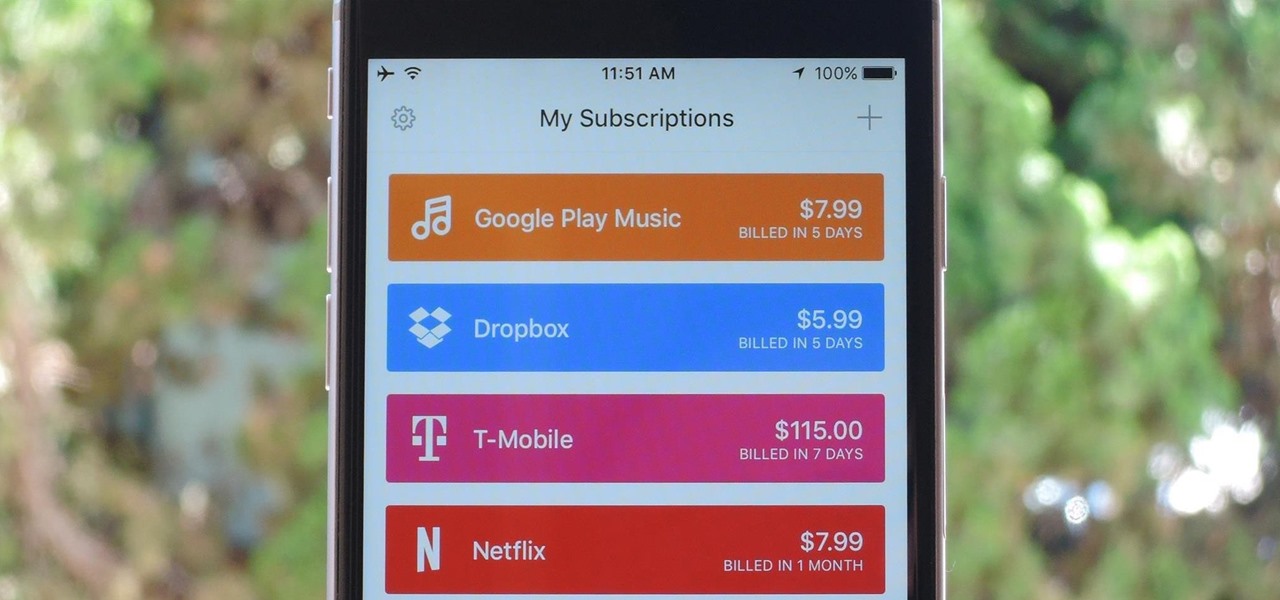
As the internet continues to become a bigger part of our day-to-day lives, we slowly but surely start to rack up a bunch of web-based subscriptions. These internet subscription services—Netflix, Hulu, and Amazon Prime, just to name a few—may seem innocuously cheap individually, but when combined, they actually comprise a significant portion of our monthly bills.

Watching the NCAA Men's Division I Basketball Tournament without cable used to be easy. As long as you had an internet connection, CBS and Turner (TBS, TNT, and TruTV), which co-broadcast March Madness, let you watch all 67 games online free of charge.

Coverage for the 88th Academy Awards, aka the Oscars, will air live this Sunday, February 28th at 4 p.m. PT (7 p.m. ET). The ceremony itself, hosted by Chris Rock, is set to begin at 5:30 p.m. PT (8:30 p.m. ET).

NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.

I mentioned in 2015 I wanted to start a 'DoXing' series, and since I havent seen this on Null Byte, I am now going to introduce this to the community.
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?

Google seems to be following Apple's and Microsoft's lead, as the "point" update to Android 6.0 Marshmallow (6.0 -> 6.1) will reportedly allow multi-screen support. Android 6.1 is expected to debut in June 2016.

Welcome back, my tenderfoot hackers! WordPress-based websites are among the most numerous on this planet (maybe other planets too, but I can't vouch for that). According to WordPress's own website, WordPress powers 23% of the top 10 million websites. That's approximately 2.3 million sites using WordPress!

Over the past decade the Internet community has been witness to the rise of many new forms of online interaction. These new technologies have given rise to anonymous networks (like TOR), black markets within the deep web network (like the Silk Road), and even forms of digital currency, or more accurately crypto-currencies, such as Bitcoin. All of these technological advancements have contributed to securing users around the world and protecting their privacy. Therefore it is no surprise that ...

You'll have to forgive me if I sound a little overexcited about this, but in my opinion, Google's "Now on Tap" is one of the most innovative™ smartphone features that I've seen in years. Sure, Microsoft heard about the feature being in the works and rushed out a similar Android app so they could say they were first, but that solution pales in comparison to this one.

Computer system authentication is critical to keeping systems safe from unwanted users, intruders, and abusers. Basically, authentication is the process of the potential user proving they are an authorized user.

Imagine this scenario: You exploited a system using metasploit and you want to install a backdoor. You have a few options;

One tweet can get your fired from your job. At least, in the cases of Gilbert Gottfried, Rashard Mendenhall, Ozzie Guillen, and Mike Bacsik, who were all either fired or forced to resign from their jobs after posting regrettable tweets online.

The only mail I like getting comes in the form of an Amazon package, but when I go to my mailbox, it always ends up being a pile of credit card offers and catalogs I could never see myself ordering from. Those pieces of junk mail usually end up in the trash, which is horrible when you think about all the trees that had to get cut down in order to produce them.

There's no denying it was a hectic 2014 here in the United States. We saw the rise of ISIS, dealt with an Ebola scare, and witnessed the turmoil in Ferguson (and its aftermath). Plus, let's not forget about all of the hype revolving around The Interview, in which Sony was hacked.

Earlier this month, John Oliver spent a segment on Last Week Tonight explaining native advertising, a practice followed by many online media outlets such as BuzzFeed, The New York Times, and VICE, which combines editorial content along with sponsored advertisements.

A few days ago I finally finished my 2 week journey into trying to get OpenVas to work properly. You all may have noticed that you can't just click the setup openvas in kali and have it working properly.

As Microsoft unveiled their new Windows Phone 8.1 software update yesterday, undoubtedly the most memorable takeaway was their showcase of Cortana. Competing directly against Apple's Siri and Google's Now, Cortana is Microsoft's entry into the digital voice assistant fray, and the official replacement to their search app.

We softModders come from all walks of life, and sooner or later, our devices begin to reflect who we are. Maybe you've followed one of our guides on customizing your Nexus 7, such as getting the exclusive Google Experience Launcher or hiding the navigation buttons for more screen space, or maybe you used one of the various Xposed mods we've covered.

Sometimes I actually search Google Images for things other than GIFs and pictures of athletes' extremely hot wives. Google Images has helped me with school projects, work, and proving my friends wrong on numerous occasions. Unless you're strictly using it for the latter, you're going to have to be aware of copyrights.

There are already hundreds of glitches out there for Grand Theft Auto 5 Online, but most of them are useless. Most of them don't do anything to benefit your gameplay, but they're still pretty fun to mess around with. One such glitch, shown off by YouTuber AquibTV below, lets you inside any building in Los Santos. Los Santos is a big ass city and there are tons of buildings that you cannot get into without using a glitch like this one.

Want the best view of Los Santos in Grand Theft Auto 5 without having to purchase a plane or steal a chopper? You can enjoy the sights of the Los Angeles replica by hopping on one of the trains rolling around the city—and forget about riding in one of the cars, we're going straight into the cockpit.

As you level up in online gameplay for Grand Theft Auto 5, certain vehicles become inaccessible—no longer spawning as they regularly would. One such vehicle is the Cargobob helicopter, otherwise known as the largest and heaviest helicopter in the game. If you're no longer able to spawn a Cargobob in GTA 5 and want one for your own, you can purchase one with a little help from YouTube user omgurheadsgone.

So, you've got a brand new PlayStation 4, but unfortunately, you've got "No Signal" now, too. You can't really game or watch movies on your new toy if you can't even bring up the PlayStation menu on your TV screen.

If you are willing to teach online, you might have thought of making online courses. But if you found it too hard, you can start with micro-courses, that can be created in 10 to 30 minutes. Step 1: Define 5-7 Main Points That You Will Cover in Separate Lessons.

Some women see Halloween as a once-a-year opportunity to dress in something skimpy without dealing with as much scrutiny as usual. That can be fun, but not everyone is comfortable enough wearing so little, and the costumes are so boring and repetitive. Some of us just don't feel like freezing.

If there's one way to get a visceral response from someone, it's bringing up the DMV. Regardless of the reason, whether it's the long lines, disgruntled employees, or just general inefficiency, I have yet to meet a single person who doesn't mind the trip. Just look at all those happy faces.

If you weren't aware, all music purchased online through iTunes, Amazon, and other digital audio providers have information embedded that can be used to identify the buyer and transaction of the digital music file. This may seem like something you should be disclosed about in their terms of use, but it's not.

We've all had that awful, sinking feeling when something you've been typing away at is suddenly gone. Maybe you accidentally hit the Back button, lost your internet connection, or your computer crashed, but whatever the reason, losing your work totally sucks. A lot of word processing programs have a built-in auto-save feature to prevent you from losing everything, but most websites and blogs haven't gotten there yet. An extension for Chrome and Firefox called Lazarus: Form Recovery can help y...

UPDATE: The whitehouse petition has received enough signatures to require a response from the government. Your voices have been heard! Now we wait...

UPS gives you all the tools you need to take away the complications and confusion of international shipping. UPS provides simple, step-by-step online instructions and helps guide you through the required documentation to reduce the likelihood of customs delays.

It's finally here. After months of amazing games and one of the best playoffs I've seen in years, two teams have finally made it to the top of the mountain. The Baltimore Ravens and the San Fransisco 49ers are set to square off February 3rd at the Mercedes Benz Superdome in New Orleans, Louisiana for Super Bowl 47. Historically, the most watched event on television is the Super Bowl, but that's exactly where the problem lies—television.

For the most part, keyboard shortcuts are great. They save you some time and make it easier to do everything right from the push of a button. But like most things in life, there is always a caveat, and in this case, for me—it's a huge one.

Most of us have some sort of malware scanner or antivirus program on our computers, but what about our smartphones? A lot of people don't realize that computers aren't the only devices that are susceptible to malicious software and apps—they can follow you on your smartphone or tablet, too.

Sitting in the Powell Library at UCLA was a constant thing for me. Directly after class, I would streamline my way there to study all night until my eyes shuttered to sleep. For the most part, my classes and professors managed to keep my studying online via PDFs, emails, long essays and journal entries.

Apple's new iPhone 5 has enjoyed three weeks out in the public since its September 21st release. Millions of consumers have been shelling out big bucks and waiting in long lines just to get their hands on it. But sometimes users forget to actually keep their hands on their new phone, causing something like this... It only takes a second to drop your new iPhone 5, but the pain of picking up the phone and turning it over to reveal a cracked display lasts a lifetime. Well, not exactly a lifetime...

Are you interested in beginning research of your family's history? I began this journey about 3 or 4 years ago and here is what I found. I've done almost ALL of my research online, and gotten farther, faster and more comprehensively than anyone else who has researched my family the old fashioned ways. This is the kind of thing that technology is made for. Here's how to use it.

QR codes allow you to quickly and easily store and retrieve data within a single image. Much like barcodes at grocery stores, QR codes are images that can be scanned to discover data, such as an online website URL. Additionally, they can also be created by inputting text data into a QR code generator. Try scanning some of the QR codes in this video with an app on your phone or tablet to see how they work!

Mission 12 is one of several points in the StarCraft 2 campaign when you are presented with options for what mission you want to do. This video will show you how to beat one of them, Safe Haven.