
News: Religious Tolerance
I write this post as an afterthought on the recent mass burnings of the Quran by U.S troops. Let me lay down the facts first to clear any misunderstandings:


I write this post as an afterthought on the recent mass burnings of the Quran by U.S troops. Let me lay down the facts first to clear any misunderstandings:
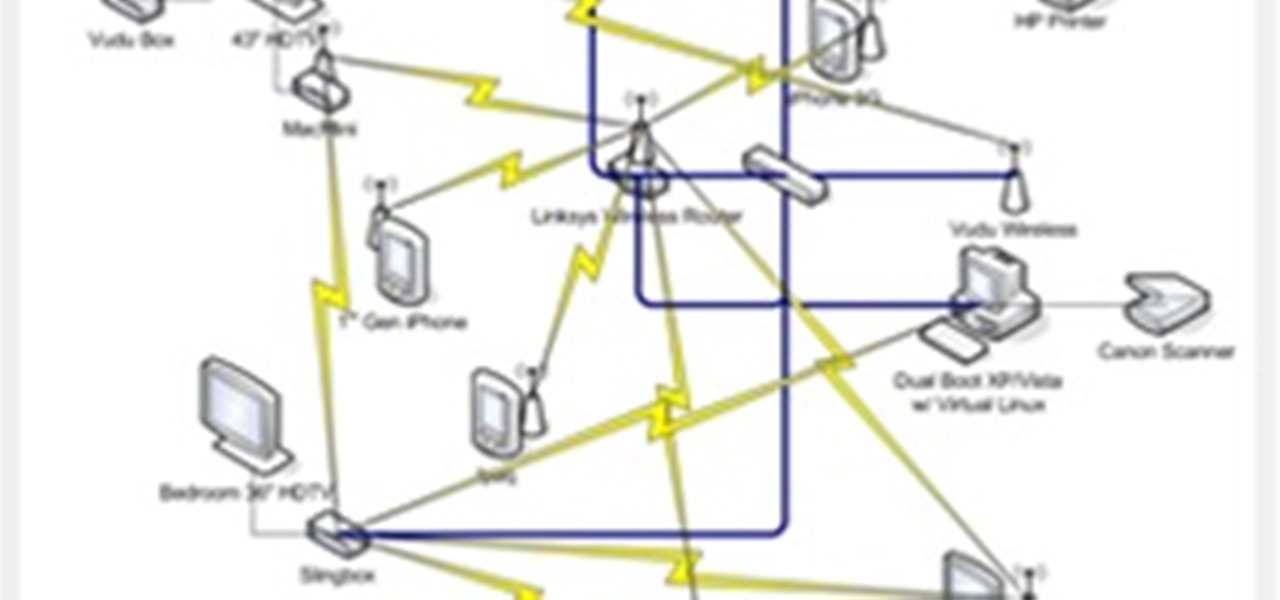
This article will be about setting up a static IP (Internet Protocol) address in Windows Seven. To see whether you should set one up, ask yourself the following: Do I have many computers in the house hold? Do I get connection issues often? Did you answer yes to both? Then you should set one up.
The department of Homeland Security released a list of 'words and phrases' it uses to search social media for terrorism, and whatever else they decide they are looking for that day. Read some of these. A few are obvious "bomb, nuke" and some "target, event" are just down right vague. More reasons to watch what you do on the Internet. You are not the only one watching!

So far, there have been some excellent entries to our WTFoto Stock Photo Challenge, but the battle is not over yet. You still have a couple days left to submit your best find to the WTFoto community corkboard for a chance to take the crown. Remember, we're looking for an absurd stock photo image that nobody's ever seen before. Entries are due Monday, February 27th, 11:59:59pm PST. One second later and, well... I'll probably just let it slide. But 2 seconds later and you're out!

Today's guide is on creating a password protected folder on Windows 7 without any additional software. Yes, you heard that right. No extra software at all! This guide is intended for beginners. But please note, this method should not be used to store financial or otherwise highly confidential material. It might be a good place to hide a planning document for a family member's birthday party or similar occasion where you need to keep something secret temporarily.

A funny one.

I'm starting a series on the top astronomers, with probably about eleven astronomers that I will be covering overall. So, let's start out from the top, with the top most important astronomer. In my opinion, Galileo Galilei is the top astronomer.

There's an old joke about these furry fellows: Panda eats, shoots and leaves.

Welcome to the Mad Science World! Hold onto your radiation-shielded hard hats—we're going to be posting a ton of great how-to articles and videos every week, showcasing the maddest of the mad science experiments on the web. We hope you will be inspired to try these projects at home, but always remember—safety first!

For the limited-free-building contest I gave myself an even more extreme challenge: what could I do with only ONE block type? I chose nether brick stairs, in the gold challenge pack, because stairs are great.

As a web developer, I often read articles about hackers (from the lowly to the knowledgeable) infiltrating websites via the dreaded 'SQL Injection' method and completely taking control, changing, gaining access, or destroying the owner's data. As a fellow web developer, I'm sure you want to know how to protect against it. Well, here it is! In this article, you will find out what SQL Injection is, what you can do to protect against it, and additional recommendations that are easy to do and onl...

In the first part of this series, we learned about darknets, as well as how they came about. But these patches of forgotten Internet are not the oasis of free information you might think. Despite being hidden—or just harder to come across—these networks are no more safe then anywhere else on the 'clear' Internet. The nature of networking and routing means your location is always known in server logs. It only takes one phone call to your ISP with your IP address to obtain both your physical ad...

My palace for a city that has no fewer than 7 100k block structures (will have 15-20 when the central blvds are finished - map link : http://www.minecraftworldmap.com/worlds/_IgOQ ). Today's tip - at the start of the video - how did I put in the lighting for players to navigate the palace hedgemaze (at the start and end of the video).

In this article, I'll show you how you can make your very own bullet/shell bottle opener. All you need is a .50 caliber deactivated round and some workshop tools!

Are you the expert hacker we're looking for? Do you have a great idea for an article on Null Byte? Do you have a passion to write, and more importantly... teach?

Tonight, I saw Mercury for the first time. Mercury is a hard planet to see, even though it is quite bright, because it's orbit is so close to the sun. The angle Mercury makes with the Earth and the Sun is never more than about 25 degrees and most of the time it is much less. As a result, you can't ever see Mercury during the night but at a couple of times in it's orbit you can see it at either dawn or dusk. Right now, Mercury is close to it's greatest eastern elongation and can be seen low in...

Snapshot: 12w08a brings us a few nice things a few things I'm not so sure about and a few things I just hope Mojang doesn't incorporate into the next official update.

Here's a simple and easy addition to your own Jacob's Ladder. If you don't have one, here's how to make a Jacob's ladder.

Looking for some new furniture? Don't know what to do with that small corner in the living room? Do you need more room for storing and organizing, but that tiny gap of space gives you no real freedom of choice?

Accounting and Finance Degree

As many of you Null Byters may know, I was planning on writing this article a week or two ago. Better late than never! So, let's get right to it then—choosing the right Linux distro for your needs.

I'm sure most everyone has some kind of fluorescent light source in their home; those long white tubes that emit a bright white light when turned on, or maybe a few of the CFL power-saver bulbs. These bulbs actually require very little "power" (i.e. a high voltage:almost no current ratio) to emit light. In fact, static electricity is enough to make them flicker. Inside these tubes is a gas, and when electricity flows through that gas, it gets "excited" and produces light.

This parkour map seems nearly impossible for the standard Minecraft player... to build AND to jump! Can you imagine being the one to set the timing for the boats/pistons? I'd certainly go mad...

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

Although +Google Chrome has been getting many deserved kudos for its innovations and speed, many people still prefer to use +Mozilla Firefox as their primary browser. If you’re a dedicated Google+ user, you know that there are many Google+ Chrome browser extensions available to modify your Google+ experience. What you may not know is that there are also Firefox extensions you can use for Google+.

We’ve all been there before. Relentlessly refreshing Ticketmaster and filling in those CAPTCHA codes only to receive the miserable “No tickets are available at this time” message. That’s because ticket brokers with a dozen screens and God knows how many browsers snatch up anything and everything.

Do you need to email your wife your Social Security number? Send confidential business plans to your partner in Thailand? Send your hacker buddies the recovered hashes from last night's breach? Try using GPG, a valuable and easy to use open-source encryption program.

Have you ever forgotten your password and didn't know how to get back on your computer? Or ever had an annoying roommate you wanted to play a trick on to teach them a lesson? Or perhaps overly religious parents who think the internet is of the devil and won't let you read online articles about elliptic curve cryptography applications to C++? Well, then this article is for you!

The art of disguise is a very important skill to master, no matter if you're a hounded celebrity trying to ditch the paparazzi or just someone who'd like to step out of the house without being recognized. If you think simply throwing on sunglasses and a hat is a good disguise, you are so wrong.

There's not much going on this week in the skies above, but there are a lot of conjunctions to take a peek at! And of course, there's the comet Garradd that's still showing its tail to us down here on Earth, so make sure to catch it before it's gone. The rest that's going on this week:

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

Last week, I introduced a project that demonstrated how a BB machine gun could be made out of a soda bottle using only a handful of readily available parts. If you missed it, you can check out that project here before reading on.

Welcome to the WTFoto Stock Photo Challenge, the first of many future WTFoto Challenges to come at you every Tuesday. Every week, there will be a different challenge, and sometimes you could even win a prize. But for today's go, let's just keep it fun...

As you progress in the world of information security, you'll find yourself in situations where data protection is paramount. No doubt you will have files to hide and secrets to share, so I'm going to show you how to use the GNU Privacy Guard (GnuPG or GPG for short) to encrypt and decrypt as you need. GPG is a great open-source version of Pretty Good Privacy (PGP), a similar application used for encryption, but licensing and patent problems led to the development of GPG in its wake.

Hello, fellow Null Byters. Today, with mixed feelings, I want to let you know that this is my last official post as the admin of Null Byte. I've come to the decision that I need to spend more time focusing on my studies. Over the past 5 months, I have enjoyed building this community and teaching people unorthodox methods of doing things, creating things, and hacking them. But I'm also excited to be delving deeper into the studies that brought me here in the first place.

Taking good care of our colon should be one of our capital concerns. Do you know that like the air we breathe, the colon additionally becomes polluted with toxins? Toxin accretion will appear for as continued as you continuously eat. These toxins become the account of a abatement in activity and added problems like constipation, gas, bloating, etc. So now, imagine how acceptable activity could be after these toxins!

This creepy-as-hell vintage jam ad is a WTF as it comes. It's not uncommon to find old ads that are somewhat off kilter. Think you can find a legit ad that's more unsettling than this one? I challenge thee!

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

The stair is considered by many people to be one of the, if not the most, versatile blocks in Minecraft. They can completely change the look and feel of a build and increase its quality. In this post, I will highlight just a few of the options you have for using them.

As my in game name (TehGeekFather) would suggest I tend to like things on the Geekier side of things. Games being one of them. (duh I'm on a Forum dedicated to Minecraft) That being said I am a huge Fallout fan. (NO! not the band. <Sigh>) I'm referring to the post apocalyptic series first developed by Black Isle Studios, the roll playing game division of Interplay, back in 1997. Fallout 1 and 2 were pretty big back then open game play, being able to complete tasks in different ways depending ...