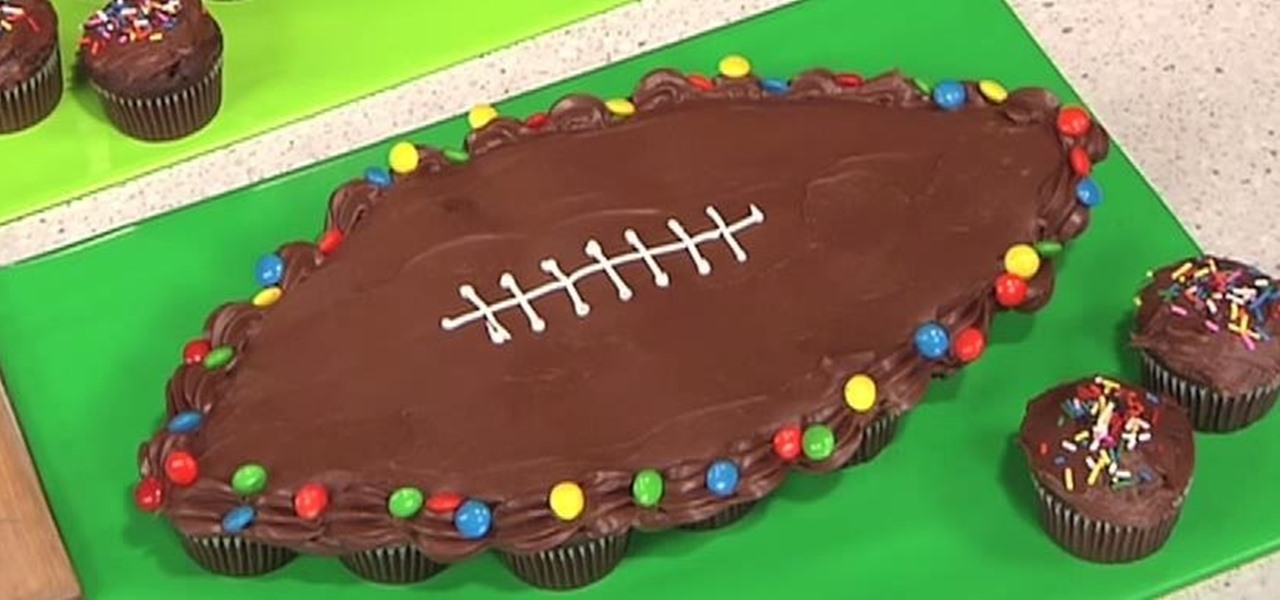
What kind of cake goes best with the Super Bowl? If you guessed a football-shaped cake, you guessed right. In this video recipe, Betty Crocker shows you how to whip up a super easy American football cake that's also a pull-apart cake, because Super Bowl fans don't have time to slice and serve.

The Jack ass Crew has to drink different kinds of liquids blindfolded and they have to guess what it is by the taste. If They Get it right then they get it right but if they don't they have to drink all of that liquid. The liquids have to be different for each person and they could be anything that isnt posoinous or deadly.

Put the guys about 10 stories up on some kind of swing and then put a giant target on the ground and have the dudes all take dumps to see who gets closest to the bulls eye.

The mission to rise above the fray to become a leading player in the augmented reality business is a moving target that depends on innovation, resources, and timing.

An attacker can repurpose public MyBB forums to act as command-and-control servers. It only takes a few lines of code to configure a MacBook to fetch commands and send responses to any website the attacker desires.

Your phone's keyboard is one of the most commonly used apps. Whether you're typing out status updates, sending private messages, or just bombarding everyone in sight with as many emoji as you possibly can, you probably couldn't get by without a good keyboard app.

If there is a major blind spot in the AR space in 2019, it's the impact that blockchain technology will eventually have on the software distributed in AR clouds.

The price of hacking Wi-Fi has fallen dramatically, and low-cost microcontrollers are increasingly being turned into cheap yet powerful hacking tools. One of the most popular is the ESP8266, an Arduino-programmable chip on which the Wi-Fi Deauther project is based. On this inexpensive board, a hacker can create fake networks, clone real ones, or disable all Wi-Fi in an area from a slick web interface.

Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

Mystery is a tricky thing. Used correctly, it can give onlookers the impression that wondrous and perhaps valuable things are afoot. However, once the veil of suspension of disbelief is removed in any significant way, that same mystery can quickly turn into not just skepticism, but outright anger at what may have seemed like an attempt to dupe trusting onlookers.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

Every time you make a call or send a text, you're giving the recipient your phone number. This can be quite the security vulnerability, opening yourself up to scammers, spammers, and the feds. In this how-to, we'll look at what a burner phone is, why you might want one, and how to get started using a free second phone number on your regular smartphone.

Right now is that magical time of year when the general public decides to embrace their inner fattie and get baking in the kitchen. Hello, pies and cakes and cookies and everything carbs. Goodbye, diets—see you in the next year, when you cripple us with unbridled guilt and longing.

Hello ladies and gentlemen, I'm back with another informative(hopefully) article for you all. Once again I would like to apologize for my absence for about a week or so. I have some stuff going on with my life and university and I haven't found enough time to make a fully in-depth article. In this article I'm going to walk you through one of the main networking protocols when it comes to communication across the Internet between programs, aka UDP(User Datagram Protocol).

A spare key is one of those things that never seems like a huge deal until you need it. If you've ever lost your keys, had them stolen, or locked yourself out of your house or car, you know how difficult and embarrassing it can be trying to get your door open.

I was getting kind of sick of ordering delivery pizza (this happens at least 2-3 times a month). It was time to put a spin on gourmet pizza, but I just didn't know what it would be. Without pizza dough or an oven that is capable of creating the perfect pizza crust (I don't have an oven that can go up to a 1000 degrees), I decided I would use potatoes instead. This recipe is elegant enough to serve at a dinner party, but easy enough that you can cook it within 5-15 minutes.

In the first part of this series, we took a factual and technical look at the history of the Internet. I explained how all of these wires and servers got here in the first place. Obviously, a firm did not just create and build the Internet around 1995! Now that we know how the Internet came to be, we can get into the really fun stuff—what the Internet looks like now! Well, that's not quite the network design I was talking about, but it does show what the Internet looked like back in 2007 befo...

If you're always taking blurry and underexposed pics with your mobile device, try using some of the tips below to turn your phone into a valuable photography asset. It doesn't matter if you have an iPhone, Android smartphone, or even a first-gen camera phone... you can still take some beautiful, winning photographs.

Now that 3D display maker Looking Glass Factory is closing in on $2.2 million raised in its crowdfunding campaign for the consumer-grade Looking Glass Portrait device, the company now has a 3D content generator to go with it.

It's incredible what technology can do these days, but sometimes, it gets a little scary. For instance, FaceTime's "Eye Contact" feature, which Apple beta-tested in iOS 13 but released with iOS 14, makes it appear like you're looking right at the camera, even when you're actually looking at your friend on the screen. If you find this artificial trick a bit creepy, rest assured you can turn it off at any time.

Good communication is essential when managing teams and overseeing complex projects. Whether you're developing the latest and greatest app or trying to get ahead of a large data science project, effective communicators are always in high demand.

Navigating a pandemic is new for everybody, which makes staying on top of your finances more important than ever. Fortunately, financial freedom is possible when you focus on budgeting and investing wisely.

While we haven't covered Amazon Web Services, or AWS, on Null Byte before, Amazon's cloud computing platform is ripe for attack by hackers, pentesters, and cybersecurity researchers. It's also an excellent cloud hosting service to build or use vulnerable-by-design AWS setups and frameworks.

Staying inside during the coronavirus pandemic isn't easy for most of us. As important as it is to keep away from others, it can be challenging to keep to ourselves day after day. That's why mobile game developers are stepping in to help; many are making their games free for a limited time, to provide some much-needed fun during scary times.

There are times when leadership is tested. This is one of those times. As government and business leaders around the world are grappling with the unfolding coronavirus pandemic, the real-time responses to the crisis from many leaders have been great and, at times, less-than-optimal.

It's been said time and time again: reconnaissance is perhaps the most critical phase of an attack. It's especially important when preparing an attack against a database since one wrong move can destroy every last bit of data, which usually isn't the desired outcome. Metasploit contains a variety of modules that can be used to enumerate MySQL databases, making it easy to gather valuable information.

Because timing is everything, the latest entry in the location-based augmented reality gaming sweepstakes, Ghostbusters World, has arrived just in time for Halloween.

If you haven't heard, another big OEM has decided to drop the headphone jack. OnePlus, the hero of the people, has just announced that the OnePlus 6T will not have the popular port. With this decision, audiophiles and others are limited to just three big-name options.

After first being announced at Mobile World Congress 2018, the ASUS ZenFone 5Z will finally be coming to the US. Deemed an iPhone X clone by some, there is more than meets the eye when it comes to this flasghip. While it is similar to the iPhone X, in some ways, it improves on the design.

Earlier this month, when Apple announced at WWDC that iOS 12 would include an augmented reality tape measure called Measure, iPhone watchers seemed impressed by the new addition to the company's AR arsenal. Well, just a couple of weeks later, on June 19, it appears that Google remembered it had its own Measure app as well.

Thanks to its advanced cameras, the Galaxy S9 can capture videos at an astonishing 960 frames per second (fps). To put it in perspective, you now have you the ability to record the world around you in ways that previously required expensive professional camera equipment. And that's just the tip of the iceberg.

In the Android community, Samsung's slow updates have long been the accepted norm. With the Note 8's recent Android Oreo update, Samsung completed annual version updates to their 2017 flagship lineup. Now is a great time to look back on how Samsung has fared with updates over the past few years. Hint: It's not pretty.

When traversing the web, you'll regularly come across websites that require you to create an account. With the majority of these accounts, protection is limited to a simple password. Despite this, many people are still using weak passwords such "123456." For these reasons, you really need a password manager, and our research has shown that LastPass is still your best bet.

Chris Brogan is no stranger to using multiple social media platforms all from the comfort of his phone. In fact, not only does he have over 350,000 followers on Twitter, but he's also an avid YouTuber, Instagrammer, podcaster, and blogger.

Last June, Meta began shipping their Meta 2 mixed reality headset, to the delight of many. In September, it was announced that shipping had been delayed until the end of the year. Then it appeared that Christmas would bring something magical when Meta sent out an email four days before the big holiday saying that the Meta 2 developers kits were finally shipping. Unfortunately, having a few on order here at Next Realit,y we are still patiently waiting for ours to arrive.