When building anything of a social nature, be it a local roller derby or softball team, a club dance night for chiptune, or building new technology markets, the community around those ideas are an important factor in helping these things not only come into existence but to grow into something that enlightens everyone involved. The community around an idea can actually make or break these new ventures — and this applies to augmented and mixed reality as well.

Apple just unveiled a red iPhone and iPhone 7 Plus, dubbed the iPhone 7 (PRODUCT)RED Special Edition, to commemorate the ongoing global fight against AIDS. Apple fans the world over are sure to swarm in and gobble up the initial stock shortly after the new color is released at 8:01 a.m. (PDT) on March 24, 2017, so we'll go over some tips to help you secure a red iPhone before it's sold out.

Add antibiotics to the possible list of culprits responsible for honeybee decline around the world. While it may come as a surprise, antibiotics are commonly mixed into feed used by commercial beekeepers to maintain their hives. In a recent study published in PLOS Biology, researchers from the University of Texas at Austin found antibiotics used to treat honeybees may be a contributing factor in individual bee death and colony collapse.

Google is working on something so big they had to name it after an entire galaxy: A new operating system that merges Android and Chrome OS into one unified front.

Welcome back, my budding hackers! As I have mentioned many times throughout this series, knowing a bit of digital forensics might keep you out of a lot of trouble. In addition, digital forensics is a burgeoning and high paying career. Some knowledge and certifications in this field will likely help you land a Security Engineer position or put you on the Incident Response Team at your employer.

Whether I'm in my car or making dinner, I always have music playing. And since I don't like to keep my headphones on me at all times, I end up using my Android's built-in speakers a good portion of the time.

If you've ever seen one of those Samsung commercials from about a year back, you know that the Galaxy S series of phones come with a feature that allows you to do certain things by making gestures in front of your screen. They call this feature Air Gesture, and it enables you to perform certain functions without even touching your phone.

Welcome back, my fledgling hackers! Scripting skills are essential is ascending to the upper echelons of the hacker clique. Without scripting skills, you are dependent upon others to develop your tools. When others develop your tools, you will always be behind the curve in the battle against security admins.

The absence of a physical keyboard is both a gift and a curse. When it was announced in 2007 that the first iPhone would have a touchscreen only, people literally lost their shit. Now, almost 7 years later, you'd be hard-pressed to find a smartphone that still has a physical keyboard.

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

What can't coconut oil do? This edible oil, extracted from the copra or meat of a coconut, has done what most other food, beauty, and health trends have not: demonstrated real lasting power. Indeed, the "superfood" continues to make headlines, with its many uses the subject of debate, study, and fervent support. From the obvious (cooking) to the less so (home improvement), there are likely many coconut oil uses you're not yet aware of.

In this video series, watch as professional guitarist and skilled craftsmen Frank Pope teaches how to build an electric guitar. Learn how to cut the body, install the truss rod, make the fingerboard, make fret inlay, install the bridge, set the wires and electronics, and stain and finish the wood. With this easy step by step tutorial, you can finally get an electric guitar that is exactly what you are looking for. Take the art of guitar playing to the next level with the help of the experts f...

Over the years, the internet has become a dangerous place. As its popularity has increased, it has attracted more hackers looking to make a quick buck. However, as our dependency on the web grows, it becomes increasingly difficult to sever all ties. This means we have to protect one of our weakest points, the password.

A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer inside these routers has become so popular and easy that automated tools have been created to make the process a breeze.

Android has several features built into the platform that improve user experience but require extra attention to prevent a security breach. By modifying these settings, you can drastically reduce the possibility of someone exploiting your device or intercepting information.

Super Mario Run has been one of the most insidiously addicting iOS games to come out in recent years for iPhone. And now, as of March 22, Android users can get in on the fun, too.

Many of our members here at Null Byte are aspiring hackers looking to gain skills and credentials to enter the most-valued profession of the 21st century. Hackers are being hired by IT security firms, antivirus developers, national military and espionage organizations, private detectives, and many other organizations.

Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?"

One of the biggest problems in data security is authentication of data and its source. How can Alice be certain that the executable in her inbox is from the venerable Bob, and not from the not-so-venerable Oscar? Clearly Alice wants to know because if this file is actually sent to her by Oscar, the file might not be a game, but a trojan that can do anything on her computer such as sift through her email and passwords, upload her honeymoon pictures, or even turn on microphones and webcams. Thi...

Today's post is a small go-to guide for beginner programmers in Null Byte. With many of our community members picking up programming from our Community Bytes, it only makes sense to lay out a one-stop guide for your reference. Hopefully this guide will help you make an educated and thoughtful choice on what programming languages you want to learn, and how you want to learn said languages.

On Monday, the social media giant Facebook suffered a massive outage that, as of this writing, is still in effect.

Over the past decade, China tech giant Tencent has invested in several companies with varying roles in the augmented reality industry.

The latest generation of Spectacles aren't AR smartglasses per se, but Snap is intent on demonstrating that the wearables are capable of storytelling powered by augmented reality.

Android updates don't have as many headlining features as they once did, but that's the point. If you keep updating software to add features and fix bugs, you'll eventually reach a point where the main focus is polish. That doesn't mean you can't get excited about a fresh coat of wax.

It wasn't long ago Apple released iOS 13.2 to the masses. The second major update to iOS 13 included 22 new features and changes that added a significant layer of depth to an already feature-filled experience. Apple isn't ready to stop the fun, however, as iOS 13.3, released Dec. 10, has a decent amount of new features too.

Over the last few years, the only thing teased by Magic Leap more than the Magic Leap One itself has been the company's flagship gaming title Dr. Grordbort's Invaders. The game, developed by New Zealand studio Weta Workshop, finally got its debut last week during the L.E.A.P. conference in Los Angeles.

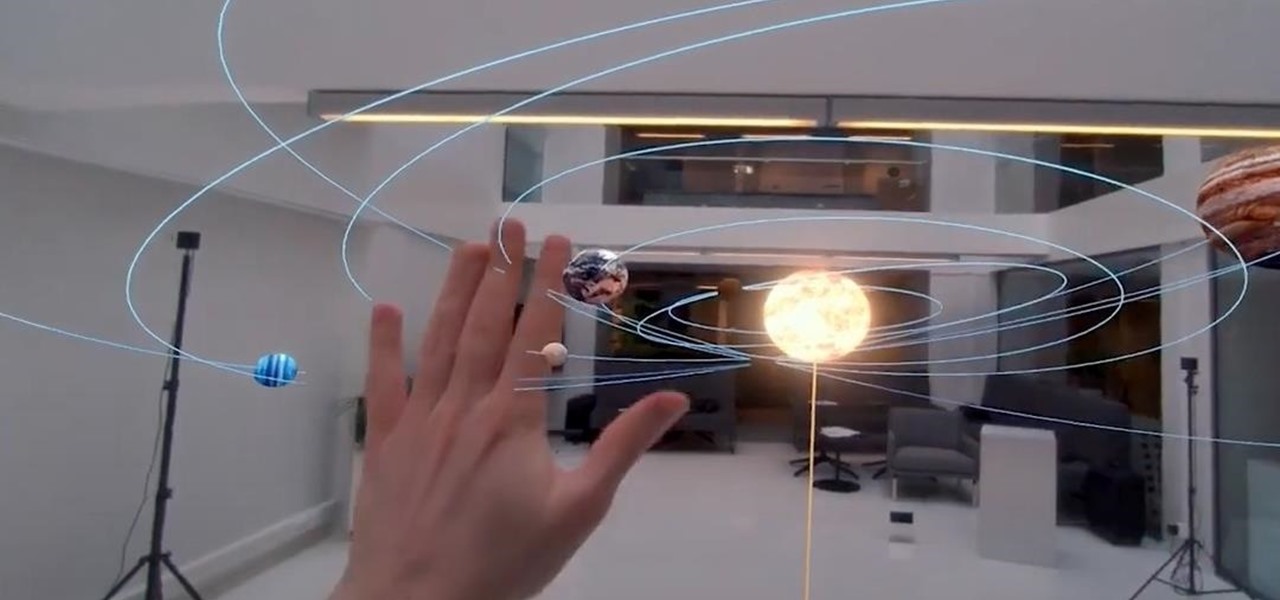
While many of you were off surfing and lounging on some sandy beach or trying to figure out how to balance work with sky-high summer temperatures, I've been talking to all the companies that make augmented reality what it is today.

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.

Google just released the second developer preview of the Android 8.1 update for Nexus and Pixel devices, and even though it's just a point-one release, there are lots of cool changes. Before you run off to join the Android beta program and try the new version, it's worth reading up on what's new.

On July 20, 1969, humans set foot on the moon for the first time. But some say our microbes beat us there. With the Space Age came new questions about microscopic invaders from outer space and concern about where we are leaving our microbial footprints. The questions are even more relevant today.

One major component of Level 4 and Level 5 driverless cars is in very short supply. Venture capitalists and engineers from around the world are racing to fill the LiDAR production, price, and performance void.

With any continuously active software, it can start to become fairly complex after a few years of updates. New features and revisions both get layered into a thick mesh of menu systems and controls that even pro users can get bewildered by. If you are new to a certain application after it has been around for many years, it can be downright intimidating to know where to begin.

Now that Google has announced its new Pixel smartphones, folks who rushed to buy an iPhone 7 might be experiencing a bit of buyer's remorse. The new Pixel and Pixel XL are packed to the brim with cutting-edge features and top-notch hardware, and Google seems to be taking direct aim at the iPhone 7 with its Pixel marketing (and their groan-worthy jokes during the keynote).

Greetings aspiring hackers. I have observed an increasing number of questions, both here on Null-Byte and on other forums, regarding the decision of which USB wireless network adapter to pick from when performing Wi-Fi hacks. So in today's guide I will be tackling this dilemma. First I will explain the ideal requirements, then I will cover chipsets, and lastly I will talk about examples of wireless cards and my personal recommendations. Without further ado, let's cut to the chase.

Since Android is an open source operating system, that means anyone with a little know-how can download, view, and even alter its underlying code base. Manufacturers do it all the time, which is how we end up with skins like TouchWiz and Sense. But when Android's awesome third-party development community gets their hands on this code, we end up with custom ROMs like LineageOS and MIUI.

There's an ongoing debate about whether or not it's safe or even desirable to rinse meat before you cook it. Many fall into the anti-rinsing camp, saying that it's not effective at dislodging bacteria, especially on poultry, as we've discussed before. Meanwhile, some argue that rinsing certain meats, like bacon, could be beneficial since it possibly prevents it from shrinking.

UPDATE: The mod discussed below is no longer available for download. We are looking for an alternative and will update this page when we find one.

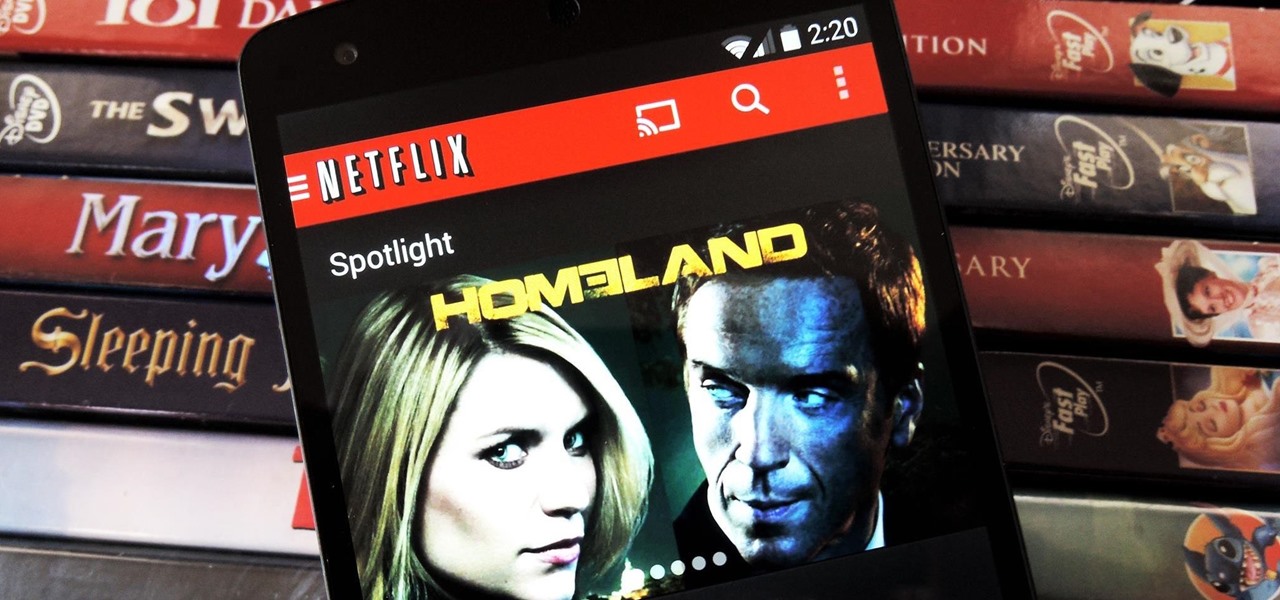
Out amongst the ether of the internet lies a completely different version of the Netflix library you've come to know and love. Because of licensing and rights fees, the streaming media giant maintains separate libraries for each country it services. Ultimately, this means that certain movies and TV shows are only available in certain countries.

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.