A few months ago, iOS 12.1 came out with a handful of useful new features, and iOS 12.2 goes even further. While some of iOS 12.2's new features for iPhone are much welcomed, there are some that we'd be better without.
Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

When it comes to digital security, one of the best ways to protect yourself is to use two-factor authentication. Most apps these days support it, including Facebook, a site where the more privacy you can muster, the better. However, of the two 2FA options available for Facebook, only one should be used as the other will share your phone number with the world, a huge privacy concern.

In 2018, augmented reality went from the vague promise of interesting things in the near future to tangible developments in software and hardware, proving that immersive computing is indeed the future.

Every photo you take is brimming with metadata such as iPhone model, date and time, shooting modes, focal length, shutter speed, flash use, and geolocation information. Share these pictures with friends, family, or acquaintances via texts, emails, or another direct share method, and you unwittingly share your location data. Even sharing via apps and social media sites can compromise your privacy.

If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for a birthday, Christmas present, or other gift-giving reason, these also make great gift ideas.

The new iPhone XS and XS Max have more issues than just their hefty price tags. Customers have only had the phones for a handful of days, but some are already complaining of cellular and Wi-Fi connectivity issues on both models. If your experience is the same on your XS or XS Max, there are steps you can take to get your iPhone reliably back online.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

In a surprising twist of expectation management, Magic Leap managed to not only ship but deliver the Magic Leap One I ordered on Wednesday by 4 p.m. PT on the same day.

Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than others, and a little Python could be used to brute-force any weak hashes to get the passwords they were created from.

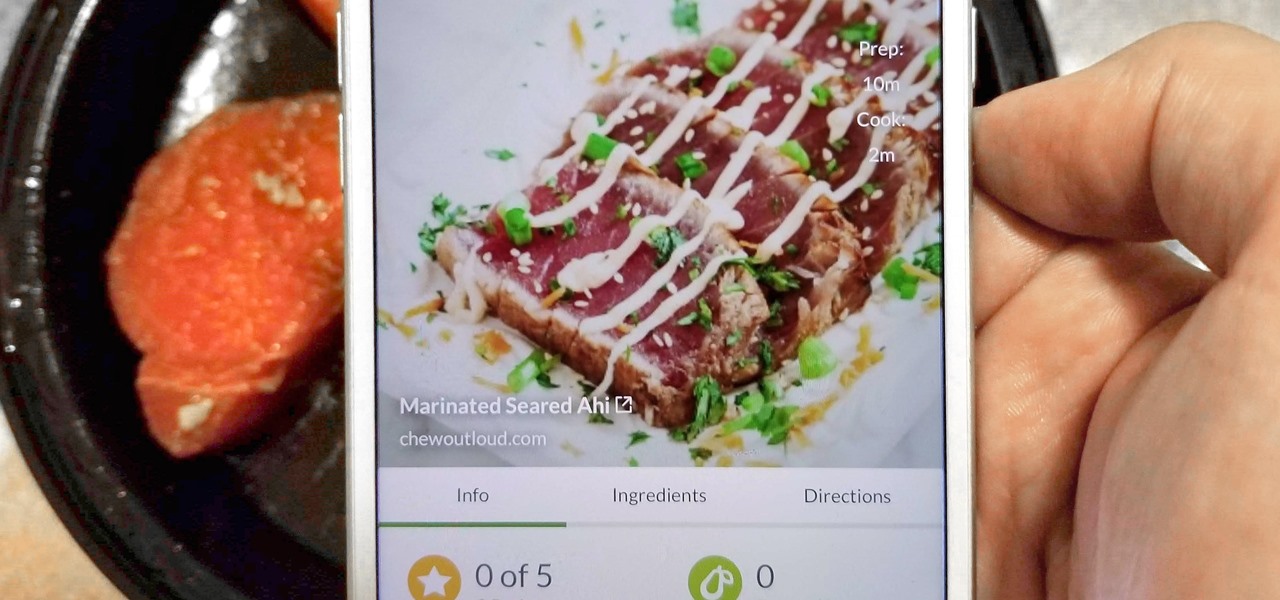
With Tasty dominating Facebook videos and online cooking flourishing, it can be cumbersome to keep track of all your recipes. Someone might send you something, and storing it in an app like Pocket is like jamming all your school papers in one folder — it just isn't practical. Fortunately, there's a better way to catalog your recipes so you can always have them on hand.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

According to Google at their 2018 I/O conference, Google Assistant is now available on over 500 million devices. Now that the assistant is available on iPhones as well, Google has to give iOS users a reason to switch to its assistant over the built-in Siri. Today, Google has eight more reasons for users to do so.

The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you need to have a solid grasp of ... you've guessed it ... SQL.

In the Android community, there's a lot of discussion about how display notches should be used. For some, hiding the notch is more appealing, but others feel that hiding it wastes screen real estate. Well, Essential just provided another solution that should satisfy both sides.

One of the best gifts that someone with an iPhone can receive is a paid app, hot new movie, bestselling album, gift card, or anything else in iTunes, Books, or the App Store that costs money. Even if it's a small $0.99 game that you heard a friend talking about, a gesture like this can go a long way. Gifting apps and media is now easier than ever, even if you don't have an iOS device yourself.

Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial gain.

Deleted bank statements and private photos are still within an attacker's grasp, so don't think that emptying your recycling bin is enough to keep your files from coming back to life. It's possible for a hacker to recover compromising files and images from a backdoored computer completely without the victim's knowledge.

With Gboard, Google created a keyboard with more functionality than just inputting words. The app includes features such as GIF search and live text translation, but it gets even better when you let it learn more about you. With this data, Gboard grows from a good keyboard to one that can complete your sentences.

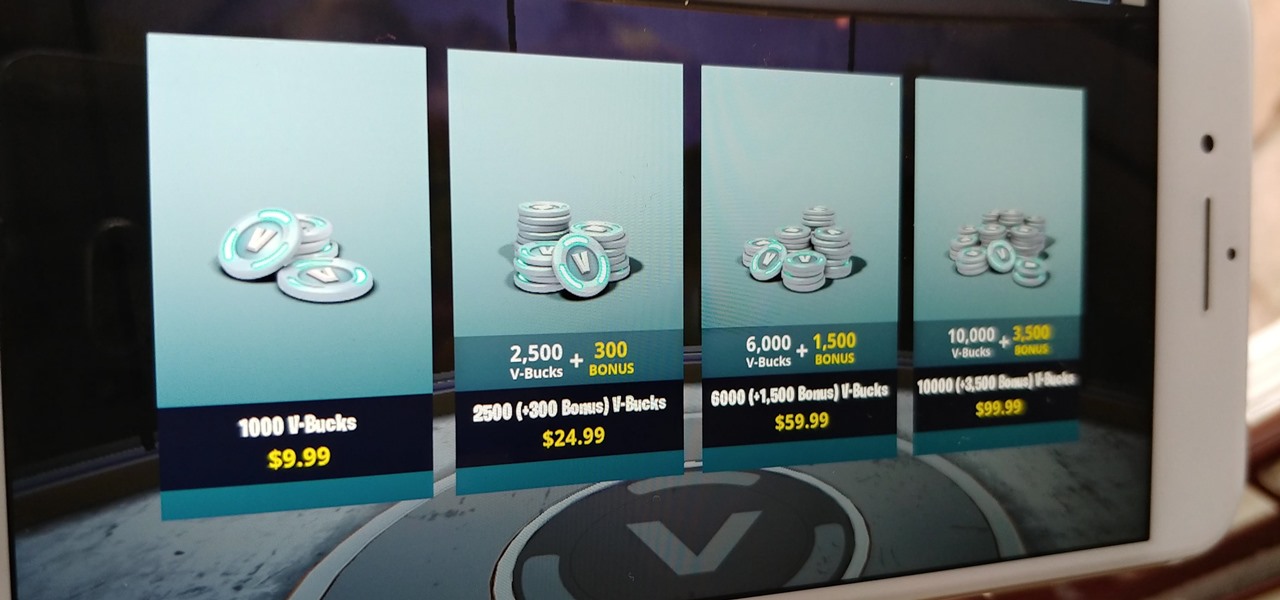
Thanks to its free-to-play strategy, many items in Fortnite Battle Royale require V-Bucks, the in-game currency. You can purchase V-Bucks with real-world money, but many would rather earn V-Bucks instead of getting nickeled and dimed by micro-transactions. While limited, there are a few ways to earn free V-Bucks in the game.

In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greeting card being delivered to our intended target.

Starting your morning right is an essential first step to a productive day. Whether you're running late, rushing to catch up on the day's news, or lagging behind with early emails, little hiccups like these can have a trickle-down effect and ultimately ruin your day. Like with many problems, though, your smartphone can help.

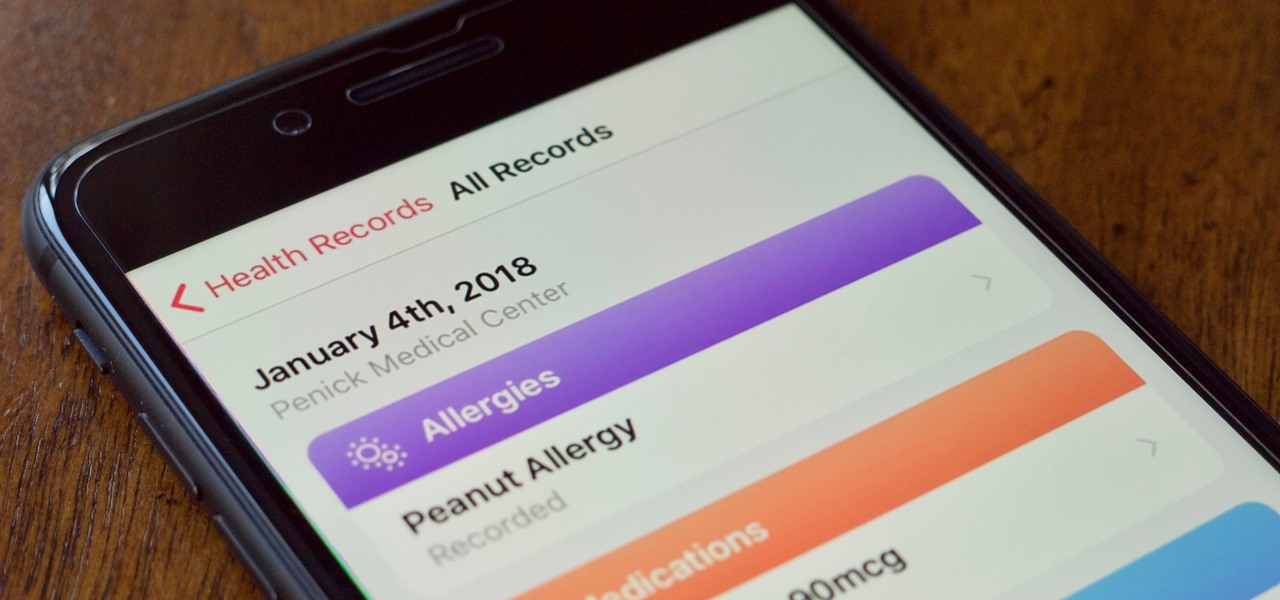
Mobile phones are not only essential for work and communication, they're quickly becoming an integral asset to our health. Your iPhone can store valuable data about fitness, nutrition, heart health, and so much more. And since iOS 11.3, your iPhone can even import a list of allergies, medications, immunizations, hospital visits, and other health information from your doctor or hospital.

This is a very exciting time for mixed reality developers and fans alike. In 2017, we have seen a constant stream of new hardware and software releases hitting the virtual shelves. And while most of them have been in the form of developer kits, they bring with them hope and the potential promise of amazing things in the future.

With the V30, LG has really delivered an amazing smartphone that hits all the major features consumers want. Amazing camera, beautiful edge-to-edge display, great battery life, water resistance, and smooth performance — there isn't much not to like about the LG V30. Unfortunately, it does suffer from heavy bloatware thanks to the carriers. The good thing is, unlike in the past, you are not stuck with it.

So much information exists online that it's easy to get lost in data while researching. Understanding the bigger picture can take a lot of time and energy, but narrowing the question to one that's easy to answer is the first step of any investigation. That's why analysts use open-source intelligence (OSINT) tools like Maltego — to help refine raw data into a complete understanding of a situation.

Since its debut, retro thriller Stranger Things and its characters have become ingrained in our popular culture — especially the telekinetic Eleven. For cosplayers, it didn't take long before they grabbed their boxes of frozen Eggo waffles, blonde wigs (or bald caps), and pink smocked dresses to transform into El herself.

Apple officially unveiled the long-awaited iPhone X, its tenth-anniversary edition iPhone, on September 12. With preorder and release dates just around the corner, you'll want to brush up on all things iPhone X to make sure you get your hands on one as soon as possible. After all, preorders start Friday, October 27.

Clumsiness is the great equalizer when it comes to smartphones — it makes no distinction between the most expensive flagship handset and cheaper mid-range models. A hard drop onto pavement will usually result in a shattered screen, regardless of how pricey your device is. And with a smartphone breaking every two seconds, we're truly our own handset's ultimate nemesis.

In the case of rotting food, microbes are not our friends. Now, scientists have developed a new food wrap coated with tiny clay tubes packed with an antibacterial essential oil that can extend the shelf life of perishable food, so we can waste less and eat more.

People infected with HIV take many different types of pills every day to decrease the amount of virus in their body, live a longer and healthier life, and to help prevent them from infecting others. That could all be in the past as new clinical trials testing the safety and effectiveness of a new type of treatment — injections given every four or eight weeks — look to be equally effective at keeping the virus at bay.

More prescriptions for antibiotics are written for ear infections than any other type of infection. A new study comparing the incidence and causes of ear infections in children between the ages of six months and three years found that the incidence of ear infections over the last decade has dropped significantly since the 1980s.

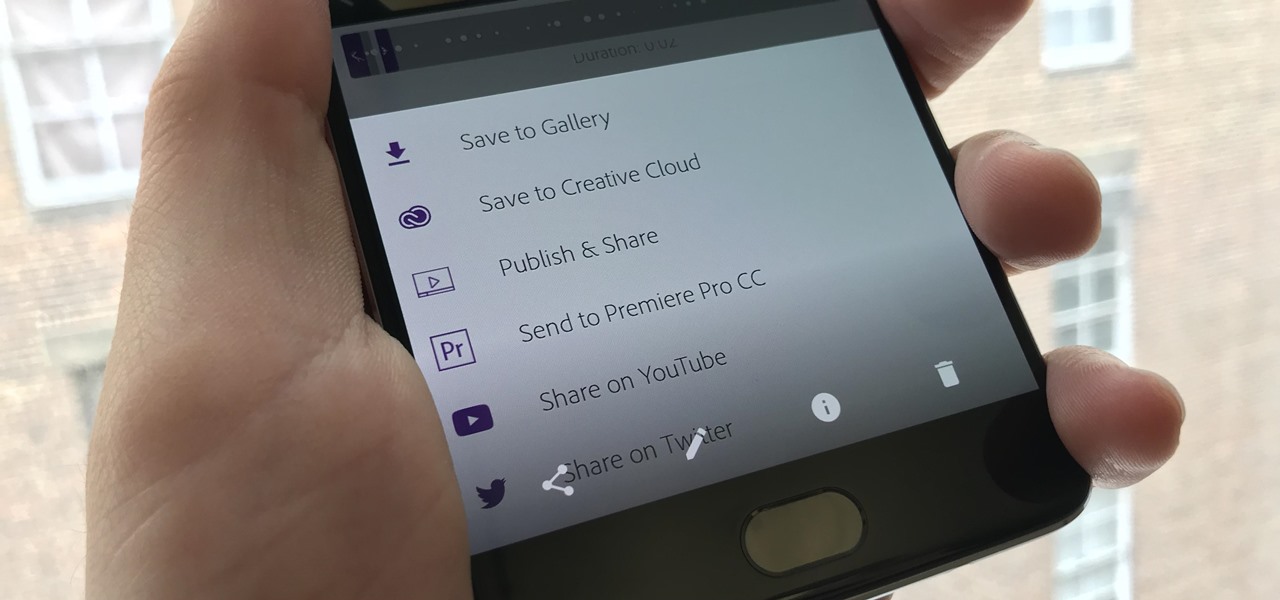
If you've taken the time to edit a video on your iPhone or Android phone, you probably have a purpose for it. Maybe you want to share it to YouTube in hopes of making the next viral sensation. Maybe you just want to save the video to your phone to show off to friends and family when you can.

When you first set up an iPhone, you'll be prompted to create a six-digit passcode to unlock your screen and access certain system settings. If you skip this step, you can always go back and create one, which we highly recommend. Without a passcode, everything on your iPhone is accessible by anyone who gets their hands on it — nosey friends, hackers, thieves, local law enforcement, the FBI — and you don't want that, do you?

Type 1 diabetes is an attack on the body by the immune system — the body produces antibodies that attack insulin-secreting cells in the pancreas. Doctors often diagnose this type of diabetes in childhood and early adulthood. The trigger that causes the body to attack itself has been elusive; but many research studies have suggested viruses could be the root. The latest links that viruses that live in our intestines may yield clues as to which children might develop type 1 diabetes.

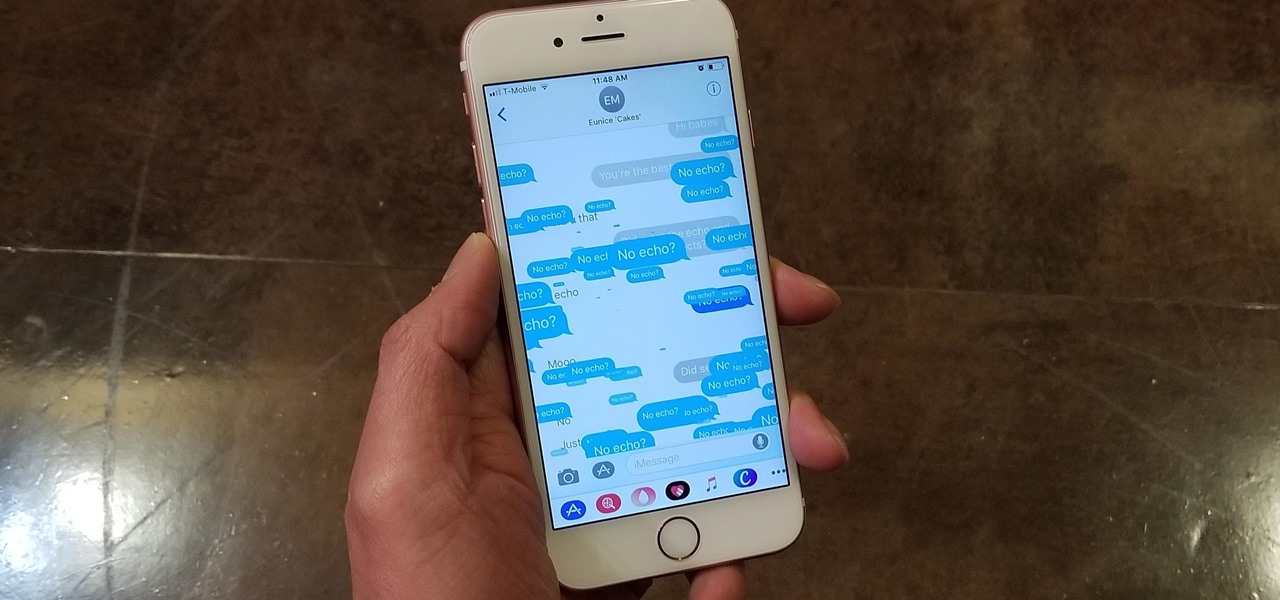
Apple gave the Messages app a massive makeover with iOS 10, with a slew of options that made iMessages on the iPhone a lot more fun. While not quite as comprehensive, iOS 11 builds upon that success and makes the app more user-friendly and all-inclusive.

You can send and receive money from your iPhone using Venmo, Square Cash, Facebook Messenger, and even Snapchat. There's also Zelle, which offers quick-pay solutions in major banking apps such as Bank of America, Chase, and Wells Fargo. However, Apple has a built-in system to transfer money, with person-to-person payments being available in the Messages app ever since iOS 11.2.

We can add one more health effect of our gut bacteria to the growing list. Researchers from the UK have just reported that the gut microbiota plays a role, both directly and indirectly, on the toxicity and efficacy of chemotherapy. Their findings are published online in the journal Nature Reviews Gastroenterology & Hepatology.

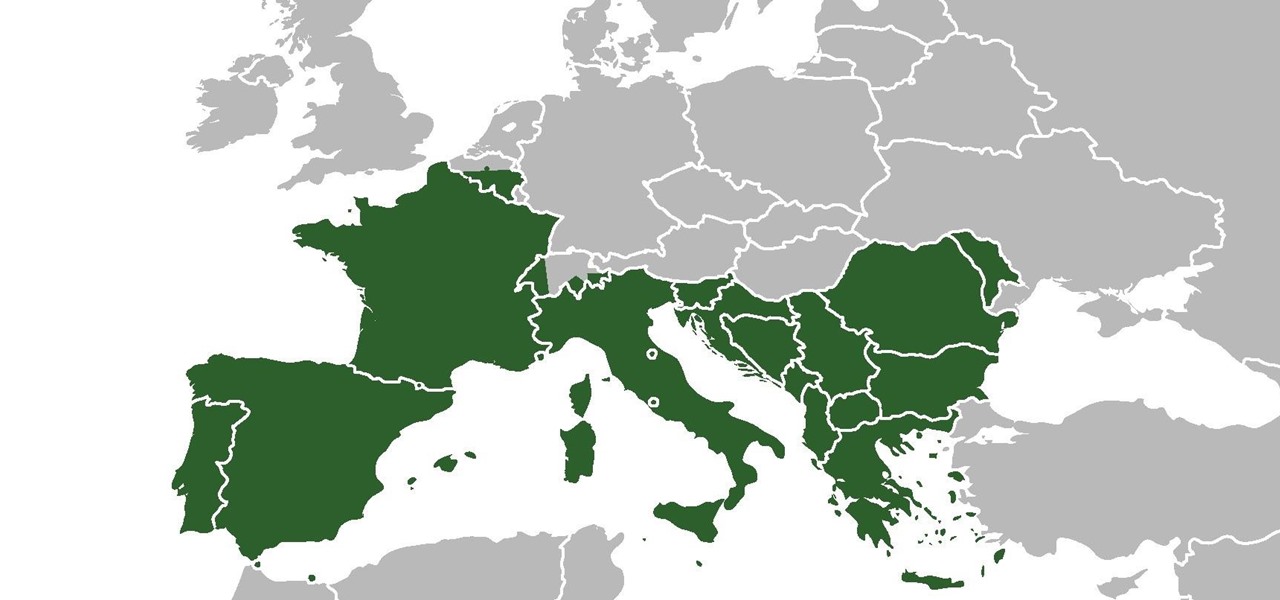
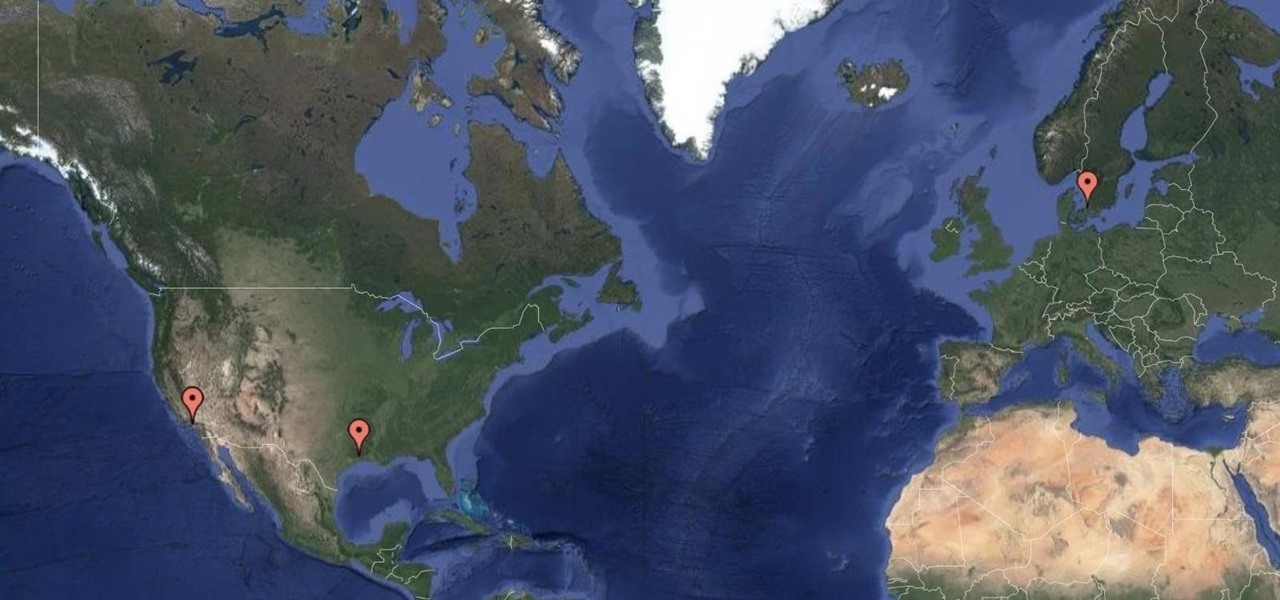
The beauty of southern Europe won't protect it from invasions of disease-carrying ticks and mosquitoes—in fact, the Mediterranean climate and landscape may be part of the reason the bloodsuckers are expanding there, bringing unique and terrifying diseases in their wake.

You can get eggs and high-quality compost from backyard chickens—but you can also get Salmonella.