Here's something fun for the Null Byte community to do—a coding competition! This week, I wanted to get everyone involved by offering you all a nice library of possible program types to choose from and try to code. At the end of this competition, all of the submitted programs will be reviewed by the community and myself. The coder that receives the most votes will be dubbed THE BEST.

In this article, I'll show you how to create a simple yet effective way of scaring off intruders. Of course, there are methods around this approach, but it's great for office pranks and general fun. The project requires a little background knowledge in electronics and circuitry, like reading schematics and using a soldering iron.
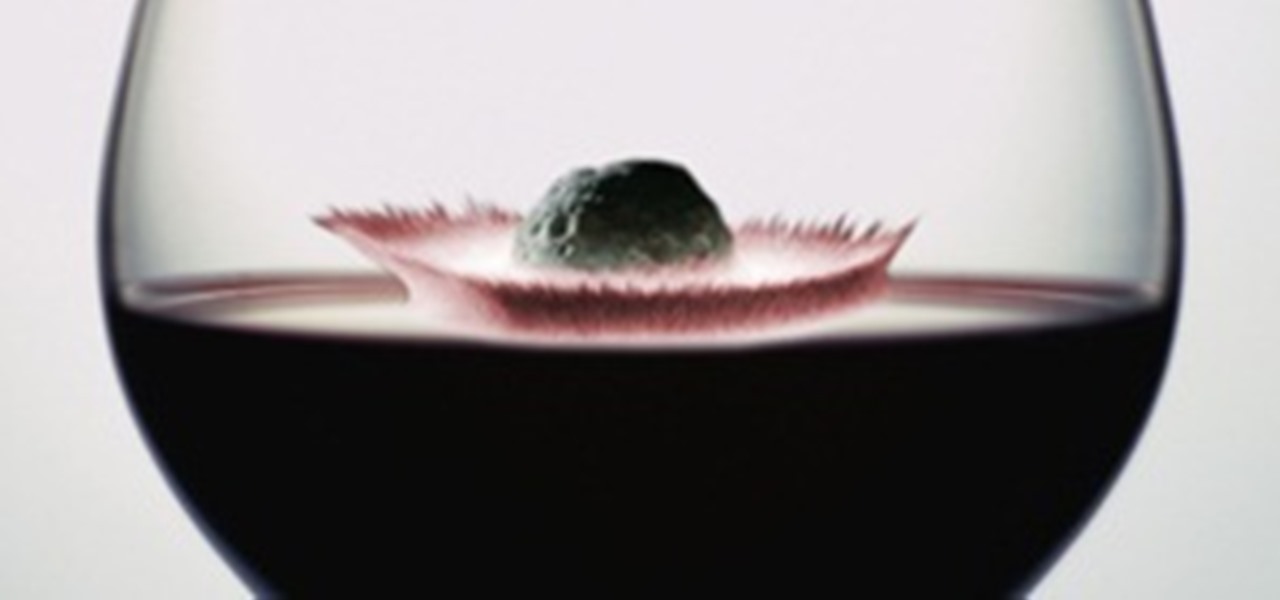
What happens when you combine a passion for astronomy and a love of wine? Cabernet that's out of this world. Literally. It's called Meteorito, and has a berry, nutty flavor with just a hint of iron and nickel. The wine was made by oenophile and amateur astronomer Ian Hutcheon, who runs his own vineyard and established an observatory in Chile called Centro Astronomica Tagua Tagua.

The comet Garradd is almost at its peak now, plus there's plenty more events going on this week, so be sure to observe!

A hacker from Anonymous broke off communication with an FBI agent posing as a Symanec employee after being offered $50,000 to not publish the Symantec pcAnywhere code online. And in a not surprising turn of events... the code was released today on peer-to-peer networks.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. This past weekend, our Weekly Workshop focused on building a suffocation trap. But today, we're going to be covering a different type of redstone trap in Minecraft—one with a 100% success rate (perfect for PvP servers).

You might be sitting there thinking that I'm crazy, but the truth is you're only partially right. You can get free text messaging for life, all for a cheap, one-time fee. But, how can that be possible? An exploit in AT&T's prepaid GoPhones is the culprit behind this sweet, oh-so rare opportunity for exploitation. The exploit grants a lifetime of free texting, assuming that the company stays afloat from now until the end of time.
Yes it’s the 21st century and yes, everyone’s busy, everyone’s connected. Accept it. Move on. Be happy.

With Valentine's Day right around the corner, it's time for some heart-origami! In the video below, see how to fold a winged origami heart. General Information

We'd like this to be one of the last HTS mission announcements, at least for now. As soon as Null Byte finds a server to play with (anyone want to donate one?), we are going to start doing root the box competitions, which is like king of the hill, except you have to hack a server and maintain access. Each server will have numerous known security holes. But for now, back to the normal flow of things...

Another way to make your build really stand out is to choose the right environment. This can either be accomplished by just taking the time to look for suitable land, or by terraforming the world to fit your needs. Like the last one, this tip does not require plugins like Voxel Sniper, yet can really improve the quality of a build.

Last Friday's mission was to accomplish solving HackThisSite, realistic 3. The third mission in a series of realistic simulation missions was designed to be exactly like situations you may encounter in the real world, requesting we help a friend restore a defaced website about posting peaceful poetry.

This is the third part of my electromagnetic pulse series (see Part One and Part Two). By now, I've covered the hardware and general concept of electromagnetic pulse generators, but how exactly do they disable electronics? How can an invisible field of energy have such a catastrophic effect on computers, cell phones, and most any other electronics? I'll be answering all these questions in part three of Making Electromagnetic Weapons.

Lock picking is defined by locksmiths as "the art of opening a lock without the key". There's many ways to accomplish this, but I'm specifically interested in using a lock pick set. Since locks vary in shapes and size, it's better to stick with just one kind of lock at first. Most locks are based on fairly similar concepts, so sharing methods across locks is possible.

Originally made as portable convenience locks, padlocks are known for their cheap, simplistic and relatively secure design. Their construction is made up of a body, shackle and locking mechanism, with the shackle typically assuming a "U" shape to be easily linked to things like fences and chains.

Hey everybody, here is my entry for the medieval building contest. I don't actually care if I win, it was just fun to think about.

I'm sure we've all heard about MSN and Yahoo! Messenger, right? They can be useful, but the setup can be quite time consuming for those who need to use it just once or twice—and the privacy statements are a real bother. For example, we must provide our real details. You could use Fake Name Generator, but if you get caught, you will have your account suspended. I don't have a law degree, but to my understanding the United States recently passed legislation that gives the authorities the power ...

What should you do if you ever get stung by a jellyfish? First things first—do not urinate on your jellyfish sting. Contrary to popular belief, human urine can aggravate any stingers stuck onto your skin, causing more venom to release. Your best bet for relieving your jellyfish sting is to get yourself some vinegar, shaving cream and a razor.
Why Should I care? You should care since the decision they make are based on what us the people want. So if you do not want make your voice or opinion heard you will not get what you want. So as a result will ether mean you will benefit or hate the result?

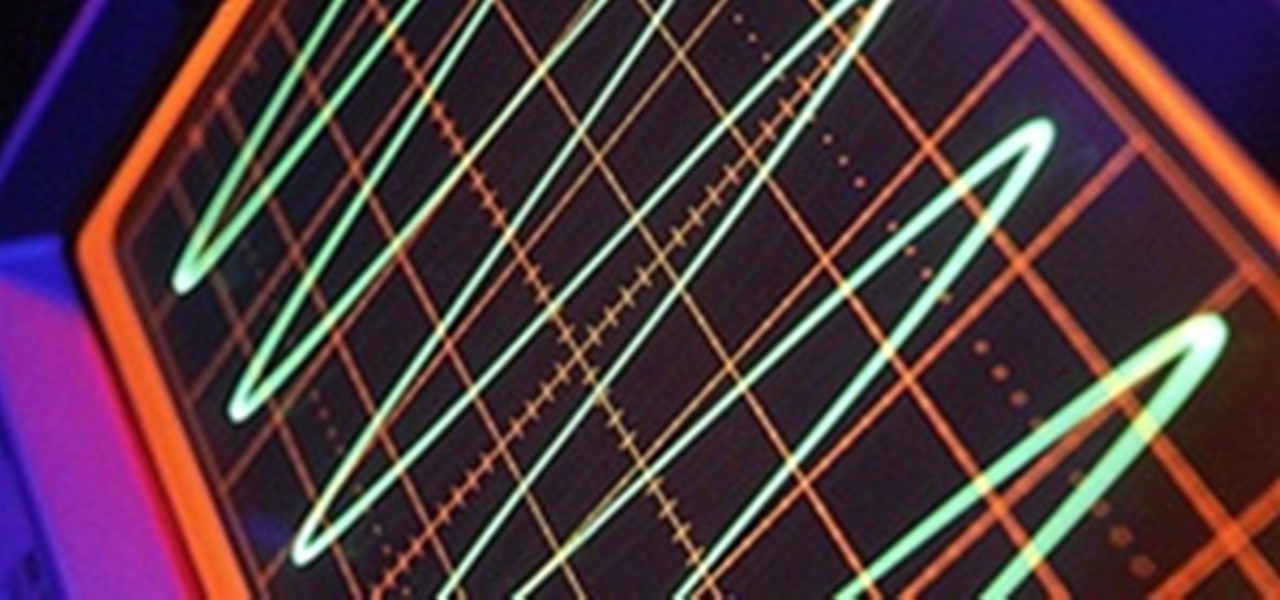
In this article, I'll be showing you how to make a cool visual representation of sound using an old cathode ray tube (CRT) television, a stereo, and a sound source. You'll also need a pair of wire cutters, and a few screwdrivers. To properly understand this project, it's a good idea to learn a little bit about how CRT TVs work. Check out this article on how they work.

Representative Henry A. Waxman is in charge of California’s 30th Congressional district. He is part of the House Energy and Commerce Committee. Ever since he began his career in the government business, he has been involved with health and environmental issues. He represents cities such as Santa Monica, Beverly Hills, Agoura Hills, Calabasas, Hidden Hills, Malibu, Westlake Village and West Hollywood, as well as such areas of Los Angeles as Beverly-Fairfax, Pacific Palisades, Brentwood, Beverl...

Insight Description: In our government class, each student was required to participate in any branch of government from local such as working with your community representatives; state; working with your senator or an organization and federal; which you can entreat in a presidential campaign. The total number of students who participated was Twenty-one and each individual needed to complete at least Ten hours or more.

There are so many hackers around these days, and they are becoming very smart. So smart that they have successfully taken down many government websites. The most recent attack was on the Department of Justice (DOJ). To read about the history of these hackers, check out Wikipedia.

This sweet little knitted heart cushion is easy to create and makes a lovely gift. It can also be used as a sachet. Here are the directions.

Despite starting on Macintosh computers, Avid focused their non-linear video editing programs on Windows systems after stiff competition from Final Cut Pro. But now they're coming back around, with Avid introducing their first iPad version of the Avid Studio home editing software, a miniature version of their industry-geared Media Composer. It will be directly competing with Apple's own iMovie for iPad.

In this article I'll show you how to make a simple IP address notifier. The program will text you your new IP address, in the event that it changes. For those of you with dynamic IPs, this is very useful. I'm constantly frustrated when my IP changes, and it's handy to be notified via text when it happens. To use the program, you'll need Python 2.7 or later, urllib2, and a program called "text" (see this article here to get it).

At some point, we all go from organized to disorganized. Let's assume you are a business executive working in a busy corporate building. Chances are you are going to get a heavy workload and it will impact how clean your workspace is. However, this article is about keeping your desktop clean and clutter free, along with the use of software to find documents you have misplaced.

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. Have you ever fallen victim to a redstone trap? Well, this week's Saturday workshop will give you the confidence you need in order to make your own! This workshop will be centered around creating a suffocation trap with an extra added surprise.
If you are looking for ways/opportunities for you to be politically involved you have come to the right place. Here is a series of links that will take you to a webpage of a location where you can volunteer in and make a difference. In each section you will find:

In this article, I'll show you how to create a simple yet accurate demonstration of the "rising ionized gas" principle. In other words, a transformer, two metal prongs and lots of evil laughter. Remember those large "towers" in the background of Frankenstein movies with a "lightning bolt" rising upwards every few seconds? That's called a Jacob's Ladder; one of the coolest awe-inspiring demonstrations of high voltage. Here's a video of the final product: Materials and Tools

This week's AON might be a little short, but finally, the Garradd comet's peak has come! I picked the Garradd comet to follow because it's a bright and easy-to-follow comet. Be sure to observe it! If you need help finding it, you can find more information here.

How many Facebook friends do you have? The average person on Facebook has around 140 friends while some hit the ridiculous Facebook friend limit of 5,000. Facebook states that its services are for people you know in person. I don't think anyone has 5,000 friends in person, do you? Personally, I don't even think Megan Fox has 5,000 friends in person, so how could any regular person have that many? But that's beside the point.

We're aiming for this to be one of the last HTS mission announcements, at least for now. As soon as Null Byte finds a server to play with, we are going to start doing root the box competitions, which is like king of the hill, except you have to hack a server and maintain access. Each server will have numerous known security holes. But, for now, back to the normal flow of things...

In this article, I'll be covering Triggers and Coils, part two of the series (see part one here). Generally, a simple EMP generator consists of four components; a capacitor, a transformer, a trigger and a coil of copper wire. The transformer component can be varied, but the coil is very important, and must be precisely tuned.

One of the best ways to make a great build is to build around the environment. Fancy plugins like World Edit and Voxel Sniper aren't always necessary. In the real world, people can't just edit the environment to their every whim and need. They have to work around it. Not only does building around your environment help to make your build look nicer, it helps to make it look more realistic. In the above picture, I could only make a small house because I wanted this build to work with the enviro...

Hello and welcome to another InfoSecurity World tutorial. The intent of this article is to teach one how to encrypt sensitive files. When set up correctly with a strong password, it would be almost impossible to hack. Even the FBI have had issues decrypting this software. I'm here to teach you how to create a general encrypted container—not the complex hidden TrueCrypt volume.

Many windows users, if not all, run into a virus infection once in a while. This is unavoidable when using Microsoft's operating system. Without digressing too much, the fact that Windows is such a popular OS with no controlled software sources makes it easy for viruses and malware to spread. And while there's a plethora of antivirus tools for Windows, sometimes infections (such as certain scareware) can disable the install and/or use of antivirus systems and render your OS unusable until cle...

I want to write this article because in my childhood, I had experienced internet stalking which ultimately ended in physical stalking which then lead to several attempted abductions. I have now learned how to use the internet safely, who to communicate with and I've learned how stalkers work.

I have to say, the Xbox 360 controller is the best controller ever created. When I first held it back in 2005, I swore that the dudes working at Microsoft came over and took a molding of my hands because of how great it felt. The thing felt like it was born there.