Using a Phillips head screwdriver remove the screw under the handle in the back of your iMac. Remove the screws outlined in the picture below. Remove screws 1 and 2 with a standard Phillips head screwdriver. Screws 3 and 4 use a standard flat head screwdriver. After removing the screws, gently pull out all of the plugs. Next holding the clear handle just below the bar code, pull out the section of the iMac.

Brown construction paper comes in handy when you are working at a site. It however can be a pain to access and cut. Watch this how to video to make an easy access rolling paper rack at any construction site. Use it to cover floors and cabinets without having to bend over.

Sometimes the difference between a sprain and a fracture can only be identified with an x-ray. However with the help of this first aid how-to video you will learn to properly treat a sprain. Complete a modified primary survey of the work related accident, access the limb that was injured, and apply ice. These first aid tips will help your workers stay healthy.

The first of a two part series on setting up your linux server and network for external access through your cable modem or DSL. Covers modifying the Linux servers network setting to a static IP address.

A tutorial about why the two page resume isn't appropriate for most IT positions, and how to access a Linux server remotely and change the run level to turn off the GUI.

Once you have access to the Detroit City Hub in Deus Ex: Human Revolution, it's possible to unlock a secret achievement dubbed 'Balls' on the Xbox 360 version of the game. This Giant Bomb walkthrough will help you locate the basketball hoop you'll need to earn the achievement with, and give you a little tip on how to easily get the ball through the hoop.

WPA-secured wireless networks, or WiFI Protected Access, is a form of internet security that secures your wireless LAN from being accessed by unauthorized users. Safer than WEP, or wireless equivalent privacy, WPA still has weaknesses that are prone to cracking - IF, that is, you know what you're doing.

If you'd like to have access to all your files at home without the hassle of spending money on expensive file hosting services or installing foreign software on your computer that could potentially harm it? Well Google has the answer for you, taking over the world one more computer at a time! In this video you will learn how to use your Gmail account and a Gmail Drive shell Extension to gain access to your files from any computer regardless of location!

In this tutorial, we learn how to open & utilize the trunk area of a 2010 Prius. To access the cargo area, open the rear hatch by pressing on the release above the license plate. To keep items out of sight, there is a sliding cover that you can pull back and hook into slots. To open, pull towards you slightly, then reel it in. There is additional space under the floor which can be accessed by twisting the locks and removing from the vehicle. Underneath this, there is a cargo bin, and undernea...

Google is the biggest and best search engine on Earth, and if you are a webmaster and want your website to be a big success it would really behoove you to know as much about how it works as possible. The Google Webmasters series of videos and website were created to teach webmasters, SEO professionals, and others how Google works by answering their questions and giving them insights into how they can best integrate and utilize Google's functionality to improve their business. This video will ...

Vince shows viewers hot to access the Chuck Norris trick on Google. First, you need to open your web browser and go to Google. In the Google search bar type in 'Find Chuck Norris' and click 'I'm feeling lucky'. Make sure you do not click enter but the 'I'm feeling lucky' button to the right. You will get a funny message that says 'Google will not search for Chuck Norris because it knows you don't find Chuck Norris, he finds you'! The suggestions should read 'Run before he finds you' and 'Try ...

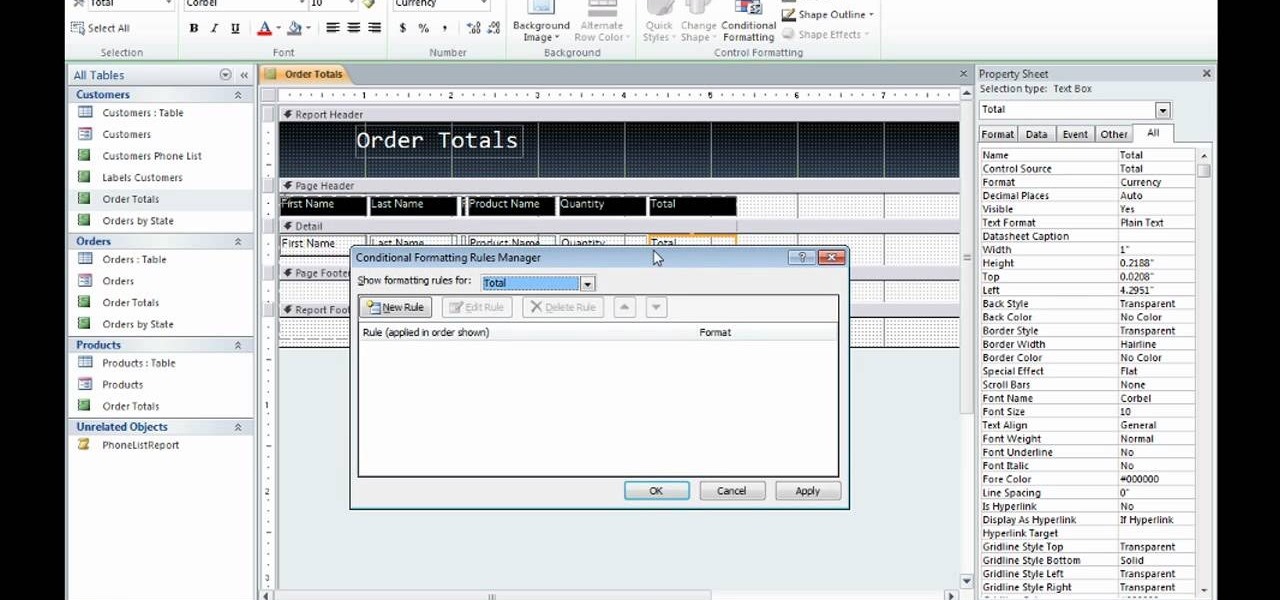
lyndapodcast teaches you how to apply conditional formatting withing Microsoft Access 2010. You click View - Design View. Click the Total tab and you'll notice some highlighted options above. Click Format and then Conditional Formatting. This where you will create rules. Click the new rule button. Now you will see the conditions with drop-down menus. Type in the numbers you want and then select the formatting you want when the rule is true. The preview below will show you how the numbers will...

In this video tutorial, Chris Pels will show several aspects of defining and using master pages in an ASP.NET web site. First, see how to create master pages declaratively using the ASP.NET master page model and learn what information is best suited to a master page compared to an individual content page. Next, see how to programmatically assign master pages on-the-fly in an individual content page. Also learn how to create a base page class which assigns a master page programmatically for al...

It wasn't too long ago that the power menu for stock Android didn't offer much beyond turning the device off, but Google has steadily added more functions, like capturing screenshots and provisioning access to emergency information.

Smartphones are more like computers than actual telephones. Unfortunately, thieves, hackers, and other bad actors know this and are always looking to make money off your personal data. Thankfully, your Galaxy S20, S20+, or S20 Ultra has tools to combat these threats — as long as you know where to look.

The camera system on the iPhone has never been better. Apple's iPhone 11, 11 Pro, and 11 Pro Max sport some of the best shooters on the market. But no level of quality makes up for the fact that shady apps can access your cameras for nefarious reasons. You can take control of the situation, however, and block any app you want from using your rear and front-facing cameras.

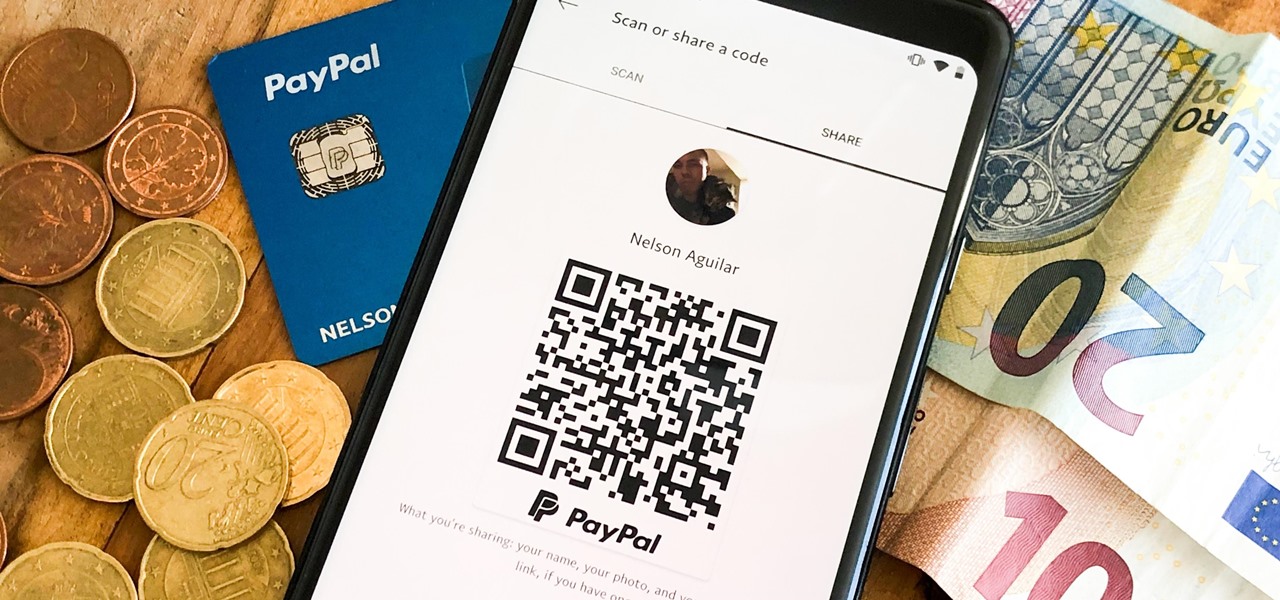
There are many ways to send and receive money on PayPal. You can use an email address, a phone number, or a PayPal.Me link, but if you're standing right next to the person you're trying to pay or get digital cash from, the easiest way, by far, is to use QR codes.

Whether we like it or not, our personal information and smartphones are tied together at the hip. The former needs the latter to deliver a personalized experience that matches our individual needs. This personal data, however, makes your phone a prime target for thieves of all sorts to turn your privacy into illicit profit.

During the keynote at WWDC earlier this year, Apple introduced the latest iteration of its mobile operating system, iOS 12. Despite a thorough demo on stage, Apple glossed over new eye tracking features that use ARKit 2. Developers can now use the TrueDepth camera on the iPhone X, XS, XS Max, and XR to determine where your eyes are looking, opening up incredible new possibilities for new apps.

In iOS, the Control Center is an easy way to toggle settings such as Wi-Fi, Do Not Disturb, and Low Power Mode. Its Android counterpart is called "Quick Settings," which provides much of the same functionality with a few bonuses. If you're curious about how this toggle menu works or miss having it before you made the switch from Android, you can test it out on your iPhone right now.

When BlackBerry made the move to Android OS, they were aware of the limitations it presented. Unlike with BB10, they didn't create the operating system and would have to deal with the vulnerabilities already included. As a result, they added numerous security enhancements, and at the heart of this is DTEK.

Many operators use elevators to control access to particular floors, whether it be the penthouse at a hotel or a server room in an office building. However, the law requires them all to have a fire service mode, which gives emergency access to restricted floors, and a hacker can use that to bypass security altogether.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.

The threat of an evil access point has been around for a long time, and with the rise of open public Wi-Fi, that threat is often overshadowed by how comfortable we are using third-party Wi-Fi hotspots at coffee shops and public spaces. While we've shown an evil twin attack using the Aircrack-ng suite of tools, MitmAP is a Python tool to configure custom APs for many types of wireless attacks.

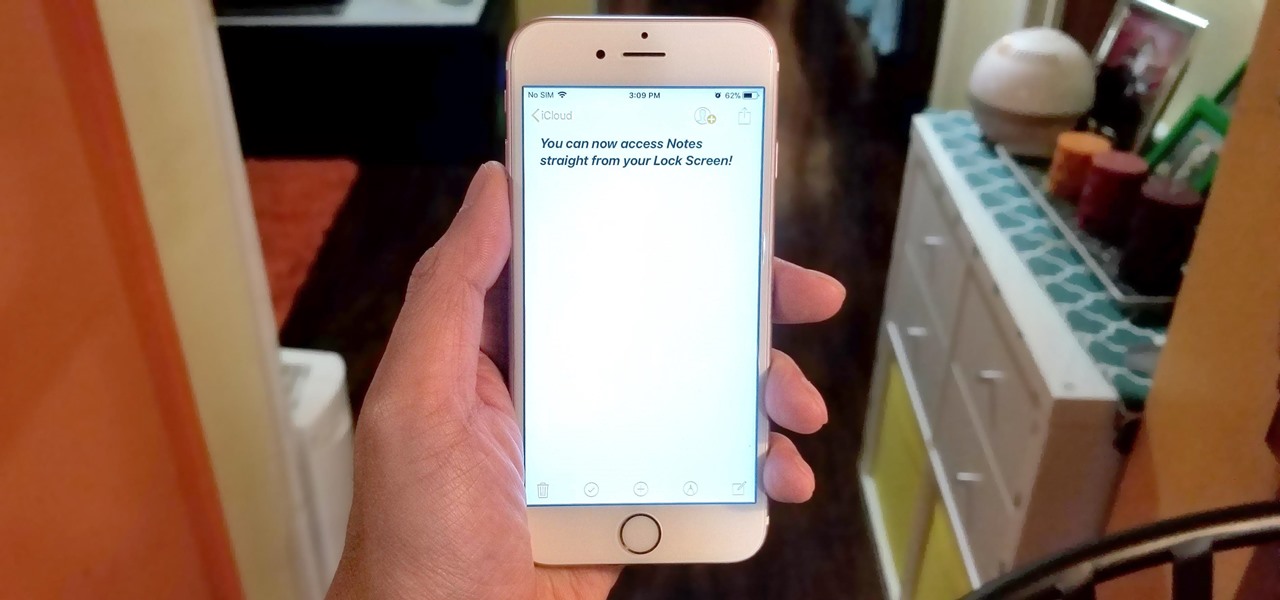
All to often, many of us are struck with a brilliant idea out of nowhere, only to forget about it moments later thanks to the distractions of daily life. Sometimes, the actual process of jotting these ideas down in our iPhones can be a holdup, as the idea we want to record fades from memory before we can even unlock our devices and open Notes to get started.

AirDrop is an underrated feature that lets you to quickly transfer files like songs and photos via Bluetooth and Wi-Fi from your iPhone to Macs and other iOS devices. It's been a staple in the Control Center ever since iOS 7, prominently displayed for easy access. However, with iOS 11, that quick access to AirDrop has seemingly disappeared.

Is the Home button the main reason you haven't pulled the trigger on a new iPhone? Are you worried that you'll miss its functionality too much, or that simple things like accessing your home screen will be too hard? Well, don't worry about any of that, because Apple came up with some intuitive gestures that makes the old Home button seem clunky and outdated once you get used to things.

So, Nintendo's never really been good at the whole online thing. Most of the time, we forgive them, because they are masters at creating games meant for solo play or local multiplayer. Sometimes, though, that doesn't fly. Take a game like Splatoon, for instance. Although it redefines the genre, it is still, at its core, a shooter. Shooters are meant to be played online, with your friends, yelling at each other over voice chat.

The peaceful, pastel and doily-filled world of Pinterest is my oasis. My account conveys who I want to be and what I want to accomplish, so the idea of someone hacking it and ruining my favorite escape for me is heartbreaking. Fortunately, Pinterest has updated its security, implementing three new features to hack-proof your account.

Over the course of the past century or so, media consumption has gone from a few readers enjoying their local print publication to billions of users viewing countless hours of video across the globe each day. This was a gradual evolution at first, but recent advancements in mobile connectivity have sent us into a climb the likes of which we have never seen before.

Okay, so you finally got around to rooting your Android device—now what? Well, to get the most out of your Superuser status, you'll need to find some good root apps, which will allow you to easily add features, reduce battery drain, remove ads, and much more.

If you're completely new to Android, you're in for a treat with all of the software tweaks and customization options that your smartphone or tablet offers out of the box. But if you really want to take things to the next level, the ability to mod your device expands exponentially when you're rooted.

Quite a few things have changed with Windows 10, but one of the more central features that has received a makeover is the old Windows Explorer program, which has been renamed to File Explorer in this version.

Welcome back, my tenderfoot hackers! Hacker newbies have an inordinate fixation on password cracking. They believe that cracking the password is the only way to gain access to the target account and its privileges. If what we really want is access to a system or other resources, sometimes we can get it without a password. Good examples of this are replay attacks and MitM attacks. Neither requires us to have passwords to have access to the user's resources.

Google's Chrome Remote Desktop, which allows for remote access to your personal computer from your smartphone, has been out for almost a year now. Sadly, it's only been available for Android devices—until now. So, if you got an iPhone (or other iOS device), you can now access and control your computer directly from your smartphone or tablet just like with Android.

Lending someone your phone to make a call is always an awkward situation, as you closely monitor them to make sure they stick to a phone call rather than wandering off into private applications like your photo or messaging apps. You don't necessarily want to eavesdrop on their conversation, but trusting people with your phone is difficult, especially if you have some risqué or embarrassing pictures stored on it.

This video will show you how to protect others from accessing saved password on Google Chrome. Saving account passwords in browsers are useful for time saving as well as threatening for malicious activity. This is dangerous for security. So you must protect your accounts detail from others to secure your browsing. Watch the video and follow all the steps carefully.

We upload photos in our Facebook albums. If we want to make a slideshow of them online then watch this video. This video will help you how to create slideshow from Facebook images online. Here we take a website photosnack.com. Other websites are also available. See the video.

The newer Graph Search in Facebook can help you find friends in specific cities, photos of a particular subject, restaurants that your friends liked, and a whole lot more. One thing it can't help you with just yet is searching public posts on Facebook, which you could do in the previous search version. Actually, some users do have the option to search public posts with Graph Search, but it's very limited and doesn't include me. If you're like me and don't have access yet, there is a workaroun...

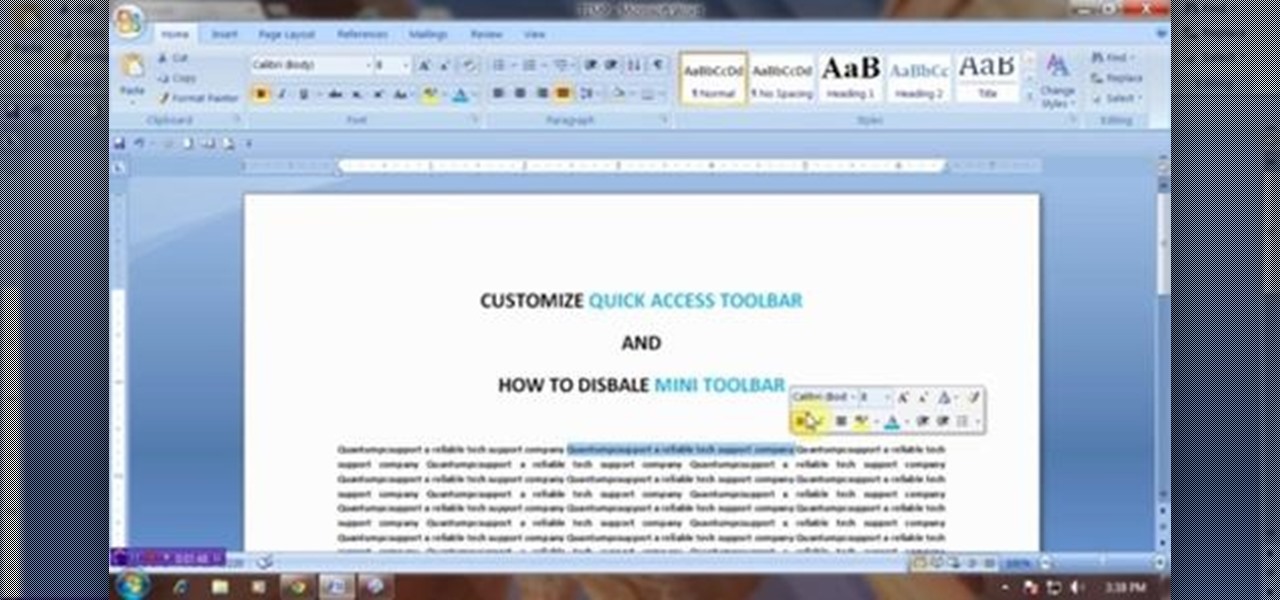
This video will show you how to customize quick access toolbar and delete mini toolbar in MS Word 2007. These 2 things are very useful. Watch the video and follow all the steps to employ it yourself.