John explores some ideas on how you might use VoiceThread, a newcomer in the diverse Web2.0 space, that allows you to post pictures and video online and get input from others through voice-enabled comments. VT has some really cool possibilities for the educator. For now, at least, you can get a Pro-account as an educator and set up identities to use for students in your classroom. Teachers can also use VT to post presentations with narration.

This is a tutorial that shows you how to record your computer screen and save it as a video. This is useful for recording something you want to put online. The program I use is called SnagIt. This works for Vista and XP.

Learn the double paradiddle rudiment and a technique to "spice it up" a bit in this online video drum lesson. The double paradiddle is simply a rudiment to practice to improve coordination but can be used in your everyday playing.

If you're putting your email address online on your own website, or sites like facebook or myspace, you may want to be a bit clever about it. Check out this tutorial and see how to protect your email address from spam.

Learn how to use Virtualdub - a free video editing program available online. Learn how to use Virutualdub to edit videos and convert video file formats.
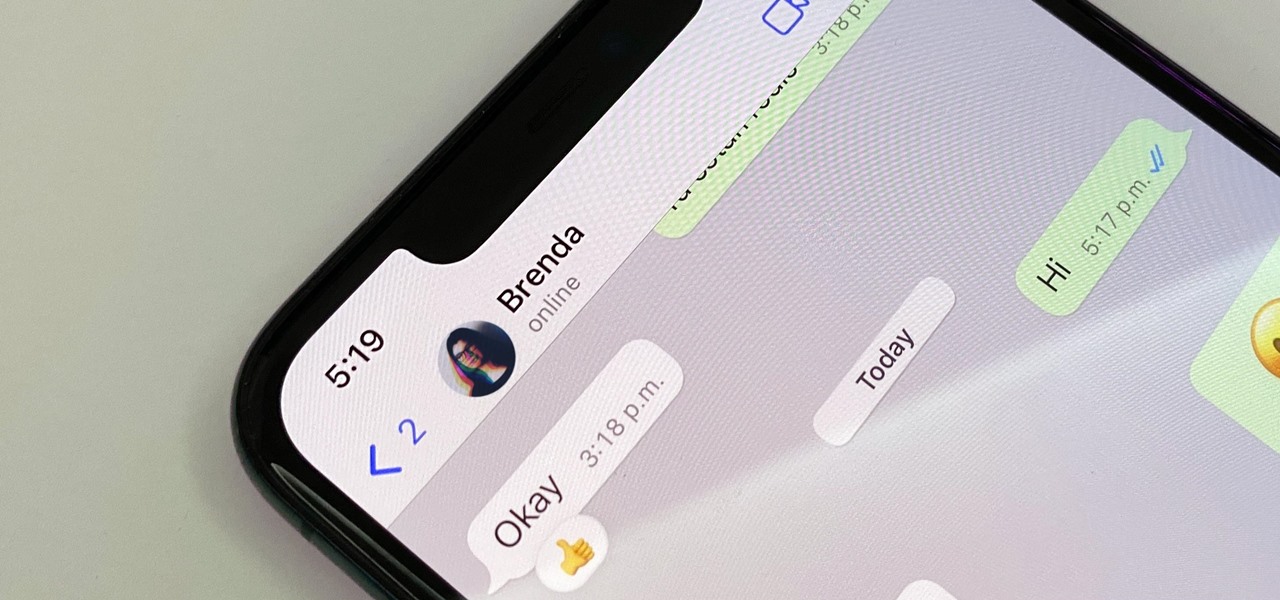
By default, everyone on WhatsApp can see when you're using the app. If someone recently messaged you and sees you're currently online, they may think you're avoiding them if you don't respond right away — especially if you don't share read receipts. However, you can block them from seeing your online or last seen status and apply it to everyone or just specific contacts.

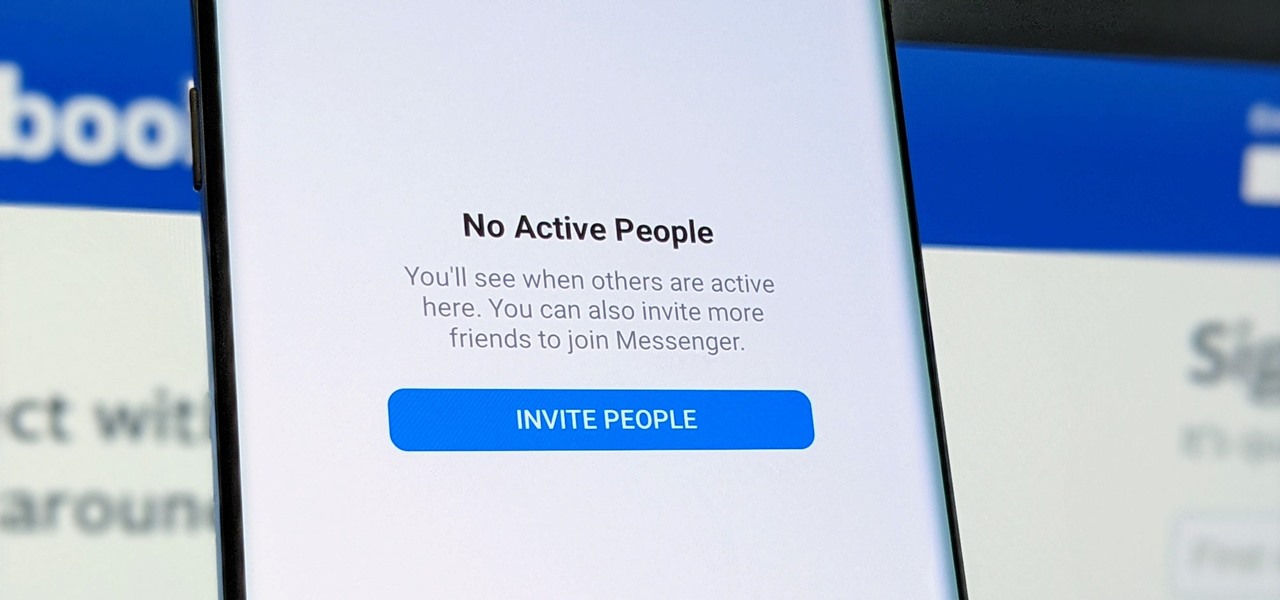
Facebook Messenger's user base has grown so much that it has taken over text messaging as the primary contact method for many people. However, sometimes you might want to hide your online status from specific contacts and appear offline to others. There's a neat little trick you should know that can help you achieve this.

Correctly identifying the underlying technologies that run on a website gives pentesters a considerable advantage when preparing an attack. Whether you're testing out the defenses of a large corporation or playing the latest CTF, figuring out what technologies a site uses is a crucial pen-tester skill.

Among the younger generation, Roblox rivals major titles like Minecraft as one of the most popular online games out there. In fact, it's common to hear children tell new playmates to "friend me in Roblox!" so they can play together online. There's nothing inherently sinister here, but with all the online interaction, kids' safety becomes a factor.

One of the main reasons Authy was able to top our list of the best two-factor authentications apps was its ability to transfer access to a new device. This feature ensures that whenever you get a new phone, you don't lose all your tokens. However, if the process is done incorrectly, you can leave your account vulnerable.

If you didn't get the memo, passwords aren't enough protection for your online accounts. Even a long and complex password offers only one line of defense which can falter. Two-factor authentication adds an additional layer, bolsters your defense, and decreases the risk of your account becoming compromised.

Passwords and data stored in web browsers are extremely valuable to hackers. If not for financial gain, black hat hackers may still leak your passwords and personal information for amusement. Never undervalue what you're worth to a hacker.

Apple removed the Wish List feature from the App Store when iOS 11 was released, which was a huge disappointment, to say the least. While the Wish List still remains in the iTunes Store, it seems gone for good for apps, but that doesn't mean you can't still keep a wish list of interesting apps and games to buy later — using software already on your iPhone.

Using Hydra, Ncrack, and other brute-forcing tools to crack passwords for the first time can be frustrating and confusing. To ease into the process, let's discuss automating and optimizing brute-force attacks for potentially vulnerable services such as SMTP, SSH, IMAP, and FTP discovered by Nmap, a popular network scanning utility.

When traversing the web, you'll regularly come across websites that require you to create an account. With the majority of these accounts, protection is limited to a simple password. Despite this, many people are still using weak passwords such "123456." For these reasons, you really need a password manager, and our research has shown that LastPass is still your best bet.

The Pixel 2 debuted a really cool feature that identifies any songs playing nearby and automatically displays the track's name on your lock screen. It's honestly one of the most inventive smartphone features we've seen in a while, especially considering how Google did it — but strangely, it's not enabled by default.

Mobile augmented reality developer Blippar has updated its mobile app for iOS and Android with an augmented reality face profiles feature based on the company's real-time facial recognition engine.

Killing more than 29,000 people each year, infection with Clostridium difficile (C. diff or CDI) is the most common healthcare-associated infection in the US. In a disturbing development, new research reveals recurring cases of the infection are soaring.

As much as you try to safeguard your personal information, you may have made a small mistake by giving your phone number to the wrong entity, and now you're being bombarded with dozens of spam calls every day. To help parse your call log and reject the proper numbers without answering or trudging through voicemail, a good reverse phone lookup app is needed.

New statements from Apple make it clear that they do not believe a hacker, or group of hackers, breached any of their systems. This comes after a recent report from Motherboard that a hacker gang called the "Turkish Crime Family" is threatening to remotely wipe up to 559 million iPhones by April 7.

Whether you're a seasoned wine drinker or just beginning to explore the wondrous world of fermented grapes, finding fantastic wine on a budget isn't as difficult as one may think. With these 8 tips, you'll see how and why you need not shell out $45 to get a great-tasting, high-quality bottle of wine without settling for vino.

Welcome back, my greenhorn hackers! The Holy Grail of any hacker is to develop a zero-day exploit—an exploit that has never been seen by antivirus (AV) and other software developers, as well as intrusion detection system (IDS) developers. In that way, you can exploit systems with your newly discovered vulnerability with impunity!

After seeing the title of this post from me, you might be thinking, "Why did The Joker made another post on a topic on which we already have a nice sticky post?"

Welcome back to control structures, part two featuring the three types of loops. Here we go! What Is a Loop?

Welcome back, my hacker novitiates! A short while ago, I introduced you to regular expressions. Regular expressions are a language that is particularly useful for finding complex text patterns in streams of data.

This video will show you handy tips and tricks about Google search engine. These tips will help you to speed up your computing or browsing experience. This video contains tricks like Search by location, Filter image search, how to see sites that aren't online, movies running in a city theaters etc. This video is the 2nd part of the serial. You could also watch the part 1 here vimeo.com/104089915.

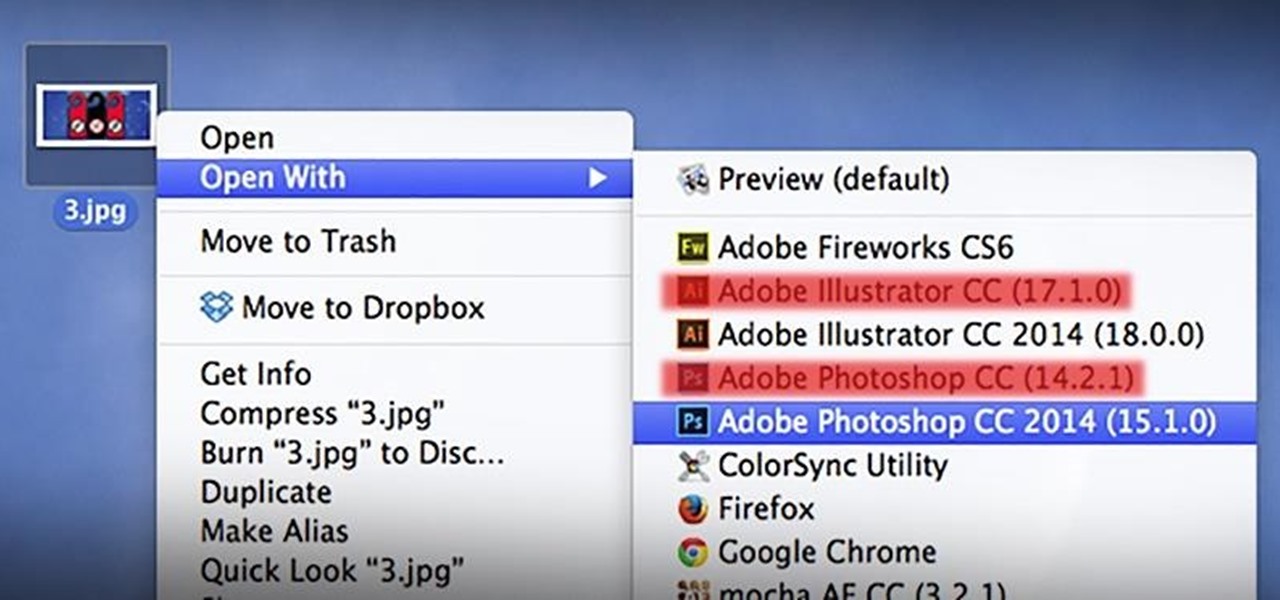
As a regular Mac OS X user, I have a love/hate relationship with the "Open With" contextual menu. Sometimes, it has just what I need. Other times, it's often packed with unnecessary or duplicate items, or missing the app I want to open the file up with the most.

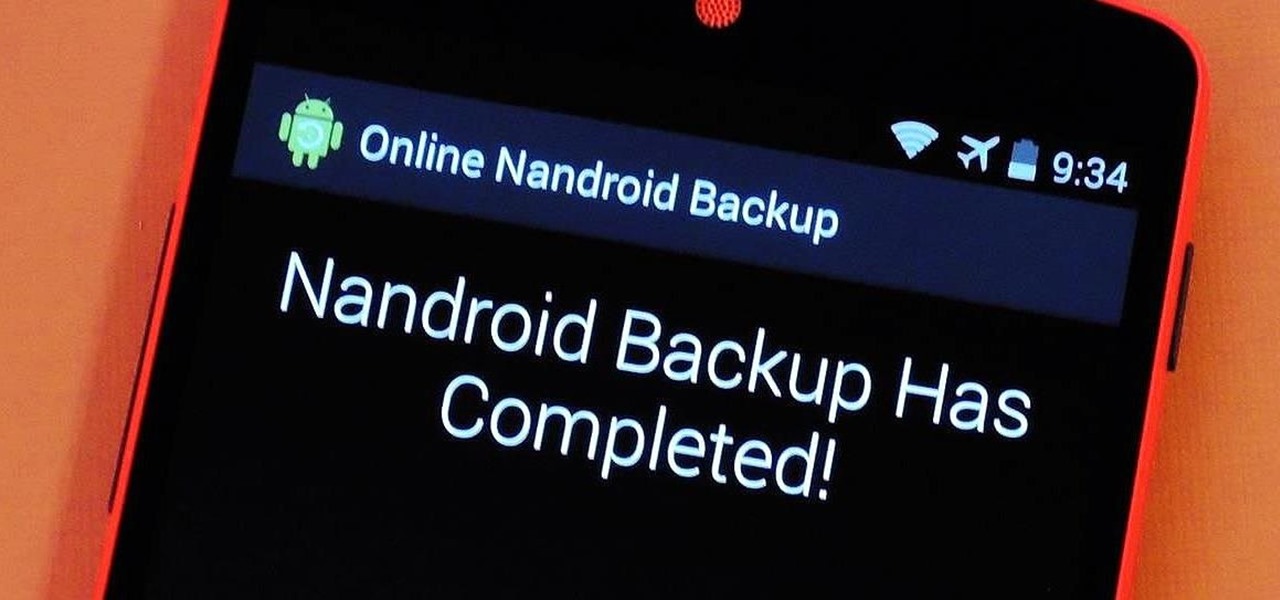
If you have a custom recovery installed on your Android device, the first thing you should have done as soon as you finished installing it was to create a Nandroid backup. But if you didn't, I'm not here to judge—I'm here to show you a much easier way.

Free online dancehall step tutorials every wednesday at 10am for the entire summer! Learn your favorite dancehall steps in the privacy of your own home! This one covers the Nuh Linga steps.

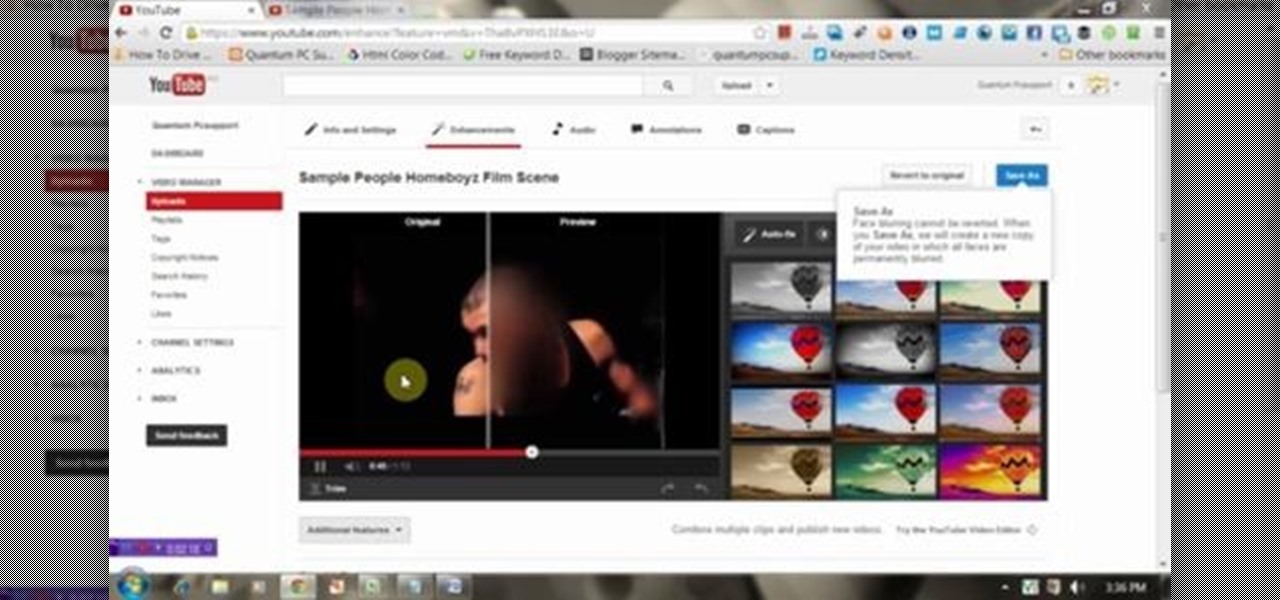
We know that YouTube is the most popular online video sites. But this video will provide an idea how to blur faces in YouTube video. So please watch the video and follow all the steps to do it yourself.

Overweight dancer Whitney Thore has become a star - shaking her 25-stone booty in online videos. The 29-year-old radio producer's clip A Fat Girl Dancing showcasing her incredible dance skills went viral and earned her fans the world over. Whitney, who has Polycystic Ovary Syndrome, wants to destigmatise the word 'fat'. Six months ago she launched the No Body Shame Campaign fight fat phobia and teach people to love their bodies.

Welcome back, my novice hackers! My recent tutorials have been focused upon ways to NOT get caught. Some people call this anti-forensics—the ability to not leave evidence that can be tracked to you or your hack by the system administrator or law enforcement.

Learn How to Draw Johnny Test with the best drawing tutorial online. For the full tutorial with step by step & speed control visit: How to draw

Learn How to Draw FanBoy with the best drawing tutorial online. For the full tutorial with step by step & speed control visit: How to draw

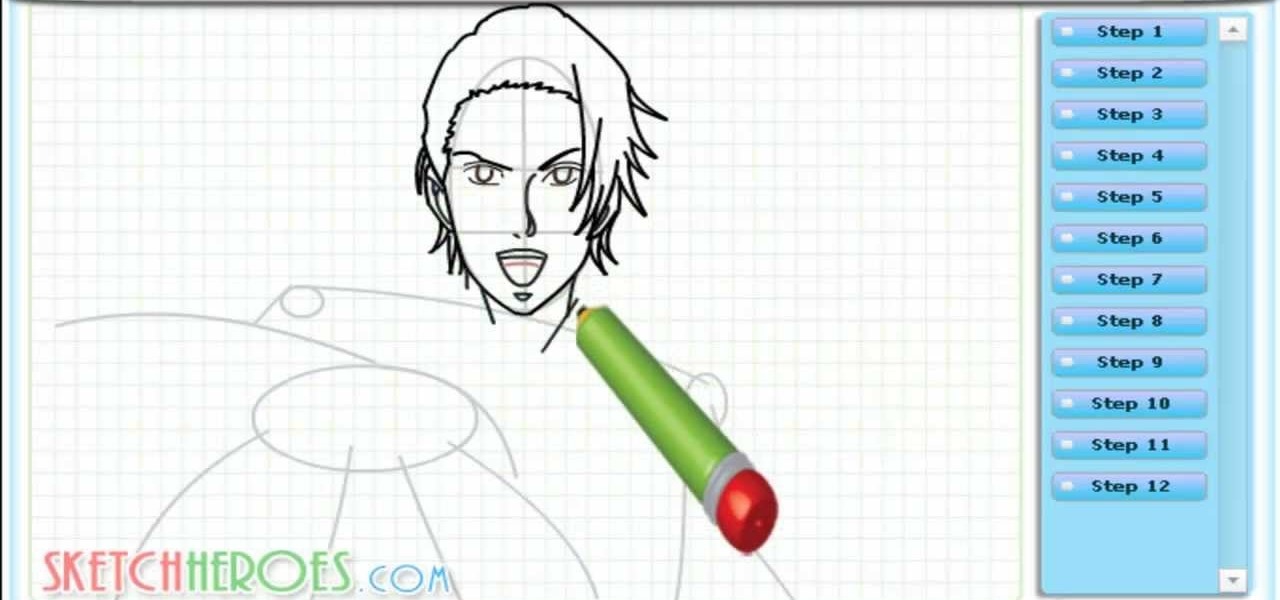
Learn How to draw Yoruichi Shihoin of Bleach with the best drawing tutorial online. For the full tutorial with step by step & speed control visit: How to draw.

Learn How to Draw Kinji Tohyama (area the Scarlet Ammo) with the best drawing tutorial online. For the full tutorial with step by step & speed control visit: How to draw

Learn How to draw Snow White with the best drawing tutorial online. For the full tutorial with step by step & speed control visit: How to draw

Learn How to Draw Miss Martian (Young Justice) with the best drawing tutorial online. For the full tutorial with step by step & speed control visit: How to draw

Learn How to Draw Kou Ichinomiya (Arakawa under Bridge) with the drawing tutorial online. For the full tutorial with step by step & speed control visit: How to draw

Learn How to Draw Justin (Total Drama Action) with the best drawing tutorial online. For the full tutorial with step by step & speed control visit: How to draw