You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.
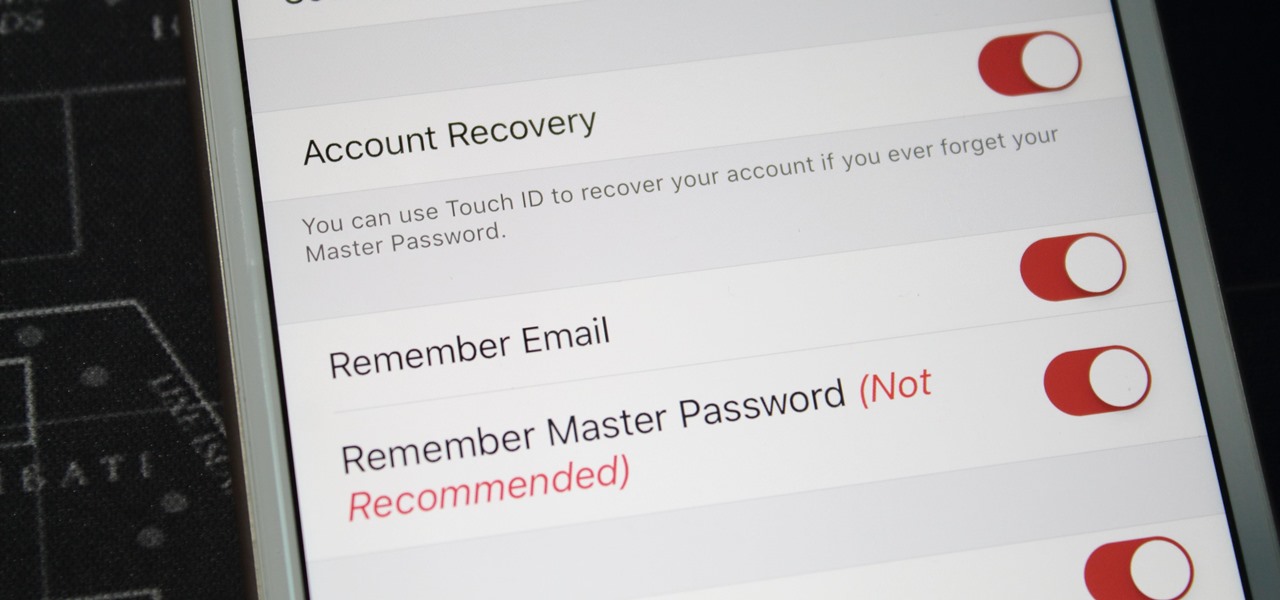
With any password manager, the only password you need to remember is the master password that locks the vault from both hackers and the company. This makes the master password very important. But what happens if you forget this password? Well, LastPass has you covered.

RIP Touch ID. Apple's fingerprint sensor on iPhone and iPad models with Home buttons is about to become phased out on Wednesday, Sept. 12. While Touch ID will remain an integral part of models from the iPhone 5S to the iPhone 8 Plus, as well as the iPad Air 2 through the sixth generation iPad, Face ID will completely take over as the default security method for unlocking future iOS devices.

Traditional subdomain enumeration techniques create a lot of noise on the target server and may alert intrusion detection systems to an attacker's intentions. For a stealthier approach, there's a tool with the capability of finding hundreds of subdomains related to the target website without alarming the server administrators.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.

Sex makes the world go 'round, and when it does, so does gonorrhea. Finally some good news on the growing menace of drug-resistant gonorrhea — a large, long-term study shows a vaccine may work in reducing the incidence of an increasingly dangerous infection.

Open-source data scraping is an essential reconnaissance tool for government agencies and hackers alike, with big data turning our digital fingerprints into giant neon signs. The problem is no longer whether the right data exists, it's filtering it down to the exact answer you want. TheHarvester is a Python email scraper which does just that by searching open-source data for target email addresses.

Single and living in NYC? Forget bars, the female-empowered dating app, Bumble, has just opened a place where you can meet up with your online lovers.

Bitcoin, the decentralized cryptocurrency notorious for its status as the currency of the dark web, seems to be shedding its shady past and is now enjoying soaring highs not seen since 2014. The highly volatile online commodity reached parity with an ounce of gold back in March amid speculation of a pending ETF approval from the Federal Trade Commission. Since then, Bitcoin has doubled in value and analysts predict a bitcoin could reach $100,000 in value in 10 years.

If you've got big plans to lose weight and get healthier in 2017, know up front that it will be an ongoing challenge. It's not easy to break bad habits, and it's even harder to form new and better ones.

Welcome back, my rookie hackers! The Golden Fleece of hackers is to develop a zero-day exploit, an exploit that has not been seen by antivirus (AV) software or and intrusion detection system (IDS). A zero-day exploit is capable of skating right past these defenses as they do not contain a signature or another way of detecting them.

Welcome back, my tenderfoot hackers! Web apps are often the best vector to an organization's server/database, an entry point to their entire internal network. By definition, the web app is designed to take an input from the user and send that input back to the server or database. In this way, the attacker can send their malicious input back to the servers and network if the web app is not properly secured.

Welcome back, my tenderfoot hackers! Recently, Microsoft released a new patch (September 8, 2015) to close another vulnerability in their Windows Vista, 7, 8, and 8.1 operating systems. The vulnerability in question (MS15-100) enabled an attacker to gain remote access to any of these systems using a well-crafted Media Center link (MCL) file.

Welcome learners, lets us proceed further with the information we already have. In this post we will explore more about finding hacked accounts online. We will look into how to find juicy info in pastes which are deleted on Pastebin.

Depending on who you ask, internet connectivity should be a basic human right. With Google recently embarking on a project to provide internet capabilities to remote corners of the world using balloons and satellites while Facebook attempts to do the same with unmanned drones, the concept of free web access is steadily gaining steam.

Welcome back, my hacker novitiates! Recently, I demonstrated a hack where you could redirect traffic intended for one site, such as bankofamerica.com, to your fake website. Of course, to really make this work, you would need to make a replica of the site you were spoofing, or better yet, you could simply simply make a copy of the original site and host it on your own server!

Welcome back, my hackers apprentices! To own a network and retrieve the key data, we only need to find ONE weak link in the network. It makes little sense to beat our heads against heavily fortified systems like the file and database server when we can take advantage of the biggest weak link of all—humans.

Welcome back, my rookie hackers! The more we know about a system or network, the better our chances of owning it and not leaving a trace for investigators to follow. One of the often overlooked sources for information is the Simple Network Management Protocol (SNMP). Many rookie hackers are not even aware of it, but it can prove to be a treasure trove of information, if you understand how it works and how to hack it.

At the beginning of regular gameplay in Grand Theft Auto 5, you play the role of Michael robbing a bank in North Yankton with his accomplices—shooting police and evading a high-speed train in the process. While you do revisit North Yankton during regular gameplay in Los Santos, it's strangely unavailable for online play.

Automation applications bring the future a little closer. If you've seen Minority Report or other futuristic sci-fi movies, the intrigue of having your electronics work independently is something we can all appreciate.

First of all I am glad that I was able to find this website and become part of it. So far I love it. Recently Playstation created a competition where a person has to show how online gaming is good. Pretty simple right? You can enter with an image or a video, however I do not think that an image can really show the fun of online gaming. I have created a video which does show some of the good parts of online gaming and I also tried to keep it fun. I would really appreciate if you would have a l...

Ascension from Black Ops Zombies is one of the coolest maps in online gaming, and has a rather secret Pack a Punch machine you can unlock to upgrade your precious guns. This video will show you how to unlock it by flying on the lunar lander three times then tracking it down.

The ultimate measure of a Call of Duty Black Ops player, or player of most any other online multiplayer shooter, is their kill-to-death ratio, or KD. If yours is lower than 1 you're dying more than you kill, and you probably want to improve you skills and start doing some pwning. This video tutorial will give you a lot of great advice and tips on how to do so. These include class setups, sniping spots, and other awesome knowledge.

Killzone 3 is the biggest shooter to hit the PS3 in quite some time, and one of it's few awesome unique IPs. This video will teach you how to not be a n00b in this awesome game while using the Marksman (hint: spawn trapping), Infiltrator (stabby stab), Engineer (helps Marksman with ammo for more spawntrapping), Medic (revives Marksman for more spawntrapping), Tactician (spawn-point seizing) classes. Spawn

Sleep is Death might just be the future of online gaming. It allows two players to create a story together in a competitive fashion quite unlike anything else ever seen before. This video will teach you how basics of character control in Sleep is Death and help you star telling your story.

This tutorial will let you hack into a wide selection of web cams and online security cameras. The hack is actually quite easy, and is best done with a browser like Mozilla Firefox. Navigate to Google in your browser, and then type in "inurl:viewerframe?mode+refresh". This piece of code will open up a list of active webcams. Then just surf through your choices and watch whatever you want. You can even change the camera angle and zoom in and out of the picture!

If you can't get access to a wifi hotspot or an Internet connection with your PSP, you can use this method to get online. You will need access to a computer that is online, and a USB cord that can connect the computer to your PSP. Then, open up the command prompt on your computer, configure your IP and then add your PSP as a device on the network. This method uses the DNS method of getting to the Internet rather than having to hack a wifi connection.

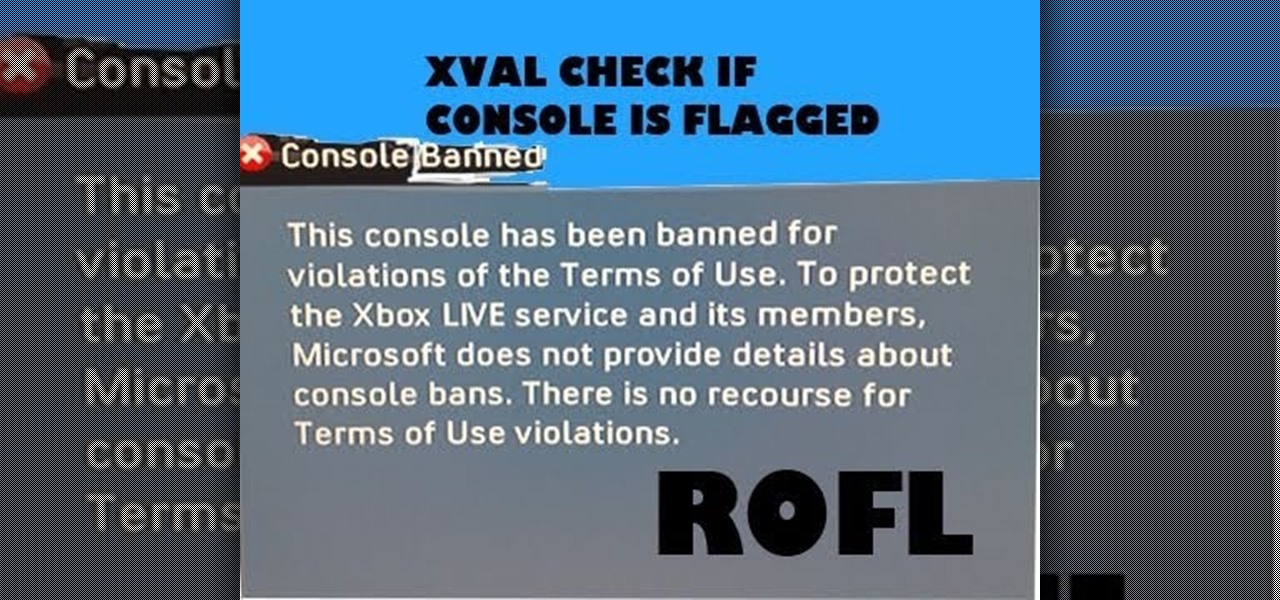
If you engage in any nefarious activity on Xbox Live or simply like to swear a lot when you're playing online, your account may be flagged for a ban. Getting banned sucks, so watch this video to see how to use a program called XVAL to check your account and see if it's been flagged for banning in the next ban wave.

Lots of people have problems with XBox Live matchmaking due to the NAT for their network not being Open. It's not readily apparent how to make your NAT open, but this video will show you how to do it.

You can get push alerts to your iPhone from lots of things online like Facebook and Foursquare, but now here's a way to get push alerts sent to your phone from everyday household objects like the mailbox or the refrigerator. In this Arduino project, a mailbox is wired so that a push alert is sent to the iPod when mail is delivered.

Take it from us: Quality makeup brushes make all the difference between an uneven, lightly pigmented makeup look and a beautiful, expertly applied one. Great brushes allow you to use less product (saving you $) and to apply makeup with more precision.

Let's be honest here: While the web opens up a whole new, vast world of dating opportunities, it simultaneously opens up the possibility of creeps, stalkers, and just plain crazy types.

In this video, we learn how to create a good "make money" website. If you are starting out and trying to make money online, it can be done if you do a lot of work. If you aren't making any money, don't do this, wait until you have money so you are a credible source. You must be able to prove to people that you make a lot of money with this, and you can share with people how to do it as well. Your site will just get included with all the other websites that don't give enough information and do...

Are you sitting alone on a Friday night wondering why you haven't met Mr. Right yet? Well that may be your problem right there - you're just sitting and not actually putting yourself out there! If you're usually super busy at work and other commitments, then you're probably dreading the thought.

iChat is gaining steam as a mainstream online chat program. Fortunately for you, you little prankster, it is exceptionally easy to change someone else's iChat away message to whatever hilarious thing you want from your computer! This video will show you exactly how to do it, with no software to download or anything. Aren't easy hacks great?

In this video tutorial, viewers learn how to watch Star Trek: The Original Series online for free. Begin by opening your internet web browser and go to the You Tube website. Then click on the Shows tab on the top of the page. Now click on the Most Popular tab and select Science Fiction under Shows in the sidebar. Then select Star Trek: Original Series and select the episode that you wish to watch. This video will benefit those viewers who are Star Trek fans, and would like to learn how to wat...

Tying knots can be fun and a great way to help pass the time. They can be used to decorate a variety of different things. For this video tutorial, you'll be finding out how to tie a dragonfly knot easily. It's a decorative Chinese knot and is one of the more popular ones searched for online. So check out the video above, pay attention, and enjoy!

Google is one of the most powerful forces on the Internet, and their technology can be the key to helping you find success in whatever your online endeavor might be, from web design to filmmaking. This video is a part of their Google Webmaster Series, offering help to webmasters the world over on how to best utilize Google in their work. This video will show you how to ensure that your Wordpress blog is safe from the hacker attacks that are so common for Wordpress users.

The internet has been a massive financial windfall for millions of people around the world, and it can be for you as well! There are a lot of ways to make money on your couch by using the internet, and this video will show you five great ways to do it! These include making websites and forums, advertising, and gambling. If you're hard up for cash, give it a whirl!